A Better Alternative to IP Whitelisting
Every single organization needs to secure network resources, and control who accesses resources. But as organizations grow and need to provide access for a greater number of users, the more vigilant they need to be with access control. One common method that smaller companies use for access control is IP whitelisting.
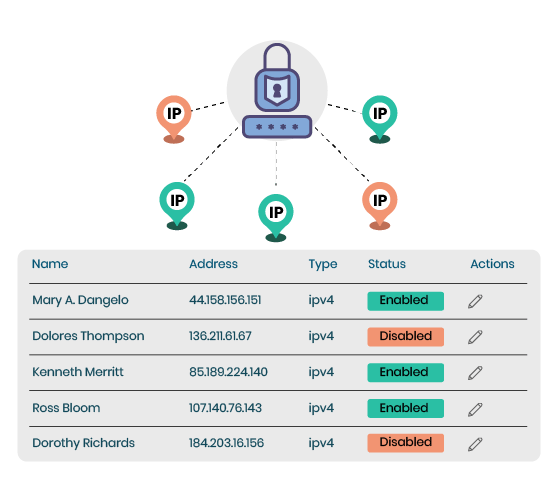
IP whitelisting is a security measure that permits access to specific IP addresses while blocking all others. It's a way of ensuring that only trusted sources can access your network or data. This is particularly useful for businesses that want to secure their information on servers. However, it's important to note that this method requires users to have static IP addresses, which are IP addresses that do not change.
However, while IP whitelisting can be a great security feature, it isn’t always practical for larger organizations. Whitelisting when you have a lot of users is very time consuming, and often ends up being a never-ending task to manually maintain.
IP Whitelisting Limitations
The biggest roadblock for IP Whitelisting is the types of IP address an authorized user might have. An internet-capable device will have one of two different kinds of IP addresses:
1. A static IP address, which means the address doesn’t change, or
2. a dynamic IP address, which means the address can and will change.
The majority of users will have dynamic IP addresses because that is how most internet service providers assign IPs. A lot of dynamic addresses are renumbered every 24 hours or some multiple of 24 hours. Outages can also lead to an IP address change.
The problem with this is that each time a dynamic IP address changes, your system administrator needs to add the new IP address to the whitelist. Then you have to keep track of which IP addresses are for which people. When the IP address is changed or a user is no longer allowed access, you need to delete the old IP address from the whitelist. Removing access is just as important to good access control as granting it.
While this is certainly doable for smaller organizations, you can probably imagine how it could become unsustainable for larger companies, or businesses that require a lot of different remote connections. To maintain IP whitelists, larger organizations might actually have to have a dedicated employee (or team of employees) on hand just for adding, managing, and removing IP addresses from the whitelist.
However, there are different solutions available for organizations that can no longer sustain IP whitelisting — and companies of all sizes are shedding their cumbersome IP whitelists in favor of more manageable access control solutions.
A Better Way to Manage Network Access
Let’s look at a company that provides a cloud-based platform for geospatial analytics. They are a remote-friendly company and hire the top talent from all across the United States. Because their teams are all geographically distributed, everyone has to be able to access company resources from their own homes and remote workplaces.
For a while the company utilized IP whitelisting to ensure only authorized users were accessing the network — but as time went on and the workforce grew substantially, the existing process of whitelisting IP addresses was no longer sustainable. There were just too many employees with dynamic IP addresses, and it was too difficult to stay on top of it. They needed a new solution for the entire remote workforce, which could allow simplified access control and management, without wasting time and resources.
The company chose OpenVPN Access Server as the solution of choice to provide remote employees with secure access to private company resources. The company then used the easy-to-install Amazon Machine Image to deploy Access Server within the Amazon Web Services Virtual Private Cloud that housed the other internal servers.
To authenticate the employees, they interfaced OpenVPN Access Server with their identity directory using RADIUS, and they implemented multi-factor authentication (MFA) by connecting to their MFA provider over RADIUS.
With the Access Server solution in place, employees access their applications securely from office or home — and the security administrators no longer need to manage cumbersome IP whitelists. By investing in OpenVPN Access Server, the company provides a secure remote access solution for its employees, with simple, effective management tools.
Network Access and OpenVPN
When it comes to simplifying your remote access capabilities, a VPN can help you out in two different ways.
OPTION 1: Reduce Whitelist Maintenance
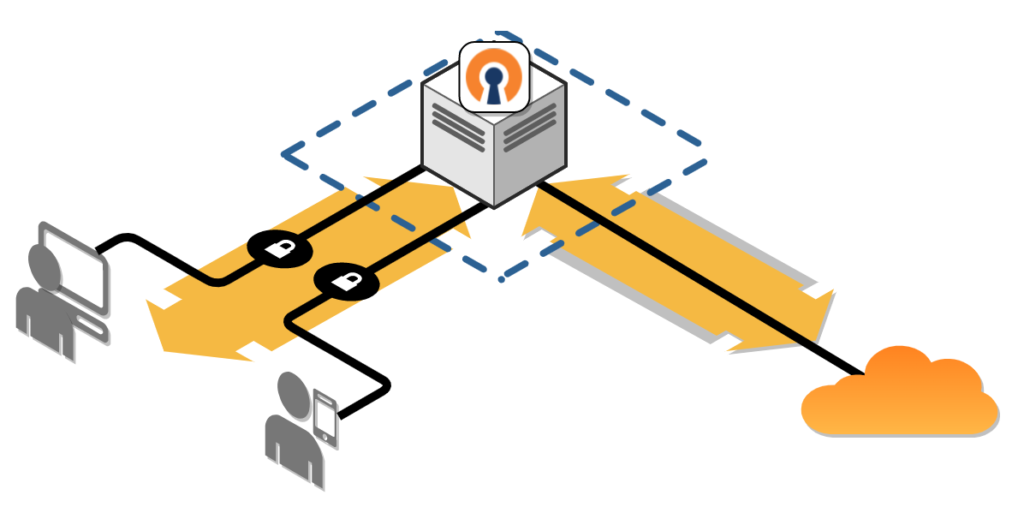
To avoid constantly changing the whitelist due to dynamic IP address changes, you can have the users connect to a VPN server first. This will act as an internet gateway and mask the IP address of the users with its public IP address. All users will appear to have the same IP address and your whitelist only needs to have the IP address of the VPN server. Only users that need access are given VPN accounts. Any connected VPN client will have secure access.
For more ways to configure and use OpenVPN Access Server, check out our documentation.
OPTION 2: Eliminate Whitelists Entirely
If your organization has outgrown IP whitelisting, or you are simply looking for a more manageable solution, OpenVPN Access Server can help with that too. With Access Server, you protect your valuable data by granting access through the VPN. Clients connect with the server, validating the connection both ways, and an insecure internet connection becomes an encrypted tunnel over the public internet. Using OpenVPN Access Server, you can easily protect your data communications, secure IoT resources, and provide encrypted remote access to on-premise, hybrid, and public cloud resources.
To get OpenVPN Access Server on AWS, start by purchasing a license.
For instructions on using RADIUS for authentication, check out our guide.
For further resources, take a look at Securing Remote Access with a VPN.