Comparing OpenVPN Access Server with OpenVPN Community Edition
DATASHEET
OpenVPN: understanding the difference between the community open source and the enterprise Access Server
OpenVPN is a well-known name in the cyber security space for providing one of the best VPN protocols. What’s the difference between the open source VPN project and the business VPN solution, Access Server? Here’s an overview of each, a comparison chart of their features, and a list of benefits provided by both products.
OpenVPN Open Source
The OpenVPN open source project, also called Community Edition (CE), is the open source Virtual Private Network (VPN) project. It creates secure VPN connections over the internet using a custom security protocol that utilizes SSL/TLS. It has emerged to become the de-facto standard in the open source networking space. The project was started by OpenVPN co-founder James Yonan and is published under the GNU General Public License (GPL). It has over 50 million downloads to date and is a community-supported OSS project.
OpenVPN Access Server
OpenVPN Access Server is a VPN solution designed specifically for businesses, built on the open source project. Access Server comes in a single package to simplify the implementation of a VPN remote access solution. It includes an economical licensing model based on concurrent connections, is easy to set up and scale, and can be deployed simply on the cloud.
| Features | OpenVPN Access Server | OpenVPN Community Edition |
|---|---|---|
| Customer Support | ||
| Dedicated support ticket system covered by our global team of professionals | ||
| Supported by open source community (IRC, web forum, mailing list) | ||
| Security | ||
| VPN tunnels use OpenVPN protocol | ||
| Configurable encryption ciphers | ||
| Integrated, out-of-the-box LDAP support | available as a plugin | |
| Integrated, out-of-the-box RADIUS support | available as a plugin | |
| Integrated Google Authenticator 2FA support | available as a plugin | |
| Post-authentication script support | ||
| Authenticate with pre-shared keys | ||
| Authenticate with certificates | ||
| Authenticate with certificate and username/password and 2FA | ||
| Uses OpenSSL encryption library | ||
| Graphical Interface | ||
| Administration web interface for server configuration | ||
| User web interface for VPN client and profile downloads | ||
| Customizable Portal branding | ||
| View log files in web-based admin site | ||
| Toggle between TLS settings in web-based admin site | ||
| Simple hostname (custom URL) setup through web-based admin site | ||
| Easily switch between NAT or Routing using web-based admin site | ||
| Manage DNS Settings in web-based admin site | ||
| Setup split tunneling with one click using web-based admin site | ||
| Simple import of web server certificate using web-based admin site | ||
| Simplified Access Control List (ACL) management with web-based admin site | ||
| Installation | ||
| Automated PKI setup | ||
| Client software bundled with connection profiles. Connect clients can also import profile from server. | ||
| Easy deployment | ||
| Pre-built virtual appliances | ||
| Compatible with any clients that support OpenVPN protocol | ||
| Embedded in some router firmware | Router can be used as a client to setup VPN to Access Server | |
| Available for DD-WRT | Router can be used as a client to setup VPN to Access Server | |
| Available on AWS Marketplace | ||
| Available on Microsoft Azure Marketplace | ||
| Available on Google Cloud Marketplace | ||
| Available on DigitalOcean Marketplace | ||
| Included in most major Linux distributions | Not included in repository, but most Linux distros supported | |
| Configuration | ||
| Multi-daemon mode allows the use of all CPU cores | ||
| Simple user management | ||
| User Groups | ||
| User and Group-level access controls | ||
| Software can work in both Server and Client roles | Acts only as a Server | |
| Bridging | ||
| Command Line Interface (CLI) | ||
| API | Management Interface | |
| Scalability and availability | ||
| High-availability failover solution | Managed by the user outside of the VPN software | |
| Multi-node cluster solution | Managed by the user outside of the VPN software | |
| Easy scalability | Managed by the user outside of the VPN software | |
| Cost | ||
| Free to use | (limited to 2 VPN connections) | |
| Purchase licenses | ||
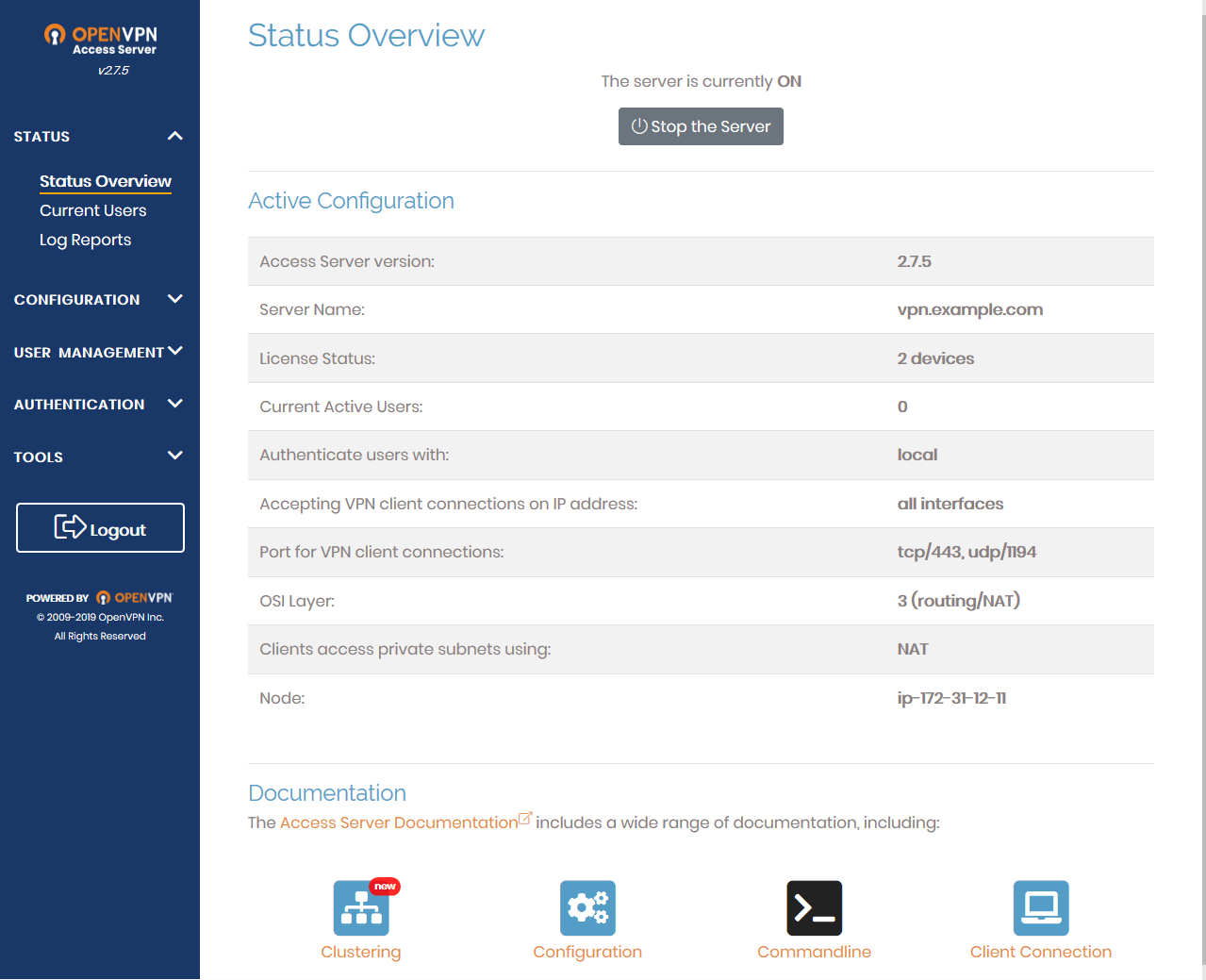
OpenVPN Access Server’s Admin Web UI
OpenVPN Access Server provides you with a powerful and easy-to-use web-based admin site that makes VPN management and configuration simple enough for anybody (with or without Linux knowledge). Access Server integrates OpenVPN server capabilities, enterprise access management, and OpenVPN Client software packages that accommodate Windows, mac, Linux, and mobile OS (Android and iOS) environments.
One way to present a clear visual of the strength of the Admin Web UI is to compare setting up Google’s Multi-factor Authentication with Access Server versus Community Edition (please note, this is a high-level overview for the purpose of presenting the comparison, not in-depth instructions for set up):
Google Authentication with Access Server
What you need to begin:
OpenVPN Access Server on your server (Linux server, virtual machine, cloud image, etc)
-
Step 1: Enable Google Authenticator
Enable Google Authenticator in the Admin Web UI.
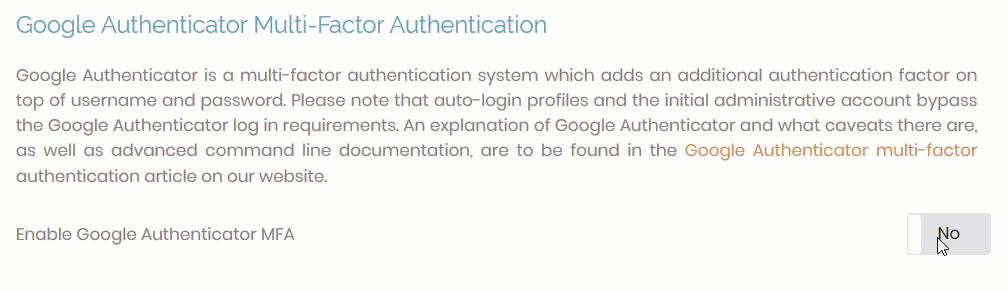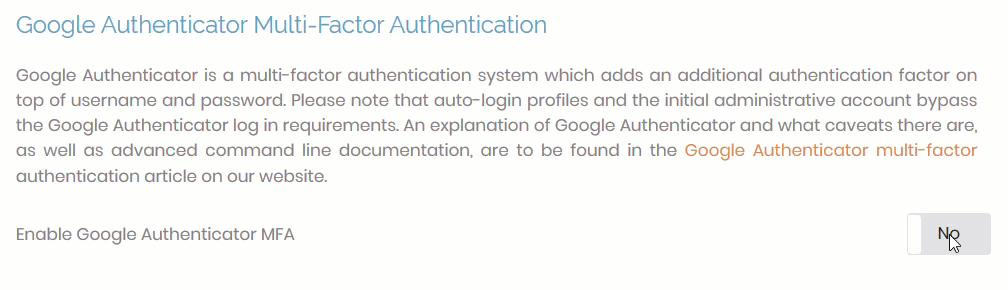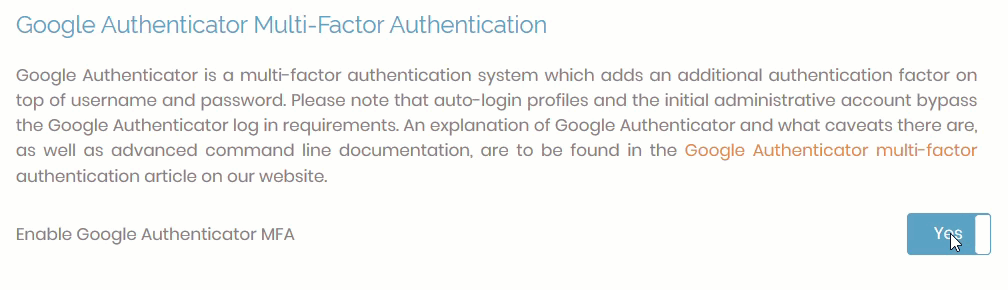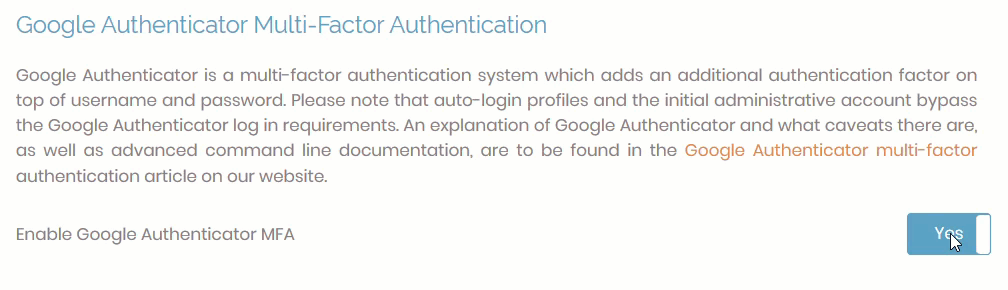
-
Step 2: Users Log In to Client Web Service
Users can now log in to the Client Web Service in their browser. Once they’ve entered their credentials, they’ll receive a screen with a QR Code to scan with Google Authenticator, after which they can download the client for their appropriate operating system.
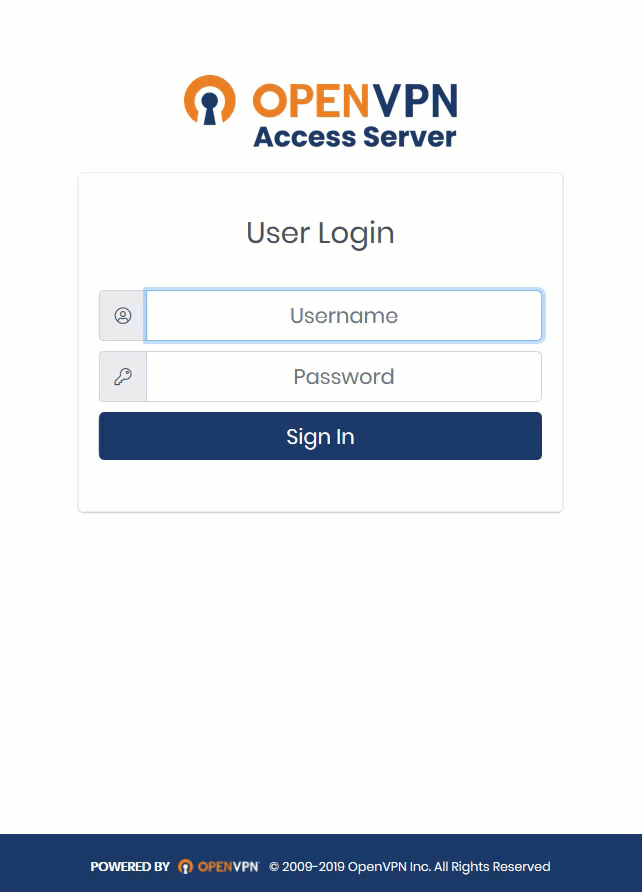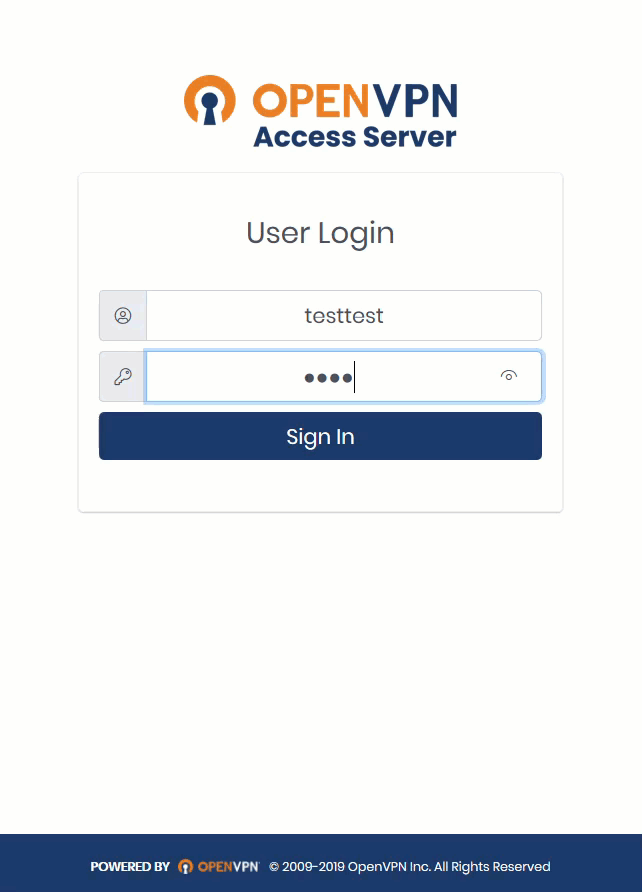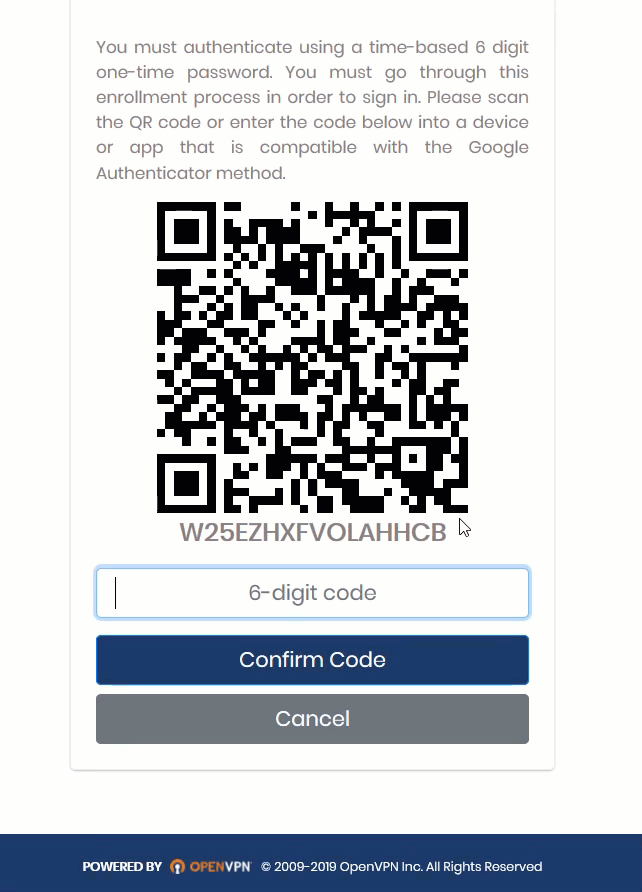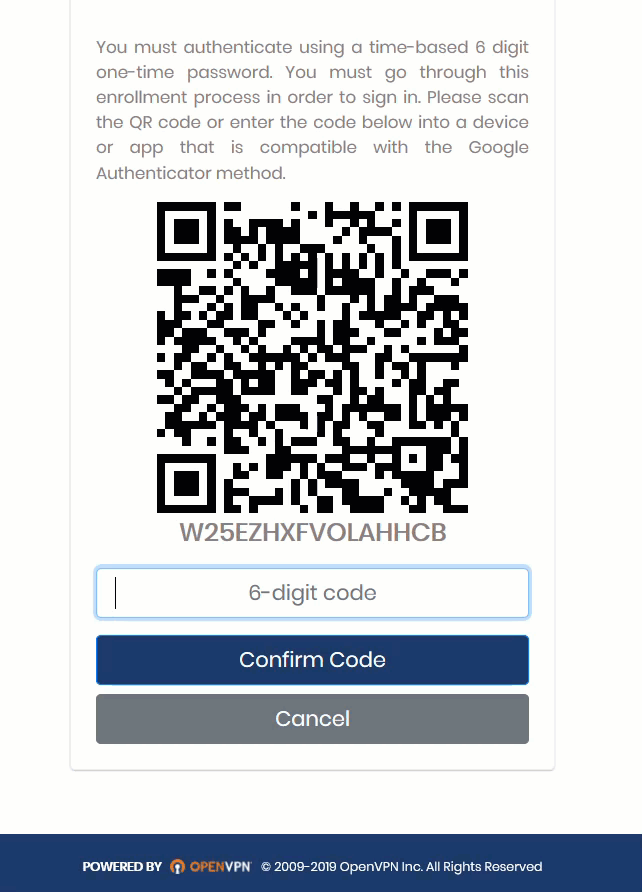
We provide a tutorial to walk a user through this set up. It took three minutes: Remote User Connection.
Google Authentication with Community Edition
What you need to begin:
OpenVPN Community Edition on your Linux server with a Public Key Infrastructure setup (certificates, keys, and master Certificate Authority)
-
Step 1: Install packages
Install a QR Encoding Library and Two-step verification:
libqrencode3libpam-google-authenticator -
Step 2: Create user and groups
Next, create a user and group necessary for the Google Authenticator to generate tokens. You will also need to create the directory where they’re stored.
-
Step 3: Modify Configuration File
Modify the OpenVPN service configuration file to add a line for PAM authentication.
-
Step 4: Configure PAM
Create a PAM configuration file for OpenVPN.
auth required /lib/security/pam_google_authenticator.so secret=[location of google auth directory from step 2]{USER} user=[google user created] forward_pass -
Step 5: Configure OpenVPN Client
The text file needed by the client device to contact and communicate with the OpenVPN server now needs MFA added.
ns-cert-type server auth-user-pass(Sys Admins often create a script to automatically generate this file and will need to change the generate_mfa() function.)
NOTE: Each of these above steps require modifications and commands specific to your OpenVPN configuration. You can find examples of such in articles online such as this one: Using Google Authenticator MFA with OpenVPN on Ubuntu 16.04, which we referenced for the high-level steps above.