Advantages of using Google Cloud Identity for authentication of both SaaS applications and VPN access
Use of a Virtual Private Network (VPN) is a great security tool to extend your private network to remote users and locations while at the same time ensuring that only authorized users can access the private network. However, even the best security safeguards will come to naught if the user identities used to authenticate VPN access are not properly maintained. The overall foundation of access security relies on the proper management of user identities. As an example, security could be compromised if the identity record and associated access rights of ex-employees are not promptly purged, or not removed from all directories.
To prevent the proliferation of directory services, and to simplify identity management processes, many companies use a single system of record and a unified directory service. This directory service is accessed by various systems and applications that each verify user identity, and a VPN Server is one such system. OpenVPN Access Server can authenticate users against any external directory that supports RADIUS and LDAP. OpenVPN Access Server v2.5.3 and later now introduces support for Google Cloud’s secure LDAP service available soon in Cloud Identity and G Suite.
With the reliance of enterprises on popular SaaS applications for essential business functions, use of single sign-on (SSO), identity federation, and the growth of Identity as a Service (IDaaS) offerings, companies are rethinking their identity management architecture. Many who choose IDaaS offerings find that identity federation protocols like OpenID and SAML are not supported by legacy applications or systems, and therefore may be forced to maintain a legacy internal directory. Google Cloud's adoption of secure LDAP for its Cloud Identity service has now made it possible to use Cloud Identity for user authentication by traditional network systems like VPN servers that have not yet adopted SAML or OpenID.
Identity management becomes simpler by using Cloud Identity as the directory service for both SaaS applications, as well as for VPN access to on-premises or cloud-hosted systems and applications. Having a single directory service for both application and network access provides an opportunity to better coordinate application and network access controls for a specific user or user group while reducing operational complexity.
Mapping Groups attribute value configured in Cloud Identity to the network access permissions for that group provides a powerful benefit in simplifying administration of access rights. Now, network access privileges and corresponding application access privilege can be easily mapped to an employee’s organizational departments and roles in Cloud Identity.
For example, the top-half of the illustration below shows Access Server deployed in various Cloud IaaS providers and all instances of Access Server are using Cloud Identity for authentication and authorization. The Access Servers have been configured with a group called ‘IT Admin’ which allows SSH. This allows any employee identity present in Cloud Identity that is a member of ‘IT Admin’ group to VPN into any of the private networks and use SSH.
A large enterprise employs a variety of security solutions meant to counter and provide coverage against common threat vectors, conform with compliance needs, and enforce corporate policies. Some enterprises may even have deployed an on-premises cloud access security broker (CASB) solution. To leverage all these security assets and controls, some companies do not want their employees bypassing corporate controls to access SaaS applications directly. To block direct access, security administrators configure SaaS applications to allow access to their employees only when the request originates from their corporate network IP addresses.
As shown in the lower half of the above illustration, having remote employees use VPN to connect to their corporate network and then access SaaS application fulfills the needs of corporate security. In addition, the use of certificates for mutual authentication, and end-to-end data encryption adds further security benefits to use of VPN for accessing SaaS applications. Now, with the use of Cloud Identity a further benefit is added: the convenience of using the same username/password to authenticate for VPN access as well as SaaS applications.
Using Cloud Identity for Authentication
OpenVPN Access Server v2.5.3 and later supports secure LDAP and has been tested to work with Cloud Identity. Specific configuration instructions can be found on our website. The secure LDAP capability of Cloud Identity is soon to be released (learn more here).
Using Cloud Identity Groups for Network Access Control
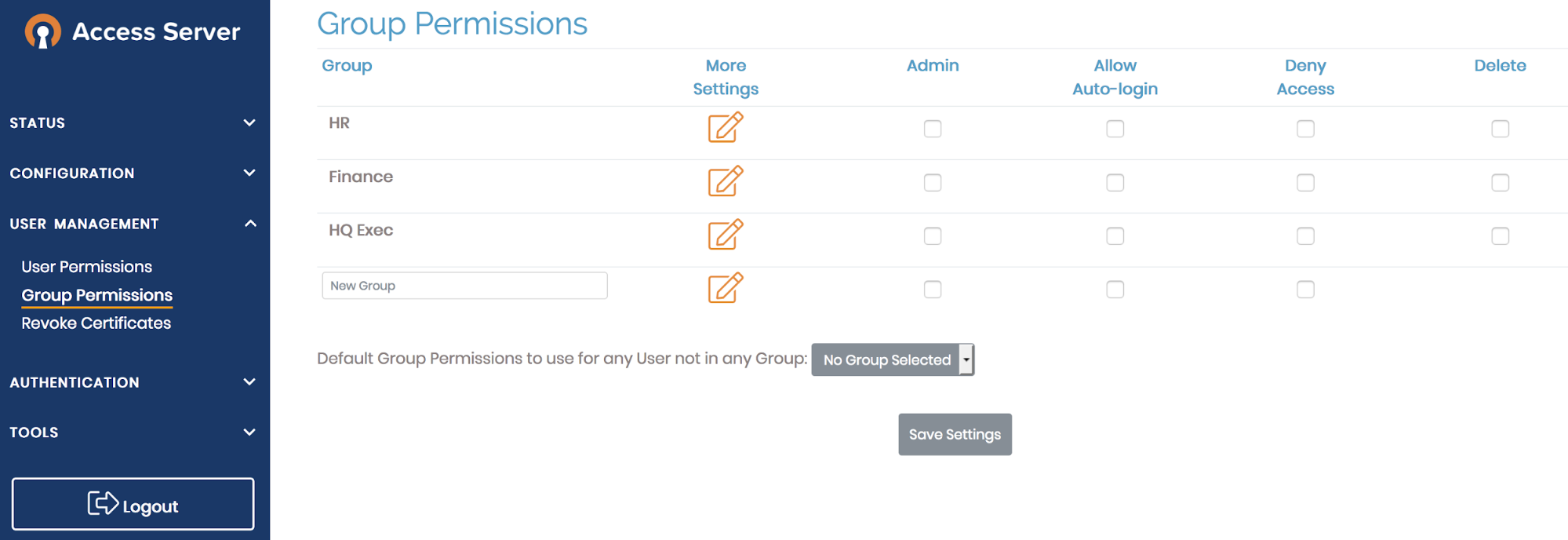
As shown in the illustration below, Access Server provides for configuration of Groups. Access controls can be configured for these groups with fine granularity down to an individual IP address and port number.
One can configure groups in Access Server corresponding to those stored in Cloud Identity and, on user authentication, enforce access controls for the user based on that user’s group membership. This mapping is done by using a script on Access Server. Instructions to setup the script are available at our website and our support staff is, as always, ready to aid our customers.
Advantages of using Cloud Identity with OpenVPN Access Server
- Leveraging the same directory service for authenticating SaaS applications and authenticating network access provides an opportunity to better coordinate application and network access controls for a specific user or user group.
- Convenience of using the same username and password for accessing SaaS applications and VPN. VPN users do not need to remember different passwords. Additional security can be added by the use of Google Authenticator that is integrated into Access Server.
- Employee access to authorized services can be enforced at the network-level by mapping the Group information stored in Cloud Identity to configured access controls in Access Server.
- Reduction in operational complexity and need for legacy directories.
About OpenVPN Inc.
OpenVPN is the provider of next-generation secure and scalable communication services. Our award-winning open source VPN protocol has emerged to establish itself as a de-facto standard in the open source networking space with over 50 million downloads since inception.
We have integrated a suite of leading-edge networking and software technologies to deliver virtual network software that provides secure, reliable, and scalable communication services, not only fulfilling the requirements of the traditional virtual private network (VPN) market, but also addressing the future demands of SDN – Software Defined Network, Remote Access to private networks, tunneling to UTM – Unified Threat Management Firewall Clouds/Gateways, tunneling to DDOS Clouds/Gateways to protect against malicious attacks.
OpenVPN is the author of open source Virtual Private Network (OpenVPN) software and the provider of multi-platform OpenVPN applications across all OS platforms ranging from Windows, MAC, Linux, Android, and iOS and end to end OpenVPN Server on Cloud, OpenVPN Server as Virtual Appliance, OpenVPN Server as Software Packages, and OpenVPN as a Service (Private Tunnel), addressing the market demands for Remote Secure Access, Access Control, and Cyber Security targeting businesses of all size across the globe.