Coronavirus Scams Are Infecting Devices Around the Globe
As the threat of coronavirus increases, businesses are sending employees to work from home, and students are shifting to online classes. But with the social distancing comes a new threat – cyber attacks.
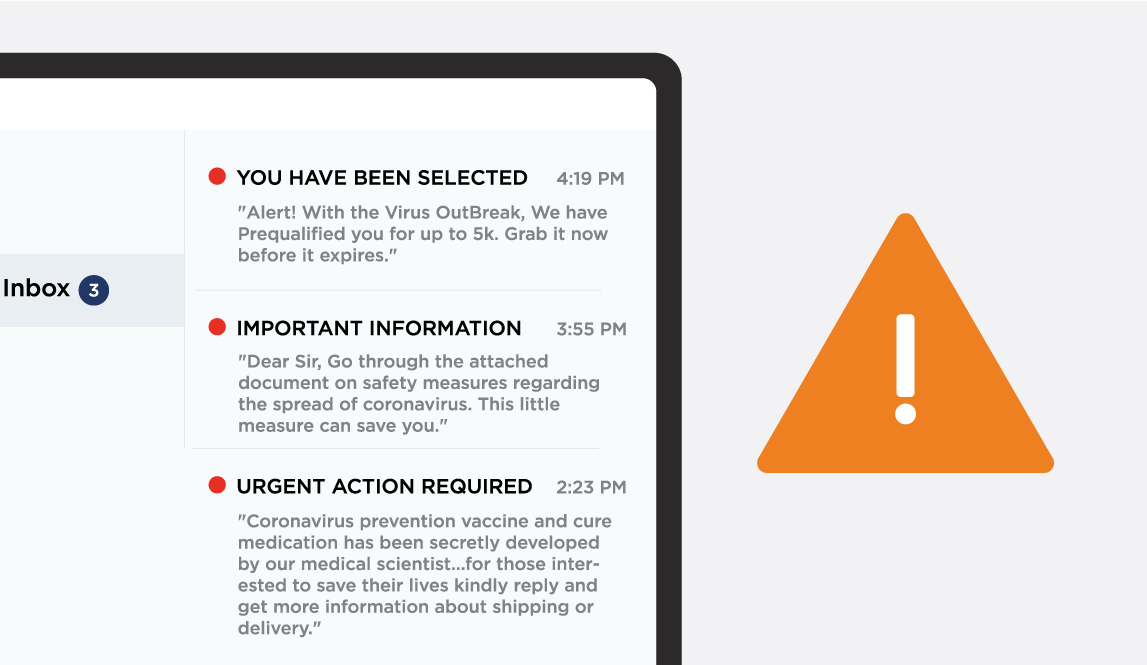
This graphic shows actual phishing emails and texts that people have received over the last few weeks. Phishing is a technique used by hackers to obtain sensitive information by disguising themselves as a trustworthy entity. Attackers often use hand-crafted emails or other types of messages with the intent to trick people into divulging personal or confidential data such as passwords and bank account information. And these newest phishing campaigns are exploiting the uncertainty and fear that many of us are currently experiencing.
In regards to COVID-19, hackers are relying on this tried-and-true method for infecting people's machines: manipulation and fear. In the last few days, researchers discovered a malware attack that preyed on the widespread panic and misinformation, sending emails that claimed to have preventative measures. The email states that there have been reports of coronavirus patients in a specific area of Japan and asks the reader to view the attached document. Once the user opens the attachment, it allows the scammer to place malware on the recipient's device.
Here are a few other examples of phishing attacks going around, some preying on people's goodwill and others impersonating the World Health Organization (WHO).
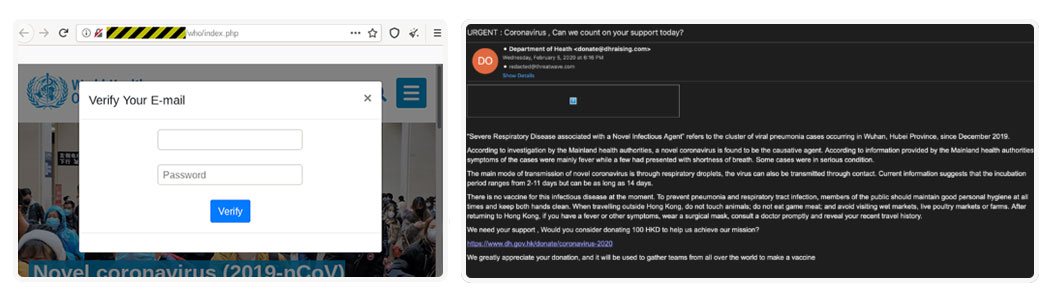
Recognizing COVID-19 Cyber Scams:
According to The World Health Organization, there are a few things they will never do or ask for. If you receive anything that contradicts their statement, you are dealing with a cyber attack. The WHO will:
- Never ask for your username or password to access safety information
- Never email attachments you didn't ask for
- Never ask you to visit a link outside of www.who.int
- Never charge money to apply for a job, register for a conference, or reserve a hotel
- Never conduct lotteries or offer prizes, grants, certificates, or funding through email.
Other organizations have also spoken out about these scams and explained how you could tell the real from the fake. You can check it out for yourself:
World Health Organization: "Beware of criminals pretending to be WHO"
Federal Trade Organization: "Coronavirus: Scammers follow the headlines"
Attorney General Mark Herring: "Attorney General Herring urges Virginians to Be Way of Coronavirus Related Scams"
Attorney General Brian Frosh: "Attorney General Fosh Warns Marylanders About Coronavirus Disease 2019 Scams"
David Emm: Principal Security Researcher at Kaspersky
Sherrod Degrippo: Senior Director of Threat Research and Detection at Proof Point
Matt Lourens: Security Engineering Manager at Check Point
Protect Yourself from COVID-19 Scams:
So what can you do to protect yourself?
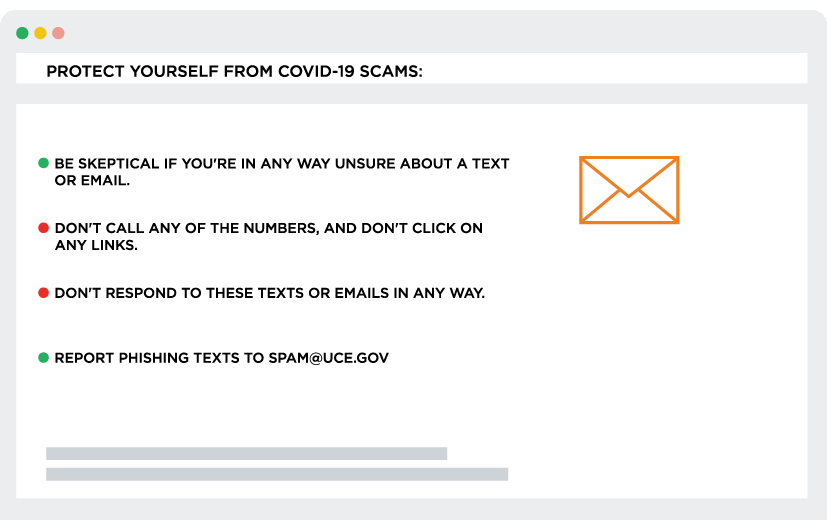
- Be skeptical if you're in any way unsure about a text or email. An example of one of these texts shows that hackers are playing on your emotions: it feels urgent, so you want to be in the know. This could be alerting you of new coronavirus cases in your neighborhood or town.
- Don't call any of the numbers, and don't click on any links. Hackers will also use tactics like "combosquatting" and "typosquatting" to create fake URLs that are easy to miss the typo—for example, adding "-security" onto a popular bank URL.
- Don't respond to these texts or emails in any way. In many cases, these emails will ask you to confirm your email and password inside of a form.
- Report phishing texts to spam@uce.gov and at FTC.gov/complaint – and to the organization being impersonated so they can let people know what to watch out for.
Businesses: Here's how to secure your remote workforce
Social engineering is another huge threat, especially in times of panic. Employees should be trained to recognize and avoid human error and deception. In social engineering attacks, the attacker will take advantage of the entire team being remote and having less communication. A call from another "employee" for help getting the phone number of a customer — may not be an actual employee. This scenario would likely not happen with a smaller company, but having processes and procedures in place to verify who someone is on the phone is essential.
Education will be the most significant factor in keeping your remote team secure. Your team should understand the dangers of logging in to the company's systems when using public wi-fi. Their home wi-fi should have a strong password as well.
Use a remotely accessed digital workspace, such as a VPN. A good business VPN will allow you to implement multi-factor authentication (MFA) to restrict unauthorized access to your network. Also, make sure to offer support and training in using a VPN. Employees should know to use it when they access emails, documents, and billing applications.
OpenVPN Access Server delivers an enterprise VPN solution for businesses of all sizes. Access Server allows organizations to protect data communications, implement access control and network segmentation, and provide encrypted remote access company resources. This is the perfect solution for businesses that have a new remotely accessed digital workspace.


