Using Cloud to Secure Private IaaS Access
Platform as a Service (PaaS) offerings from Infrastructure as a Service (IaaS) providers can be directly accessed from the internet as well as your virtual private cloud network.
Platform as a Service (PaaS) offerings from Infrastructure as a Service (IaaS) providers can be directly accessed from the internet as well as your virtual private cloud network.

Limited PaaS platform provider security controls
A PaaS environment shared responsibility security model may not protect customer accounts, apps, and sensitive data hosted on the platform from cyberattacks.
IaaS environments need customer-implemented access control
IaaS focuses on virtual machine management, so customers need robust access control to limit user access to authorized apps and services only and reduce vulnerabilities.
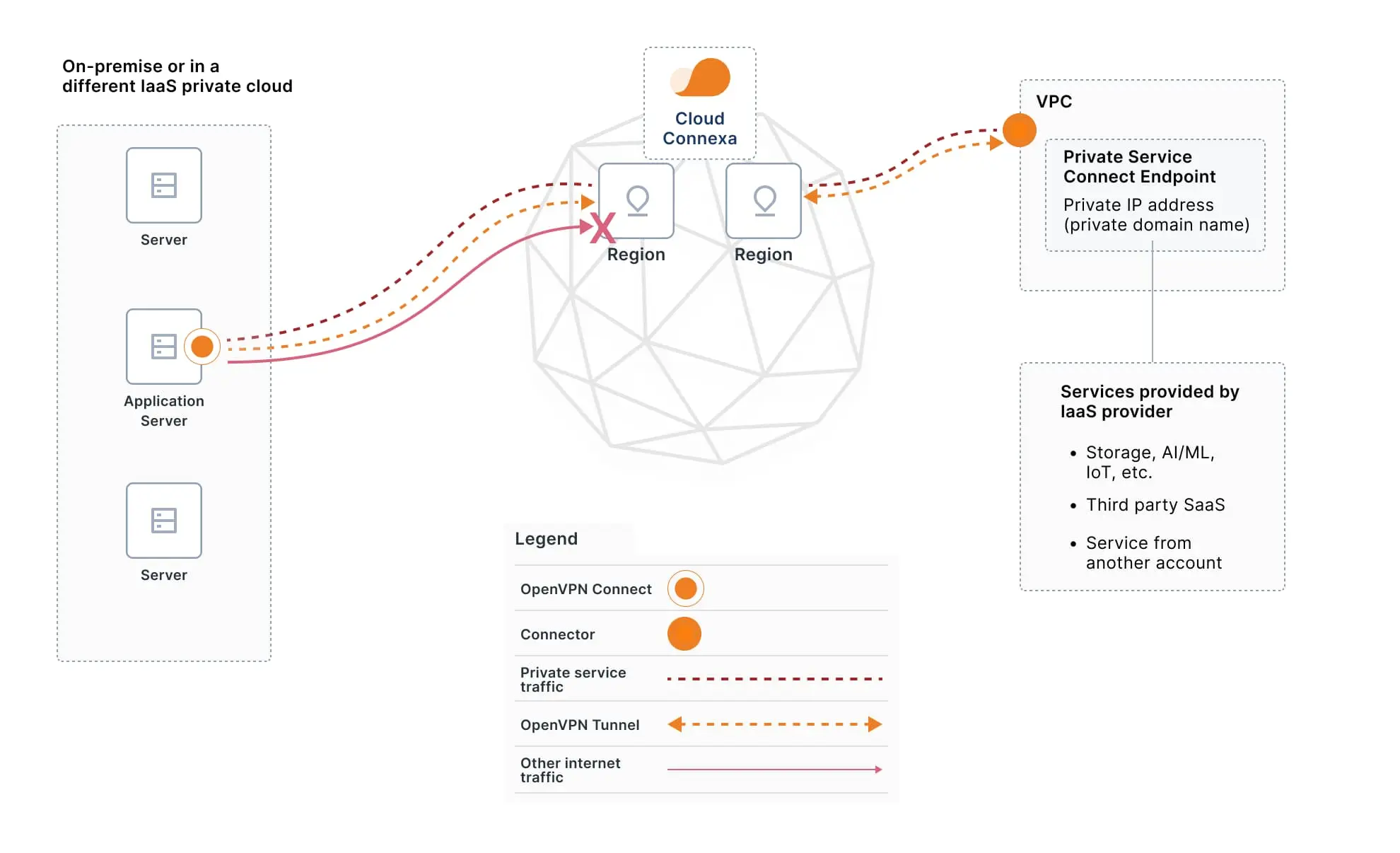
When you use Cloud Connexa to extend private services to on-premises data centers, between different IaaS environments, or directly to users you can also:
Minimized attack surface
Use AWS, GCP, or Azure to set up private DNS zones for naming your private endpoint, then set Cloud Connexa DNS to use those DNS Servers.
Accurate, reliable routing
Route to the correct connected network based on application domain names Deploy lightweight VM(s) running Connector software, then configure Applications with domain names assigned to private endpoints, and routing will be accurate even if a private endpoint’s IP address overlaps in another network.
Granular Access Control
Apply Access Controls to individual servers (Hosts), connected networks (including IP address subnets), and User Groups so you can easily authorize access to Applications offered via the private endpoints.
Robust security posture
Maximize security by configuring a Host, Network, or User Group with access limited to services offered by private endpoints, blocking access to public internet and other services.

Protecting access to SaaS
Secure your SaaS applications with OpenVPN's industry-leading SaaS security solutions. Enforce strong access control & protect sensitive data.
Read the Use CaseSite-to-site networking
Securely connect your networks. Explore enterprise-grade site-to-site VPN solutions. Get started today!
Read the Use CaseEnforcing zero trust
Enforcing zero trust access is an important layer of a good business security plan. You can configure this easily with OpenVPN.
Read the Use CaseSite-to-site VPNs & CloudConnexa
Find out how to use CloudConnexa to level up your site-to-site communication security.Learn moreCompare Access Server and CloudConnexa
Not sure ClousConnexa is right for you? Compare side-by-side to decide.Learn moreSite-to-site VPN routing with Access Server
Learn about site-to-site VPN routing with Access Server.Learn more