How a VPN Helps with Network Security
Once upon a time, network security meant servers on premise. A firewall would guard business data as internet traffic traveled in and out of the network. But today? Modern business doesn’t operate strictly on-prem.
With the COVID-19 outbreak, the number of people working off-site some or all of the time grew exponentially — and suddenly. That shift forced cybersecurity pros to revisit their security plans. Their online privacy solutions had to make sure their most valuable asset — their data — would be protected no matter where employees access it.
More & more of business's essential data is hosted in the cloud.
Even as restrictions lift, organizations still have remote teams. This means more and more of a business’s essential data and services are hosted in the cloud. These two factors mean that the need to continually revisit network security is here to stay.
The good news is that one of the most straightforward, readily available network security solutions for remote workforce internet access is a VPN, or virtual private network.
What is a VPN?
A virtual private network (VPN) is exactly what the name suggests: a network host for your team and resources that’s private and secured behind 2FA and data encryption, virtually accessible so your team can connect from anywhere.
Types of VPNs
Different VPNs offer different functionality. A layperson may just want a private connection to watch Netflix on their iPhone. Business VPNs should:
- Offer secure connections.
- Have servers in different countries.
- Conceal internet activity.
- Hide browsing history from ISPs.
- Have capacity for large volumes of network traffic.
- Include a kill switch.
Businesses of all sizes use these tools to set up the exact access & granularity they need.
Our next-gen VPN, known as CloudConnexa, supports extensive configuration options. Businesses of all sizes use these to set up the exact access and granularity that they need for their company. While there are far too many options for us to show all the setups available, we can provide you with an overview of two common setups: Remote Access and Site-to-Site.
Remote Access
Connecting employees to the private network from various remote locations.
VPN Server
Grant and control access with your VPN server hosted on the private network.
VPN Client Apps
Securely connect with the secure VPN server using clients (a.k.a. VPN app) on user’s computers and mobile devices (iPhone and other Mac devices as well as android phones and tablets)
What is Remote Access and why would it benefit my business? Read details about it here: Remote Access VPN.
Site-to-site VPN
Connecting multiple, fixed sites (branches, offices, etc.) over a public network.
Intranet VPN
Connecting remote and main offices.
Extranet VPN
Connecting partners or customers with the main office.
What is site-to-site and why would it benefit my business? Read details about it here: Site-to-site VPN routing.
Types of VPN Protocols
Remote Access and site-to-site VPNs are based on different VPN security protocols. Each VPN protocol offers different features and security:
- Internet Protocol Security or IPSec.
- Layer 2 Tunneling Protocol (L2TP).
- Point–to–Point Tunneling Protocol (PPTP).
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS).
- OpenVPN.
- Secure Shell (SSH).
How Does VPN Support Network Security?
How does a VPN work? Network security stops unauthorized entry into corporate networks by focusing on devices, not endpoints.
A VPN creates a virtual tunnel over your network so data can travel securely from Point A to Point B. IT gives employees tunnel access — usually an ID and password — so they can safely access both your private network and the public internet with a VPN connection.
And the unauthorized users? A VPN solution ensures they can’t tap into your network or connected devices.
VPN Encryption Boosts Network Security
Encryption scrambles data so only authorized users can see it. Hackers, fraudsters or other bad actors who manage to intercept it are out of luck.
Even if cyber fraudsters intercept your data, its safe inside the VPN tunnel.
Let’s assume an employee is working from a café, shared workspace, hotel, or airport, and that employee is authorized to access your company’s business-grade VPN. (Note: Business- or enterprise-grade VPNs are not the same as free VPN services.) Using a VPN client installed on their device of choice, and a public wifi network, the employee can establish an encrypted connection between the user’s device and your VPN. That device, and any other that connects to your VPN, will set up encryption keys on both ends of the network connection. Those keys will then encode and decode the information being shared back and forth.
Once the employee working at the café establishes an encrypted VPN connection, using the café’s wifi as a hotspot with a VPN client, their data is protected by the VPN. Even if cyber fraudsters manage to get into the café’s network, your employee, and their data, is safe inside the VPN tunnel.
Enhance Network Security with VPN Access Control
Like encryption, access control is a critical component of network security. Access control and management determines who has access to what (i.e., data, resources, applications) through the use of authentication and authorization. And, as more organizations move data storage and apps to the cloud, the need for access control increases because it provides more reliable access security than single sign-on (SSO).
Network administrators can reduce the risk of data breaches, both internal and external, by limiting employee access to only the data and apps they need to do their jobs. This is done by setting up multiple VPNs that connect to different resources. Then admins can assign users to a specific VPN based on access control system policies and employee needs.
The fewer people you have accessing different resources, the smaller your margin of error becomes.
How does a VPN restrict unauthorized access? By evaluating and authenticating the required credentials of authorized users. Access control then grants the access and actions associated with the user’s credentials and IP address.
The general rule of thumb for access and security should be: only give people access to what they need. The fewer people you have accessing different resources, the smaller your margin of error becomes. A VPN gives network administrators the ability to do just that.
VPN Security Extends to Mobile Devices
Many companies have a BYOD (bring your own device) policy. This lets employees use the operating system(s) — whether that's Apple iOS, Microsoft Windows, Android, or Linux — they prefer. The market size for BYOD is forecasted to reach $366.95 billion by 2022 compared to the $94.15 billion it was worth in 2014. And for good reason: allowing employees to use their own personal devices, rather than company-issued devices, is convenient and cost-effective. One potential drawback, though, is adequately securing online activity on BYOD devices.
All those billions of devices used by employees for work need to access corporate networks, and that’s where VPN technologies come into play. With VPNs, network admins can limit what devices can access. Employees can connect to public wifi with a remote access VPN client and confidential and/or personal data is invisible to the ISP (internet service provider).
Mitigate DNS Hijacking Risk with a VPN
Content filters block harmful content to protect networks and users. Modern cloud-based filters are efficient and effective.
The most obvious use for content filtering is inappropriate or NSFW (‘not safe for work’ content). It also guards against Domain Name System (DNS) hijacking attempts such as:
- Middleman Attacks.
- Malware Attacks.
- Cache Poisoning.
- Rogue DNS Server.
- Router Exploitation.
An enterprise-grade VPN service can help prevent each of these DNS hijacking scenarios by protecting routers, DNS servers, and block access to known phishing sites.
Best of All: VPNs Can Be Deployed in the Cloud
Until recently the most common types of VPN use cases were Remote Access and Site-to-Site. Remote Access VPNs are the more popular version because they grant and control access with your VPN server hosted on the private network, and users securely connect to the network using client VPN apps installed in devices.
Just as the name suggests, the latest in next-gen VPN technology, Cloud VPN, is specifically designed for the cloud; on-prem hardware is not required. This is a significant development because the number of companies opting for cloud rather than in-house data centers is growing rapidly. How rapidly? IDC reported that, "By the end of 2021 ... most enterprises will ... shift to cloud-centric digital infrastructure and application services twice as fast as before the pandemic."
With the increased use of cloud data centers, it makes sense to move network security to the cloud, too.
VPN-as-a-service (VPNaaS), including CloudConnexa, lets users securely access their company’s cloud-based apps, data, and files with an internet connection and VPN client installed on their device(s).
This next-gen VPN:
- Securely connects remote workers anywhere
- Can be set up and deployed in much less time than traditional VPNs
- Is inherently flexible, agile, and scalable
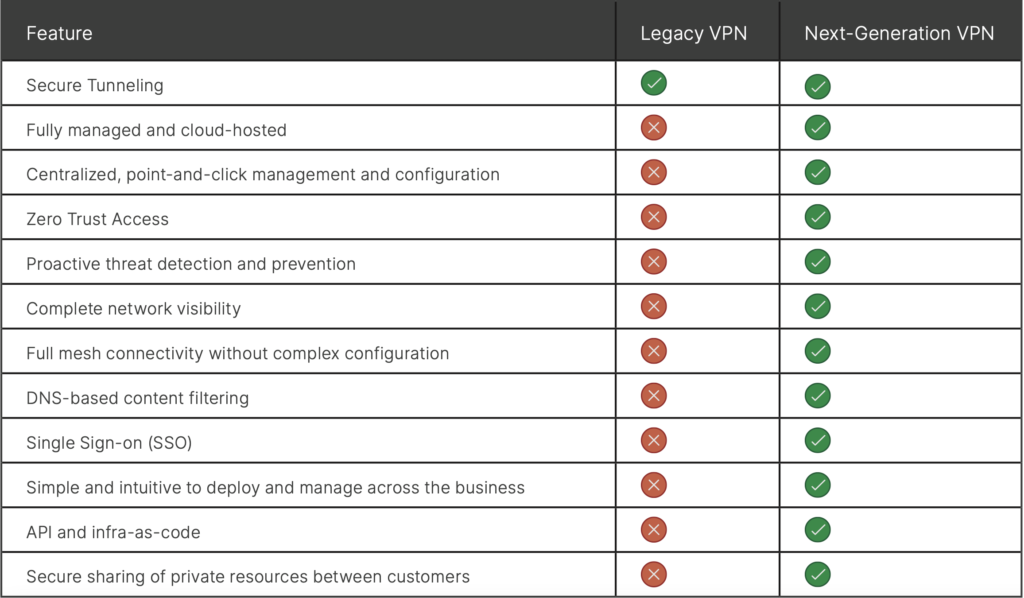
VPN: An Efficient, Reliable Network Security Solution
VPN service from a reputable VPN provider is an essential aspect of your network security. Our next-gen VPN, CloudConnexa, allows organizations to truly safeguard their assets in a dynamic, cost effective, and scalable way. CloudConnexa takes the complexity and high cost out of building and managing a secure private network. This elegant, cloud-based solution allows you to quickly and easily connect private networks, devices, and servers to build a secure, virtualized, modern internet.