Operating Systems
Windows
Tutorial: Enable routing and NAT on Windows Server 2016
This configuration tutorial provides the steps to enable routing and NAT on a Windows Server 2016.
This configuration tutorial provides the steps to enable routing and NAT on a Windows Server 2016.
You must first deploy the Routing and Remote Access Service on Windows Server.
We strongly recommend that you refer to the specific documentation for the Windows Server version that you are using.
This document provides information on deploying Routing and Remote Access Service for Windows Server 2016. You can refer to Microsoft’s own documentation here: https://docs.microsoft.com/en-us/windows-server/remote/remote-access/ras/remote-access-server-role-documentation
Open Server Manager, click Tools and select Routing and Remote Access.
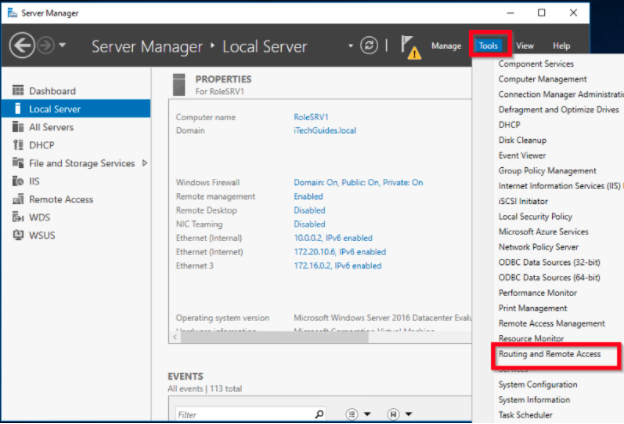
Right-click the server, and select Configure and Enable Routing and Remote Access.
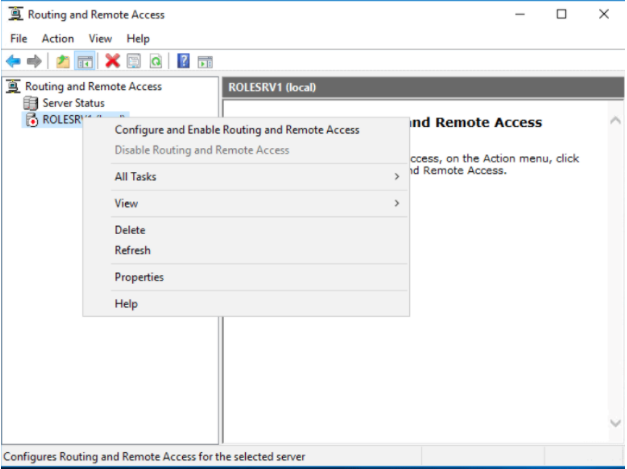
When the setup wizard opens, click Next.
If Routing is needed:
Select Custom configuration and click Next
Select LAN routing
If NAT is needed:
Select Custom configuration and click Next.
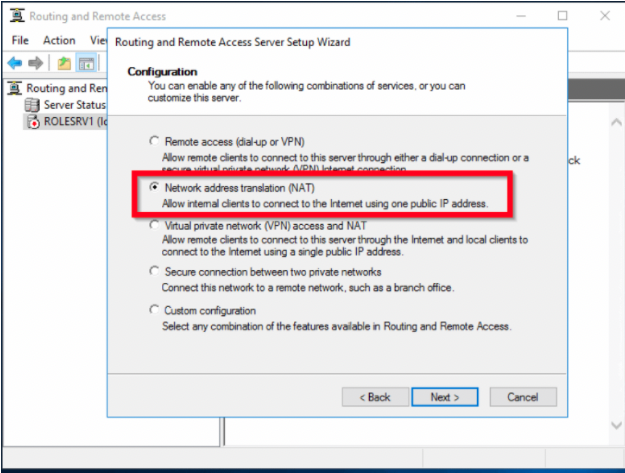
Select Lan routing.
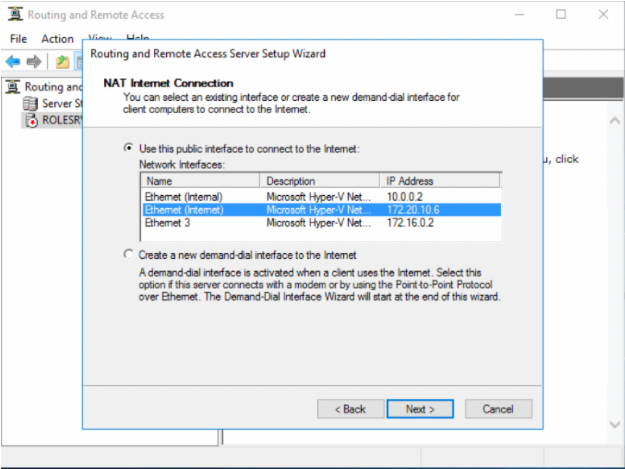
Select the network adapter that shares the internet connection (in this case Local Area Connection - TAPv9 adapter), and then click Next.
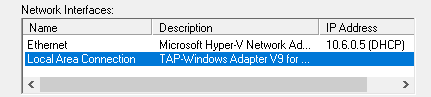
On the summary page, click Finish.
The wizard initializes and starts the RRAS service. Once the initialization completes, the server status icon changes to green.
Re-start the service/server.
Tutorial: Use OpenVPN Service Binary on Windows to Automatically Connect to CloudConnexa on Startup
This tutorial shows you how to use the OpenVPN Service binary to run as a system service. This means that if the service is properly installed and configured, it will establish an OpenVPN connection automatically on system start-up, regardless of whether it was explicitly started or not.
Introduction
Starting from the OpenVPN Connect app version 3.2, the application includes the OpenVPN Service binary that allows running an OpenVPN connection as a system service. This means that if the service is properly installed and configured it will establish an OpenVPN connection automatically on system start-up, regardless of whether it was explicitly started or not.
Follow these steps in order to do that on Windows:
Connect App Installation
Go to https://openvpn.net/client-connect-vpn-for-windows/ and click Download OpenVPN Connect V3.
Note
If you are using CloudConnexa or Access Server, you may also download OpenVPN Connect with an already existing OpenVPN Profile from the portal.
After the download has been completed, click on the set up in the Downloads pop-up bar in your browser.
In the OpenVPN Connect setup Wizard that has just opened, click Next.
Read the License Agreement and click on the I accept the terms in the License Agreement checkmark (in case you accept the terms).
Click Next.
In the Driver Selection window, choose a driver and click Next.
Click the Install button in order to begin the installation process.
Finally, click Finish in order to finish the setup process after the installation has been completed.
Starting System Service
Press Win+S on your keyboard in order to open the Search window, then type
cmdin order to find the Command Prompt.Now, click Run as Administrator in the panel on the right.
Type
cd/in the Command Prompt Window in order to go to the top of the directory tree.Next, type
cd %ProgramFiles%/OpenVPN Connect(if you are using the x64 version) orcd %ProgramFiles(x86)%>/OpenVPN Connect(if you are using the x86 version) in the Command Prompt Window in order to navigate to the default directory where OpenVPN Connect is located.Install the system service by typing the following command into the Command Prompt:
ovpnconnector.exe install.Note
The system service will not be automatically installed when you install the OpenVPN Connect app. You will still have to install the service in the Command Prompt after you have installed the app.
Optional Now, configure the OpenVPN Profile that will be running automatically with system service by typing the following command into the Command Prompt:
ovpnconnector.exe set-config Profile <path-to-Profile.ovpn>Important
Only autologin profiles are supported at the current moment. Even if the downloaded Profile has been moved to
%ProgramFiles%/OpenVPN Connect, you still have to enter the full path to the OpenVPN Profile.Note
If this step was skipped, the service will try to connect via Profile located at the service directory
namedovpnconnector.ovpn. If Connect client was downloaded from Access Server or CloudConnexa and has a bundled Profile,ovpnconnector.ovpnis a copy of a bundled Profile.Optional Specify the path to a log file by typing the following command into the Command Prompt:
ovpnconnector.exe set-config log <path-to-log>.Important
The log file will only appear in the intended directory only after the connection has been established. If there is no log file in the directory, then the connection has not been established.
Note
If not specified, the service will write logs to the file located at the same directory named
ovpnconnector.log. Apart from writing regular OpenVPN logs to the configured log file service will also report any critical errors to the system Event Viewer → Windows Logs → Applications. (Event source:OVPNConnectorService).Start the service by typing the following command into the Command Prompt:
ovpnconnector.exe start. This command will try to establish a connection via a configured Profile using system service.Important
OpenVPN Connect client should not be running, otherwise, service startup will abort.
Open the log file you specified in Step 7 or the default
%ProgramFiles%/OpenVPN Connect/ovpnconnector.login order to verify that the OpenVPN connection was successfully established. Scroll to the very end, and find the line<timestamp> EVENT: CONNECTED <OpenVPN Profile name>, which will confirm the connection's success.Important
The log file will only appear in the intended directory if the connection was successful. If there is no log file, then the connection has not been established
Notice that you can’t use OpenVPN Connect when the service is running, the application UI will be blocked by the corresponding modal window. It will disappear if you stop the service.
Notice how now, if you restart your machine, the OpenVPN connection will be established automatically on system start-up thanks to this system service, regardless of whether it was explicitly started or not.
Using System Service
You can check service status in Windows Services utility by pressing Win+S and typing Services into the Windows search bar and clicking Services in the search results.
Here, find the OpenVPN Connect 3.x Connector service in the Windows Services tab. Notice how now, if you restart your machine, the OpenVPN connection will be established automatically on system start-up thanks to this system service, regardless of whether it was explicitly stated or not.
Notice that you can stop or restart the service from this tab. If you click Stop, the OpenVPN connection will be terminated.
Important
Connection will restart automatically after the system reboot unless you remove the service.
You will also be able to start the service in case it was stopped from the Windows Services tab.
Stop and Remove System Service
You can stop the service by entering the following command into the Command Prompt:
ovpnconnector.exe stop. A OpenVPN connection will be terminated.Important
Connection will restart automatically after the system reboot unless you remove the service.
Configured paths to the connection Profile and the log file can be rolled back to default values using the following commands in the Command Prompt:
ovpnconnector .exe unset-config Profileandovpnconnector.exe unset-config log.Important
The service needs to be stopped first to change the configuration. You will be able to use a different CloudConnexa session as a system service only after running
ovpnconnector.exe unset-configProfile, as a System Service will still be present, but it won’t have the Running status in Windows Services since it will have no OpenVPN Profile associated with it. Afterward, to change the OpenVPN Profile of the system service, simply go through the steps in the section Starting System Service with a new OpenVPN Profile.If you want to remove system service run the command:
ovpnconnector.exe remove
Default Connect App settings for connection
Connection Timeout: Continuously retry (try to connect indefinitely)
Seamless Tunnel: Enabled (Block traffic while OpenVPN connection is paused or reconnecting)
The rest of the settings can be configured in the Profile itself
Tutorial: Install a Connector on Windows
This tutorial shows you how to install the OpenVPN Connect app with the bundled Connector profile on your Windows computer. The Windows computer can then be used as a Host without connecting the rest of the network to CloudConnexa or as a Network Connector making the applications on the entire network accessible.
Installing a Connector for Windows
In order to use a computer on a private Network, running Windows operating system, as a CloudConnexa Host so that CloudConnexa Users can access services running on it, follow the steps below:
Sign in to the CloudConnexa Administration portal at https://cloud.openvpn.com
Navigate to Hosts and click (+) to add a new Host.
Give the Host and Connector a name, select a Region for the Connector, and click on the checkmark icon to complete configuration.
Note
The Connector has been assigned a WPC IP Address
100.96.1.66Click on the download icon next to the Connector to show the various download options.
Click on Download Connector App for Windows option.
You can click on the Download if you want to download and install the Connector on the computer that you are working on or you can click on Copy URL button to open the URL in the browser of the target Windows computer so that the software gets downloaded directly on that computer.
Go to the Windows computer and paste the URL in the browser to start downloading the OpenVPN Connect Client and its bundled Profile. This has to be done within 15 minutes of URL generation.
Click on the downloaded installer to start the installation process.
Click on the Run button of the security warning. Note that some versions of Windows may also display a warning that the driver is not signed. Continue the installation in spite of the warning.
Click on the Next button to start the OpenVPN Connect set up Wizard.
Accept the terms in the License Agreement by clicking on the checkbox and click on the Next button.
Click on the Install button to begin the installation.
Installation progress will be shown, click on the Finish button to exit the set up Wizard.
You will see the OpenVPN Connect icon in the system tray. Launch OpenVPN Connect from your application menu.
Click on the Profile that is already present to connect to your CloudConnexa.
Optional: Windows firewall settings
If you are running any other application or service on the Host, the windows firewall needs to be configured to allow access to the service.
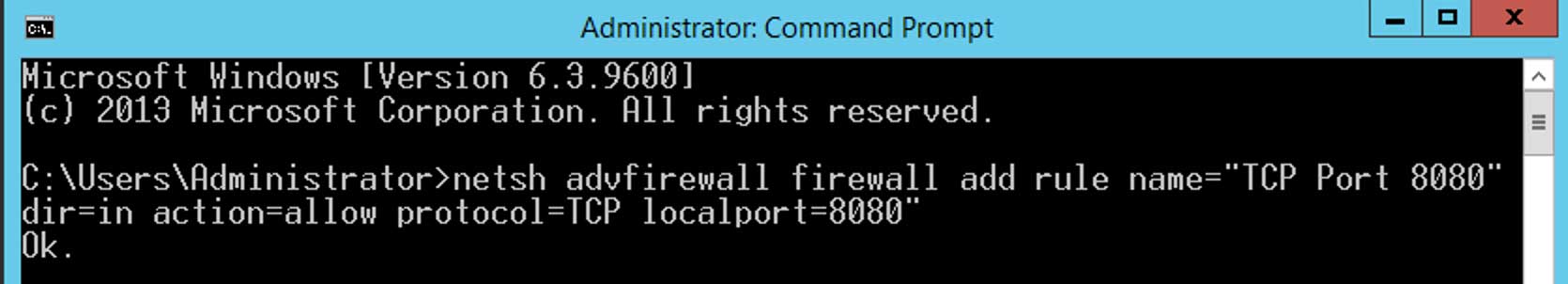
The example below shows how to allow access to a web server running on port 8080 by using netsh
netsh advfirewall firewall add rule name="TCP Port 8080" dir=in action=allow protocol=TCP localport=8080
For more on firewall configuration, see https://support.microsoft.com/en-us/help/947709/how-to-use-the-netsh-advfirewall-firewall-context-instead-of-the-netsh
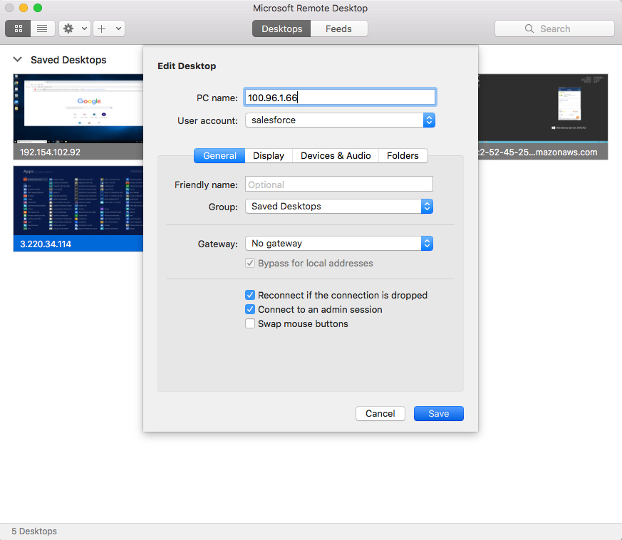
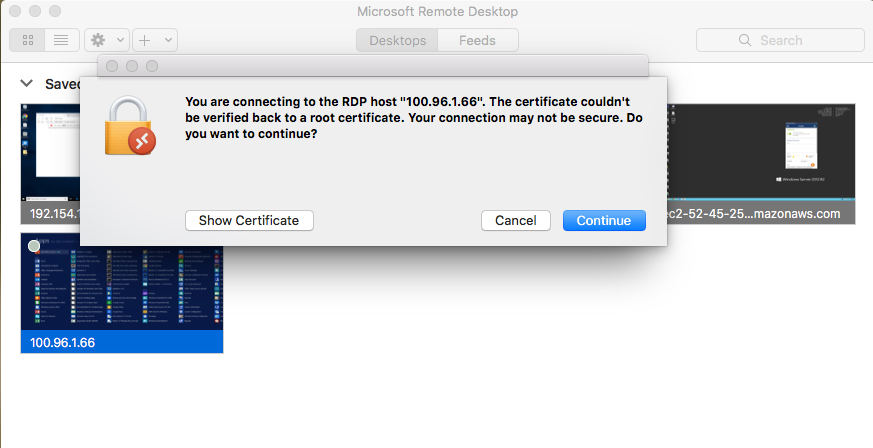
Optional: Remote desktop connection
If the Windows computer you installed the Connector on is running Remote Desktop Service, you can configure an RDP connection by using the WPC IP Address of the Connector (in this example, 100.96.1.66). The screenshots below show a macOS computer, that is connected to CloudConnexa, configuring an RDP connection and connecting to the Windows Host.
Optional: If the Connector is for a Network instead of a Host
Please see Connecting Networks to CloudConnexa Using Connectors for information on actions needed to be taken outside the scope of CloudConnexa to enable proper routing of traffic between your private Networks and WPC clients
Tutorial: Enable DCO for a Windows Connector
Data Channel Offload (DCO) improves the OpenVPN tunnel's performance by moving data packet processing from the OpenVPN userspace program to the kernel. You can enable DCO for your Windows Connector by following the steps below.
Data Channel Offload (DCO) improves the OpenVPN tunnel's performance by moving data packet processing from the OpenVPN userspace program to the kernel. You can enable DCO for your Windows Connector by following the steps below:
Note
OpenVPN Connect 3.4 and newer on Windows supports OpenVPN Data Channel Offload (DCO).
Disconnect the connection.
Navigate to Menu > Settings.
Expand Advanced Settings.
Click on the Enable DCO checkbox.
Figure 33. Screenshot of OpenVPN Connect 3.4.3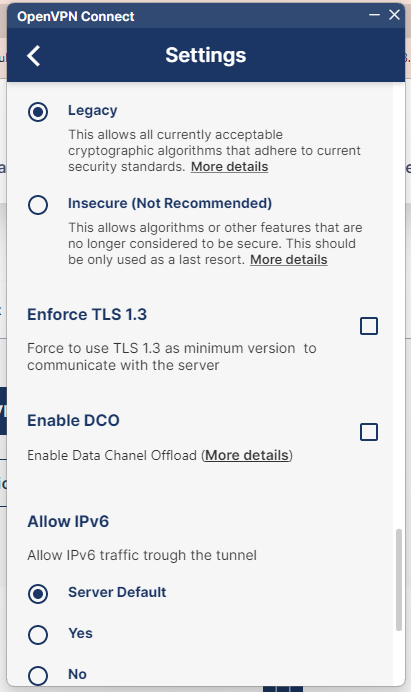
Reconnect.
macOS
Tutorial: Install a Connector on macOS
This tutorial shows you the steps to take to install a CloudConnexa Connector on macOS. You can then use the computer as a router to connect your network to CloudConnexa or as a Host to just make the services available on that computer to CloudConnexa.
To install a Connector on a private Network running macOS for a CloudConnexa Host, follow these steps:
Sign in to the CloudConnexa Administration portal at https://cloud.openvpn.com.
Access Hosts and click to add a new Host.
Give the Host and Connector a name, select a Region for the Connector, and click the checkmark to save.
Note
The Connector has been assigned a WPC IP Address
100.96.1.82Click on the download icon next to the Connector to show the various download options.
Click on Download Connector App for Mac option.
You can click on the Download button if you want to download and install the Connector on the computer that you are working on or you can click on Copy URL button to open the URL in the browser of the target macOS computer so that the software gets downloaded directly on that computer.
Go to the macOS computer and paste the URL in the browser to start downloading the OpenVPN Connect Client and its bundled Profile. This has to be done within 15 minutes of URL generation.
Click on the downloaded installer to start the installation process.
Double-click on the installer to start the installation.
Click on the Continue button.
Click on the Agree button.
Click on the Install button to begin the installation.
Installation progress will be shown.
Click on the Close button to exit the installer.
Launch the OpenVPN Connect application using Launchpad.
Click on the profile that is already present to connect to your CloudConnexa.
Optional: If the Connector is a Connector for a Network instead of for a Host
Please see Connecting Networks to CloudConnexa Using Connectors for information on actions needed to be taken outside the scope of CloudConnexa to enable proper routing of traffic between your private Networks and WPC clients
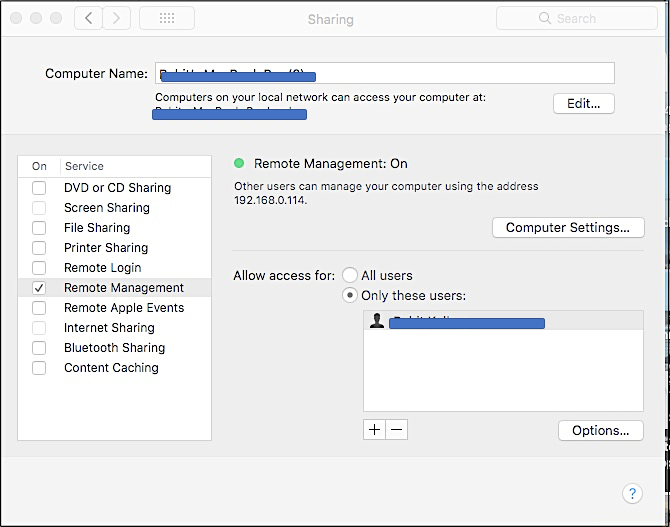
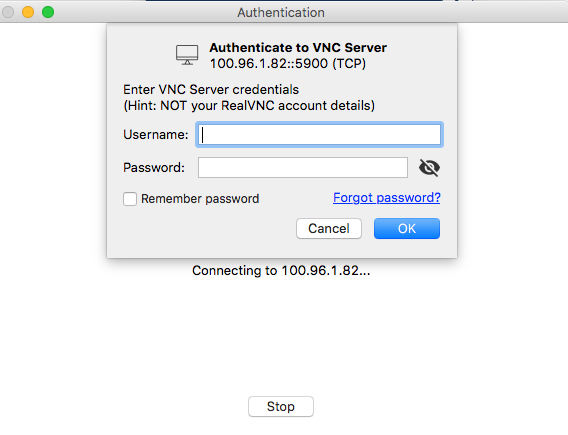
Optional: Remote Management using VNC
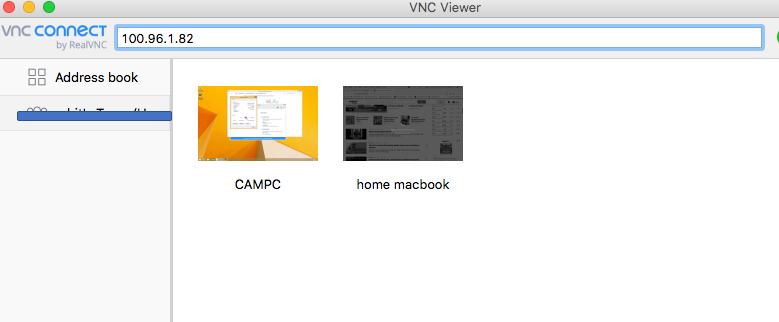
If the macOS computer you installed the Connector on has Remote Management turned ON, you can securely connect to it via CloudConnexa and VNC viewer by using the WPC IP Address of the Connector (in this example, 100.96.1.82). The screenshots below show the macOS Host being connected to using VNC Viewer
Turning Remote Management ON on the Host
CloudConnexa User remotely managing the Host by connecting to it with the Host’s WPC IP address
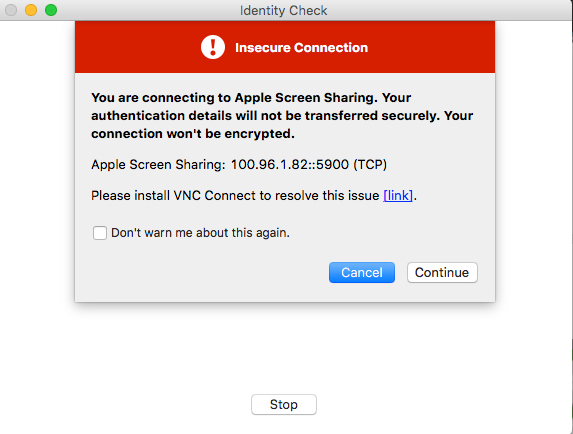
Note: While the warning is accurate about the Apple Screen Sharing connection not being secure or encrypted by the application, it can be ignored because the connection is being secured and encrypted by the use of CloudConnexa.
Tutorial: Enable routing and NAT on macOS
Follow the steps in this guide to enable routing and NAT on macOS.
Follow the steps in these two tutorials to enable routing and NAT on macOS.
Tutorial: Configure macOS Computer to be a Router
Tutorial: Configure Network Address Translation (NAT) on macOS
Tutorial: Configure Network Address Translation (NAT) on macOS
This tutorial shows you the steps to take to enable NAT on your macOS computer.
Steps: Enable NAT on macOS
Create a file titled “
pf-nat.conf” and add this rule:nat on enX from 100.96.0.0/11 to any -> enXNote
Where
enXis the main network interface of the host and100.96.0.0/11is the default WPC subnet. If the WPC subnet was changed in the CloudConnexa Portal - Settings > WPC, "please replace 100.96.0.0/11, in the command above, with the updated IPv4 WPC subnet: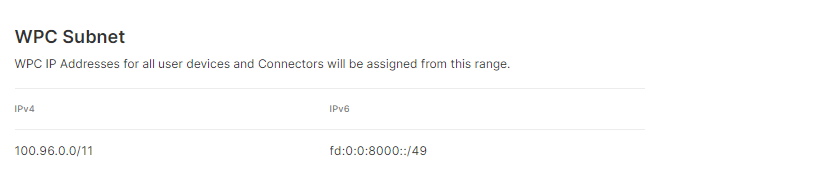
Save the pf-nat.conf file.
Start pfctl using the rule from the pf-nat.conf file.
sudo pfctl -d#disablespfctlsudo pfctl -F all#flushes allpfctlrulessudo pfctl -f /Path/to/file/pf-nat.conf -e#starts pfctl and loads the rules from thepf-nat.conffile
If you want the NAT rule to be permanent:
Create a backup of the default
pf.conffile (sudo cp -p /etc/pf.conf /etc/pf.conf.bak)Add your own rules to
/etc/pf.conf(appending them after the default Apple anchors):natonenXfrom100.96.0.0/11to any ->enXLoad your custom rules (
sudo pfctl -f /etc/pf.conf)(Re)Enable the packet filter firewall (
sudo pfctl -E)
Tutorial: Configure macOS Computer to be a Router
This tutorial shows the steps needed to configure your macOS computer to carry out routing.
Open the Terminal application and enter this command:
sysctl -w net.inet.ip.forwarding=1
Tutorial: Configure automatic login on macOS
This tutorial describes configuring your macOS computer to login automatically on restart. This will allow the OpenVPN Connect application to reconnect the OpenVPN tunnel on unscheduled restarts without requiring human intervention.
This tutorial describes configuring your macOS computer to login automatically on restart. This will allow the OpenVPN Connect application to reconnect the OpenVPN tunnel on unscheduled restarts without requiring human intervention.
It is highly recommended to setup automatic login if you have a Connector installed on your macOS computer.
Steps: Configure automatic login on macOS
Click the Apple logo.
Select System Preferences from the menu.
Click Users & Groups. In earlier versions of OS X, this is called Accounts.
Click the lock to make changes, and enter your Administrator password when prompted.
Click Login Options.
Select the Automatic login username that you want to configure.
To disable automatic login, select Off.
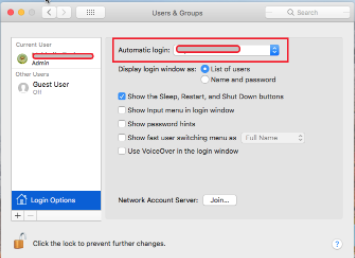
Note: If the username is grayed out, your computer requires manual login and you are unable to set up automatic login without making additional changes. Here are some possible workarounds:
If FileVault is turned on, manual login is required for all accounts. You can choose to turn FileVault off.
If an account uses an iCloud password to log in, manual login is required for that account. When changing the account password, you can choose not to use the iCloud password.
Click the lock to prevent further changes, and close System Preferences.
Linux
Tutorial: Install a Connector on Linux
This tutorial shows the steps involved in deploying a Connector on a Linux computer or VM.
Follow these steps to install a Connector for Linux:
Navigate to Networks, click Connectors, and click on the Deploy button for the Connector after it is configured and saved.
Select Deploy Connector from the dropdown list.
Click on the Provider Type dropdown list to see the list of various options and choose Linux from the Operating Systems section.
Select a distribution that corresponds to the Linux distribution you want to install the Connector on. For this example, we are using Ubuntu 22.04.
The commands to execute on the Linux computer appears.
Copy-paste the commands shown in your terminal and press the Enter key to execute the shell script.
There will be multiple times when you will be prompted with Yes/No questions. Select Yes every time.
Once all the installations are done, you will see a prompt for a set up token.
Click on the Generate Token button back on the CloudConnexa portal.
Click on the Copy icon to copy the token.
Go back to your Linux terminal and paste the token. The utility will import the Connector Profile and connect to CloudConnexa.
Click on the Next button back on the CloudConnexa portal.
The successful connection status is shown and you can click on the Finish button to exit.
Note
Refer to Using the Network Wizard for easier set up of Networks and Connecting Networks to CloudConnexa Using Connectors for information on actions that need to be taken outside of the scope of CloudConnexa to enable proper routing of traffic between your private Networks and WPC clients.
Tutorial: Learn to Install and Control the OpenVPN 3 Client
This tutorial shows how to install the OpenVPN 3 client on various Linux distributions. In addition, commands to control the client are documented.
OpenVPN 3 Client for Linux
General reference guide for installing and operating openvpn3 client on various Linux distributions.
Note
This document is a reference for the OpenVPN 3 Linux client. CloudConnexa Connector for Linux uses OpenVPN 3. Deploying Connector for CloudConnexa is covered separately here.
The OpenVPN 3 Linux project is a new client built on top of the OpenVPN 3 Core Library, which is also used in the various OpenVPN Connect clients. For more information on the project, refer to the Community Wiki.
This client is built around a completely different architecture regarding usage. It builds heavily on D-Bus and allows unprivileged users to start and manage their own VPN tunnels out-of-the-box. System Administrators wanting more control can also control and restrict this access both by hardening the default OpenVPN 3 D-Bus policy or facilitating features in OpenVPN 3 Linux.
Even though the project name carries “Linux,” it doesn’t mean it is restricted to Linux only. Any platform with D-Bus available should be capable of running this client theoretically. However, since D-Bus is most commonly used in Linux environments, this will naturally be the project's primary focus.
The release notes are stored in git tags in the project git repository. They can also be viewed here: https://github.com/OpenVPN/openvpn3-linux/releases (expand the tag to see the full text).
Distribution | Release | Release Name ($DISTRO) | Architecture | ||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Debian | 12 | bookworm | amd64, arm64[a] | ||||||||||||||||||||||||||||||||||||||||||||||
Debian | 13 | trixie | amd64, arm64[a] | ||||||||||||||||||||||||||||||||||||||||||||||
Fedora[b] | - | - | Recent stable releases | ||||||||||||||||||||||||||||||||||||||||||||||
Red Hat Enterprise Linux | 8 | - | |||||||||||||||||||||||||||||||||||||||||||||||
Red Hat Enterprise Linux | 9 | - | |||||||||||||||||||||||||||||||||||||||||||||||
Red Hat Enterprise Linux | 10 | - | |||||||||||||||||||||||||||||||||||||||||||||||
Ubuntu | 22.04 | jammy | amd64, arm64[a] | ||||||||||||||||||||||||||||||||||||||||||||||
Ubuntu | 24.04 | noble | amd64, arm64[a] | ||||||||||||||||||||||||||||||||||||||||||||||
Ubuntu | 25.04 | plucky | amd64, arm64[a] | ||||||||||||||||||||||||||||||||||||||||||||||
[a] ARM64/aarch64 architectures are in tech preview. [b] We support the most recent stable Fedora releases. Fedora release cadence information. [c] These aren't fully supported; they are only available via the Fedora Copr repositories. Consider them tech-preview. | |||||||||||||||||||||||||||||||||||||||||||||||||
Follow these steps to install OpenVPN 3 Client on Linux for Debian and Ubuntu:
Open the Terminal by pressing
ctrl + alt + Tand run the following commands in it.Install the OpenVPN repository key used by the OpenVPN 3 Linux packages:
sudo mkdir -p /etc/apt/keyrings && curl -fsSL https://packages.openvpn.net/packages-repo.gpg | sudo tee /etc/apt/keyrings/openvpn.asc
Run this command to obtain the Linux distribution-specific information and assign it to the
DISTROvariable for use in the next step:DISTRO=$(lsb_release -c -s)
Important
We recommend that you're cautious about the distribution and release you are running. Distribution and version should preferably be retrieved using the
hostnamectlcommand, where the User needs to link the Operating System field with the table of the supported distribution.Install the proper repository:
echo "deb [signed-by=/etc/apt/keyrings/openvpn.asc] https://packages.openvpn.net/openvpn3/debian $DISTRO main" | sudo tee /etc/apt/sources.list.d/openvpn-packages.list
Fetch the latest package information:
sudo apt update
Install the OpenVPN 3 package:
sudo apt install openvpn3
Packages for these distributions are provided via a Fedora Copr repository. For supported release versions, refer to the table above.
To install the OpenVPN 3 Client for Fedora, Red Hat Enterprise Linux, AlmaLinux, or Rocky Linux:
Open Terminal by typing Terminal into the search bar.
For Red Hat Enterprise Linux, install the Fedora EPEL repository:
RHEL 8:
sudo yum localinstall https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
And enable the
codeready-builder-for-rhel-8-${ARCH}-rpmsrepository because some EPEL packages may depend on it:sudo subscription-manager repos --enable "codeready-builder-for-rhel-8-$(/bin/arch)-rpms"
RHEL 9:
sudo yum localinstall https://dl.fedoraproject.org/pub/epel/epel-release-latest-9.noarch.rpm
Rocky/Alma:
sudo yum install epel-release
Rocky 8 / Alma 8: And enable the PowerTools repository because some EPEL packages may depend on it:
sudo yum config-manager --set-enabled powertools
Install the OpenVPN 3 repository:
RHEL, AlmaLinux, and Rocky Linux:
sudo yum install -y https://packages.openvpn.net/openvpn-openvpn3-epel-repo-1-1.noarch.rpm
Fedora:
sudo yum copr enable dsommers/openvpn3
Install the OpenVPN 3 Linux client:
RHEL, AlmaLinux, Rocky Linux, and Fedora:
sudo yum install openvpn3-client
Please note that by this point, you should have downloaded a .ovpn connection profile to your machine.
Run these list items:
Download a connection profile and import it into the Configuration Manager:
openvpn3 config-import --config /file/to/profile.ovpn --name CloudConnexa1 --persistent2
This stores the file under the name CloudConnexa.
This flag ensures the connection profile is preserved when the system reboots.
Tip
This command can be run by an ordinary, unprivileged user on the system; the user who runs this command becomes the owner of the configuration profile.
Grant the root user access to the imported CloudConnexa connection profile:
openvpn3 config-acl --show --lock-down true1 --grant root --config CloudConnexa
The --lock-down true argument is optional, but restricts the root user from extracting the contents of the connection profile via the openvpn3 commands (or via D-Bus APIs).
By adding --transfer-owner-session true to the command above, the current User running this command (the owner of the Profile) also becomes the “VPN session owner” if the root is the User starting the VPN session (typically via the systemd openvpn3-session@.service).
sudo systemctl enable --now openvpn3-session@CloudConnexa.serviceThis tells systemd to enable an OpenVPN session service (openvpn3-session) to be started when the system is booting, using the configuration profile name CloudConnexa. The --now argument also instructs systemd to start the session instantly.
Start the VPN session and create the necessary symlinks in system directories to ensure the service starts whenever the system reboots:
sudo systemctl enable --now1 openvpn3-session2@CloudConnexa3.service
At this point, the OpenVPN session can be managed via either the systemctl command using the openvpn3-session@CloudConnexa.service or using the openvpn3 session-manage, openvpn3 session-acl and openvpn3 sessions-list commands.
If the connection profile ACL has --transfer-owner-session enabled, the end-user can also manage the VPN session completely without needing root privileges.
To start a one-shot configuration Profile, type the following command into the Terminal:
openvpn3 session-start --config ${MY_CONFIGURATION_FILE}Important
A one-shot configuration Profile means that the configuration file is parsed, loaded, and deleted from the configuration manager as soon as the VPN session has been started. No configuration file is available for re-use after this approach. This is achieved by giving the configuration file to the
openvpn3 session-startcommand directly.To import a configuration file for re-use and start a VPN session, type the following command into the Terminal:
openvpn3 config-import --config ${MY_CONFIGURATION_FILE}Note
Using this approach, an imported configuration file can be used several times, and access to the configuration file itself is not needed to start VPN tunnels. By default, configuration profiles imported are only available to the User who imported the configuration file. But OpenVPN 3 Linux also provides an Access Control List feature via
openvpn3 config-aclto grant access to specific or all users on the system.Important
This loads the configuration Profile and stores it in memory only. That means if the system is rebooted, the configuration Profile is not preserved. If the –persistent argument is added to the command line above, the configuration Profile will be saved to disk in a directory only accessible by the User. Whenever the Configuration Manager is started, configuration files imported with –persistent will be automatically loaded as well.
To start a new VPN session from an imported configuration Profile, run the following command:
openvpn3 session-start --config ${CONFIGURATION_PROFILE_NAME}Note
When a configuration Profile is available via
openvpn3 configs-list, it can quickly be started viaopenvpn3 session-startusing the configuration Profile name (typically the filename used during the import)
To list all available configuration profiles, run this command:
openvpn3 configs-list
Important
A configuration file typically contains generic options to connect to a specific server, regardless of the Device itself. OpenVPN 3 Linux also supports setting more Host-specific settings on a configuration Profile. This is handled via the openvpn3 config-manage interface. Any settings here will also be preserved across boots if the configuration Profile was imported with the --persistent argument.
Note that it is possible to use the D-Bus path to the configuration Profile:
openvpn3 session-start --config-path /net/openvpn/v3/configuration/..
Note
In either of these cases, it is necessary to have access to the configuration Profile on disk. As long as configuration profiles are available via
openvpn3 configs-list, all needed to start a VPN session should be present.
Once a VPN session has started, it should be seen in the session list:
openvpn3 sessions-list
Using the
openvpn3 session-manage, a few things can be done, but most typically, the--disconnector--restartalternatives are most commonly used.Use the D-Bus path to the session. Disconnect a running session:
openvpn3 session-manage --session-path /net/openvpn/v3/sessions/..... --disconnect
Important
You can start a new session with this or another OpenVPN Profile only after disconnecting from the current session using the command in this listitem.
Once this operation has been completed, it will be removed from the
openvpn3 sessions-listoverview.
Retrieve real-time tunnel statistics from running sessions:
openvpn3 session-stats --config ${CONFIGURATION_PROFILE_NAME}or
openvpn3 session-stats --session-path /net/openvpn/v3/sessions/...
Retrieve real-time log events as they occur:
openvpn3 log --config ${CONFIGURATION_PROFILE_NAME}This might be quite silent, as it does not provide any log events from the past. Issue an
openvpn3 session-manage --restartfrom a different terminal, and log events will occur. You may want to boost the log-level with –log-level 6. Valid log levels are from 0 to 6, where 6 is the most verbose.Note
VPN sessions are also owned by the User who started them. But the Session Manager also provides its own Access Control List feature via
openvpn3 session-acl
Note
This section is valid only for RHEL-7. Please refer to Using .ovpn Profile for all other distributions.
Please note that every time you start a session, it will load automatically on the system start-up. To change the Profile of a VPN Session that is autoloaded, follow the list items below:
Run the command:
sudo openvpn3 sessions-list. It will show information about your active session. Check the value of the Path parameter.Run the command:
sudo openvpn3 session-manage --session-path YOUR_PATH --disconnect, where YOUR_PATH is the value of the Path parameter from list item 1.Run the command:
sudo openvpn3 sessions-list.You shouldn’t see any active sessions.Run the command:
sudo openvpn3 configs-list. It will show information about your active configurations. Check the name assigned to your active config.Run the command:
sudo openvpn3 config-remove --config "YOUR_CONFIG_NAME", where YOUR_CONFIG_NAME is the name of the configuration file from list item 4. You will be asked to confirm the removal of the configuration. Type YES (in uppercase) to confirm.Run the command:
sudo openvpn3 configs-list. You shouldn’t see any active configurations.Run the command:
sudo nano /etc/openvpn3/autoload/Connector.conf. This is the Profile that will be replaced.Press Ctrl + End, then hold ctrl + shift + ↑ until the whole file is highlighted, and finally, press ctrl + K.
Open the Profile you wish to use instead of the existing one. Press Ctrl + A and then ctrl + C.
Then go back to the Terminal, press the right mouse button, and choose Paste. Notice the difference between the old and the new Profile.
Once you’ve replaced the Profile, press ctrl + X and confirm changes by typing y and pressing Enter.
You can run cat /etc/openvpn3/autoload/Connector.conf to check the changes are saved.
Run the command:
sudo openvpn3 config-import --config /etc/openvpn3/autoload/Connector.conf --name "YOUR_CONFIG_NAME"Run the command:
sudo openvpn3 session-start --config "YOUR_CONFIG_NAME."Run the command:
sudo openvpn3 sessions-list. It will show that a new session is active and connected.Restart the computer and check if the autostart Profile has indeed been changed. Just run the
sudo openvpn3 sessions-listcommand once again. Certainly, the autoload is now set for the new Profile!
Tutorial: Enable DCO for a Linux Connector
Data Channel Offload (DCO) improves the OpenVPN tunnel's performance by moving data packet processing from the OpenVPN userspace program to the kernel. You can enable DCO for your Linux Connector by following the steps below.
Data Channel Offload (DCO) improves the OpenVPN tunnel's performance by moving data packet processing from the OpenVPN userspace program to the kernel. You can enable DCO for your Linux Connector by following the steps below:
Note
${CONFIGURATION_PROFILE_NAME} needs to be substituted with the configuration profile name (typically the filename used during the configuration profile import) in use. Use openvpn3 configs-list to display the list of configuration profiles. For more information on OpenVPN 3 commands, refer to Tutorial: Learn to Install and Control the OpenVPN 3 Client and the Community Wiki.
Install the DCO kernel module for Ubuntu.
sudo apt install kmod-ovpn-dco
Disconnect the running OpenVPN tunnel.
sudo openvpn3 session-manage -c ${CONFIGURATION_PROFILE_NAME} --disconnectAdd DCO to the configuration profile.
sudo openvpn3 config-manage --show --config ${CONFIGURATION_PROFILE_NAME} --dco trueStart the tunnel with the DCO option.
sudo openvpn3 session-start -c ${CONFIGURATION_PROFILE_NAME} --dco true
Tutorial: Use the Linux OpenVPN 3 Connector integrated with Cockpit
We have extended Cockpit with an add-on to provide a web-based graphical frontend to the Linux OpenVPN 3 client that acts as the CloudConnexa Connector
Cockpit is a web-based graphical interface for servers that facilitates system administration. It lets you see your Linux server in a web browser and perform system tasks with a mouse.
We have extended Cockpit with an add-on to provide a web-based graphical frontend to the Linux OpenVPN 3 client that acts as the CloudConnexa Connector. Refer toGitHub.
Installation
On some IaaS Marketplaces, there are CloudConnexa Connector listings that have a readymade image to use to spin up an instance. For example, Google Cloud Platform.
Or, you can install it manually on a Linux computer using the instructions shown on GitHub.
Import Profile and Connect
Open your web browser to
https://IP_ADDRESS_OF_MACHINE:9090and login with the username and password of any local account on the system.Click OpenVPN Connector from the Navigation.
From the CloudConnexa Administration Portal, click Copy .ovpn Profile Token from the Deploy drop-down menu for the Host or Network Connector that will be deployed on this Linux machine.
Paste the token in the Cockpit Token field.
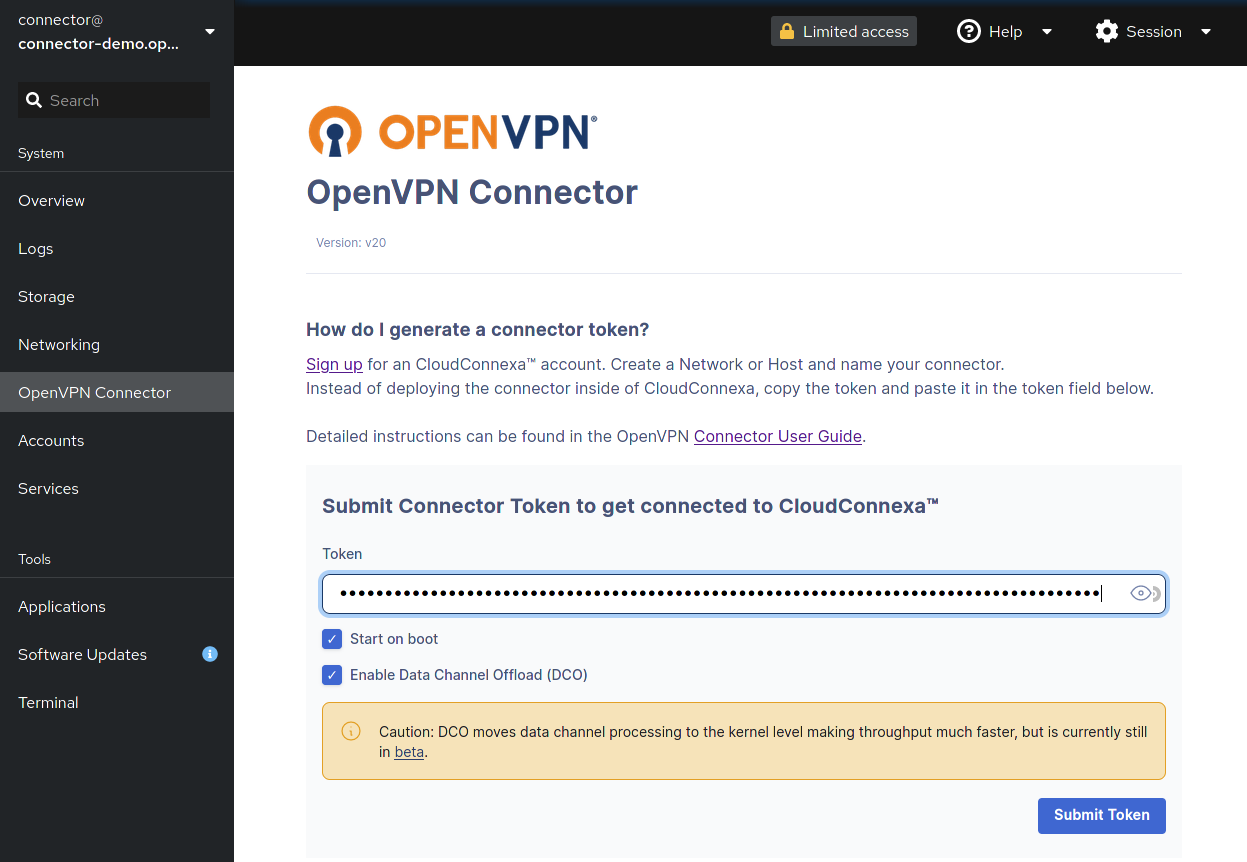
When checked, Enable Data Channel Offload (DCO) improves Connector performance by moving the data channel process to the kernel.
Click Submit Token.
Click Connect.
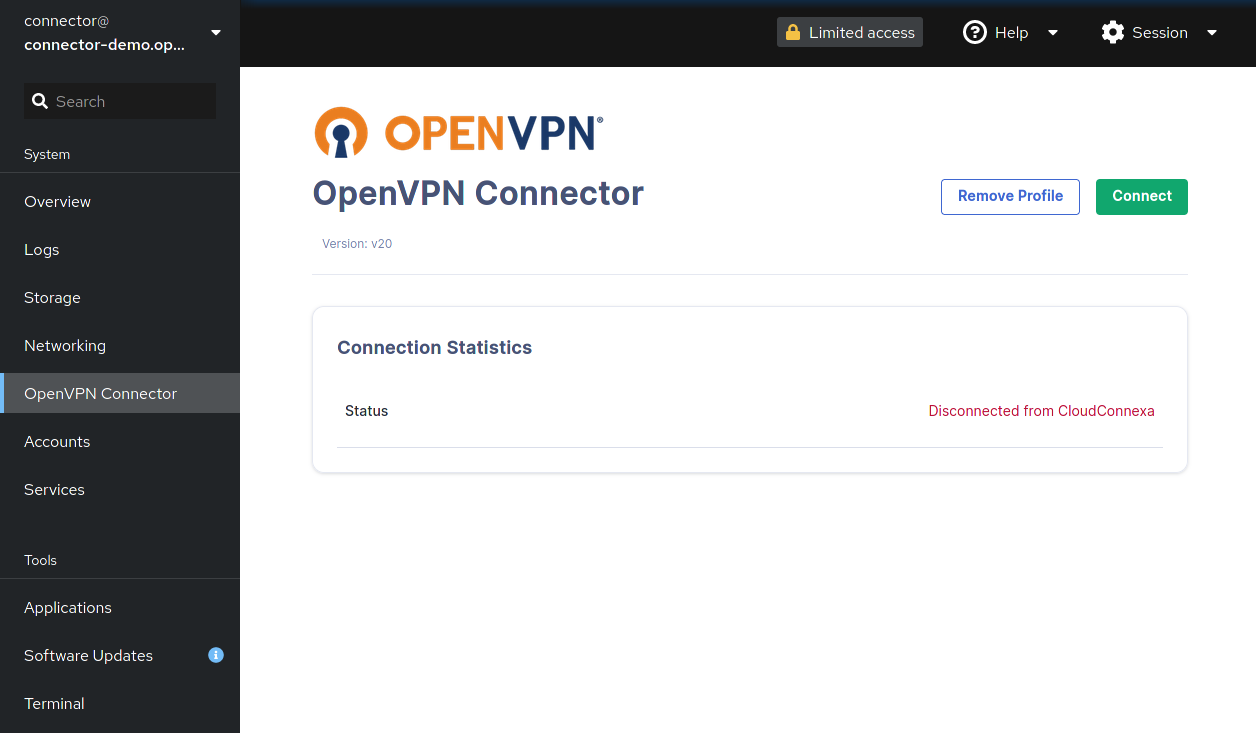
Connection Statistics
On successful connection, the connection statistics will be shown.
Connection Statistics | Definition |
|---|---|
Bytes IN | encrypted bytes since the session started received outside the OpenVPN tunnel by the client from the server |
Bytes OUT | encrypted bytes since the session started sent outside the OpenVPN tunnel by the client to the server |
Packets IN | encrypted packets since the session started received outside the OpenVPN tunnel by the client from the server |
Packets OUT | encrypted packets since the session started sent outside the OpenVPN tunnel from the client to the server |
TUN bytes IN | unencrypted bytes since the session started received within the OpenVPN tunnel by all hosts connected to the same WPC |
TUN packets IN | unencrypted bytes since the session started sent within the OpenVPN tunnel by all hosts connected to the same WPC |
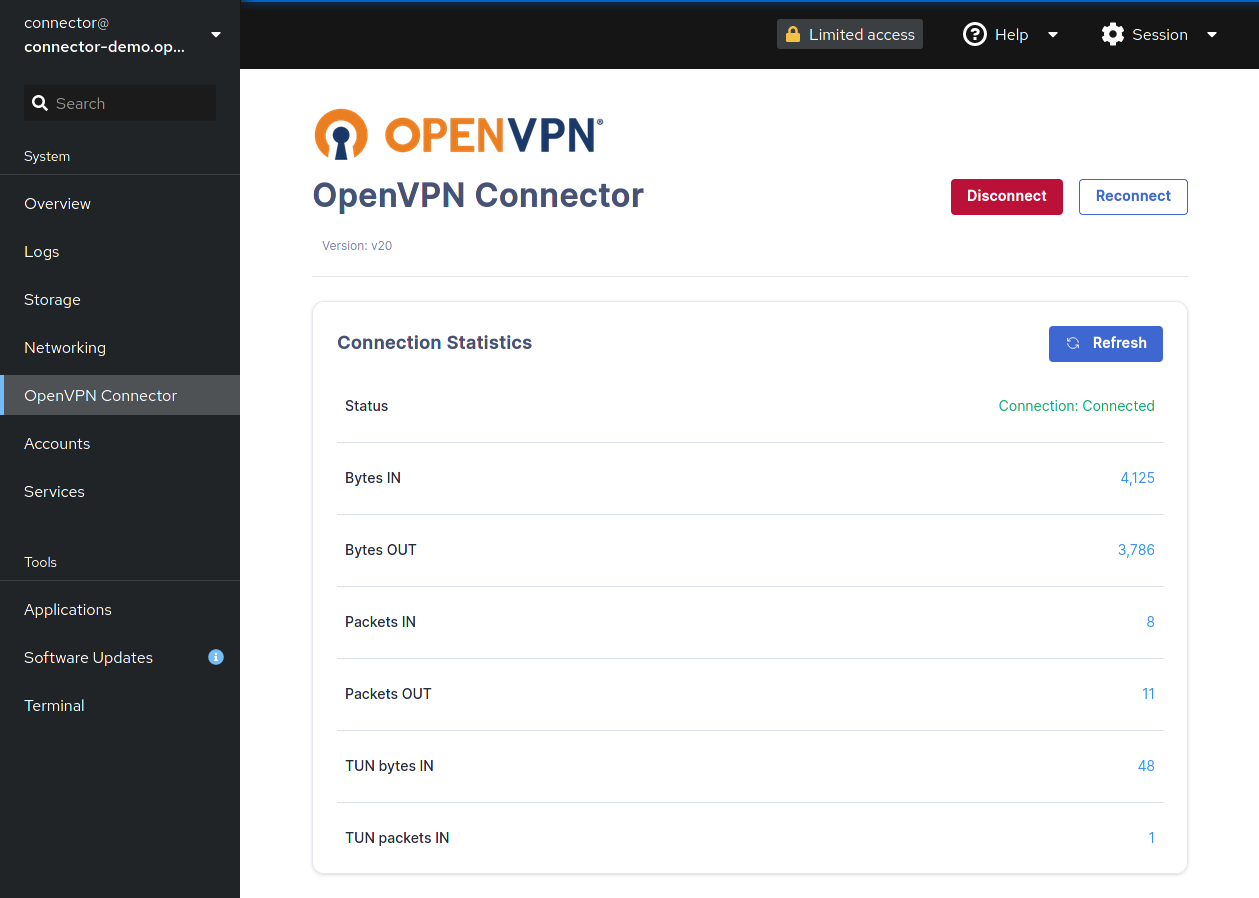
The statistics page also has action buttons:
Button | Action |
|---|---|
 | Refreshes current session |
 | Disconnects current session NoteTo restart the Connector session, you must regenerate a Connector profile token. |
 | Reconnects session NoteUsed in case of timeout or other issues during the current session. Reconnects with current profile token. |
Remove Profile
Disconnect the session if ongoing.
Click Remove Profile.
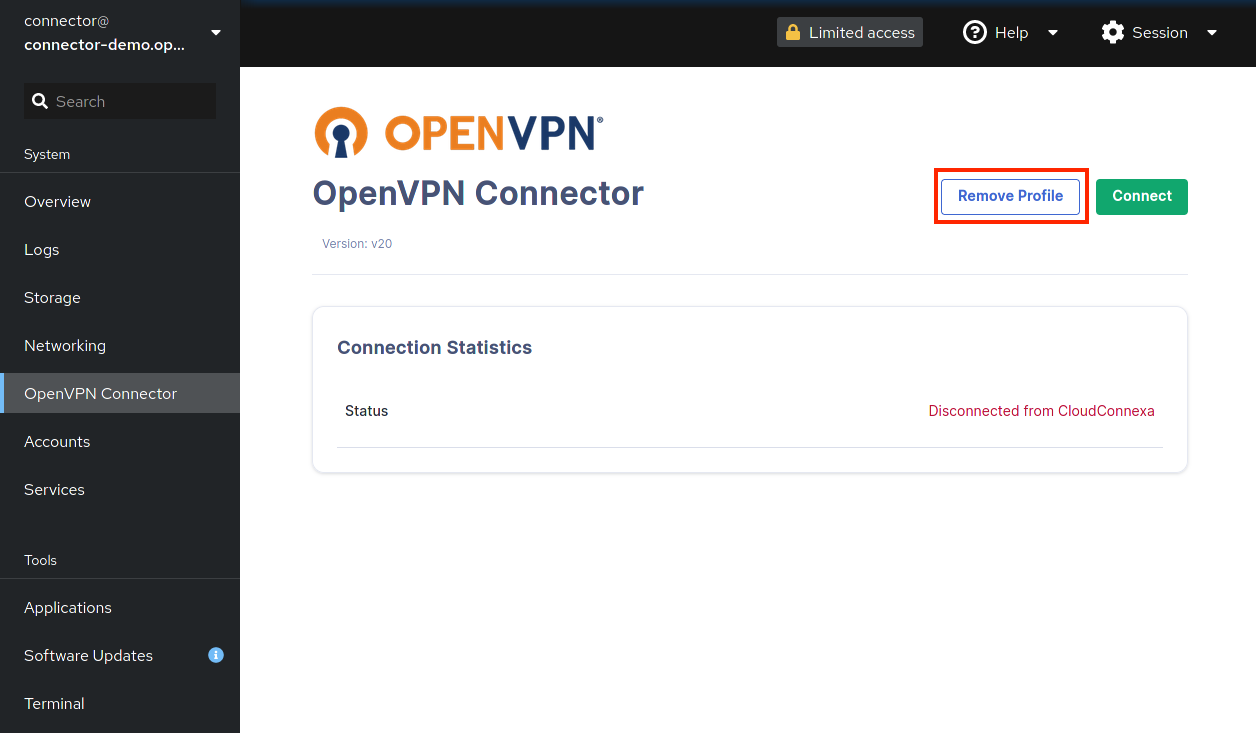
In the confirmation dialog, click Delete Profile.
Tutorial: Enable routing and NAT on Linux
The scripts generated for the various Linux distributions for Network Connectors already have the commands included for enabling NAT and routing. These instructions are mainly for informational purposes.
The scripts generated for the various Linux distributions for Network Connectors already have the commands included for enabling NAT and routing. These instructions are mainly for informational purposes.
Routing on Linux
Note
The templates and scripts used for deploying Connectors on Linux, IaaS, and Virtual Private Servers from the Administration Portal include the needed commands for NAT and IP forwarding by default.
To enable IPv4 forwarding, use the following commands on the command line:
sudo sed -i 's/#net.ipv4.ip_forward=1/net.ipv4.ip_forward=1/g' /etc/sysctl.conf sudo sysctl -p
To enable IPv6 forwarding
sudo sed -i 's/#net.ipv6.conf.all.forwarding=1/net.ipv6.conf.all.forwarding=1/g' /etc/sysctl.conf sudo sysctl -p
This will enable forwarding in the Linux kernel.
NAT on Linux
Note
The templates and scripts used for deploying Connectors on Linux, IaaS, and Virtual Private Servers from the Administration Portal include the needed commands for NAT and IP forwarding by default.
Use the following commands on the command line:
sudo apt install iptables-persistent
IF=`ip route | grep default | awk '{print $5}'`
sudo iptables -t nat -A POSTROUTING -o $IF -j MASQUERADE
sudo iptables-save | sudo tee /etc/iptables/rules.v4
sudo ip6tables -t nat -A POSTROUTING -o $IF -j MASQUERADE
sudo iptables-save | sudo tee /etc/iptables/rules.v6 The iptables rule uses the NAT packet matching table (-t nat) and specifies the built-in POSTROUTING chain for NAT (-A POSTROUTING) on the external networking Device (-o $IF). The variable ‘IF’ stores the default interface. POSTROUTING allows packets to be altered as they are leaving the Connector instance. The -j MASQUERADE target is specified to mask the private IP address of a node with the IP address assigned to the default interface.
The above is sufficient if you are fine with all traffic being NATted. However, if you need Hosts on the Network to distinguish between different WPC clients or Connectors, you need to use “! -d xx.xx.xx.xx/xx” in the NAT rule where xx.xx.xx.xx/xx is the subnet of the target LAN subnet, otherwise traffic to that subnet will also be NATted. The example below shows how to use the iptables command so that NAT is not used if the destination is in the 10.10.0.0/16 subnet.
sudo iptables -t nat -A POSTROUTING -o $IF ! -d 10.10.0.0/16 -j MASQUERADE