How to Encrypt RDP to Protect Against Attacks in 2021
With the lockdowns in 2020 came rapid digital adjustments in all industries. This included ramping up the use of Remote Desktop Protocol (RDP), and with that increase came an increase in attacks. According to ESET’s Q4 2020 Threat Report, RDP attacks increased 768% between Q1 and Q4 last year.
RDP clearly had a target on its back.
Has that target gone away this year? The numbers for the beginning of 2021 are in, and the answer is a resounding, “No.”
In February 2021, Kaspersky reported 377.5 million attacks targeting RDP:
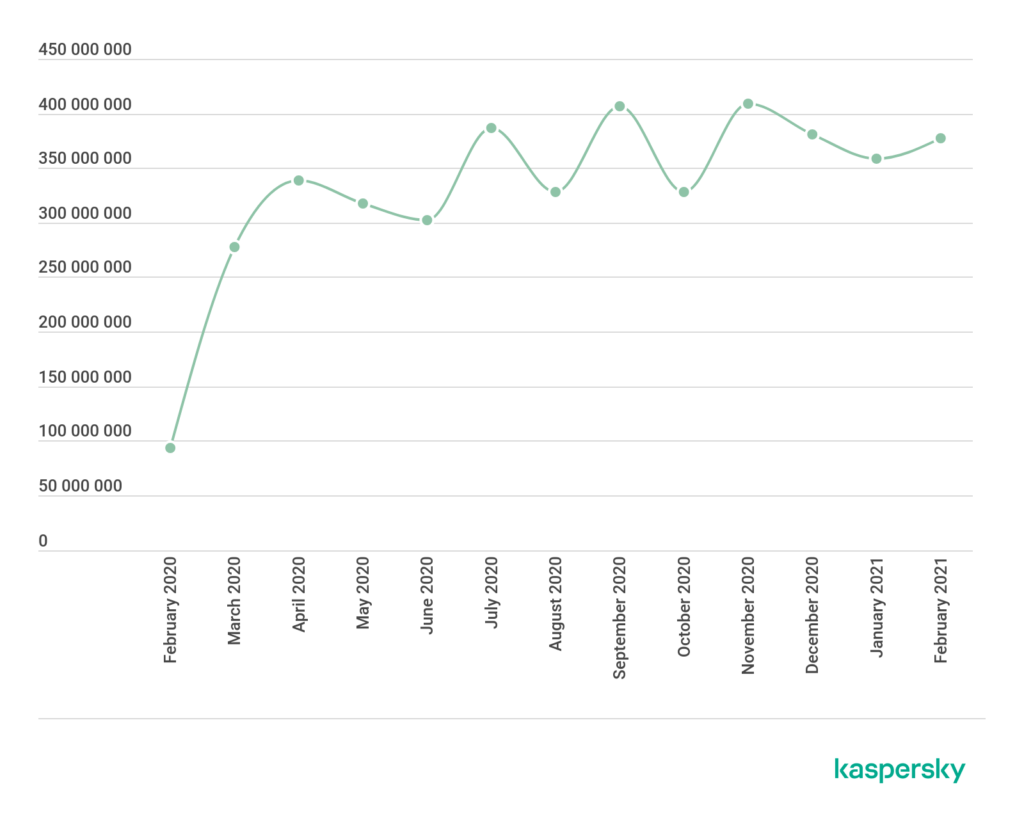
This graph shows the number of brute-force attacks against the RDP protocol. It paints a compelling picture of the RDP attack landscape: attacks skyrocketed with global lockdowns last year, and they aren’t trending back down.
Businesses will continue to provide access over RDP — and cyber criminals will still target it.
Remote work, after all, is here to stay. People will return to offices, connect in person again, and even sit in those meeting room chairs. But they will also still connect from home, attend virtual events, and depend on connections over the public internet. Businesses will continue to provide access over RDP — and cyber criminals will still target it.
Those targets may lead to dangerous outcomes when RDP is left exploitable — outcomes like ransomware. ZDNet reported that nearly half of ransomware attacks start with a compromise with RDP.
Why target remote desktops?
There are three compelling reasons for targeting RDP with brute force attacks:
- Network access: If an attacker can gain access using RDP, they gain complete control of the machine. Once they’re in, they get to work.
- Wide use: RDP is Microsoft’s proprietary protocol for enabling remote access to Windows servers and workstations. This means its use is widespread. It’s used by employees and entire companies, which provides a broad attack surface.
- Hasty setups: Organizations may have rushed to implement and configure RDP when lockdowns kept workforces at home. Missing important security steps increases the risk for businesses and employees, opening up access points for hackers.
“The solution here is not to avoid the risk, but to mitigate it.”
- Francis Dinha, OpenVPN CEO
How to Protect RDP
When implemented correctly, using RDP is a great tool for remote access. Virtualizing computers not only supports employees working from home, but increases productivity by giving them access to that desktop environment they’re used to. As a Microsoft product, it’s easy to manage for system administrators already working as a Microsoft shop, and users are familiar with it. So don’t brush it aside, but be aware that now, more than ever in the history of RDP, adding security is imperative. Here’s how:
- Enforce strong passwords: Many attacks are brute-force attacks, which require little effort by the attacker, but eventually get in when they find the username/password combination that fits. Think of it like trying every key on a keychain until one matches the lock. When people use simple passwords, brute-force attacks eventually succeed. Every business needs to educate employees about password hygiene. It’s good to include multi-factor authentication as well.
- Always update: Keep your software updated so you always have the latest patches. In 2020, Microsoft patched a number of remote desktop flaws. Companies that haven’t applied those are still at risk.
- Use an enterprise VPN: Any RDP network on the public internet is at risk. Isolate it behind the encryption and privacy of a virtual private network. We have an on-demand webinar to guide you through a step-by-step process of setting up OpenVPN Access Server with RDP. You can also set it up with our OpenVPN-as-a-Service product, CloudConnexa.
Remote Desktop Access Over OpenVPN Access Server
The diagram above shows a scenario without protection, and a scenario using an OpenVPN tunnel. At the top left, a remote worker accesses their work desktop over the internet, but a hacker gets in as well — either through stealing credentials or through a brute-force attack.
In contrast, the scenario on the right adds in OpenVPN Access Server. By using an enterprise VPN, it encrypts data communication between the work desktop and the remote worker. Access Server uses certificate verification in addition to user credentials, which verifies both the identity of the client and the server. This handshake ensures that only the remote worker gains access, blocking the hacker. The OpenVPN client, with the matching certificate, creates an OpenVPN tunnel through the internet to Access Server.
The office landscape has completely shifted.
Access Server also has the ability to use access control, only allowing access to a specific work desktop for that remote worker. For instance, user Sam connects his VPN client and can access the work desktop in our diagram, but user John can't. Instead, John has VPN access to a different resource, like a file server. The steps for setting this up are covered in detail in our on-demand webinar, with OpenVPN’s Access Server lead, Johan Draaisma.
No End in Sight for RDP Attacks
Businesses will continue to support the use of RDP going forward. The office landscape has completely shifted and likely won’t fully return to what it looked like pre-pandemic. Some of the workforce will continue to work remotely, while others will have hybrid options. This means attackers know that RDP is an effective vector to target.
“When teams are forced to make the change to remote work suddenly, as many were in 2020, they often skip over essential security measures in order to keep productivity up,” writes our CEO, Francis Dinha. “This means that the attacks and data breaches we saw associated with remote work in 2020 were not inevitable; remote work does not mean your team is doomed to a breach. Rather, it simply tells us that we have to be proactive.”
As more businesses take the necessary steps to secure RDP, we hope to see the number of successful attacks go down.