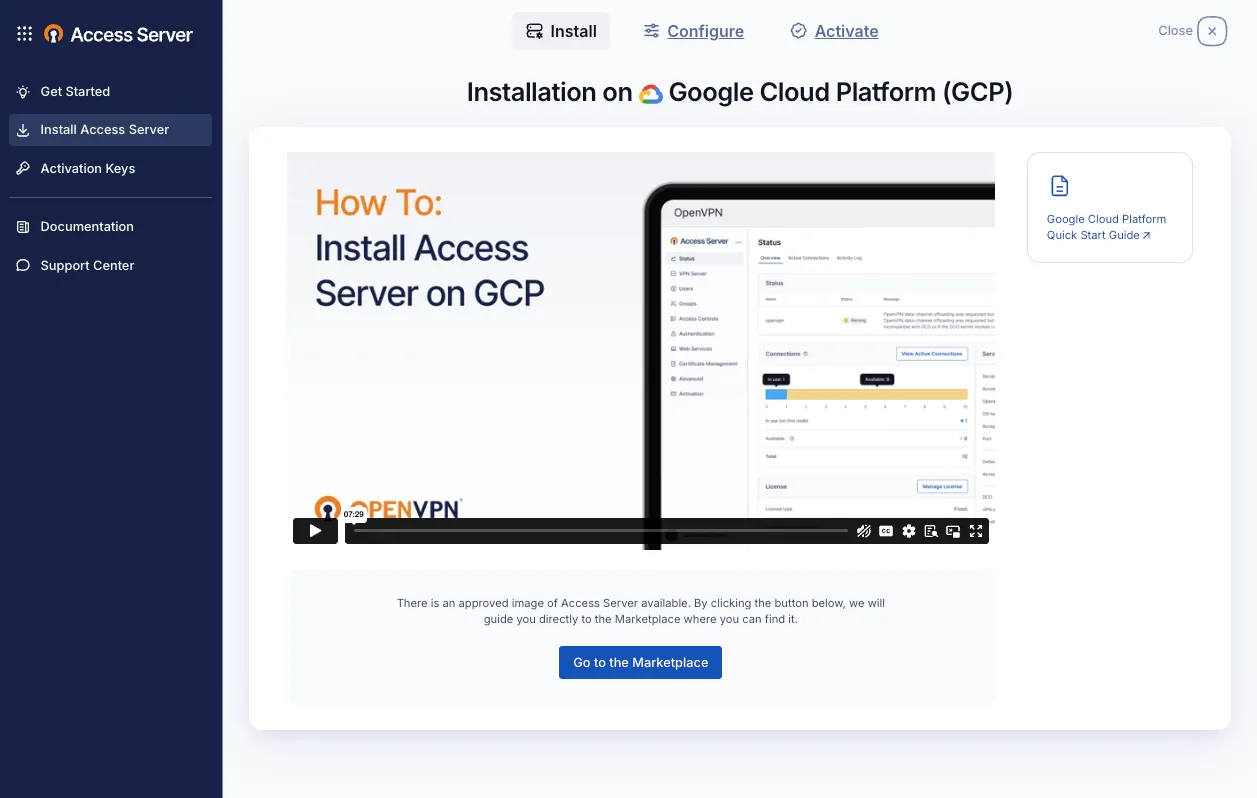
Secure Your Network on Google Cloud with Access Server
Connect your remote workforce to your virtual private cloud (VPC) with the trusted security of OpenVPN and the flexibility of Google Cloud. Deploy our pre-configured VPN appliance in minutes from the Google Cloud Marketplace — no complex configuration required.