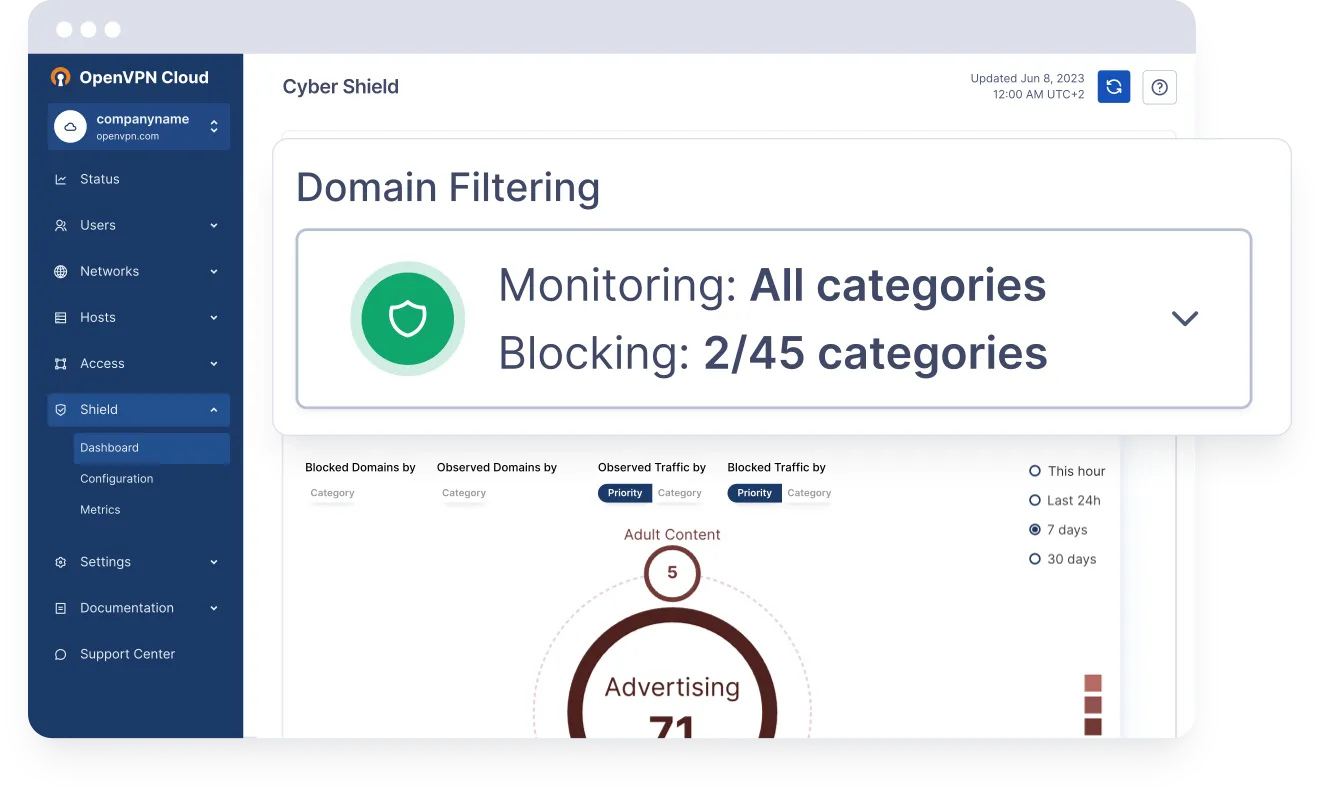
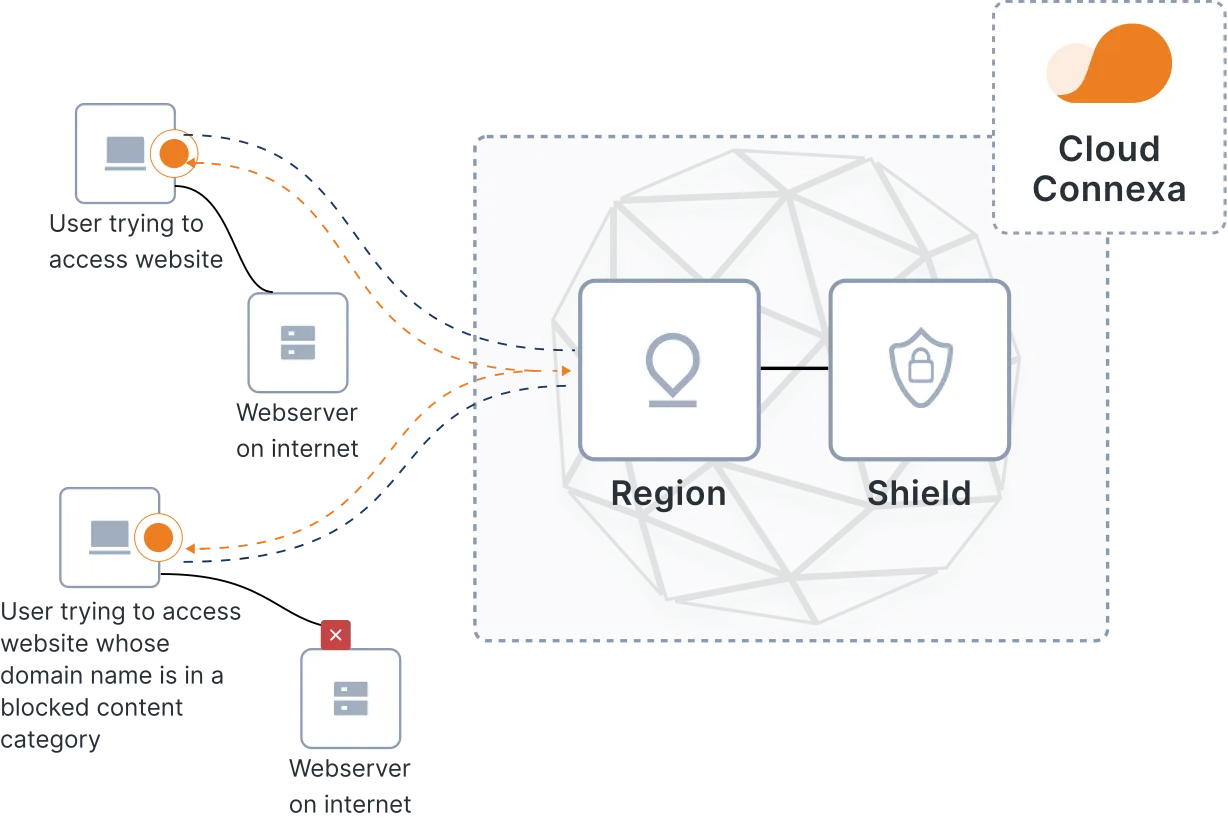
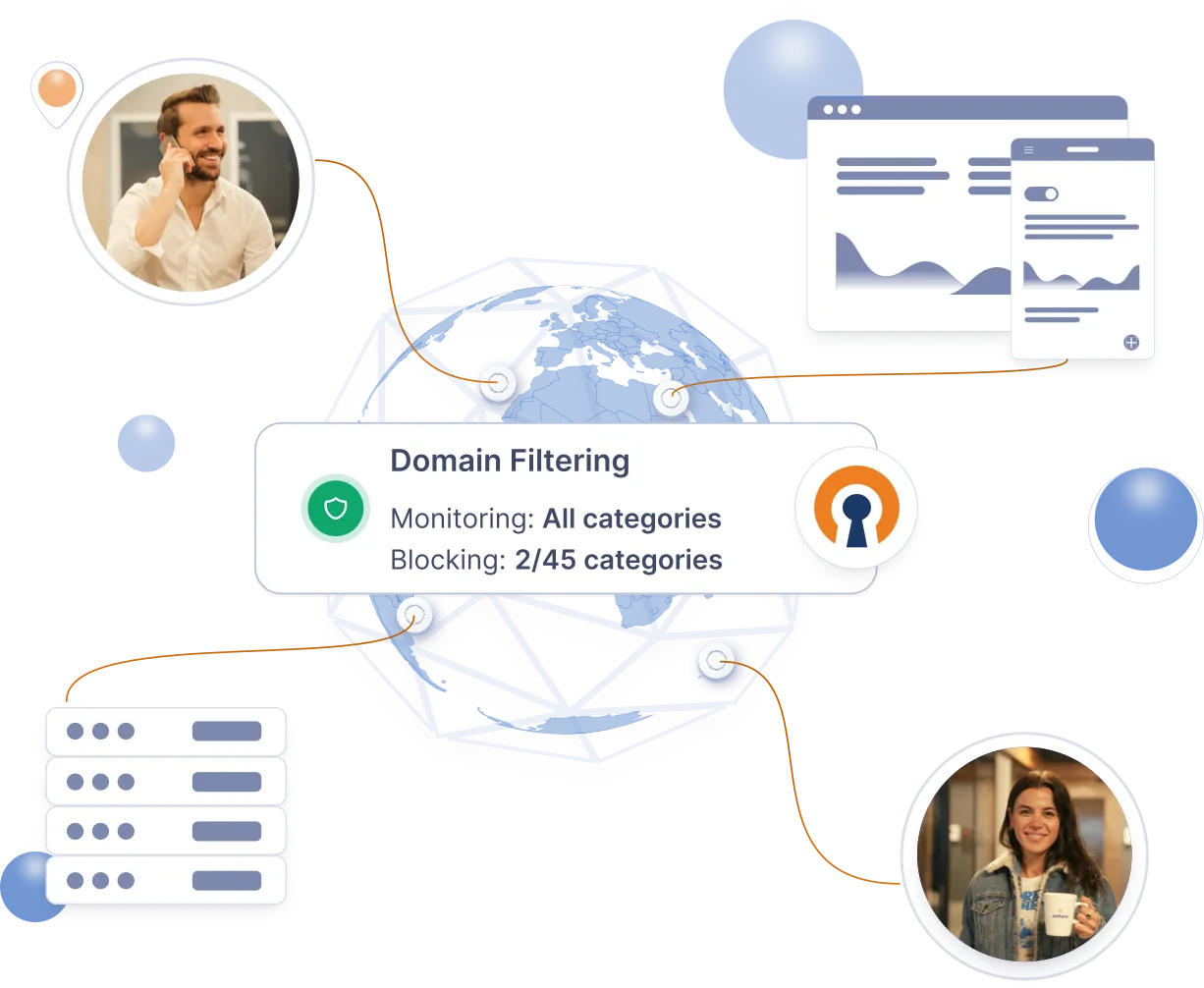
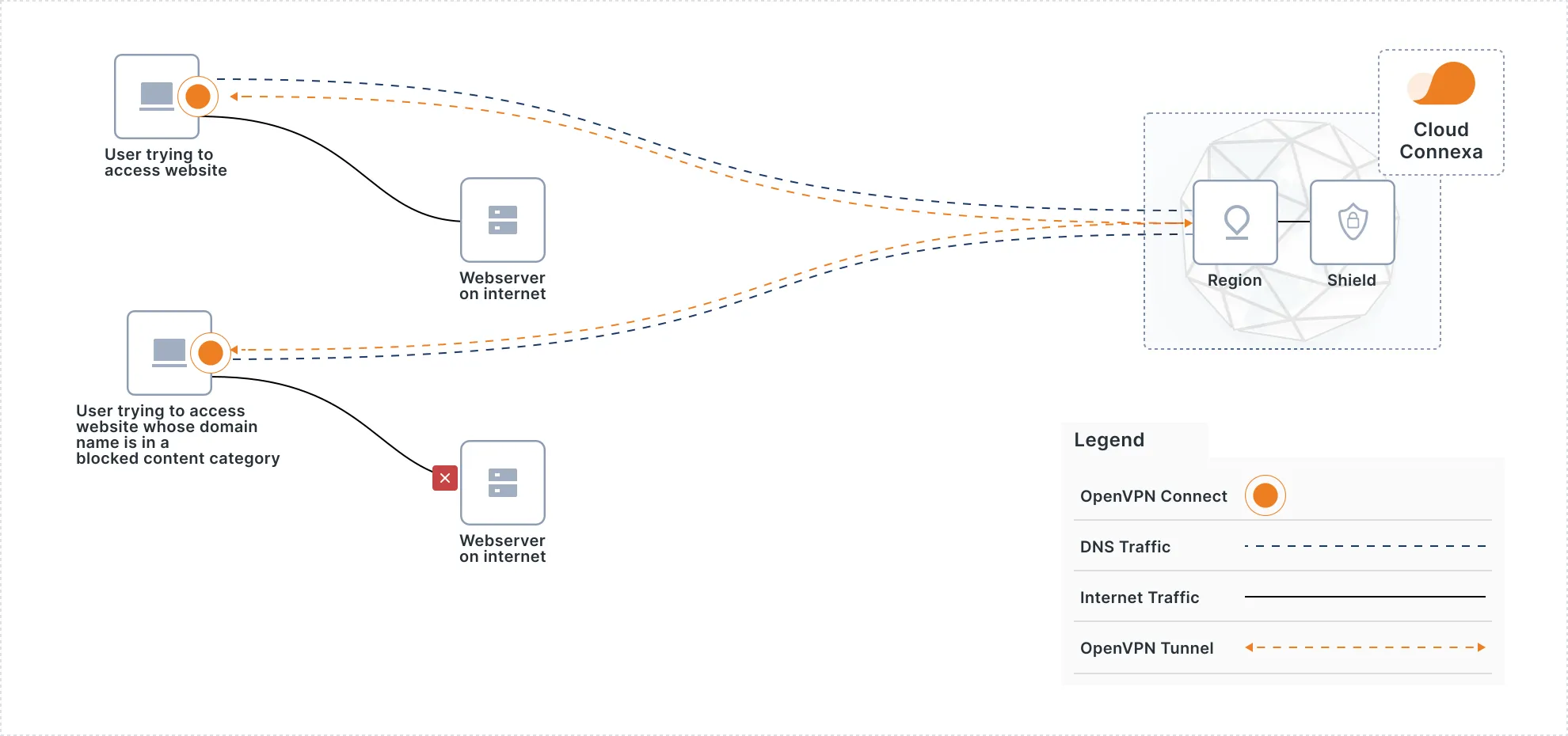
DNS Security & Content Filtering for Superior Threat Protection
Your distributed workforce accesses the internet from a variety of devices, making DNS security services, internet policy, and content enforcement more complex while remaining critical to combatting network breaches.