Third Party Access Control Are you in control?
Are you in control of your office building? Of your resources? Of your own network?
Do you have the control to determine who — or what — has access to your resources?
Access control, simply put, is all about controlling who gets access to what. It is one of the most fundamental security practices, and is crucial to protecting your organization. Without proper access control, the right people might not have enough access to get the job done…or the wrong people might have too much access. Neither is good for business.
There are two different kinds of access control: physical and logical.
You probably already have physical access control in place — doors that only some people have keys to, buildings that only certain employees are authorized to access. But what about your logical access control? How are you controlling access to computer networks, system files, and data? Is the control in your hands?
Chances are your network is being accessed by more users than just your full-time employees — access might be needed for guests, contractors, or business partners. But an “all or nothing” approach to network access doesn’t make sense for a lot of businesses — your users don’t all need equal levels of access.
Business partners don’t need (and shouldn’t be given) access to the same information and resources as employees, and guests don’t need the same level of access as your contractors.
And to take it a step further: not all employees need access to all the same resources. Your marketing team probably doesn’t need access to supply chain management tools, and your HR team doesn’t need access to the system infrastructure. Your administrator will need complete access, but that’s about it. Everyone else should be limited in what they can get to.
The general rule of thumb should be: only give people access to what they need. The fewer people you have accessing different resources, the smaller your margin of error becomes.
That’s why you need access control — and OpenVPN Access Server can provide exactly that.
How it Works
Access control systems authenticate and authorize users by evaluating the required credentials — verifying that the person or application is who or what it claims to be, and authorizing the appropriate access levels and permissions associated with the username or IP address. Users are then enabled to connect to the authorized network resources.
Our VPN, Access Server, can be configured to provide exactly this control, using LDAP to access Active Directory for authentication.
What is LDAP?
LDAP stands for “Lightweight Directory Access Protocol” and is the standard for storing organizational information. It acts as a phone book of sorts, and allows for the network to share information about users, systems, networks, services, and applications — and it can be used to determine how much network access a particular user has. LDAP is mostly used by medium-to-large organizations, and is the standard for communicating record-based, directory-like data between programs. But it is not limited to contact information — or even information about employees. LDAP can be used to look up encryption certificates, services on a network, and provide SSO (single sign-on), which is when a person uses a single ID and password to gain access to multiple systems. The most common method of utilizing LDAP is through Active Directory.
What is Active Directory?
Active Directory (AD) is Microsoft’s version of LDAP, developed for the Windows domain networks. AD authenticates and authorizes all users and computers in a Windows network, and assigns and enforces security policies. Many of our customers that ask for LDAP are actually planning on using Access Server with Active Directory.
Use Case
Consider a home security company — they use third-party contractors to install security systems in their customers homes. The company wants their contractors to have access to in-house workforce management software...without necessarily giving them access to 100% of the company resources in the network.
However, they didn’t want to limit the resources available to full-time employees.
The company came up with a solution: A VPN. The company installed OpenVPN Access Server at their datacenter, and Connect Client software in each of the contractor’s work tablets. Access Server used LDAP to access the company Active Directory for authentication, and to differentiate contractors from employees. Their server was configured so that contractors could only gain access to email and workforce management servers — whereas employees were granted greater network access.
Both the contractors and employees can now use the VPN to access internal services from anywhere — but the company is in control of who has access to what. Providing internal access using a VPN does not need to mean that services on the entire internal network are accessible for use. Using access control based on the VPN user's group membership, the company was able to restrict contractor's access to only the services that they are authorized to use.
Configuring Access Server to Allow LDAP Authentication
OpenVPN Access Server can be configured to allow LDAP Active Directory authentication: from there you can apply specific settings to your Access Server users to determine who can log on, and what information they have access to. By configuring Access Server to allow LDAP, you are taking the control of your network into your owns hands — which is exactly where it should be.
You can configure your Windows Server 2016 running an Active Directory, so that OpenVPN Access Server can connect to it and use the objects in the directory for authentication. Through this, you can:
- enable SSL to ensure a secure link between Access Server and the Active Directory server
- configure rules for different Active Directory groups (for example: only allow one AD group to use the VPN while other groups are blocked)
- allow only specific Active Directory users to log in
- apply specific settings (like special access) to specific users and groups on Active Directory
To configure your Windows Server 2016 running an Active Directory:
- Log on to the Admin UI as openvpn administrative user.
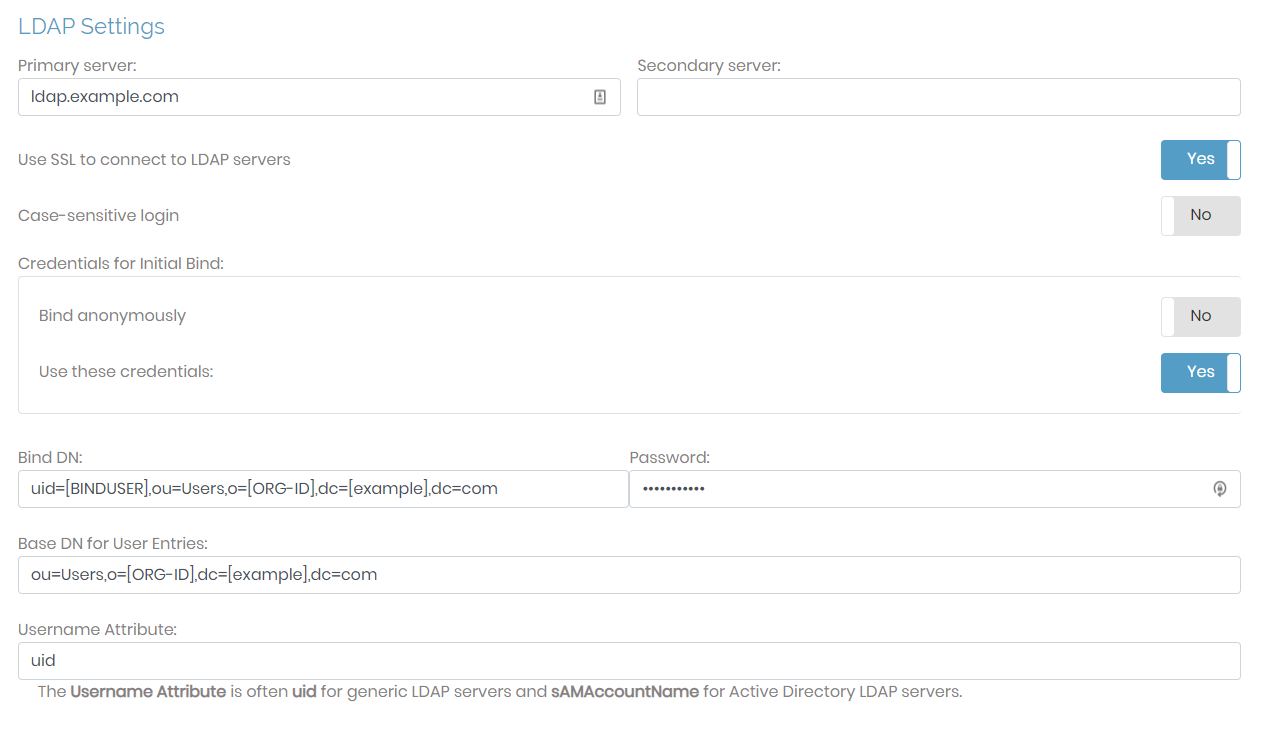
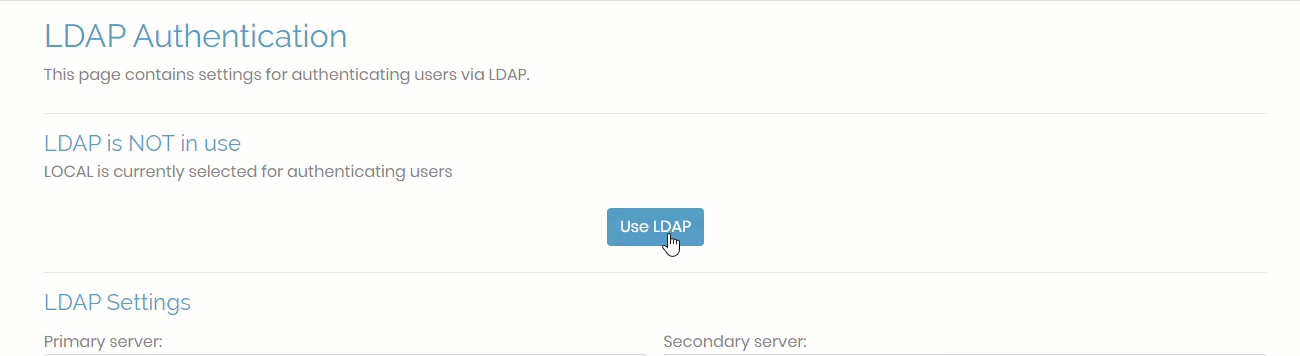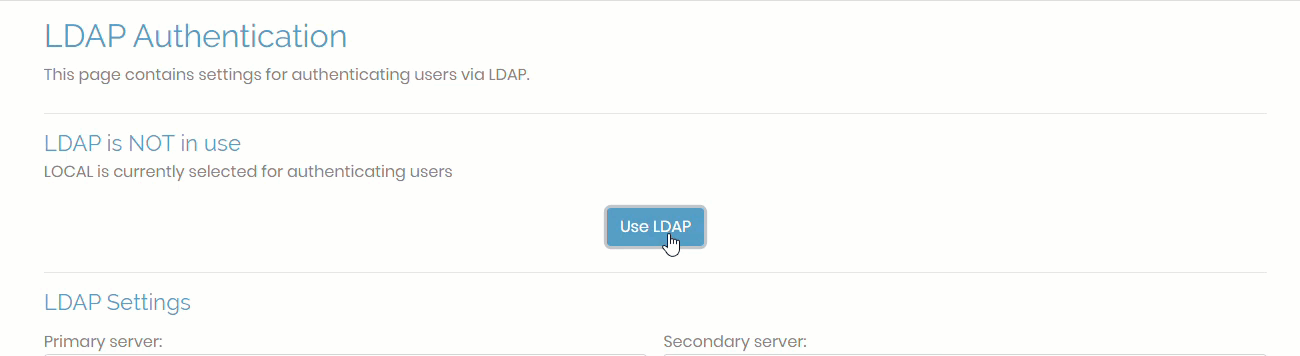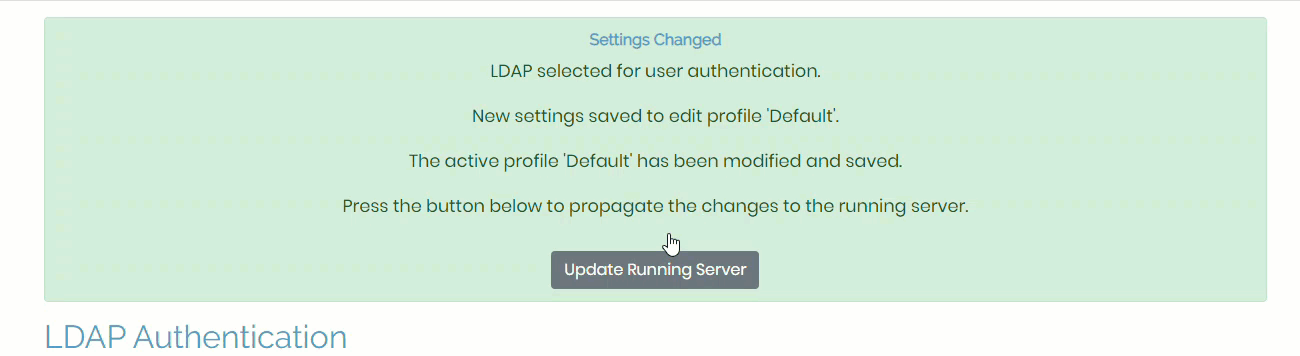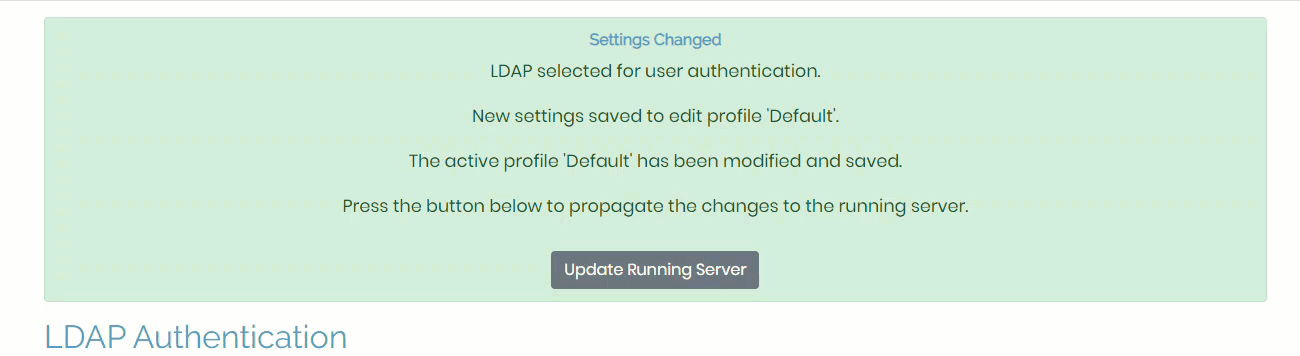
- Go to Authentication, LDAP, and set address of your server, bind DN, and base DN of your LDAP directory.
- Click save settings to store the changes. There’s no need to click Update Running Server yet.
- Scroll to the top and click on Use LDAP.
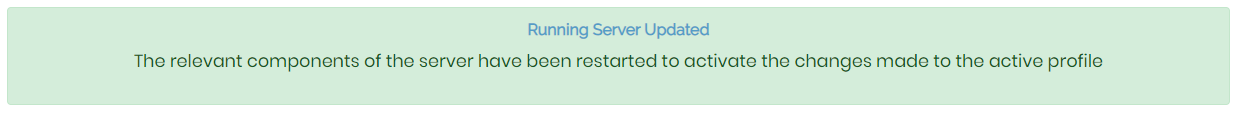
- This time make sure to click Update running servers to implement the changes.
For more detailed instructions, we offer a step-by-step guide that will walk you through the process. It will also show you how to apply specific settings to Access Server users; allow only specific users to log on; and set it so that only users from a particular group can log on.
In order to configure OpenVPN Access Server with Google Secure LDAP, you can also follow the instructions in this helpful Google Secure LDAP guide.