How to Build a Zero Trust Architecture
$4.45 million.
That’s the average cost of a data breach in 2023, according to IBM’s annual Cost of Data Breach report, representing an increase of 15% over the last three years. Cyberattacks are changing, and traditional techniques and over hyped new AI technologies are not enough. Your business needs a security model that has been removed from the hype cycle and is validated and without hyper-inflated expectation and disillusionment. Enter Zero Trust Architecture — a paradigm shift that fundamentally changes how organizations protect their digital assets.
But what is Zero Trust Architecture (ZTA) and how does it differ from Zero Trust Network Access (ZTNA)? If you have ZTNA, isn’t that enough? Let’s dive in.
Understanding Zero Trust Architecture: What’s the difference between ZTNA and ZTA?
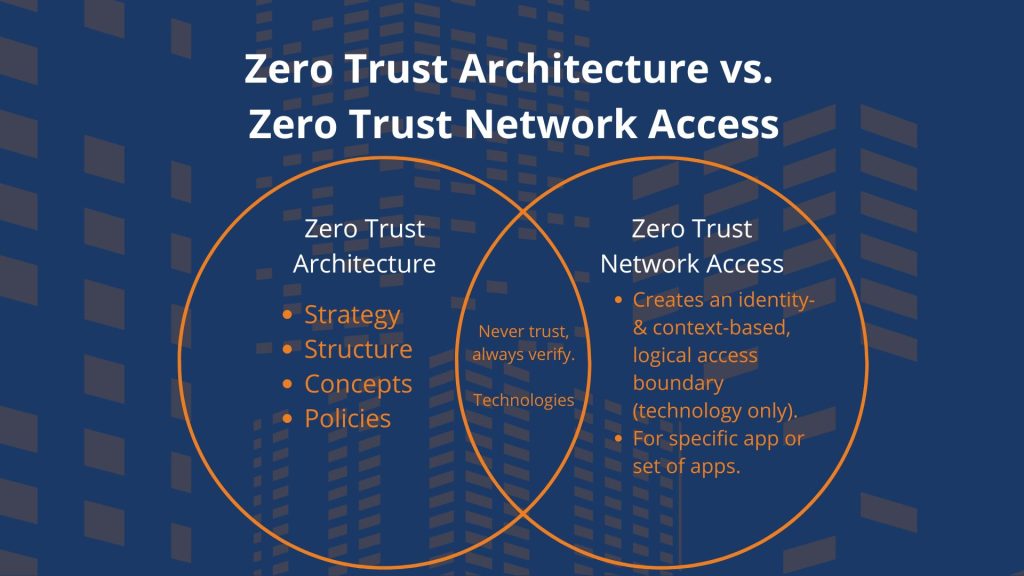
Zero Trust Architecture is a security model based on the principle of "never trust, always verify."
Defined by NIST, zero trust architecture is “an enterprise’s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a zero trust architecture plan.”
In other words, unlike traditional security models that assume everything within the network is safe, ZTA assumes that threats could exist both inside and outside the network. This model enforces strict identity verification and access controls, ensuring that only authenticated and authorized users have secure remote access to resources. And importantly, zero trust architecture refers to the overall security strategy and structure, including technologies, policies, and concepts.
But wait, isn’t that the same as ZTNA, or the zero trust security model as a whole? Not quite.
Zero trust network access, or ZTNA, is the main technology associated with ZTA (not to be confused with zero trust access). However, ZTNA is not one single technology or solution — rather it is a combination of technologies that make up zero trust architecture. For example, one such technology that delivers the essentials of ZTNA tenets is a business VPN. By creating a secure virtualized network, you’re able to continually verify and enforce the principle of least privilege access.
In other words, zero trust architecture is the structure, while ZTNA is the collection of technologies within that structure.
Key principles of zero trust
Whether we are talking about ZTA or ZTNA, there are a few key principles that carry through both. These include:
- Never Trust, Always Verify: Every access request is thoroughly verified, regardless of where it originates – even if it is originating from a device that is recognized and used often. This helps prevent attacks through cloned IP addresses.
- Least Privilege Access: Users are granted the minimum access necessary to perform their tasks, reducing potential attack vectors. This means there is not one single employee, including the CEO, who has access to every single system. By doing this, even if one person’s credentials are compromised, a bad actor will not immediately gain access to every possible part of the attack surface, thereby minimizing the attack surface and reducing risk overall.
- Assume Breach Mentality: Constantly operate under the assumption that a breach has occurred, and design systems to minimize damage and speed up detection and response. This requires continual testing and thinking like a threat actor to identify potential weak points in your security strategy and attack surface.
Specific to ZTA, there are a few additional key principles in the zero trust device pillar, according to the National Security Agency:
- Identification, inventory, and authentication
- Detection of unknown devices and configuration compliance checks of known ones
- Device authorization using real time inspections
- Remote access protections
- Hardware updates and software patches
- Device management capabilities
- Endpoint detection and response for threat detection and mitigation
Benefits of implementing zero trust architecture
Despite its popularity in recent years, zero trust isn’t just a buzz word anymore and has made its way through the hype cycle. What started as an answer to a major network security flaw, implicit trust, is now on its way through Gartner’s “slope of enlightenment” to the “plateau of productivity.” That means zero trust has withstood the test of changes in technologies and workforce changes.
Stability in strategy isn’t the only reason to consider a zero trust framework. Research from IBM found that zero trust reduces the cost of a data breach by about $1 million.
To have the mindset “never trust, always verify” can seem a bit daunting. It requires your team to never let their guard down, no matter where they are in the organization. But ZTA doesn’t have to be a negative or overwhelming architecture to implement. In truth, by simply implementing ZTNA essentials you’ll see many of the same ZTA benefits that make it such an attractive architecture.
For example, the zero trust approach as a whole can help you gain:
- Enhanced Security Posture: By continuously verifying users and devices, organizations can better protect against unauthorized access and can create more secure access for users.
- Reduced Attack Surface: Limiting access to only what is necessary reduces the number of entry points for attackers.
- Improved Visibility and Control: Continuous monitoring and strict security controls provide better insight into network activity and potential threats. You’ll also have more granular control over cloud environments.
- Lower costs if an attack is successful: With fewer resources that can be compromised in a single breach, you can reduce or mitigate the high costs of a breach.
Pillars of Zero Trust Architecture
We mentioned earlier that ZTA is made up of ZTNA technologies or zero trust solutions and policies. While that is true, there are also a few additional pillars of ZTA to consider.
Identity and Access Management (IAM)
Strong IAM is crucial for ZTA. This includes implementing robust authentication methods such as multi-factor authentication (MFA) and single sign-on (SSO) to ensure that only verified users can access the network.
Network segmentation and microsegmentation
Dividing the network into smaller, isolated segments and applying granular access controls helps limit the lateral movement of threats within the network. This approach confines potential breaches to isolated segments, minimizing their impact. Network segmentation also helps enforce least privilege. You can dive into how to set up micro-segmentation in our recent post about implementing ZTNA.
Continuous monitoring and risk assessment
Real-time visibility into network activity is essential for identifying and mitigating threats. Behavioral analytics and anomaly detection tools can spot unusual activity, while automated threat response mechanisms can swiftly address breaches. However, this takes a human element as well. This can’t all be automated or relegated to a software — you’ll need someone who is able to review these logs, conduct random pen-testing, and create response actions to see this have the most impact.
Implementing Zero Trust Architecture
Implementing ZTA begins by implementing ZTNA technologies and moves into implementing zero trust policies and procedures. But, when it comes down to it, the biggest obstacle is creating a shift in the mindset around ZTA and ZTNA as a whole.
It should be noted that implementing an entirely new architecture can be far more daunting than implementing one set of technologies. Many small and mid-size businesses find it more effective to ease into zero trust implementation, first setting up ZTNA basics and then moving into the architecture as a whole. No matter which strategy you prefer for your business, there are a few commonalities to consider:

Assessing current security posture & identifying critical assets and data
Begin by evaluating your current security infrastructure to identify vulnerabilities and critical assets. This assessment forms the foundation for your zero trust roadmap.
During this step, you’ll identify all users, their locations, and how they typically interact with assets and sensitive data in your organization. Identify critical assets and systems and where they are currently housed, how they can be accessed, and through which networks your team works. If you have a business VPN product in place, this is a good time to determine what data is currently being routed through tunneling or split tunneling so you can note any traffic that should be tunneled and isn’t (yet).
You may find this step to be the most time consuming — don’t worry, that’s actually a good thing. The more deeply you know and understand your attack surface and current security risks and posture, the easier it becomes to identify the areas of weakness that should be addressed first.
Designing a zero trust roadmap & integrating zero trust with existing security tools
Next, you’ll need to take your assessment and design your zero trust roadmap. This can be broken into a few smaller steps.
- To start, clearly define the zero trust policies you’d like to enforce. Do you want to completely adopt zero trust and enforce SSO, the principle of least privilege, microsegmentation, and IAM? Or are you hoping to start with more of a soft launch, first enforcing MFA?
- Next, you’ll select appropriate technologies and solutions that align with your security goals. However, this doesn’t mean you need to overhaul your tech stack or even consider a whole new suite of security tools. It’s fairly likely that you already have many of the tools and security solutions you already need, you just need to make sure the policies are configured properly to enforce zero trust architecture.
For example, you likely already have a VPN for secure remote access or protecting access to SaaS apps in place. That means you are already able to enforce some of the core principles of zero trust, like least privilege access and continuous sign-on, without needing to purchase entirely new software.
- Finally, map out a phased implementation approach to create a smoother transition. Map out the time it will take to implement each individual step, and don’t forget to factor in the most important element into your phased approach: the human element. In your phased approach, make sure the people who will be monitoring for threats and vulnerabilities are phasing these new technologies and procedures into their days.
Training and educating employees
Employees play a crucial role in the success of any security initiative, but especially when it comes to zero trust. Training and educating your team on zero trust principles and best practices fosters a culture of security awareness and adherence to new protocols, but it can’t rest only with the security or IT team. Zero trust requires an organization-wide culture shift to embrace the skeptical — and if your team is used to being trusted implicitly, this can come with some push back.
When educating employees on your zero trust initiatives, try adjusting the message and frame it positively: you’re on a journey to “build digital trust.” Remind them that zero trust as a practice does not mean you want to lock them out of systems, or that they will need to take extra time consuming steps that they really don’t care about. Rather, it just means they will need to verify their identity to gain full access to the things they need so they can prevent phishing attacks and breaches.
Zero trust architecture best practices
Although ZTA (and ZTNA) are ongoing practices and architectures that will continually evolve with the changes in cybersecurity, there are a few best practices to keep in mind. These include:
- Regularly review and update zero trust policies. You may find it useful to review these on a quarterly, semi-annual, or annual basis, but they should be reviewed at least once per year.
- Implement strong password policies and MFA. Passwords are the very baseline of security for all zero trust models. Periodically check that all password policies are being followed and help any users with outdated passwords update them immediately.
- Encrypt data both at rest and in transit. Data on the move is data at risk. Secure encryption through a VPN provider or network security provider is crucial.
- Conduct regular security audits and penetration testing. Go beyond phishing tests and make sure that your team is regularly looking for any suspicious activity as well as any areas where bad actors may be able to gain access.
- Ensure timely patching and updates of systems and applications. This includes looking into all security vulnerabilities for software providers and making sure all software is up to date.
- Foster a culture of security awareness among employees. If possible, conduct periodic surveys to make sure that the team has a baseline of knowledge on how to keep the company safe and implement training sessions for areas where people may lack knowledge.
The future of zero trust architecture
ZTA is not immune to trending technologies, like AI and machine learning. Although these enhancements may one day reshape the architecture as a whole, for now ZTA remains a dynamic, forward-looking security model. For IT managers, the future will likely involve more zero trust initiatives — whether full zero trust architecture or smaller technology adoptions like zero trust network access. No matter what the future holds, the transition from a perimeter-based security model to zero trust is not linear and it is not done with the flip of a switch. It is a journey.
To find out how OpenVPN can help in your journey to zero trust, take a tour of our cloud-based secure remote access VPN, CloudConnexa.


