DNS Security: Your Key To Working Remotely
Say goodbye to “work from home” — and say hello to “work from wherever.”

Once upon a time, working from home was a privilege offered to a lucky few — or reserved for extenuating circumstances like bad weather or illness. Today, remote work is a prevalent offering, and most computer-centric roles have remote options. With how commonplace working from home has become, many believe the next logical step is to deregulate where employees are working and leave it up to their discretion. After all, if it doesn’t impact the quality of their work, why shouldn’t valued employees be allowed to choose?
In some cases, “work from wherever” is actually necessary to get jobs done. There are many job positions that require employees to travel to customer locations to help with installations, or to different networking and recruiting events. If those employees can’t “work from wherever,” they have to put their work on hold until they return to their home or the office. That kind of downtime isn’t practical. Employees must have reliable network access regardless of where they are working.
The issue with working from wherever that when employees are not at home or in the office, they likely only have access to public Wi-Fi options like the hotel guest Wi-Fi or the free airport connection. These connections are typically insecure and leave your employees vulnerable to DNS attacks.
DNS and Your Business
DNS, short for Domain Name System, is a naming system for internet-connected devices and resources. Hackers will often try to manipulate DNS to gain access to your data — and the most common way they do this is through DNS hijacking (also known as DNS poisoning and DNS redirection), which subverts a DNS query and incorrectly resolves it, redirecting unwitting users to malicious sites.
DNS hijacking is often used for two reasons:
- Pharming - a cyberattack that redirects traffic to malicious websites without the user’s knowledge.
- Phishing - when victims are tricked into revealing sensitive information to an illegitimate source.
DNS hijacking is a significant threat to the “work from wherever” crowd, and companies need to take precautions to ensure employees are just as safe using the coffee shop Wi-Fi as they would be logging in from the office.
Protecting the “Work From Wherever” Crowd
A quickly growing tech startup is headquartered on the West Coast of the United States, but has support centers all over the world. The support technicians regularly travel to client offices to help them install and troubleshoot their products. The techs are very reliant on SaaS tools, and often access the internet from airports, hotels, and restaurants. Because of how many employees work while traveling, the company has decided to extend “work from wherever” privileges to all computer-based employees.
Now it’s up to the head of IT and Networking at the company to ensure that every team member is equipped to work from any location. She is aware of all the risks associated with connecting to the internet from unsecured locations. Without proper protection, employees' use of DNS is vulnerable to hijacking, poisoning, and other attacks. He wants to find a solution that can provide strong DNS security — without having to install, manage, or maintain servers.
A professional contact introduced him to CloudConnexa because of it’s DNS security offerings and DNS based content filtering — as well as the fact the VPN is offered as a service so the head of IT won’t have to worry about handling servers. Now sensitive information is protected no matter where employees are working. The DNS-based content filtering allows the head of IT to block access to malicious websites that spread malware or are used for phishing attacks.
Enable DNS Protection
To get started, first complete the signup process. During the signup process, define a name for your VPN, such as yourbusiness.openvpn.cloud, as the web domain for the user portal. Once you are signed up and have created a user account, simply follow these steps to protect DNS traffic:
- Connect to CloudConnexa. On connection, DNS traffic now passes encrypted through the VPN to CloudConnexa’s DNS servers.
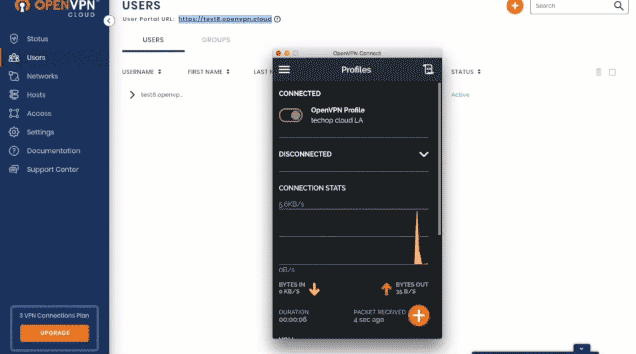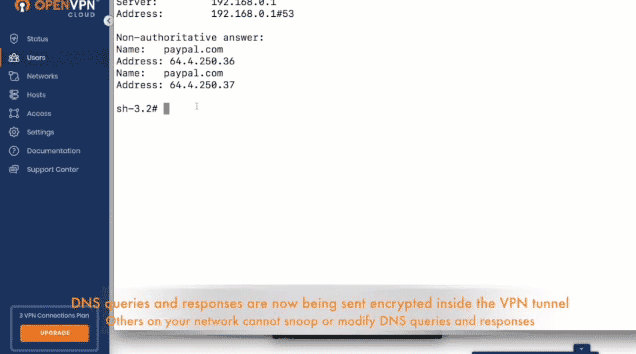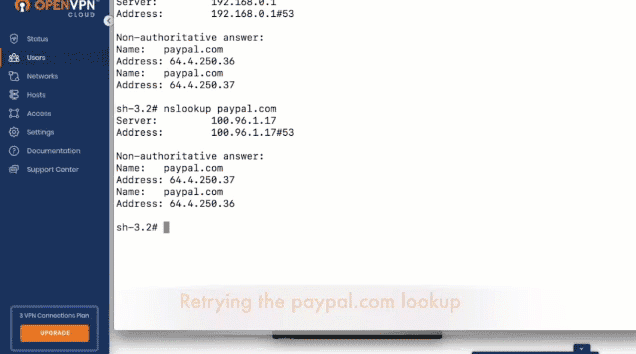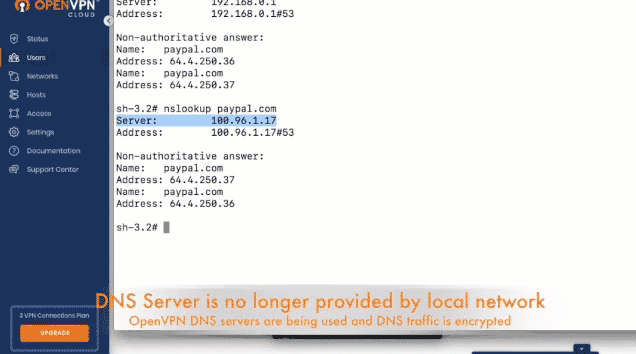
- To test, query the DNS with nslookup, a command-line tool to obtain domain name or IP address mapping. You'll see that the DNS server being used is no longer from the ISP.
- Add employees as users using their email addresses.
Get started for free with three connections. No credit card required.