Secure IoT Communication Anywhere
Get end-to-end encryption and IoT security solutions for all of your company’s devices.
Get end-to-end encryption and IoT security solutions for all of your company’s devices.

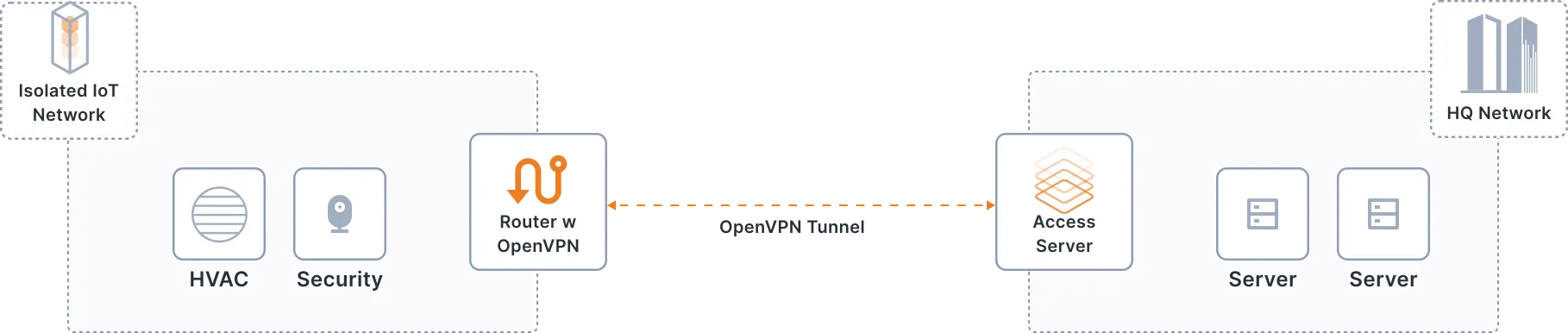
Create isolated, secure IoT networks
Reduce your attack surface and prevent lateral movement.
Use digital certificates for authentication
Connections are supported by mutual authentication using digital certificates.
Set up easily with compatible routers
Set up is easy with popular routers — including DD-WRT, OpenWrt, pfSense, Teltonika, & Ubiquiti.
IoT devices make up 30%of all network-connected endpoints. With so many connected IoT devices online and more coming every day, the attack surface is growing exponentially and putting every organization at enormous risk. Keeping your IoT network isolated from the internet reduces your attack surface and the risk of cyber attacks.
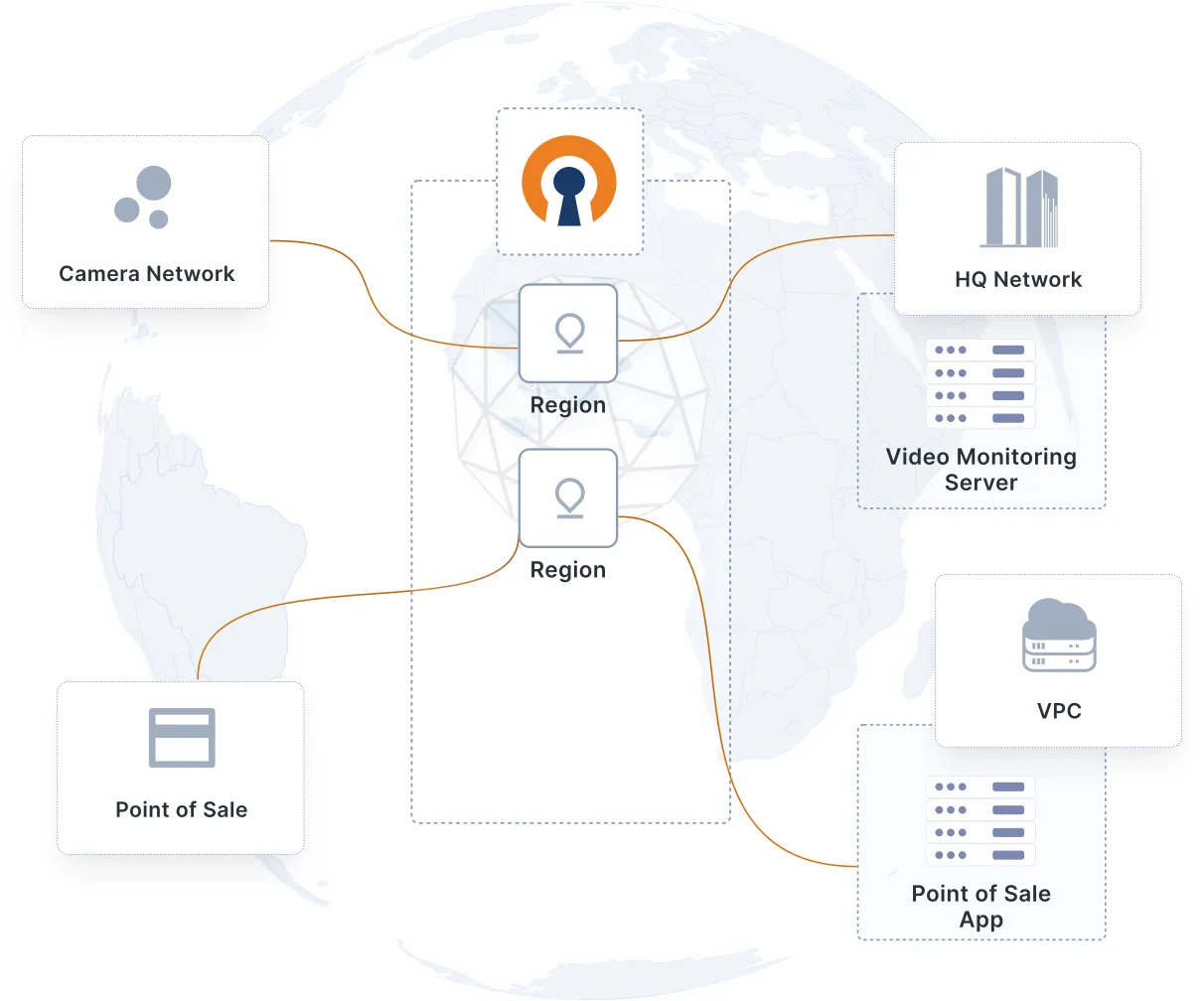
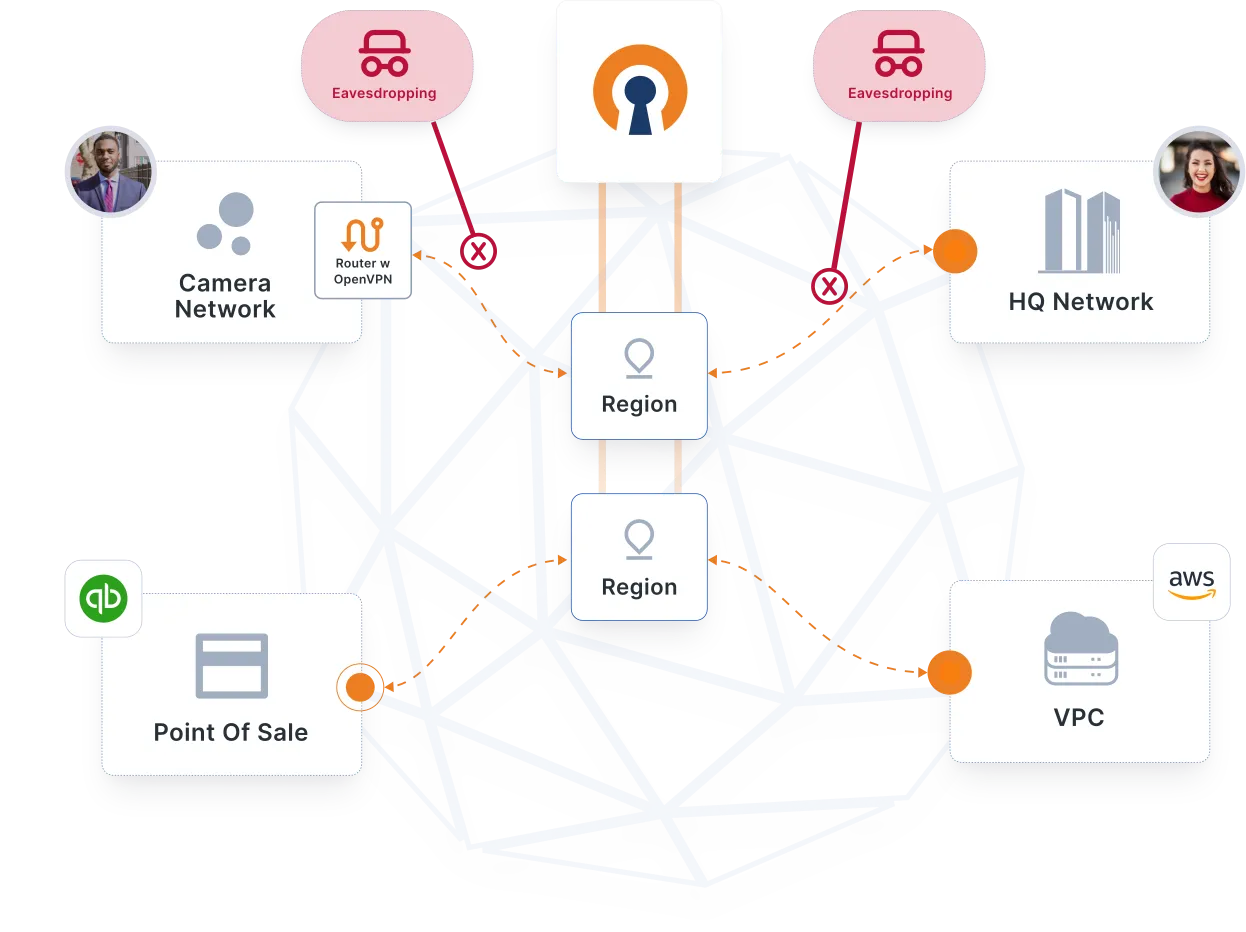
IoT devices deployed in an open environment — e.g., mobile and distributed point-of-sale systems transmitting financial data — need to be secured against eavesdropping. To combat this, a VPN encrypts all communications while they travel over the internet.
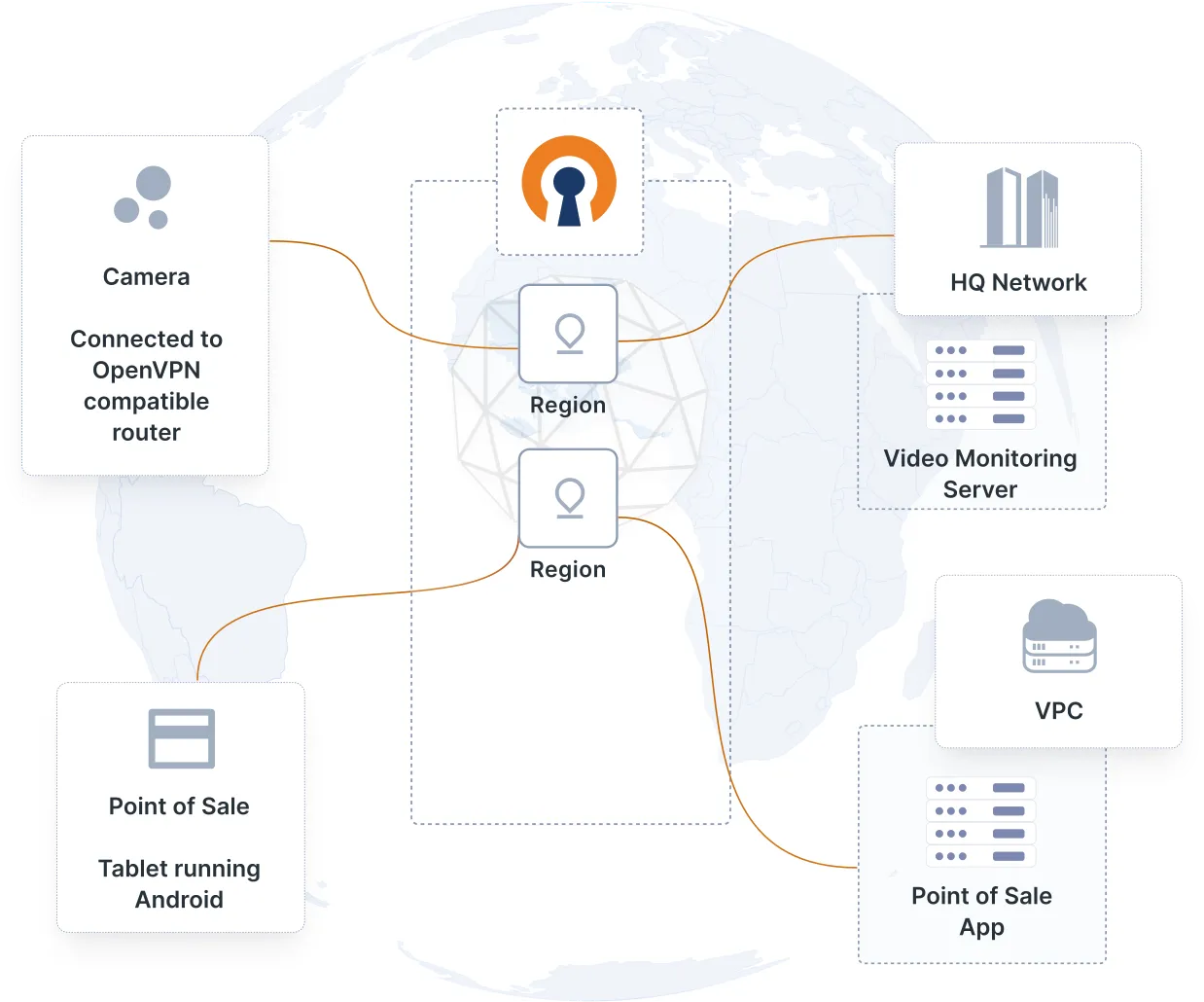
Your IoT devices can range from tablets, laptops, and smartphones to cameras, vehicles, health devices, machine sensors, and everything in between. These devices in your environment run on different operating systems, creating interoperability and security challenges. You need easy setup with compatible routers and VPN clients with extensive operating system support. The open source nature of OpenVPN enables you to adapt the code to your device.
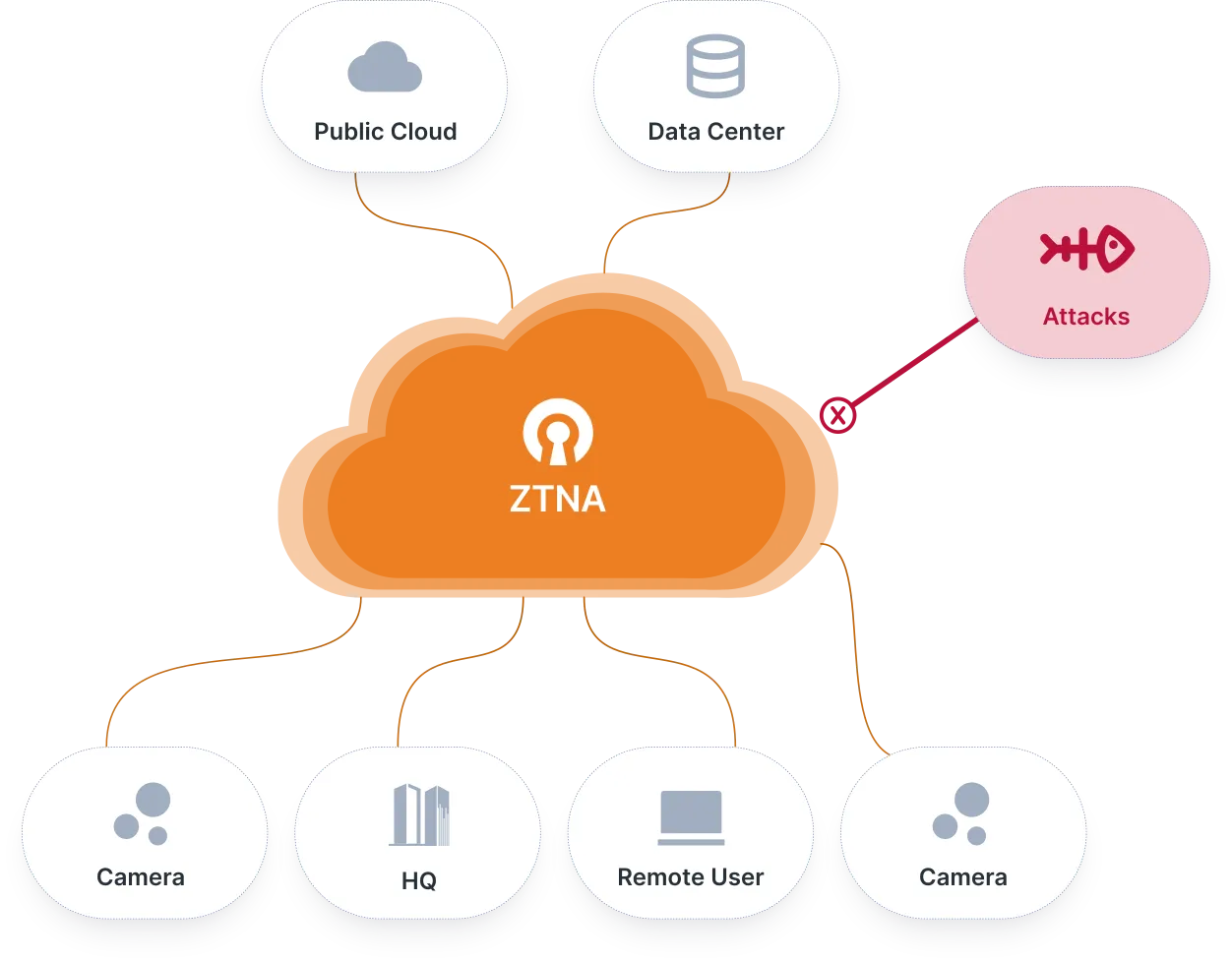
For all of the devices connecting to your network, you need to know whether they can be trusted as the devices you’re expecting. Especially in a BYOD environment, it's critical that only authorized devices are connected.
Access Server provides a secure, user-friendly experience for Secure IoT communication by giving you the ability to:
Run your own OpenVPN solution
Keep all data communications within your trust domain. Have total control of where and how many VPN servers you deploy.
Set up auto-login credentials
Protect unattended devices and routers supporting those devices, to provide always-on secure private connections with mutual authentication and digital certificates.
Create an encrypted secure virtual network
Protect devices against eavesdropping and isolate your IoT network from other business networks and the public internet.
Get enhanced flexibility and compatibility
Use the OpenVPN Connect app, and tap into the open source Community Edition.

Cyber Threat Protection and Content Filtering
No matter where or how you connect to the internet, you can be at risk of different online attacks.
Read the Use CaseSite-to-Site Networking
Securely connect your corporate network, remote offices, and cloud networks with encrypted tunnels using our site-to-site VPN solution.
Read the Use CaseEnforcing Zero Trust
Enforcing Zero Trust Access is an important layer of a good business security plan. You can configure this easily with OpenVPN.
Read the Use CaseCompare Access Server and CloudConnexa
Not sure which product is right for you? Compare side-by-side to decide.Learn moreThe IT Manager’s Guide to Buying Network Security
Use this guide and free checklist to help evaluate vendors.Get a copy