IaaS
Tutorial: Connect AWS to CloudConnexa with IPsec using VPG
This tutorial shows how to configure an IPsec connection to your AWS VPC. Once configured, site-to-site IPsec tunnel(s) connects your AWS VPC to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the AWS VPC.
By default, instances you launch into an Amazon VPC can't communicate with your own (remote) network. You can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection and configuring routing to pass traffic through the connection. Although VPN connection is a general term, in this documentation, a VPN connection refers to the connection between your VPC and your own on-premises network. Site-to-Site VPN supports Internet Protocol security (IPsec) VPN connections.
This tutorial shows how to configure an AWS Site-to-Site VPN connection between your AWS VPC and a CloudConnexa Region.
The AWS configuration involves:
Creating a customer gateway: The customer gateway is an AWS resource that provides information to AWS about the physical device or software application on your side of the Site-to-Site VPN connection (i.e., CloudConnexa Region).
Creating a virtual private gateway: A virtual private gateway is the VPN endpoint on the Amazon side of your Site-to-Site VPN connection that can be attached to a single VPC.
Caution
An IPsec VPN connection to your VPC using the Virtual Private Gateway (VPG) only allows access to resources inside a VPC. Use the Transit Gateway configurationUse this Transit Gateway configuration if you have configured public resources as Applications and IP services to be reachable via this VPC. Refer to Tutorial: Connect AWS VPC to CloudConnexa with IPsec using Transit Gateway.
Creating a VPN connection: An encrypted link where data can pass from the customer network (i.e., CloudConnexa) to or from AWS. Each VPN connection includes two VPN tunnels, which you can simultaneously use for high availability.
Downloading the VPN Configuration File: The configuration file is an example of VPN settings. It also specifies pre-shared keys for authentication.
On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the AWS VPC.
Add a Network using the Network Configuration Wizard to represent your AWS VPC and select the IPsec Tunneling Protocol option.
In the Connector configuration step, select AWS from the Platform to Connect drop-down menu. Refer to CloudConnexa Connectors and About Network Connectors.
Instructions will appear on how to configure IPsec connectivity with CloudConnexa.
Click Next.
You will see three steps:
AWS Configuration Details: Use these values when configuring the AWS tunnel.
Setup CloudConnexa Tunnel: Complete the CloudConnexa tunnel setup manually or automatically using the configuration file generated by AWS.
Verify Connectivity: After configuring the tunnel on both sides, click “Test Connection” to check that CloudConnexa can establish a connection to the remote network
(AWS) Create a Customer Gateway in AWS to represent the IPsec endpoint of the CloudConnexa Region. Refer to AWS Documentation.
Note
You can also create the customer gateway while configuring the VPN connection.
Open the Amazon VPC console at https://console.aws.amazon.com/vpc/.
In the navigation pane, choose Customer gateways.
Choose Create customer gateway.
(Optional) For Name tag, enter a name for your customer gateway. Doing so creates a tag with a key of Name and the value that you specify.
For BGP ASN, enter a Border Gateway Protocol (BGP) Autonomous System Number (ASN) for your customer gateway.
Note
The IPsec VPN is going to use static routing. Therefore, the BGP ASN does not matter here. You can enter any number here.
For IP address, enter the IP address displayed as Remote Gateway IP Address on the CloudConnexa Administration Portal's Connector Configuration page as shown in AWS Configuration Details .
(Optional, use only if you want to use certificate authentication instead of pre-shared keys) For Certificate ARN, choose the private certificate's Amazon Resource Name. For information about creating a private certificate, see Creating and managing a private CA in the AWS Private Certificate Authority User Guide.
(Optional) For Device, enter a name for the customer gateway device associated with this customer gateway.
Choose Create customer gateway.
(AWS) To establish an IPsec VPN connection between your VPC and CloudConnexa, you must create a target gateway on the AWS side of the connection. The target gateway will be a virtual private gateway. To create a virtual private gateway in AWS and attach it to your VPC, follow these steps:
In the navigation pane, choose Virtual private gateways.
Choose Create virtual private gateway.
(Optional) For Name tag, enter a name for your virtual private gateway. Doing so creates a tag with a key of Name and the value that you specify.
For Autonomous System Number (ASN), keep the default selection, Amazon default ASN, to use the default Amazon ASN.
Choose Create virtual private gateway.
Select the virtual private gateway you created, then choose Actions, Attach to VPC.
For Available VPCs, choose your VPC and then choose Attach to VPC.
(AWS Optional) If you want instances in your AWS VPC to reach other networks connected to CloudConnexa (i.e, site-to-site connectivity between your VPC and other private networks connected to CloudConnexa), enable route propagation for your route table to propagate Site-to-Site VPN routes automatically. This will configure your route table to include the routes used by your VPN connection and point them to your virtual private gateway when the status of the VPN connection is UP. Follow the steps below:
In the navigation pane, choose Route tables.
Select the route table that's associated with the subnet.
On the Route propagation tab, choose Edit route propagation. Select the virtual private gateway that you created in the previous procedure, and then choose Save.
(AWS) Now that both the customer gateway (representing CloudConnexa IPsec endpoint) and virtual private gateway (representing the AWS VPC IPsec endpoint) is configured and created, you are ready to create the VPN connection by following the steps below:
In the navigation pane, choose Site-to-Site VPN connections.
Choose Create VPN connection.
(Optional) For Name tag, enter a name for your VPN connection. Doing so creates a tag with a key of Name and the value that you specify.
For Target gateway type, choose Virtual private gateway. Then, choose the virtual private gateway that you created earlier.
For Customer gateway, select Existing, then choose the customer gateway that you created earlier from Customer gateway ID.
Select Static as the routing option.
For Static IP Prefixes, copy and paste the Static IP Prefixes displayed on the CloudConnexa Administration Portal's Connector Configuration page as shown in AWS Configuration Details .
Note
The Static IP Prefixes include the Routes of all CloudConnexa Networks configured so far. If you add new Networks or Routes and want site-to-site networking with your VPC, you must update the Static IP Prefixes.
Choose Create VPN connection. It might take a few minutes to create the VPN connection.
(AWS) Download the VPN connection configuration file needed to configure CloudConnexa's IPsec connection by following the steps below:
Open the Amazon VPC console at https://console.aws.amazon.com/vpc/.
In the navigation pane, choose Site-to-Site VPN connections.
Select your VPN connection and choose Download configuration.
Choose Generic for the customer gateway device.
Choose Download.
Note
To properly load the download configuration screen from the AWS Management Console, you must ensure that your IAM role or user has permission for the following Amazon EC2 APIs:
GetVpnConnectionDeviceTypesandGetVpnConnectionDeviceSampleConfiguration.Now that you have the configuration file from AWS, upload it to configure the IPsec tunnels to CloudConnexa.
To use the file to configure CloudConnexa automatically, Click Upload Generic Configuration File and select the file.
Note
AWS creates two parallel tunnels by default for redundancy and high availability. Two CloudConnexa Connectors, one for each IPsec tunnel, will be created .
Click Test Connection 1 and Test Connection 2 to check connectivity for both the IPsec tunnels.
Continue with the network wizard instructions.
Tutorial: Connect AWS VPC to CloudConnexa with IPsec using Transit Gateway
This tutorial shows how to configure an IPsec connection to your AWS VPC using the Transit Gateway. Once configured, site-to-site IPsec tunnel(s) connects your AWS VPC to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the AWS VPC.
By default, instances you launch into an Amazon VPC can't communicate with your own (remote) network. You can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection and configuring routing to pass traffic through the connection. Although VPN connection is a general term, in this documentation, a VPN connection refers to the connection between your VPC and your own on-premises network. Site-to-Site VPN supports Internet Protocol security (IPsec) VPN connections.
This tutorial shows how to configure an AWS Site-to-Site VPN connection using a Transit Gateway between your AWS VPC and a CloudConnexa Region.
An IPsec VPN connection to your VPC using the Virtual Private Gateway (VPG) only allows access to resources inside a VPC. Refer to Tutorial: Connect AWS to CloudConnexa with IPsec using VPG. Use this Transit Gateway configuration if you have configured public resources as Applications and IP services to be reachable via this VPC. The virtual private gateway provides connectivity to a single Amazon Virtual Private Cloud (Amazon VPC) in a Region. The transit gateway provides connectivity to multiple Amazon VPCs in a region as well as to the internet.
This configuration guide is based on the AWS knowledge center article: How do I access the internet using Site-to-Site VPN in my on-premises network?
For this configuration, the steps are explained using an example VPC (10.0.0.0/16) with two subnets: a public subnet (10.0.0.0/20) and a private subnet (10.0.16.0/20).
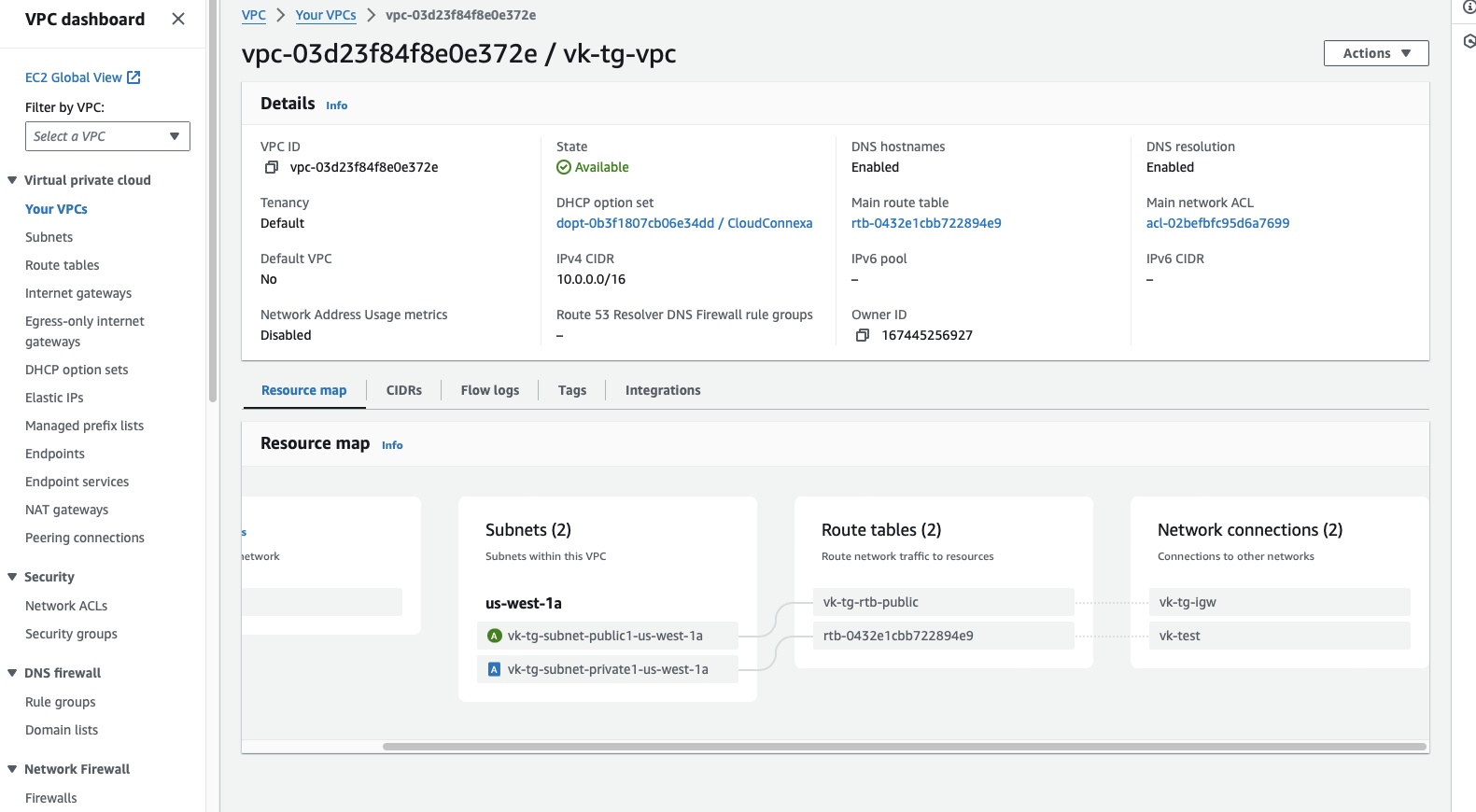
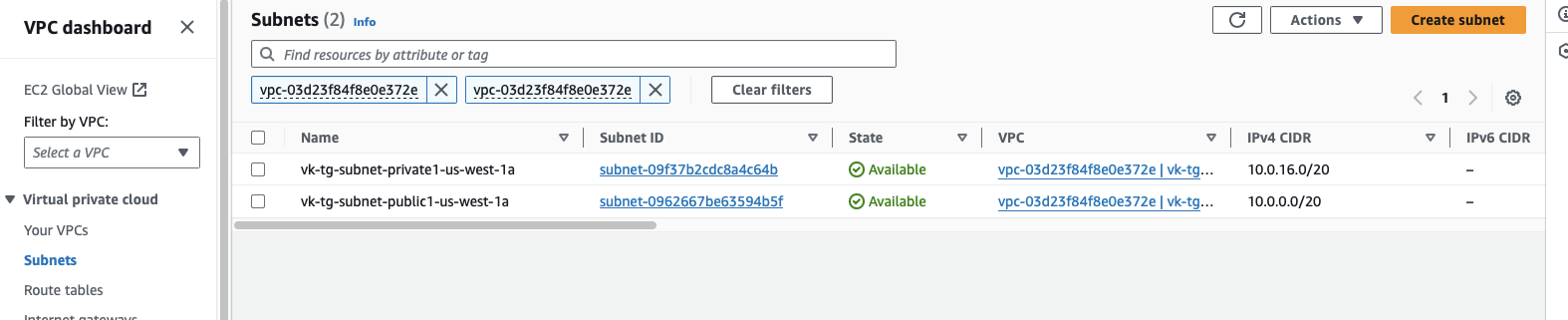
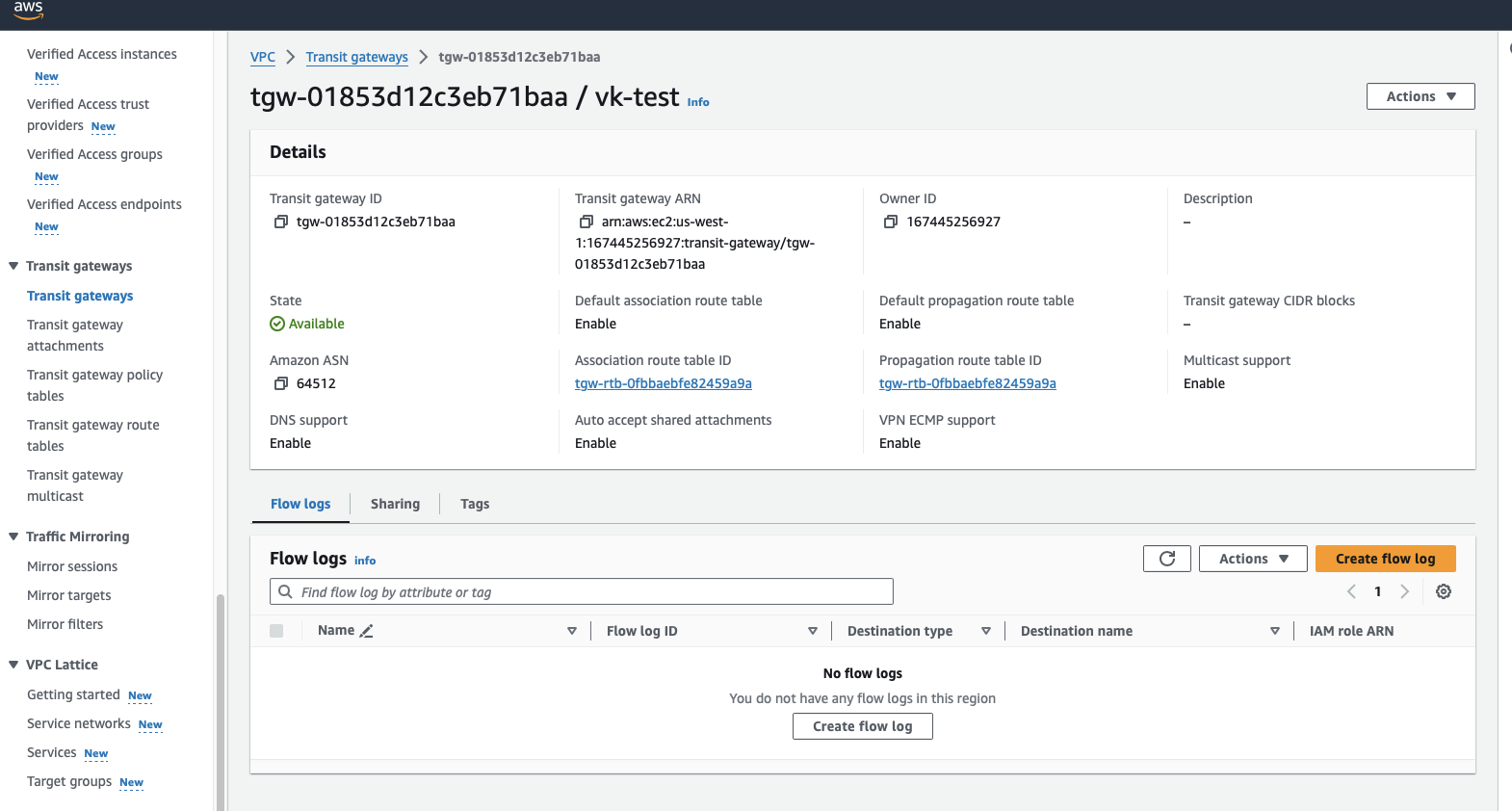
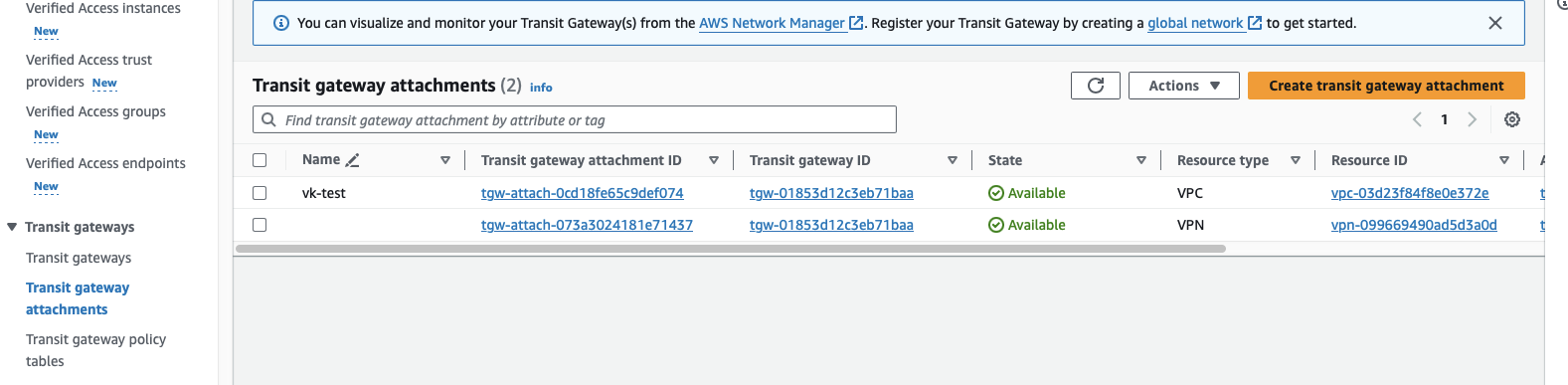
Create a Transit Gateway.
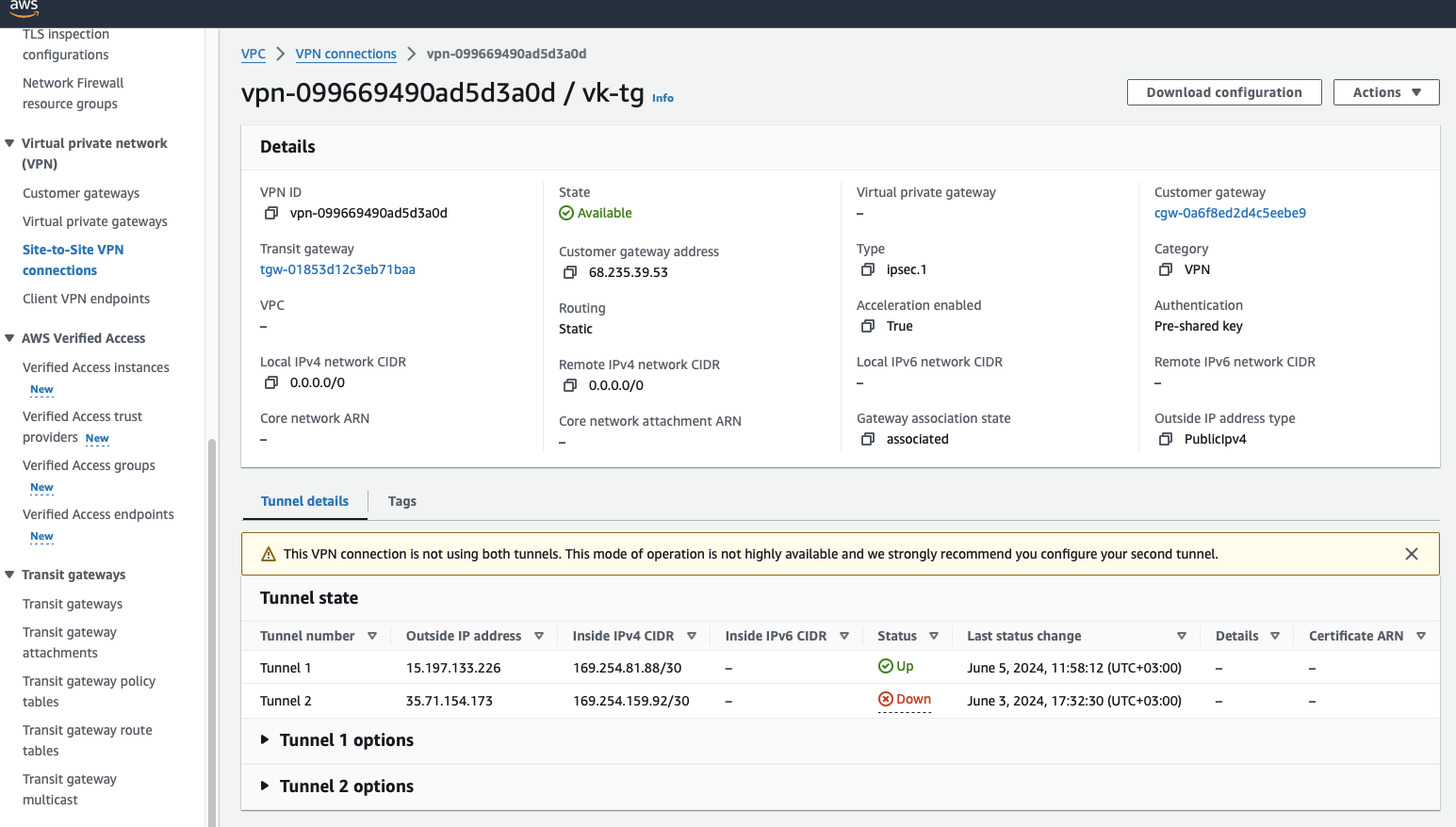
Create a Site-to-Site VPN using the transit gateway. Use Tutorial: Connect AWS to CloudConnexa with IPsec using VPG as appropriate.
Attach VPC to transit gateway.
Create a NAT Gateway in the VPC's public subnet (
10.0.0.0/20).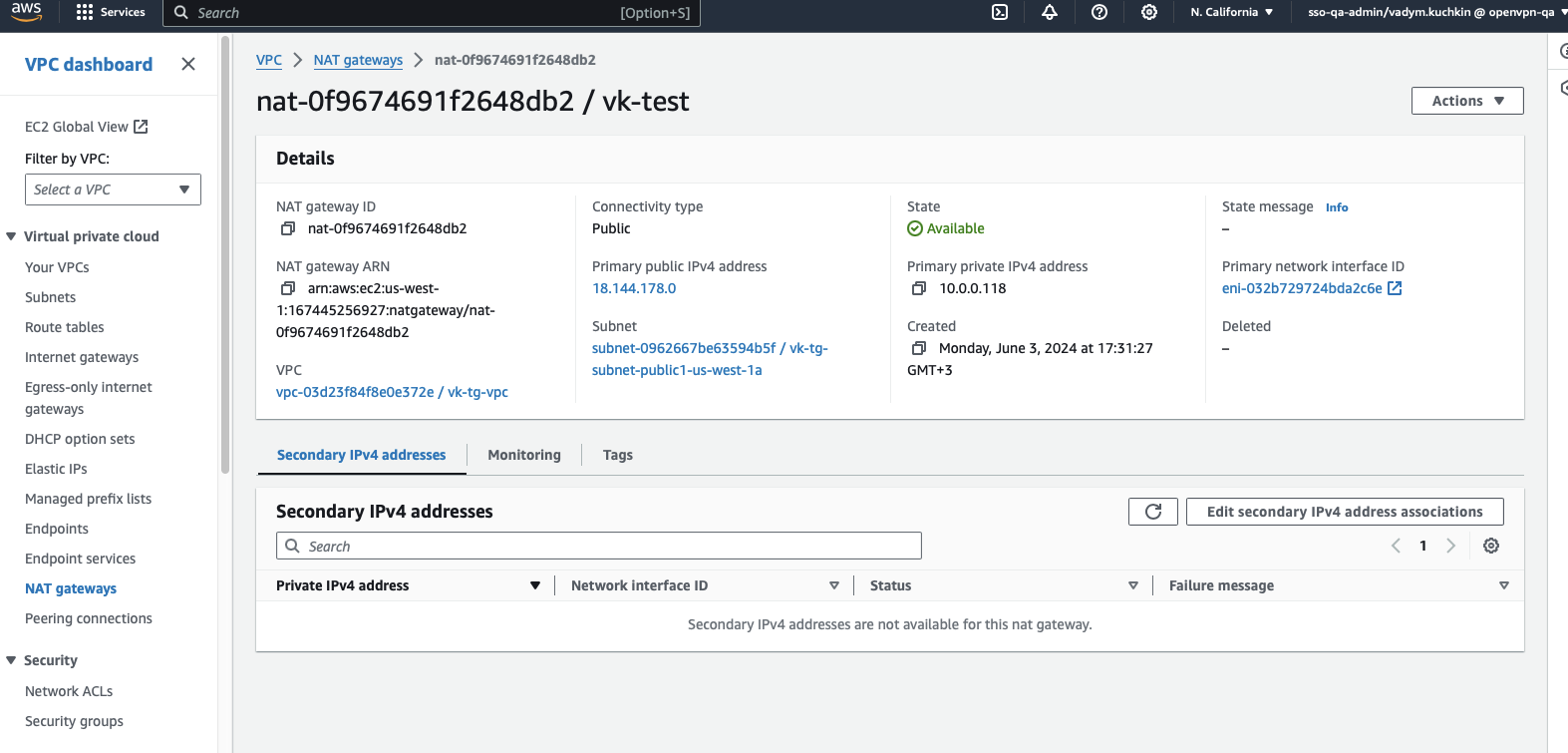
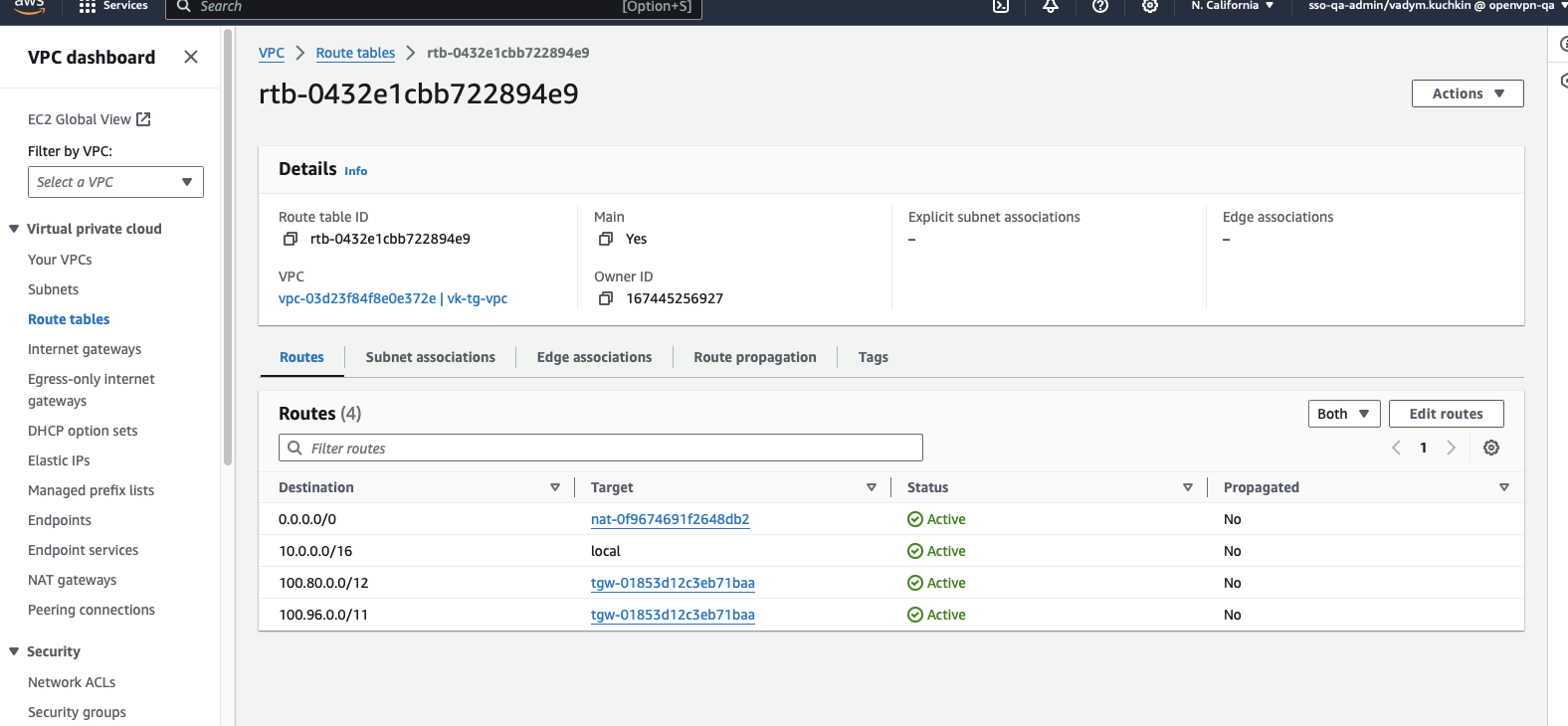
Add the below routes to the VPC's private subnet's route table:
0.0.0.0/0(default route, points to the NAT gateway)100.96.0.0/11(WPC subnet, points to the transit gateway)100.80.0.0/12(Domain routing subnet, points to the transit gateway)
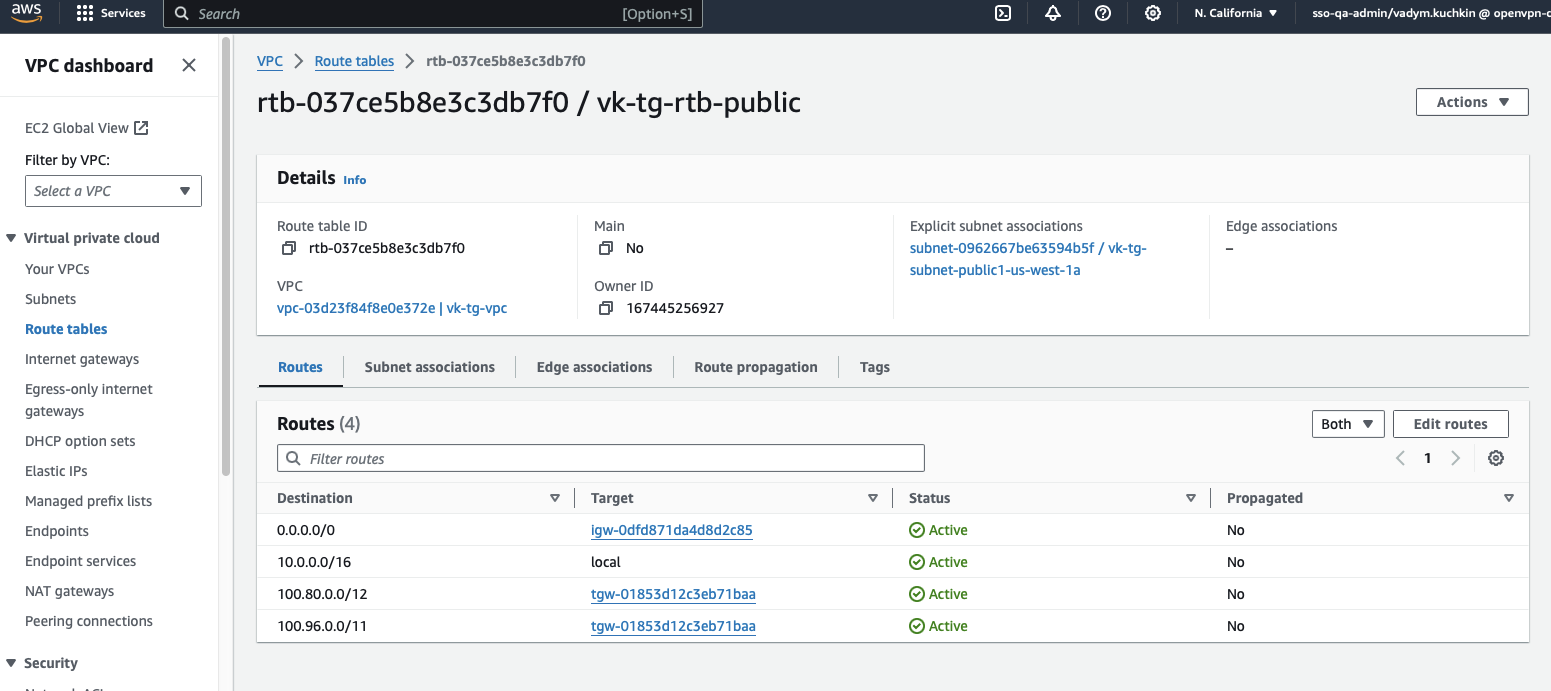
Add the below routes to the VPC's public subnet's route table:
100.96.0.0/11(WPC subnet, points to the transit gateway)100.80.0.0/12(Domain routing subnet, points to the transit gateway)
Add the below routes to the transit gateway's route table:
0.0.0.0/0(default route, points to the VPC resource)100.96.0.0/11(WPC subnet, points to the VPN resource)100.80.0.0/12(Domain routing subnet, points to the VPN resource)
Tutorial: Assign DNS servers using DHCP for AWS VPC
This tutorial shows how to configure a DHCP option set on your AWS VPC to set the DNS servers for all the resources in your VPC.
This tutorial shows how to configure a DHCP option set on your AWS VPC to set the DNS servers for all the resources in your VPC. Using the DNS server associated with the Connector's tunnel IP address subnet lets your VPC resources access Applications on the WPC using Application Domain-Based Routing.
Create a DHCP option set and configure the Domain name server as the IP address that is one before the tunnel IP address of the Connector. For example, if the tunnel IP address of the Connector is 100.96.1.18, then the DNS server IP address is 100.96.1.17.
Assign DHCP option set to your VPC.
Tutorial: Find the AWS IPsec tunnel's outside IP address
Follow these steps to find the AWS IPsec tunnel's public IP address (Outside IP Address).
To find the AWS IPsec tunnel's public IP address (Outside IP Address), follow the steps below:
Open the Amazon VPC console at https://console.aws.amazon.com/vpc/.
Click Site-to-Site VPN connections.
Click the hyperlinked Name of the desired VPN connection.
Click the Tunnel details tab.
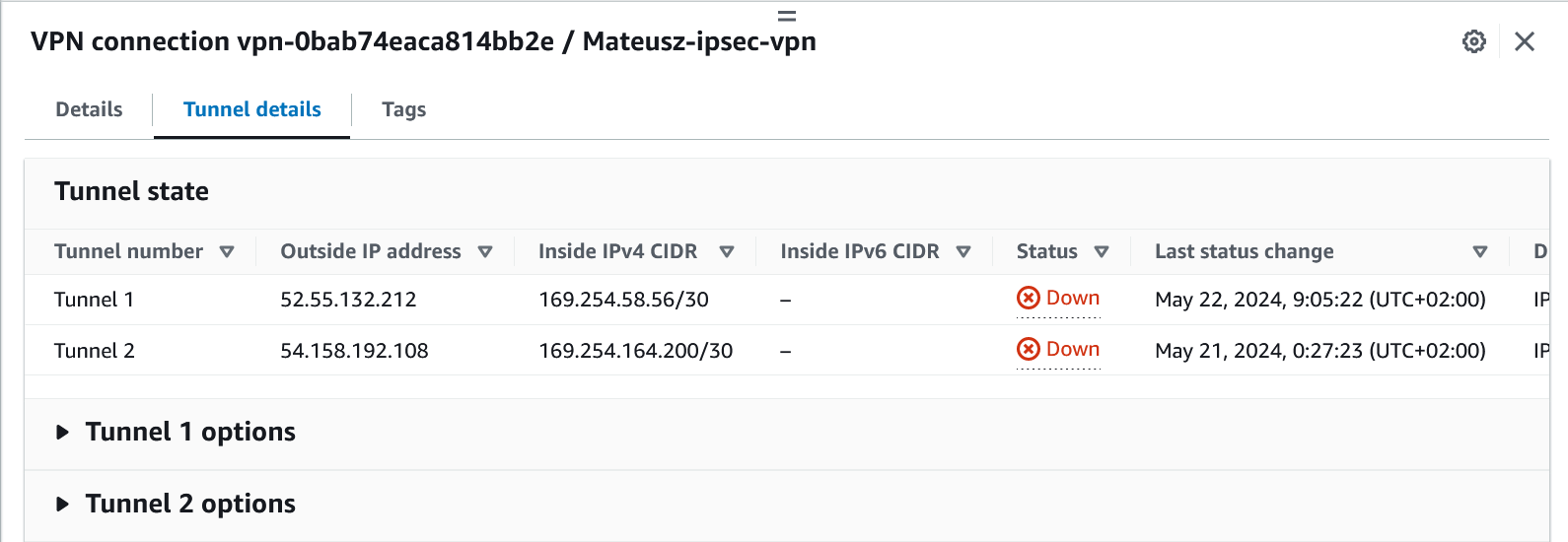
The Outside IP address will be listed in the Tunnel state section.
Tutorial: Connect Your AWS VPC to CloudConnexa by Deploying a Connector
This tutorial shows you the steps to take to deploy a Connector on your AWS VPC. Once deployed, the Connector attempts to establish an outbound OpenVPN tunnel to the configured CloudConnexa Region. On a successful connection, the AWS VPC can be accessed by your CloudConnexa Users.
Launch Connector on AWS
To configure a Network that represents your AWS Virtual Private Cloud (VPC) and install an AWS instance with a Connector that uses AWS CloudFormation, follow these steps:
Sign in to the CloudConnexa Administration portal at https://cloud.openvpn.com
Navigate to Networks and click Networks.
Select the Scenario(s) that apply to your use case.
Provide a Network Name and enter an optional Description.
Provide a Connector name, select a Region, and click Next.
Select an AWS Region.
Click Launch ad log into AWS.
On the Quick create stack web page, specify the stack details:
Stack name,KeyName,SubnetId,VpcId, and then click Next.Note
Use the existing VPC and IP subnet.
Click the I acknowledge that AWS CloudFormation might create IAM resources checkbox to allow CloudFormation to create
RouteManagerRole IAM::Roleresources. This role configures routes in the VPC Route table to use the Connector. Click Create stack.Monitor the stack creation as it goes from
CREATE_IN_PROGRESSstate toCREATE_COMPLETE.On completion, open the Resources tab to view the created resources. Check that the
RouteManagerRolewas created along with anInstancSecurityGroup,InstanceProfile, and theEC2Instance.Click on the Physical ID of the EC2 instance to check its details.
Note
The EC2 instance uses Ubuntu. If you want to connect to it with SSH, use
ubuntuas the username.The Connector EC2 automatically connects to the Region and the Network will show up as
Onlineon the Status page of CloudConnexa Admin portal.
A new EC2 instance Security Group is automatically created after the Network Connector deployment through CloudFormation. This Security Group contains only one Inbound Rule to allow SSH connections (Protocol: TCP; Port: 22; Source: 0.0.0.0/0).
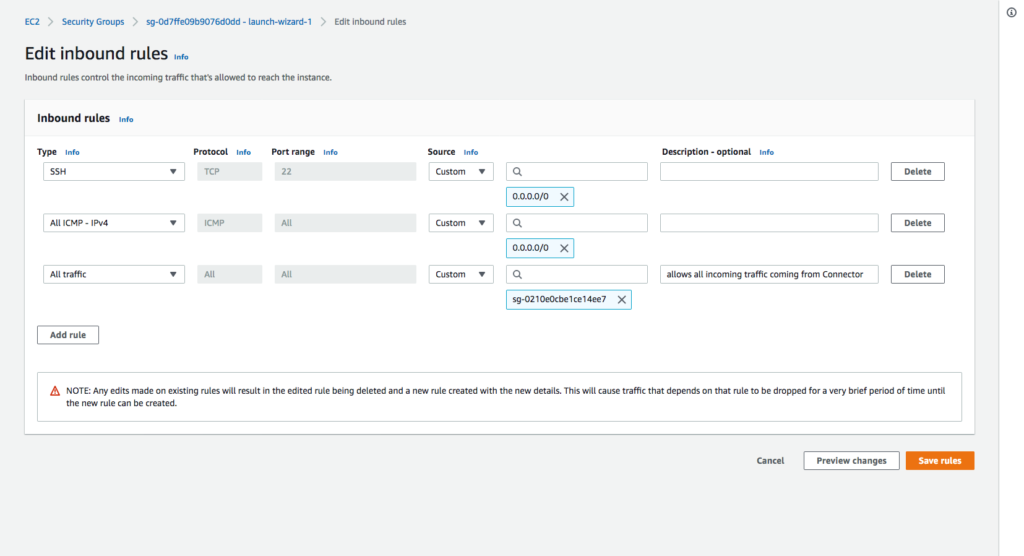
Modify existing Security Groups
If you are using Security Groups to protect any instances that need their traffic to be routed through the Connector instance, you need to add the Security Group of the Connector instance to their inbound rules.
This screenshot shows the inbound rules of sg-0d7ffe09b9076d0dd – launch-wizard-1 Security Group are being edited to add the last rule, which accepts all incoming traffic coming from the Security Group sg-0210e0cbe1ce14ee7 that is associated with the Connector instance.
Optional: Check and add routes to the VPC Route Table associated with the subnet
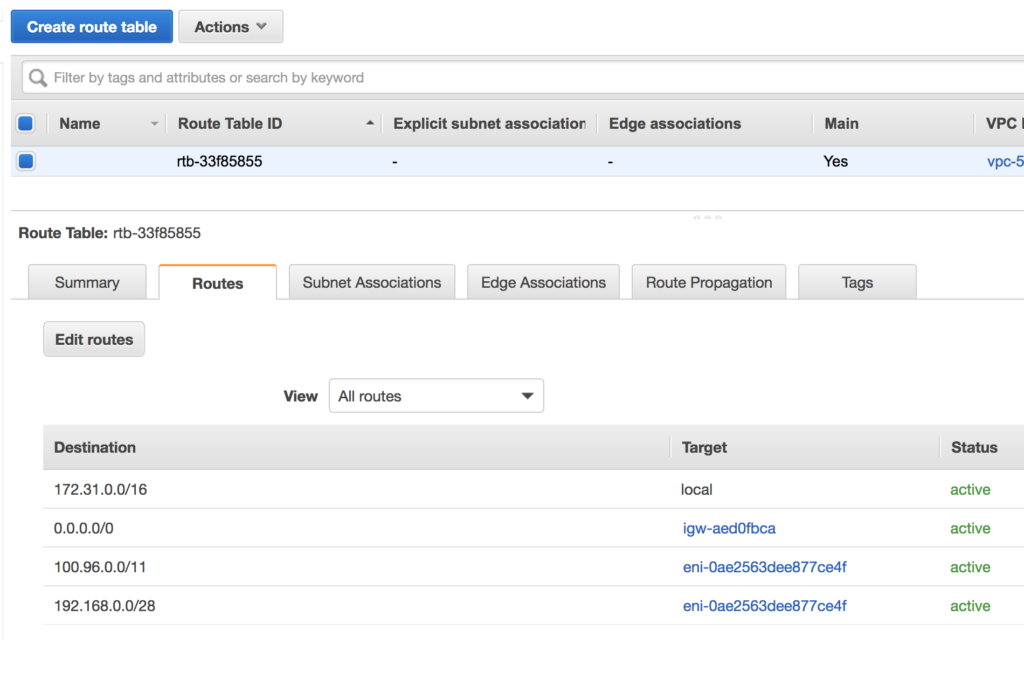
Check that a route exists in the route table for the WPC Subnet IP address range configured in Network Settings of CloudConnexa. The default WPC IPv4 subnet address range for CloudConnexa is 100.96.0.0/11. If a route to destination 100.96.0.0/11 using the Connector instance as a target is absent, add it. If other CloudConnexa Networks need to be reached from the VPC, add a route with those Network subnets as the destination and the Connector instance as the target.
The screenshot below shows how the route table should look with an entry for the CloudConnexa WPC IP address subnet (100.96.0.0/11) and an entry for subnet 192.168.0.0/28 which is another Network (for example, office Network) that is reachable via CloudConnexa. Both entries have target as the instance running the Connector.
Note: If you allow CloudFormation to create RouteManagerRole IAM::Role resources, this role will configure routes in the VPC Route table to use the Connector automatically and update the route table as new Networks are added to the WPC.
Tutorial: Connect Your Azure VNet to CloudConnexa by Deploying a Connector
This tutorial shows you the steps to take to deploy a Connector on your Azure VNet. Once deployed, the Connector attempts to establish an outbound OpenVPN tunnel to the configured CloudConnexa Region. On a successful connection, the Azure VNet can be accessed by your CloudConnexa Users.
Launch Connector On Azure
You can deploy a Connector in the Microsoft Azure environment during the Network creation process. You can choose to either launch a template directly in Azure, or download a template and launch it manually.
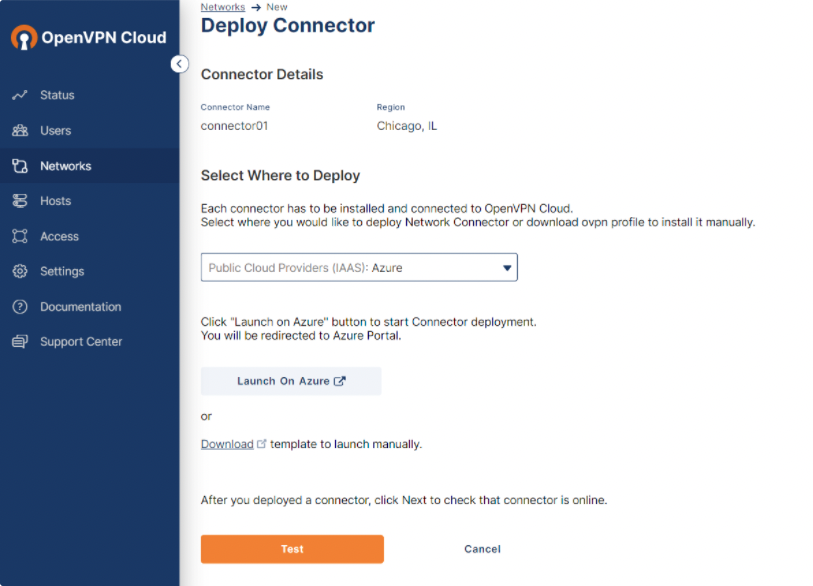
Steps: Launch a template directly on Azure
Click Launch On Azure.
You are redirected to your Azure environment, where a virtual machine (VM) is created automatically.
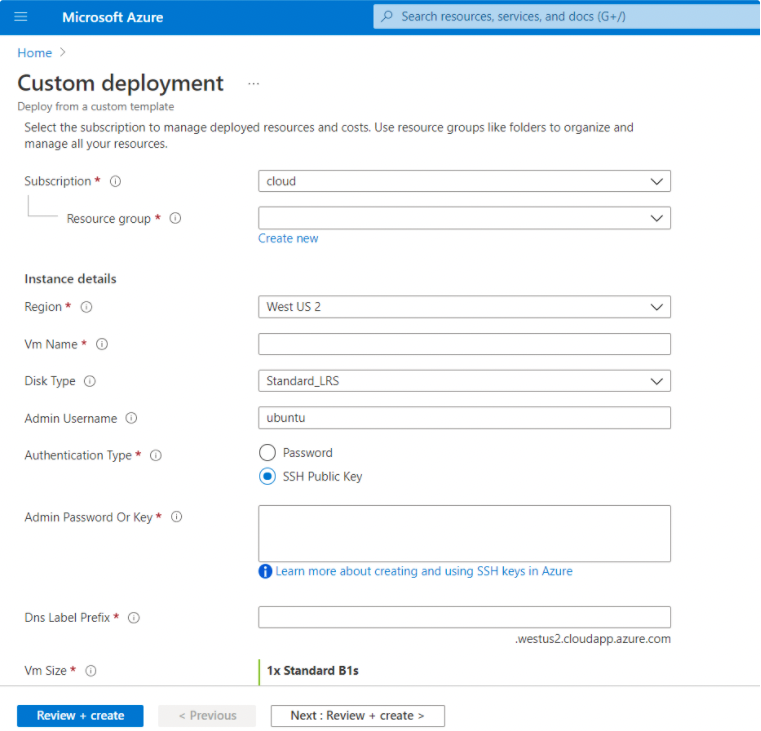
Define the parameters on the Azure VM, noting that the fields marked with an asterisk are mandatory.
Parameter
Value
Subscription
A logical container used to provision resources in Azure. It holds the details of all your resources such as VMs, databases, and more.
Resource Group
A container that holds related resources for an Azure solution. The resource group includes those resources that you want to manage as a group.
Region
The region value propagates from the resource group.
Disk Type
The type of storage to be used for your VM disks.
Admin Username
The Administrator username for the VM.
Authentication Type
The type of authentication to use on the VM. SSH key is strongly recommended.
Admin Password Or Key
The SSH key or password for the VM.
Dns Label Prefix
The unique DNS label prefix for the public IP that is used to access the VM.
Vm Size
The size of the VM.
Virtual Network Name
The name of the existing virtual Network (VNet). You can find the VNet name on the Virtual Networks page.
Subnet Name
The name of the existing subnet in the VNet you want to use. You can find the subnet name on the Subnets blade of the VNet. This subnet value must be the same as the subnet of the Network on the CloudConnexa Administration portal.
Network Security Group Name
The name of the Network security group.
Click Next: Review + create.
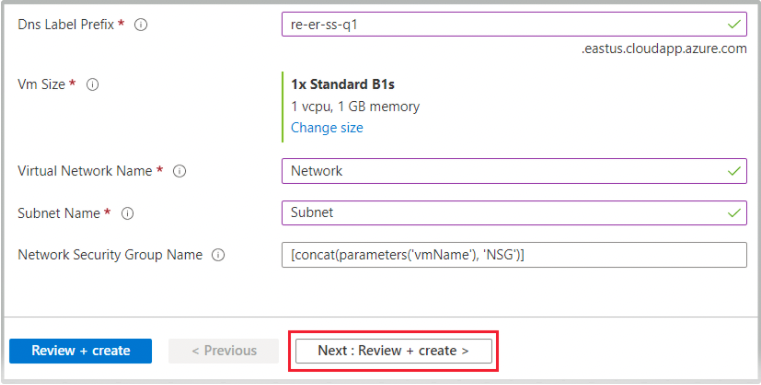
When validation passes, click Create.
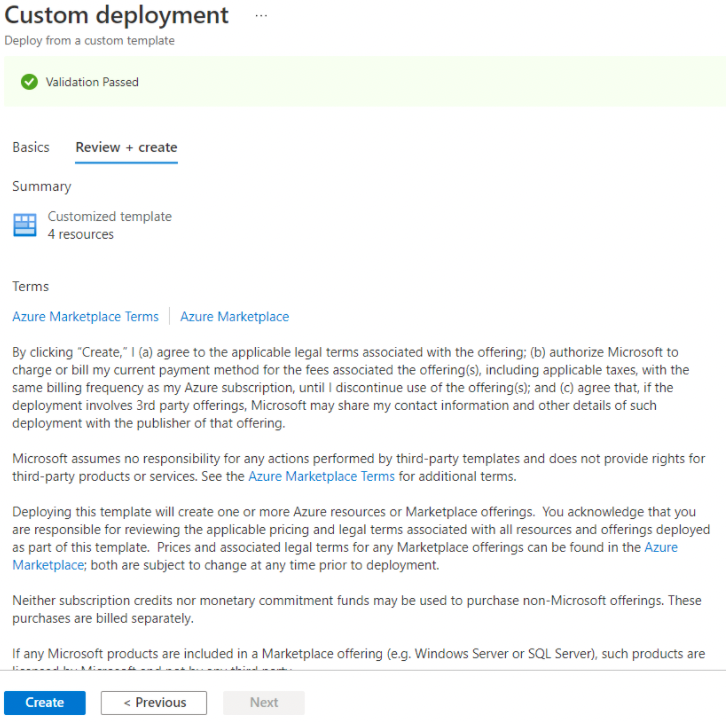
The Connector deployment is complete. You can navigate to your resource group to find your VM.
Steps: Launch Connector manually from template
In the CloudConnexa Administration portal, click Download to save the JSON Azure template to your local computer.
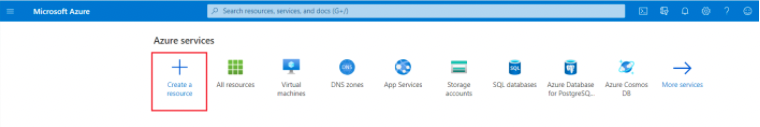
Access your Azure portal and click Create a resource.
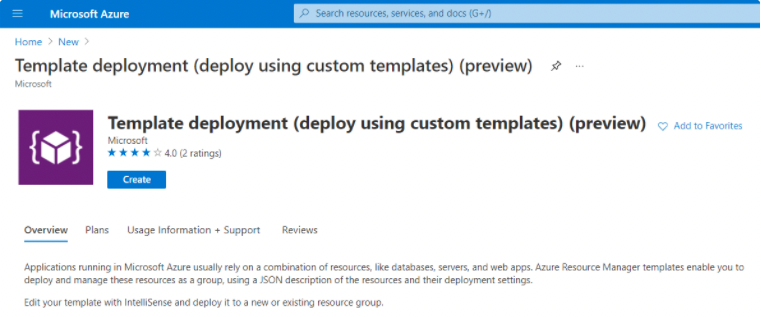
Search for Template deployment (deploy using custom templates) and click Create.
Click Build your own template in the editor.
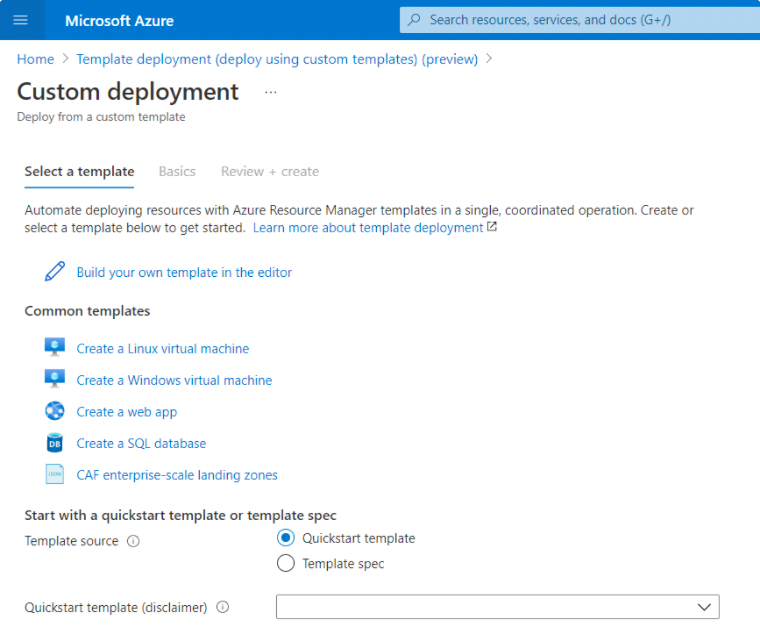
Click Load File.
Load the template file from your local computer and click Save.
Follow the steps 2-4 shown in the Steps: Launch a template directly on Azure section to complete the configuration.
Tutorial: Connect Azure to CloudConnexa with IPsec
This tutorial shows how to configure an IPsec connection to your Azure VNet. Once configured, site-to-site IPsec tunnel(s) connects your Azure VNet to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the Azure VNet.
This tutorial shows how to configure an Azure Site-to-Site IPsec VPN connection between your Azure VNet and a CloudConnexa Region. A good reference for the Azure configuration aspect of this setup is available in Azure documentation.
The Azure configuration involves:
Creating a gateway subnet: The virtual network gateway requires a specific subnet named GatewaySubnet. The gateway subnet is part of the IP address range for your virtual network and contains the IP addresses that the virtual network gateway resources and services use.
Creating a Virtual Network Gateway: In this step, you create a virtual network gateway (VPN gateway) for your virtual network. Creating one often take 45 minutes or more, depending on the selected gateway SKU.
Creating a local network gateway: The local network gateway is a specific object deployed to Azure that represents your CloudConnexa Region for routing purposes.
Creating a VPN connection: Create a site-to-site VPN connection between your virtual network gateway and the CloudConnexa Region.
On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the Azure VNet.
Add a Network using the Network Configuration Wizard to represent your AWS VPC and select the IPsec Tunneling Protocol option.
In the Connector configuration step, select Azure from the Platform to Connect drop-down menu. Refer to CloudConnexa Connectors and About Network Connectors.
Instructions will appear on how to configure IPsec connectivity with CloudConnexa. You will see four steps:
Create Azure Gateways: Use these values when configuring the Azure Local and Virtual network gateways. See steps Step 6 and Step 7.
Setup CloudConnexa Tunnel: Complete the CloudConnexa tunnel setup using values as shown in Step 8 and Step 9.
Create Azure Connection: Use this information in Step 10
Verify Connectivity: After configuring the tunnel on both sides, click “Test Connection” to check that CloudConnexa can establish a connection to the remote network
(Azure) Create a gateway subnet. Refer to Azure documentation. The virtual network gateway requires a specific subnet named GatewaySubnet. The gateway subnet is part of the IP address range for your virtual network and contains the IP addresses that the virtual network gateway resources and services use.
When you create the gateway subnet, you specify the number of IP addresses that the subnet contains. The number of IP addresses needed depends on the VPN gateway configuration that you want to create. Some configurations require more IP addresses than others. It's best to specify /27 or larger (/26, /25, etc.) for your gateway subnet.
On the page for your virtual network, on the left pane, select Subnets to open the Subnets page.
At the top of the page, select + Gateway subnet to open the Add subnet pane.
Select an appropriate Size. For example, /27.
Click Add.
(Azure) Create a local network gateway. Refer to Azure documentation. The local network gateway is a specific object deployed to Azure that represents the CloudConnexa Region (the site) for routing purposes. You give the site a name by which Azure can refer to it, and then specify the IP address of the site's VPN device to which you create a connection. You also specify the IP address prefixes that are routed through the VPN gateway to the site's VPN device (CloudConnexa Region). The address prefixes you specify are the prefixes located on your on-premises network.
In the Azure portal, go to Local network gateways and open the Create local network gateway page.
Click + Create on the Local network gateways page.
On the Basics tab, fill in the following fields:
Resource Group: Select appropriately.
Region: Select appropriately.
Name: Enter name. For example, CloudConnexa
IP address: Copy from CloudConnexa Admin Portal instructions.
Address Spaces: Copy one-by-one from CloudConnexa Admin Portal instructions.
Click Next to move to the Advanced tab and set Configure BGP settings to NO.
Click Next to move to Review + create tab and click Create.
(Azure) Create a virtual network gateway (VPN gateway). Refer to Azure documentation.
In Search resources, services, and docs (G+/), enter virtual network gateway. Locate Virtual network gateway in the Marketplace search results and select it to open the Create virtual network gateway page. Click + Create.
On the Basics tab, fill in the following fields:
Subscription: Select appropriately.
Name: Enter name.
Region: Select same Region as selected for local network gateway.
Gateway Type: VPN
SKU: Recommend to choose the default setting.
Generation: Recommend to choose the default setting.
Virtual Network: Seclect the one on which the GatewaySubnet was created.
Specify the values for Public IP address. These settings specify the public IP address objects that will be associated to the VPN gateway. A public IP address is assigned to each public IP address object when the VPN gateway is created. Create or use existing Public IP address, enable Enable active-active mode, and create or use an existing SECOND PUBLIC IP ADDRESS.
Set Configure BGP to Disabled.
Click Next: Tags >
Click Review + create to run validation.
After validation passes, select Create to deploy the VPN gateway.
A gateway can take 45 minutes or more to fully create and deploy. You can see the deployment status on the Overview page for your gateway.
From the Deployment Details section of the Azure Portal's VPN gateway Overview page, copy the two IP addresses and paste it in the Remote Site Public IPv4 Address fields of Tunnel 1 and Tunnel 2 in the Setup CloudConnexa Tunnel section of CloudConnexa Administration Portal.
Create one complex random string for use as PSK and enter it in the Pre-shared Key field for Tunnel 1 and Tunnel 2.
(Azure) Create a VPN connection. Refer to Azure documentation.
At the top of the Connections page, select + Create to open the Create connection page.
On the Create connection page, on the Basics tab, configure the values for your connection:
Under Project details, select the subscription and the resource group where your resources are located.
Under Instance details, configure the following settings:
Connection type: Select Site-to-site (IPSec).
Name: Name your connection. Region: Select the region for this connection.
Region: Same as the previous created entities.
Click Next: Settings >
In the Settings tab, configure the following values:
Virtual network gateway: Select the virtual network gateway from the dropdown list that was created in Step 7.
Local network gateway: Select the local network gateway from the dropdown list that was created in Step 6.
Shared key: The value here must match the value that was entered in Step 9.
IKE Protocol: Select IKEv2.
Use Azure Private IP Address: Don't select.
Enable BGP: Don't select.
IPsec/IKE policy: Select Custom and match all the values for the various fields with what is shown in the CloudConnexa portal. Encryption uses AES256, Integrity uses SHA256, DH Group is 14 and PFS Group is PFS2048. Change IPsec SA lifetime in seconds to 3600.
Use policy based traffic selector: Select Enable.
DPD timeout in seconds: Select 45.
Connection Mode: Select ResponderOnly.
Click Next: Tags>.
Click Review + create to run validation.
After validation passes, click Create and wait till deployment is finished.
Click Test Connection 1 and Test Connection 2 to check connectivity for both the IPsec tunnels.
Continue with the network wizard instructions.
Tutorial: Connect Your GCP VPC to CloudConnexa by Deploying a Connector
This tutorial shows you the steps to take to deploy a Connector on your GCP VPC. Once deployed, the Connector attempts to establish an outbound OpenVPN tunnel to the configured CloudConnexa Region. On a successful connection, the GCP VPC can be accessed by your CloudConnexa Users.
Deploy a Connector on GCP
You can deploy a Connector in the Google Cloud Platform (GCP) environment during the Network creation process. You must create a Linux virtual machine (VM) on GCP on which you install the Network Connector.
Steps: Install a Linux VM
Navigate to GCP and access Compute Engine > Virtual Machines > VM Instances.
Click Create Instance.
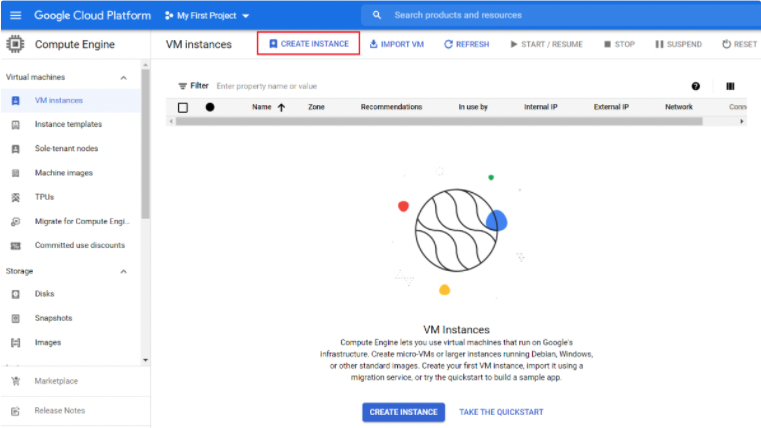
Enter the VM parameters.
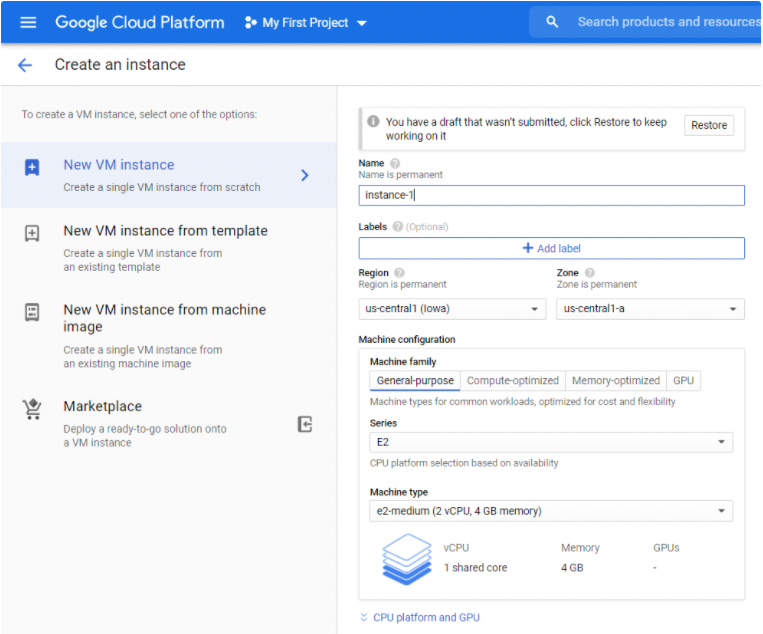
Parameter
Definition
Name
The name you assign to the VM.
Region
A specific geographical location where your VM is run.
Zone
Determines what computing resources are available, and where your data is stored and used.
Machine family
The types of VMs for common workloads, optimized for cost and flexibility.
Series
The CPU platform series.
Machine type
The VM vCPU and memory type.
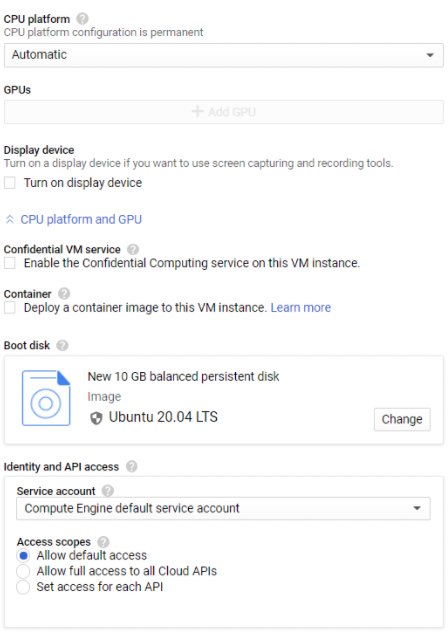
CPU platform
The microarchitecture of your VM instance.
Container
Deploy a container to this VM instance by using a container-optimized OS image.
Boot disk
Each instance requires a disk to boot from.
SSH Keys
Allow access to this instance via SSH.
Hostname
The VM instance hostname.
Network
The Network determines what Network traffic the instance can access.
Subnetwork
Assigns an IPv4 address to the instance from the subnetwork range.
This subnetwork must be the same as the Network Subnet in the CloudConnexa Administration portal.
Primary internal IP
For ephemeral, restarting an instance won't change its internal IP, but deleting and recreating an instance will.
External IP
An external IP address associated with this instance. Select an unused static IP address or choose Ephemeral to use an IP from a shared ephemeral IP address pool. Selecting None results in the instance having no external internet access.
IP forwarding
IP forwarding must be enabled.
IP forwarding allows the instance to help route packets.
Click Create.
Click the Select Linux Distribution dropdown and select the distribution that you want to install the Connector on.
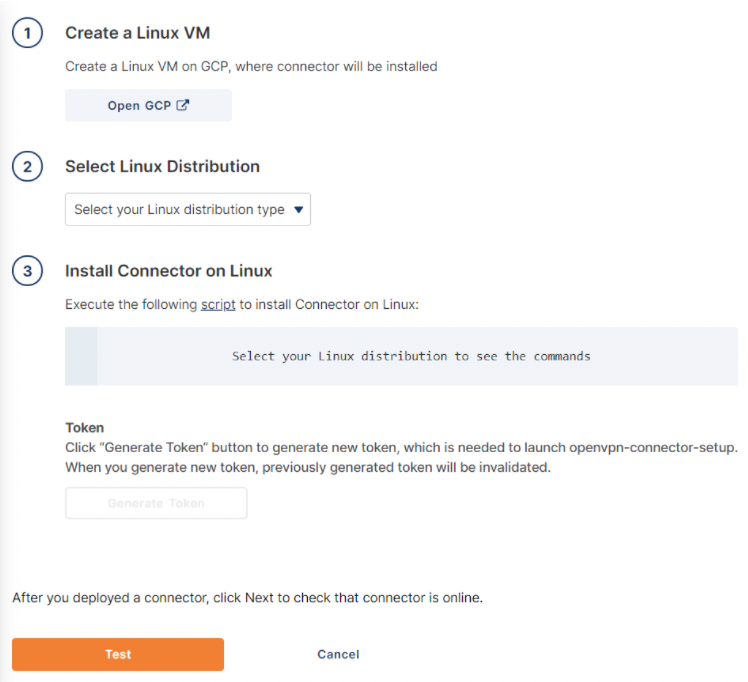
Copy the commands shown for your terminal.
Connect to your GCP VM through SSH and paste the commands.
Select Yes for each prompt.
Once the installation completes, a setup token prompt displays.
In the CloudConnexa Administration portal, click Generate Token and click to copy the token.
Access your Linux terminal and paste the token.
The utility imports the Connector Profile and connects to CloudConnexa.
Tutorial: Connect Your GCP VPC to CloudConnexa using IPsec
This tutorial shows how to configure an IPsec connection to your GCP VPC. Once configured, a site-to-site IPsec tunnel connects your GCP VPC to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access your VPC.
This tutorial shows how to configure an IPsec connection to your GCP VPC. Once configured, a site-to-site IPsec tunnel connects your GCP VPC to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access your VPC.
Add a Network using the Network Configuration Wizard to represent your Cisco private network and select the IPsec Tunneling Protocol option.
In the Connector configuration step, select GCP from the Public Cloud Providers (IAAS)section of the Platform to Connect drop-down menu. Refer to CloudConnexa Connectors and About Network Connectors.
Instructions will appear on how to configure IPsec connectivity with CloudConnexa.
You will see three steps:
Create GCP VPN: You must configure the GCP VPN with the information needed to connect to the selected CloudConnexa Region.
Setup CloudConnexa Tunnel: You will provide the Remote Site IP address, configuration, and pre-shared key or certificate to set up the IPsec tunnel.
Verify Connectivity: After configuring the tunnel on both sides, click “Test Connection” to check that CloudConnexa can connect to your network.
Go to the VPN section of Google Cloud Console.
Choose Classic VPN when you Create a new VPN connection.
For the Google Compute Engine VPN gateway, use the settings below:
Name - Enter a valid name.
Network - select the VPC you want to connect to CloudConnexa.
Region - select a GCP Region close to the CloudConnexa Region chosen for the IPsec Connector.
IP Address - create a new one or select an existing static IP address for the VPN Gateway. This is the IP address you will use as the Remote Site Public IPv4 Address in a later step.
For the New Tunnel, use the following settings:
Name - any valid name
Remote Peer Address - enter the one provided in CloudConnexa's Create GCP VPN section of instructions.
IKE Version - IKEv2
IKE pre-shared key - Type in random text and paste it in the Pre-shared Key (PSK) field of CloudConnexa's Setup CloudConnexa Tunnel section.
Note
Do not use the Generate and Copy option to generate the PSK key, as the keys it creates may be incompatible with the PSK string validation rules for CloudConnexa.
Routing options - Policy-based
Remote network IP ranges - Enter the one provided in CloudConnexa's Create GCP VPN section of instructions one by one.
Local IP ranges - enter subnets that belong to GCP VPC.
Click Done.
Click Create.
The created VPN tunnel and CloudVPN gateway will be displayed after a few moments.
In the Setup CloudConnexa Tunnel section, provide your Google Compute Engine VPN gateway public IPv4 address (see, Step 7.d) in the Remote Site Public IPv4 Address text field and the VPN tunnel PSK in the Pre-shared Key (PSK) field (see, Step 8.d).
In the Verify Connectivity section, click Test Connection to check connectivity and click View Logs to see any logs to troubleshoot failures.
Continue with the network wizard instructions.