Enforce Zero Trust Access: Never Trust, Always Verify
Zero Trust Network Access, ZTNA, is an ongoing journey, not a single product or process. OpenVPN can help you build the foundation for the right zero trust approach for your business.

Zero Trust Network Access, ZTNA, is an ongoing journey, not a single product or process. OpenVPN can help you build the foundation for the right zero trust approach for your business.

Transition from perimeter-based network security
The corporate perimeter has changed. Implement multi-factor authentication, strong password policies, and continuous authentication mechanisms to verify the identity of users and devices.
Implement least privilege access
Embrace the principle of least privilege, granting access only to those who truly need it and enforcing strict access controls based on user roles and responsibilities.
Cloak apps and reduce your attack surface
Keep bad actors at bay by eliminating points of entry and unfettered access to your corporate assets and network. Keep services private and isolated from the internet. Get ZTNA for all TCP/IP application protocols.
Your company’s network has numerous access points that require global secure access beyond network perimeter security. Protect these access points with zero trust basics.
You know access should be limited, but constantly contending with multiple authentication and identity systems can be a headache. CloudConnexa streamlines the process: mutual authentication of digital certificates, built-in 2FA, and authentication with SAML and other protocols can verify user identities before granting access. Access simplified.
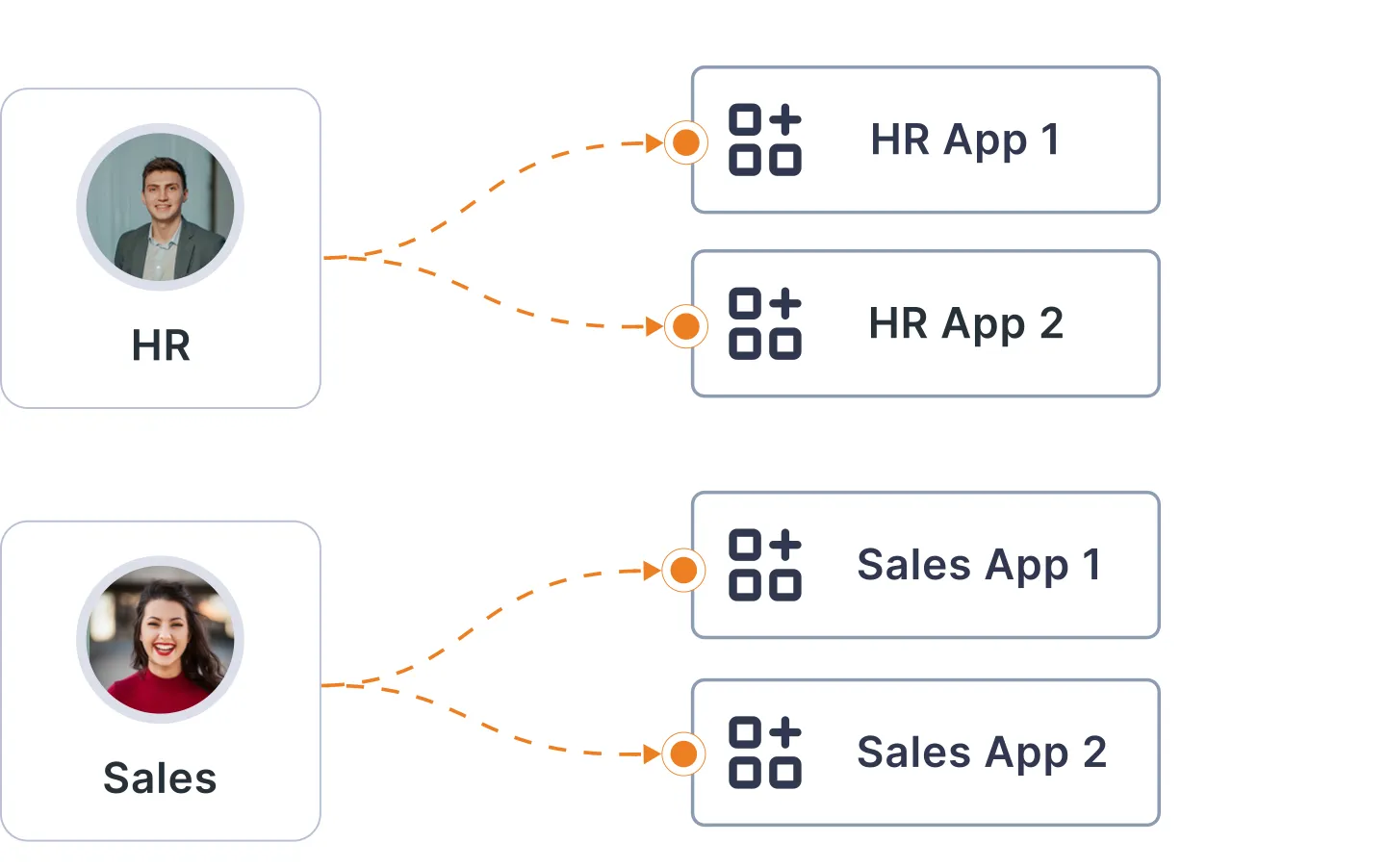
It's essential to limit your team's access to only what they need — and nothing more. Reduce your attack surface with granular identity-based access controls that ensure users and devices only access what they need. Logically segment your network to limit lateral movement and contain potential breaches.
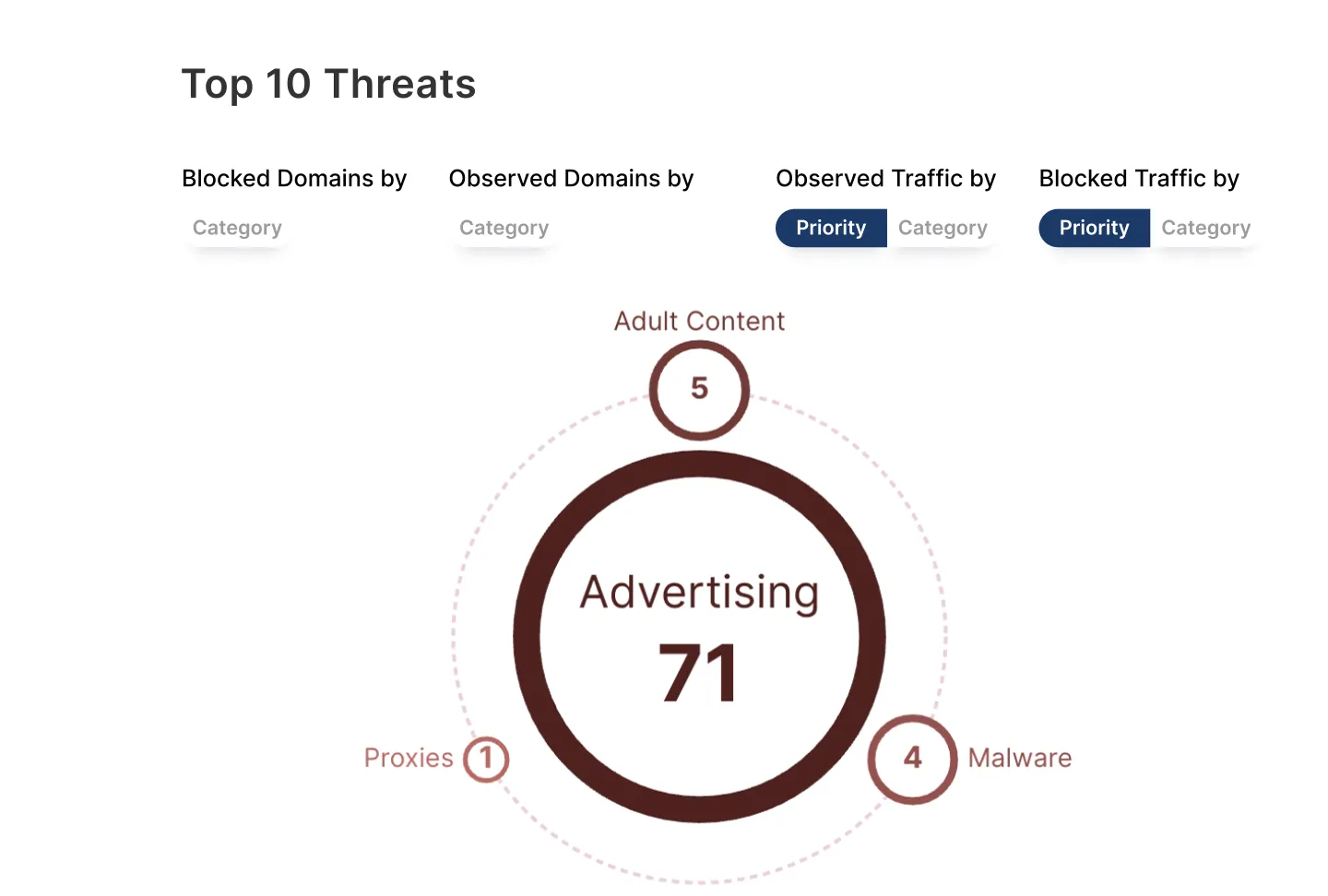
No cybersecurity tool eliminates human error — so how can you stop those errors from turning into malware or ransomware attacks? With limited access and content filtering, you can prevent these potential threats.
Using the tenets of ZTNA, OpenVPN offers continuously verified security controls to ensure access is granted only from trusted locations, to authorized and compliant devices with security hygiene features in place.
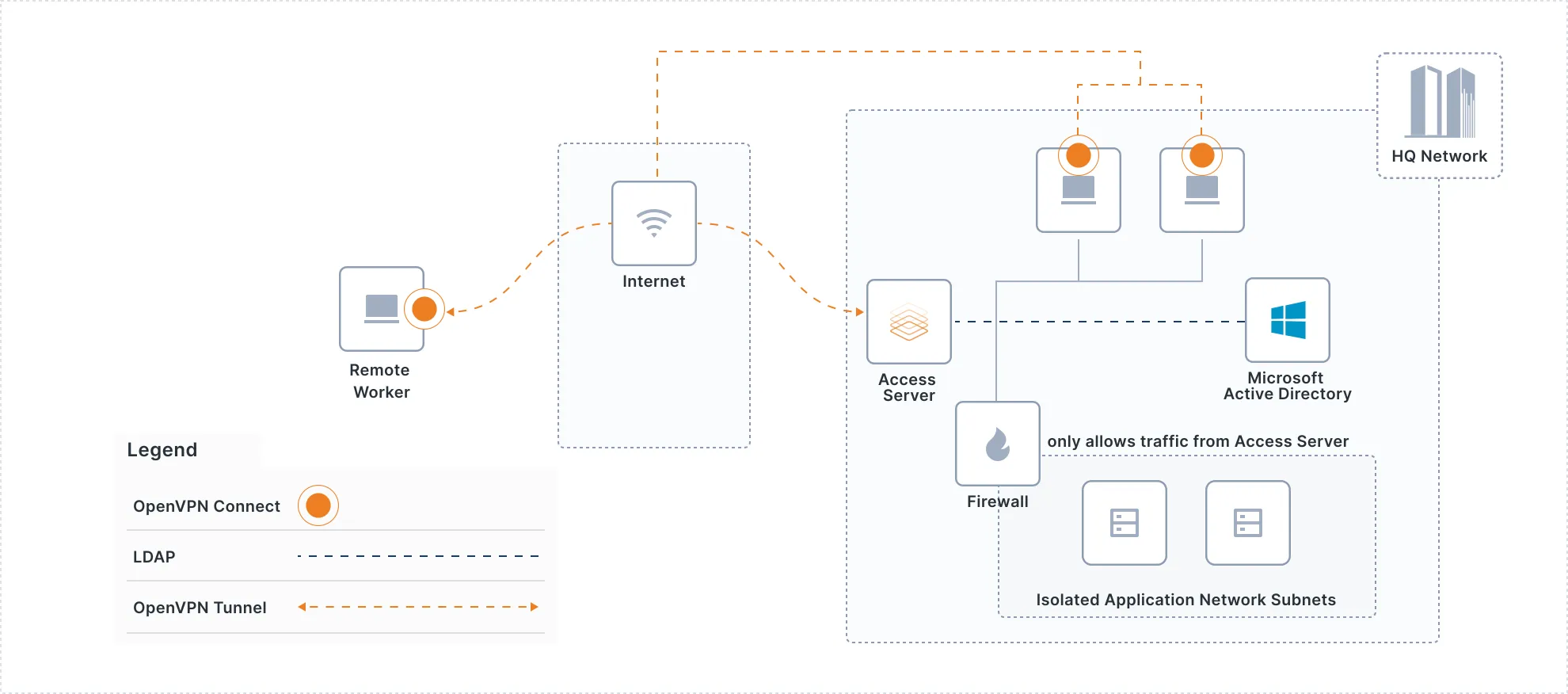
Access Server provides secure, reliable connections across all of your distributed networks by giving you the ability to:
Eliminate single points of failure
Never trust connections based solely on perimeter defenses. Define identity-driven authentication policies, then enforce secure connections for specific application resources.
Create a hybrid cloud
Define access controls based on user groups. Create access control lists (ACL) that limit access to only those resources required for every group. Map roles and departments to ACLs and enforce those at the network level.
Connect without extra headache
Classify and isolate specific application resources so they can only be accessed through your secure private network, regardless of location.
Deploy easily
Enable identity-based access control using SAML, LDAP, RADIUS, and Active Directory servers. Create a hardware address-checking script to enhance the security of your authentication by only allowing users with registered MAC addresses and UUID strings to connect to the VPN server successfully.

Cyber Threat Protection and Content Filtering
No matter where or how you connect to the internet, you can be at risk of different online attacks.
Read the Use CaseSecure Remote Access
An ideal solution for SMBs, OpenVPN's business VPN for secure remote access provides a tailor-made solution for remote and hybrid workforces.
Read the Use CaseSecure IoT Communications
Safeguard your connected devices. Explore OpenVPN's comprehensive IoT Security Solutions.
Read the Use CaseCompare Access Server and CloudConnexa
Not sure which product is right for you? Compare side-by-side to decide.Learn moreGuide: What solution does your company need?
VPN, ZTNA, SASE, SSE – cut through the acronyms and find what you need most.Get a copy of the guide