SOX Cybersecurity Compliance
Implementing Security Controls for Sarbanes-Oxley Compliance Requirements
The Sarbanes-Oxley Act (SOX) is a federal act passed in 2002 following financial scandals at Enron Corp., Tyco International, and WorldCom. The fallout from these events led Congress to strengthen disclosure and auditing requirements for public companies to restore investor confidence in U.S. capital markets. The SOX Act is a lengthy document, but the following are key things companies must do to comply:
- Provide periodic financial statements that independent auditors audit.
- Promptly report any material changes to the company’s financial situation to the public.
- Have in place adequate internal controls to detect and prevent fraud and ensure the company’s financial information integrity. This typically includes financial-type controls and controls related to the company’s IT system.
- Provide an annual management assessment of internal controls. Independent auditors must sign off on internal control reports.
Financial reporting was the primary concern when the bill was passed, but financial data and data security were also considered. Now, 20 years later, the role of technology is much more significant, and SOX cybersecurity compliance is a primary concern for companies that must meet SOX requirements. According to the FBI Internet Crime Report for 2020, $4.2B in losses were reported in 2020 (up from $1.4B in 2017), and Gartner Hot Spots lists cyber vulnerabilities as one of the most critical risk areas for auditors to address.
According to the FBI Internet Crime Report for 2020, $4.2B in losses were reported in 2020.
Recommended Reference: The Sarbanes-Oxley Act of 2002 is available on the Public Company Accountability Oversight Board (PCAOB) site.
Steps to Data Protection and SOX Compliance
The primary role of SOX cybersecurity compliance is creating and implementing reliable internal control processes for information technology (IT) infrastructure and applications containing financial data in financial reports. The goal is to have the information and reports prepared and available as quickly as possible in the event of a security breach.
The primary role of SOX cybersecurity compliance is creation and implementation of reliable internal control processes.
In 2018 SOX cybersecurity compliance gained more attention due to guidance from the Securities and Exchange Commission (SEC). The SEC guidance called for the highest levels of a company's leadership to expand their corporate governance to:
- “... the importance of maintaining comprehensive policies and procedures related to cybersecurity risks and incidents. Companies are required to establish and maintain appropriate and effective disclosure controls and procedures that enable them to make accurate and timely disclosures of material events, including those related to cybersecurity. Such robust disclosure controls and procedures assist companies in satisfying their disclosure obligations under the federal securities laws.”
- “... companies and their directors, officers, and other corporate insiders of the applicable insider trading prohibitions under the general antifraud provisions of the federal securities laws and also of their obligation to refrain from making selective disclosures of material nonpublic information about cybersecurity risks or incidents.”
The SEC guidance called for the highest levels of a company's leadership to expand its corporate governance.
This shift requires IT staff to go beyond their usual areas of expertise and engage with financial teams for comprehensive risk assessment and incident response planning. Two sections of SOX are specifically related to cybersecurity and protecting sensitive data:
- Section 302 — Requires companies to put systems in place that prevent data tampering by both unauthorized internal personnel and external forces (e.g., malware, hackers).
- Section 404 — Requires an organization’s security system to safeguard the handling of data that should be independently verified and to make all data available to auditors, including financial statements and any potential security breaches.
Good to Know: In 2013, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) released revisions and updates to the Internal Control - Integrated Framework. The new framework is meant to increase its relevance in the complex global business environment so organizations worldwide can create, deploy, and refine internal control.
So, how can internal stakeholders develop cybersecurity risk management strategies that reduce the risk of cyberattacks and meet SOX requirements? Document and data collaboration platform Workiva recommends the following as best practices for SOX controls and compliance:
- Focus on risk: The primary motivation for cybercrime is financial gain, so a company’s risk from cyber threats is always evolving. Mitigate risk with regularly scheduled audits, mapping, and flowcharts to fully understand processes and associated risks.
- Streamline systems: Integration of documentation, testing, and controls saves time and money while generating accurate, reliable information for auditors.
- Prioritize prevention: As a rule, educating employees about cybersecurity best practices should be ongoing. Verifying, in writing with signatures, that control and process owners are performing required duties keeps people honest and establishes a paper trail in the event of fraud.
- Monitor red flags: Appropriately designed controls make it easier to detect fraud or material misstatements in financial disclosures. Periodic assessments of key processes can help identify gaps that could lead to a security or data breach.
- Document: If an audit reveals weaknesses, take immediate action and document the actions taken. Documentation is an essential element of control efforts.
In the News: In August 2020, the SEC charged Howard Hideshima, CFO of Super Micro Computer, Inc., with knowingly circumventing internal accounting controls (among other things). Hideshima was ordered to pay disgorgement and prejudgment interest totaling more than $300,000 and a $50,000 penalty.
Anatomy of a SOX Audit
In the event of a SOX audit with external auditors, your company will be assessed for compliance with the following five sections:
- Section 302: Corporate Responsibility of Financial Records
- Section 401: Disclosures in Periodic Reports
- Section 404: Management Assessment of Internal Controls
- Section 409: Disclosures of Changes to Financial Conditions or Operations
- Section 802: Penalties for Altering Documents
Good to Know: Some Sarbanes-Oxley provisions — intentionally destroying, altering, or falsifying documents with the intention of impeding or influencing a federal agency investigation or a federal bankruptcy proceeding, whistleblower protection — apply to private companies. Criminal penalties include fines as well as imprisonment.
Make CloudConnexa Part of Your Company's Internal Control Structure
SOX compliance is costly in terms of time and money, but non-compliance will cost a company even more. Punishment beyond fines against individuals and the organization can include removal from public stock exchange listings and having D&O insurance policies canceled. One way to streamline SOX compliance audits and cybersecurity is to combine CloudConnexa and the NIST Cybersecurity Framework.
CloudConnexa is a critical component of a layered security approach that provides DNS-based content filtering to mitigate malware, phishing, and other attack vectors. This virtualized networking solution includes firewall capabilities, enterprise-grade encryption, IDS/IPS, access controls, and user authentication.
SOX compliance is costly in terms of time and money, but non-compliance will cost a company even more.
Cyber Shield, a built-in feature of CloudConnexa, provides Traffic Reporting with detailed statistics on traffic threats (malware, intrusion, DOS) and the device of origin. Network administrators can use detailed DNS Filter Reporting (exportable to CSV) on observed and blocked domain name queries from users for risk assessment and refining security policies.
The NIST Cybersecurity Framework outlines five straightforward steps firms can take to protect their networks and government agencies using their services from cybercrime:
- Identify
- Protect
- Detect
- Respond
- Recover
This diagram explains what each step involves:
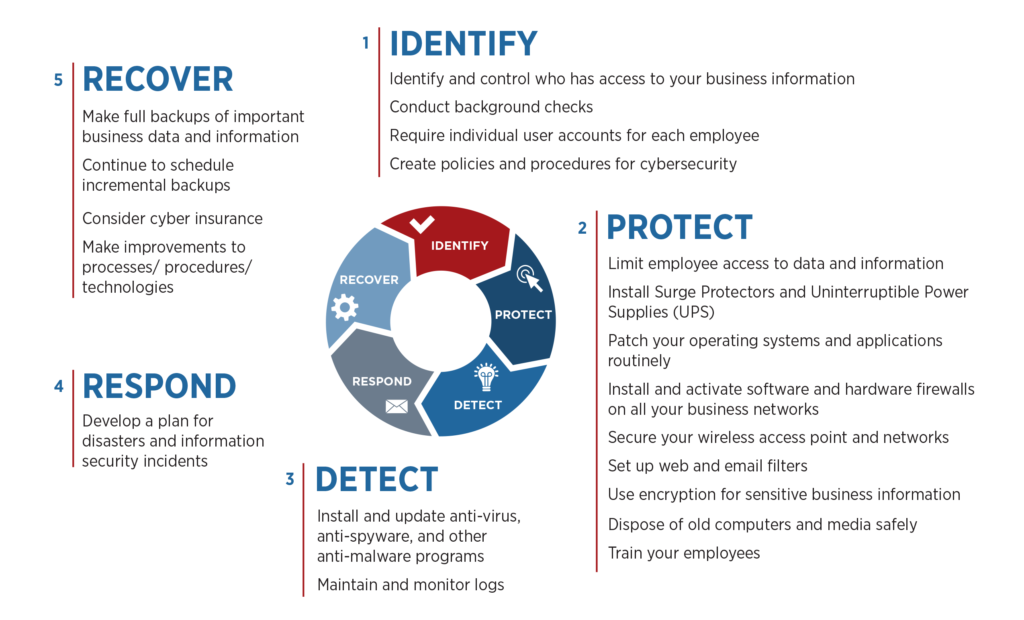
The Framework's guidance, based on existing standards, guidelines, and practices for managing and reducing cybersecurity risk, combined with an CloudConnexa secure, virtualized network, allows organizations to protect their data while enabling secure connectivity between employees, devices, and networks.
Good to Know: System and Organization Controls (SOC) is a suite of service offerings CPAs may provide in connection with system-level controls of a service organization or entity-level controls of other organizations. SOC certification may be viewed as a prerequisite for service providers to work with high-profile or tier-one organizations.
See how OpenVPN can help your company's SOX cybersecurity compliance efforts. Get started today with three free connections.


