Ingress and Egress and VPNs
2020 came with a lot of changes to daily life. Wearing masks at hair salons and barbershops. Social distancing while dining outside at restaurants. Grocery stores have implemented traffic patterns to allow people to move between aisles. Doors that were previously two-way have been changed to one-way to allow folks to ingress and egress while limiting human contact. This concept of ingress and egress traffic has also come into the spotlight regarding digital traffic and effectively managing that traffic flow — as more and more employees work from home, digital traffic patterns have changed right along with physical patterns.
Ingress = something from outside coming in
Egress = something from inside going out
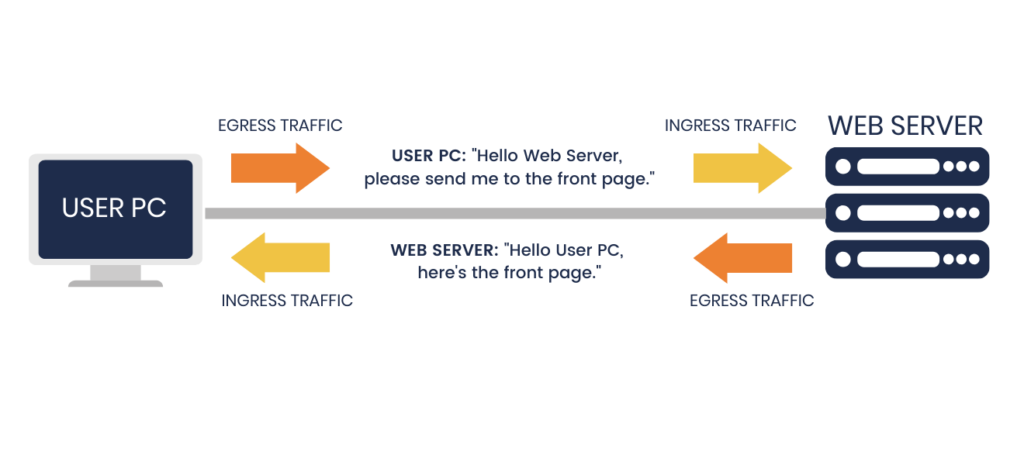
Whenever you open a web browser and access a website, your computer first sends out a request to the website server to send you the correct page, that’s egress traffic. And then the website server sends you the requested webpage, and that’s ingress traffic. To you, your request is the egress, and the response you receive is ingress. From the website server point of view, it’s exactly the reverse.
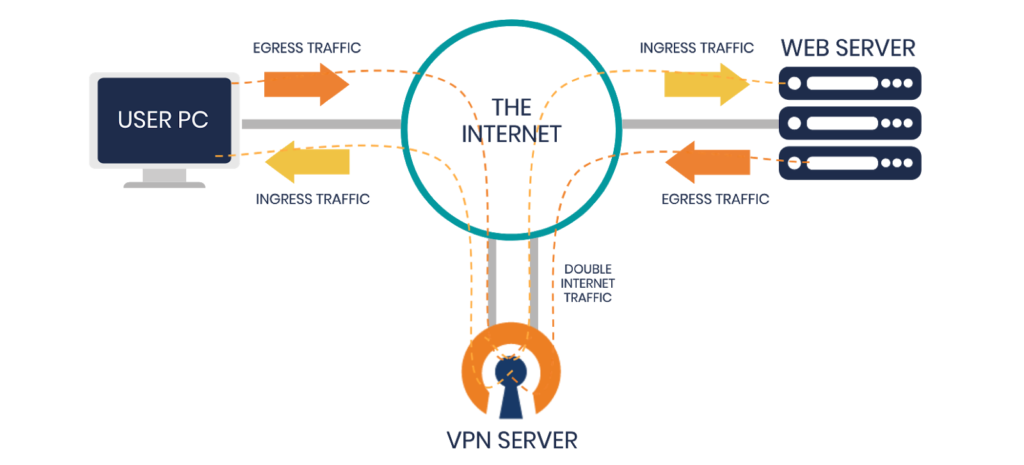
When you use a VPN, there is a server in the middle. If you are connected to a VPN server, your request will go through the VPN tunnel to the VPN server, and the VPN server will then pass it on to the server you want to reach. A response back follows the reverse path.
There is an efficient path if the servers and resources you want to reach from your VPN client are in the same private network or very close to the VPN server. But there is a less efficient path when traffic comes in from the internet, and then gets sent back out to the internet. This happens when the VPN server instructs the VPN client to send all internet-directed traffic through the VPN tunnel. When a VPN client tries to access an internet resource, all that traffic goes through the VPN server’s internet connection twice.
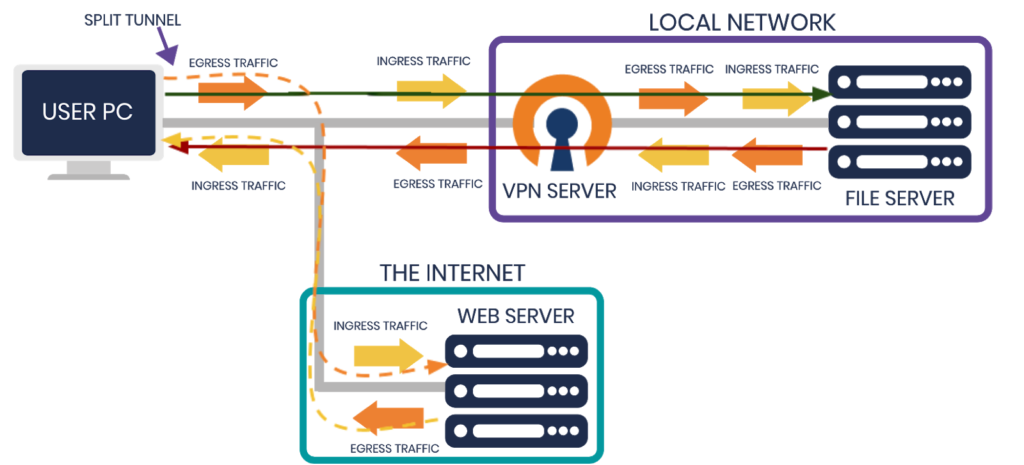
This is not ideal if your users do not need to go through the VPN server to reach the desired resources. In almost all cases, the VPN server is in a private network. The resources you want to reach are there, so it’s local traffic for the VPN server. However, many people redirect internet traffic through the VPN server even when it is not necessary. Wouldn’t it be better to skip the VPN server routing step for situations where traffic doesn’t need to take the detour? Yes. That’s where a split-tunnel setup comes in.
Split-Tunnel Redirection
A lot of companies realize their old configuration isn’t scalable with the high numbers of remote workers they now have. They are experiencing overburdened remote connections and network latency issues.
One way to address these issues is to set up split-tunneling on OpenVPN Access Server. The OpenVPN protocol has a configuration option called redirect-gateway. When turned off, this creates a split-tunnel. In this configuration, the only traffic that goes through the VPN tunnel is the traffic you want to send through. And your end user’s Internet egress point will remain unchanged, whether you’re connected to the VPN server or not. For users with OpenVPN Access Server, all of this can be easily configured with the admin web interface.
What Necessitates Full-Tunneling?
Two good use cases for full-tunnel VPN connections are both for improved security; one case for better protection on the internet, the other for safeguarding access to cloud resources.
For the first case, a company wants to provide better security for its users on the public Internet. They want to use an intrusion prevention system. This is basically a proxy server, and all of the traffic goes through the proxy before reaching the internet. From there, they have threat management solutions in place to filter through possible harmful websites, objectionable content, etc.
The second case is for companies to improve secure access to their cloud resources. They have some of their resources on public IPs. They only firewall it off to the VPN IP. This means that only users with allowed IP addresses are granted access to cloud resources. Once they’ve connected to the VPN, which assigns them an internal IP address, they can then access the resource hosted on the public Internet.
Do You Need Full-Tunneling?
Many companies use a full-tunnel setup with their VPN solutions when they don’t really need it. This means all of their end-users at home and all of their internet traffic must go through their VPN server. In the past, this wasn’t an issue for them, depending on the number of active VPN connections. However, as they rushed to connect many employees from home, they experienced a strain on their resources. This uses up a substantial amount of bandwidth and slows down their VPN. By overloading it with the sudden increase in traffic, it slowed down the users and their ability to use the internet.
What’s the fix? Many companies have chosen to split-tunnel, so the only VPN traffic the VPN server deals with is traffic for resources that are present locally. When their users connecting at home want to browse a news site, it goes through their own, residential ISPs, freeing up the company’s bandwidth to focus on routing traffic to the business network resources.
Split-Tunneling With Access Server
By setting up split-tunneling with Access Server, you can:
- Avoid overwhelming your internet connection
- Allow access to specific local resources through VPN
- Reduce the amount of strain on your VPN server
- Provide better bandwidth for employees
OpenVPN Access Server has a web-based admin interface where you can simply turn on or off the option for redirecting VPN client traffic through the VPN server. For detailed instructions on setting this up, see our resource: Split-Tunneling with OpenVPN Access Server