Anonymity, Privacy, and Security
CloudConnexa is now CloudConnexa® — learn more here.
Often, when I'm involved in discussions on various forums and discussion threads related to security and privacy on the Internet, I'm surprised how many people use the terms “anonymity,” “privacy,” and “security” interchangeably. These are actually three very different ideas, although they do have some overlapping aspects. Let's dive into the definition of each word to see how they differ.
Anonymity: your identity
The purpose of anonymity is to protect an identity from being revealed. There can be many valid reasons why that might be needed. Working in a hostile environment might make it difficult to raise awareness about the situation if you cannot do so anonymously; in many places the threat of repercussion is very real. This can play out on a small scale — in individual relationships — or on a much bigger scale. In countries with autocracies or dictatorships, for example, disagreeing with the government can be life-threatening — for both yourself and for people around you. In these cases, anonymity is essential.
Privacy: your data
Privacy is about who and what can read or access data in your possession. And it doesn't even need to be data, specifically; it can be someone observing your activity both online and in real life: where you are, when you're there, and what you’re doing. People may even pay attention to your physical whereabouts.
Privacy is important for our physical and emotional well-being. We all need breathing space where we know we can be ourselves, where we can think aloud freely without fear of repercussions or judgment.
Privacy is important for our physical and emotional well-being. We all need breathing space where we know we can be ourselves, where we can think aloud freely without fear of repercussions or judgment.
Privacy is considered so important that it is part of the Universal Declaration of Human Rights. Another example is the UN Convention on the Rights of the Child; article 16 grants all children the right to full privacy.
In the tech and computing sphere, privacy has to do with the data or information you have under your control: on your mobile phone, laptop, memory cards, etc. This information is also protected by conventions and laws.
Security: protecting your data and identity
Security is about how you can protect your data, the information you store. It goes even further to cover how you protect the devices that are in your control. This covers a quite broad spectrum, and we only touch a more narrow scope here.
Your devices
Are your devices well-protected with device encryption? This is essential to avoid your data being leaked if your device is stolen or discarded. Without encryption, anyone can easily retrieve data stored on a device, even if the device is password-protected.
Are your devices password-protected? Do they have a way to authenticate you when you unlock or power on your device? This is an important tool to restrict access to your device if it is lost, especially if it's already powered on.
Your accounts
Are your login credentials strong? An easy-to-guess password or a short password can be very easy to break on today's computing devices. Many people don't even realize that the computing power on the mobile phones we carry around is commonly much more powerful than the computers we used a decade ago. This computing power can be used to break into your accounts.
An easy-to-guess password or a short password can be very easy to break on today's computing devices. The computing power on the mobile phones we carry around is commonly much more powerful than the computers we used a decade ago.
Have you activated Multi-Factor Authentication (MFA), often referred to as Two-Factor Authentication (2FA)? This makes it harder to attack your account because a username and password won't be enough. When using MFA, you're required to provide an additional login detail, which typically has a very short lifetime and usually can only be used once. The most common strategy is to use one of the "authenticator" apps where you get a six- or eight-digit code to enter upon login, but there are also better MFA options that require you to have an additional physical device for access — for example, a special (FIDO2/U2F) USB device.
Your communication
When you use the Internet, is all your communication secure? In other words, is your network traffic encrypted? Many users don’t necessarily think about that. One way to tell whether your network traffic is encrypted is if the Internet address you visit starts with “https” rather than just “http.” But this is a bit too simplistic; there are many more communication methods (AKA “protocols”) in use today that can implement encryption. Make sure you use one with encryption.
How it fits together
These three aspects of anonymity, privacy, and security do overlap somewhat, but they stand perfectly well on their own as well. And the expectations of your own goals need to match up with these three ideas and how you plan to use them.
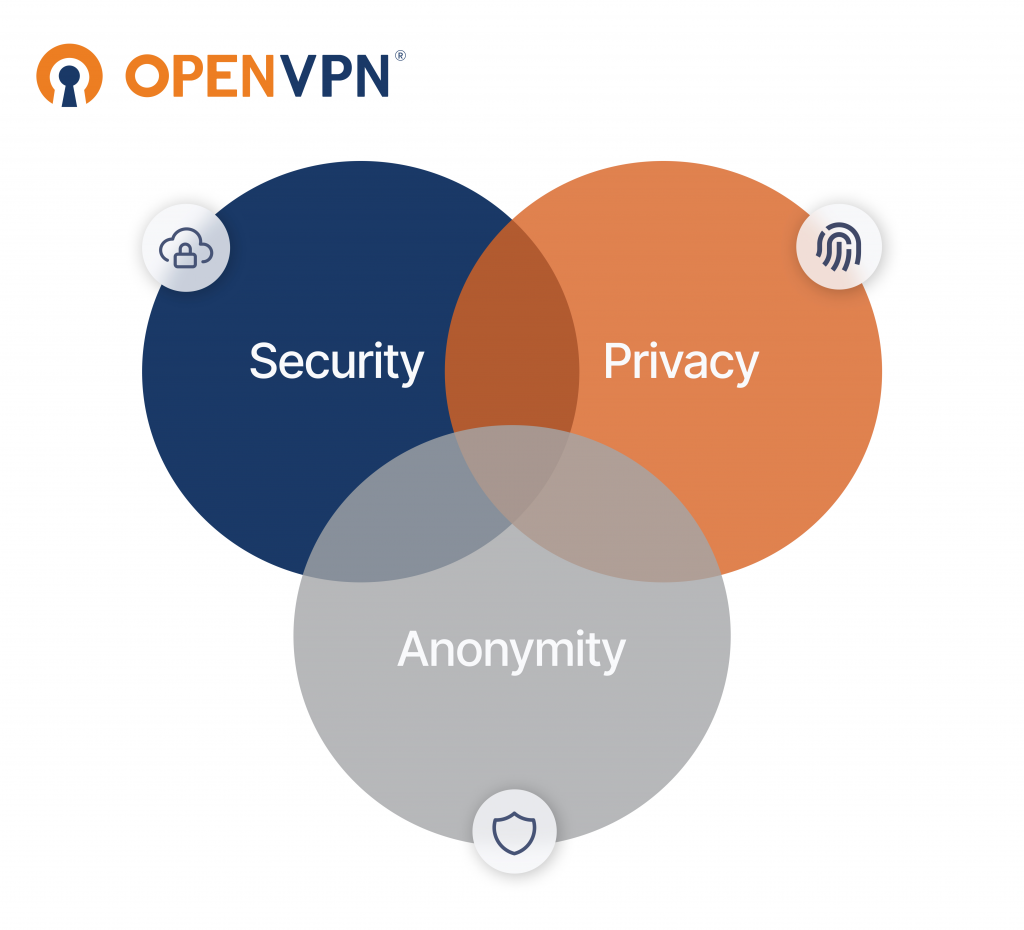
For example, it is perfectly possible to have full anonymity without privacy or security. If you carry clothes and masks hiding your face and identity, going to the shop and paying with cash, then nobody will truly know who you are, and there will be no way to trace your shopping back to your identity. Nevertheless, you will have no privacy when doing this in public; everyone nearby can see what you do and what you say. They just don't know who you are.
And security is not necessarily a given, either. If someone steals your wallet or your shopping bag, your being anonymous still does not protect your property. In fact, being anonymous might have put you more at risk. On the other hand, being anonymous might give you security by hiding who you are, like when publishing a paper opposing an oppressive regime while still being within that regime.
Another example: you can have full privacy without being anonymous. When you ensure that nobody can access your computer or mobile devices, essentially having a high security standard when handling your devices and online accounts, then you have made it really hard for an attacker to access your data without your knowledge.
If you hold a talk at a nearby town square, write articles in the local newspaper, or post on your Facebook profile with your full name, you have no anonymity, but you can still have the privacy you've established. People can track down who you are, in many cases where you live and what you do for a living, but they won't necessarily be able to access your computer or the information you store there.
While anonymity, privacy, and security do overlap, none of them necessarily exclude the other ones. Neither does one necessarily include either of the others.
As you can see, while anonymity, privacy, and security do overlap, none of them necessarily exclude the other ones. Neither does one necessarily include either of the others. In many cases there may be no need to have all three of them — though most of us definitely stand to benefit from being very much more aware of our personal security and privacy. The anonymity aspect is not one that is too often required. However, on the Internet, it may be beneficial to have some level of anonymity, at least when interacting among the masses.
Get Started Today
Ready to take your organization's privacy and security to the next level? With Access Server or Cloud Connexa, you can work from anywhere and from any device with confidence. Create an account today for two free connections and the secure network connectivity your business needs.


