Routers
Tutorial: Connect your Cisco router to CloudConnexa with IPsec
This tutorial shows how to configure an IPsec connection to your private network that uses a Cisco router. Once configured, a site-to-site IPsec tunnel connects your private network to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the private network.
This tutorial shows how to configure an IPsec connection to your private network that uses a Cisco router. Once configured, a site-to-site IPsec tunnel connects your private network to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the private network.
Add a Network using the Network Configuration Wizard to represent your Cisco private network and select the IPsec Tunneling Protocol option.
In the Connector configuration step, select Cisco from theIPsec Compatible Router section of the Platform to Connect drop-down menu. Refer to CloudConnexa Connectors and About Network Connectors.
Instructions will appear on how to configure IPsec connectivity with CloudConnexa.
You will see three steps:
Setup CloudConnexa Tunnel You will provide the IP address, configuration, and pre-shared key to set up the tunnel from CloudConnexa to your Cisco router.
Remote Tunnel Configuration This is for you to configure the Cisco router with the information needed to connect to the selected CloudConnexa Region.
Verify Connectivity After configuring the tunnel on both sides, click “Test Connection” to check that CloudConnexa can connect to your Cisco network.
In the Setup CloudConnexa Tunnel section, provide your Cisco router's public IPv4 address in the Remote Site Public IPv4 Address text field and a pre-shared key in the Pre-shared Key (PSK) text field.
Optionally, you can expand the Advanced Configuration and change the configuration as desired.
Use the information provided in the Remote Tunnel Configuration section to configure your Cisco router. The instructions cover everything that needs to be configured: firewall, IPsec tunnel parameters, startup action and DPD parameters, static routes, and DNS server.
In the Verify Connectivity section, click Test Connection to check connectivity and click View Logs to see any logs to troubleshoot failures.
Continue with the network wizard instructions.
Tutorial: Configure a DD-WRT Router To Connect to CloudConnexa
This tutorial contains instructions on how to use a DD-WRT router and configure it to use a Connector profile to connect to CloudConnexa and make the network part of your WPC.
Introduction
Many of our Users have expressed interest in using DD-WRT or related routers to connect to CloudConnexa instead of using the Connector application.
While connecting in this manner may not yield the best performance, due to the limited processing power and memory of the router, it could be useful in cases where convenience, rather than high throughput, is required.
Important
The information provided here is for EDUCATIONAL and INFORMATIONAL purposes only. We are not responsible for any damages you incur as a result of using these instructions here. For technical support, you need to contact the supplier of the router or the appropriate community forums. It is not guaranteed that all versions of the firmware will work as expected with CloudConnexa and some features may be incompatible. It is best to update the firmware to the latest version.
Downloading the Connector Profile
To configure the routers you need to use specific sections of the OpenVPN Connector Profile in specific setting configurations.
First, you need to download the Profile in .ovpn format from the Network configuration you have created in the Administration portal to represent the router’s Network.
The Profile can be downloaded by selecting it as the option in the drop-down list shown after clicking on the download icon.
Configuring DD-WRT
Before you begin, make sure your router is properly configured for a NTP server. This setting could be found under the set up tab in your router configuration. Under Time settings, make sure the NTP Client is set to Enable and the Server IP / Name is populated with a proper time server. If you do not know what your time server is, please fill in time.nist.gov in the text box as indicated.
Afterward, visit the Services tab, then the VPN tab. Under the section Start OpenVPN Client, click the Enable radio box. If you do not see this section, it is possible that your DD-WRT build is not OpenVPN enabled. Please consult the proper DD-WRT documentation for more information on the various DD-WRT builds.
Once you have selected that option, also check the Enable option under Advanced Options, this will allow you to define options required for the WPC connection to work.
The following screen should then be displayed, as depicted below:
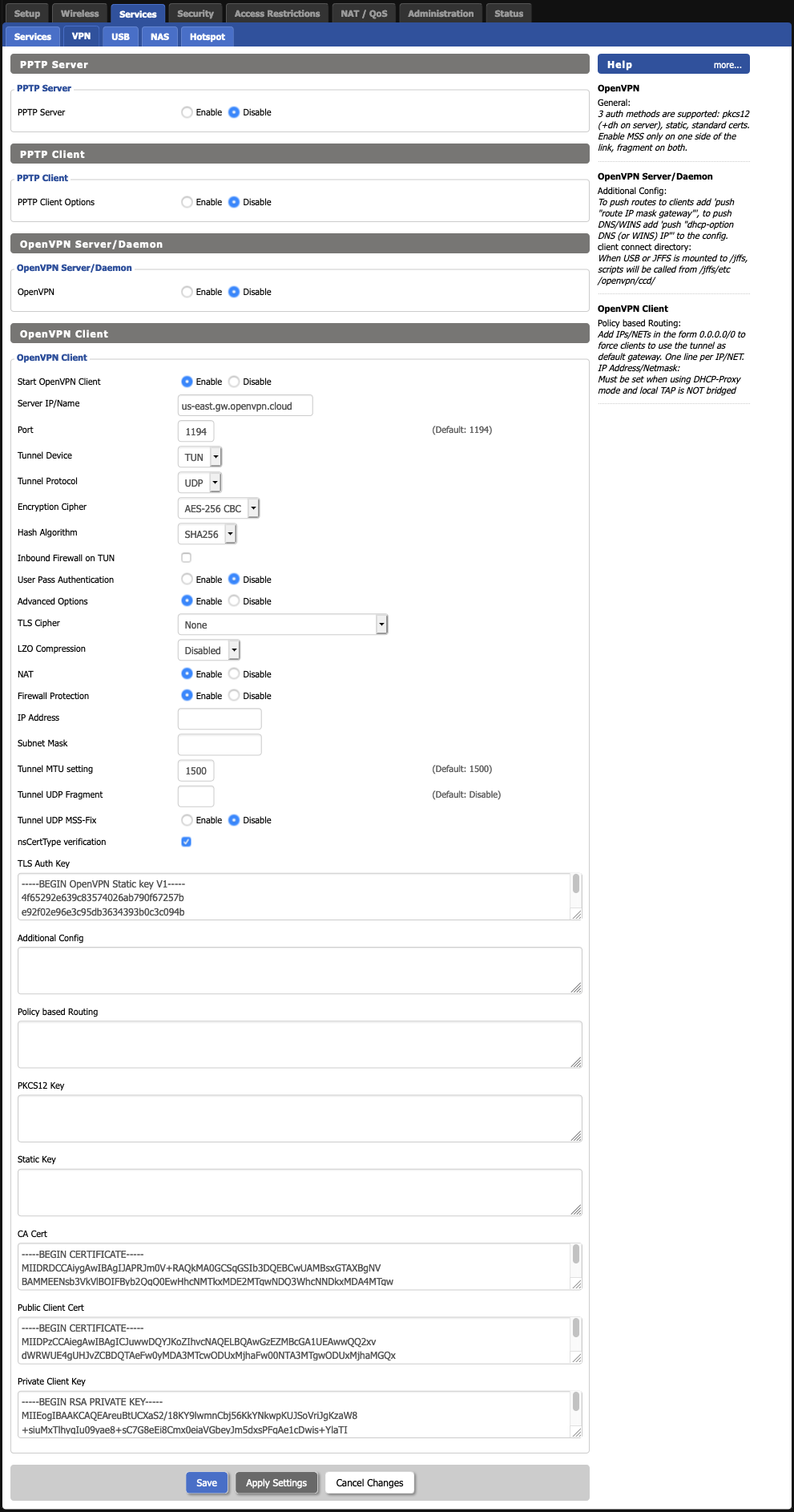
Configuration Descriptions
Start CloudConnexa Client: Enables/Disables the CloudConnexa client connection.
Server IP/Name: The hostname of the WPC server you are trying to connect to. Look inside your Profile for entries starting with remote. For example, the entry remote us.shieldexchange.com 1194 udp indicates that the hostname is us.shieldexchange.com.
Port: The port number the WPC server is listening on. If you do not know what this is, either look for the port number in remote entries such as the one shown in the previous example. In the previous example, the port is 1194. If your server is only using a single port, you may see the port number specified using the port directive (e.g. port 1194). It is preferable that you choose UDP ports over TCP, as UDP provides better reliability for your WPC sessions.
Tunnel Device: Select TUN
Tunnel Protocol: Select UDP
Encryption Cipher: Select whatever appears on the cipher line of the Profile. By default, AES-256-CBC is used for CloudConnexa.
Hash Algorithm: Select whatever appears on the auth line of the Profile. By default, SHA256 is used for CloudConnexa.
Verify Server Cert.: Located in Advanced Options. Checks to see if the remote server is using a valid type of certificate meant for OpenVPN Connections. As this is a security feature of CloudConnexa, it should be left enabled.
Advanced Options: As described previously, this option must be Enabled for you to set the required options necessary for a successful WPC connection.
LZO Compression: Enables compression over WPC. This option should be Disabled.
NAT: Creates a NAT layer over the WPC tunnel. This should be Enabled if you plan to have all your client’s traffic to be sent over the WPC tunnel under the shared WPC IP address assigned by CloudConnexa. If you want to send traffic from your clients directly over the tunnel without any address modification(s) (e.g. If you were using Advanced Routing), then this option should be Disabled. It is highly recommended that you turn this option ON, unless you know what you are doing.
Local IP Address: Specify a IP address that your CloudConnexa tunnel should use. This field is usually not applicable, since CloudConnexa automatically assigns an address upon a successful connection.
TUN MTU Setting: The maximum transmission unit (MTU) used over the WPC tunnel. Leave this at 1500, unless otherwise directed by a support staff or a Network professional.
Tunnel UDP Fragment (blank).
Note
Unless directed otherwise by a support staff or a network professional, leave this field blank.
Tunnel UDP MSS-Fix (Default: Disable).
TLS Cipher: What encryption algorithm CloudConnexa should use for encrypting its control channel. Selecting None will allow DD-WRT to auto-negotiate the strongest available cipher.
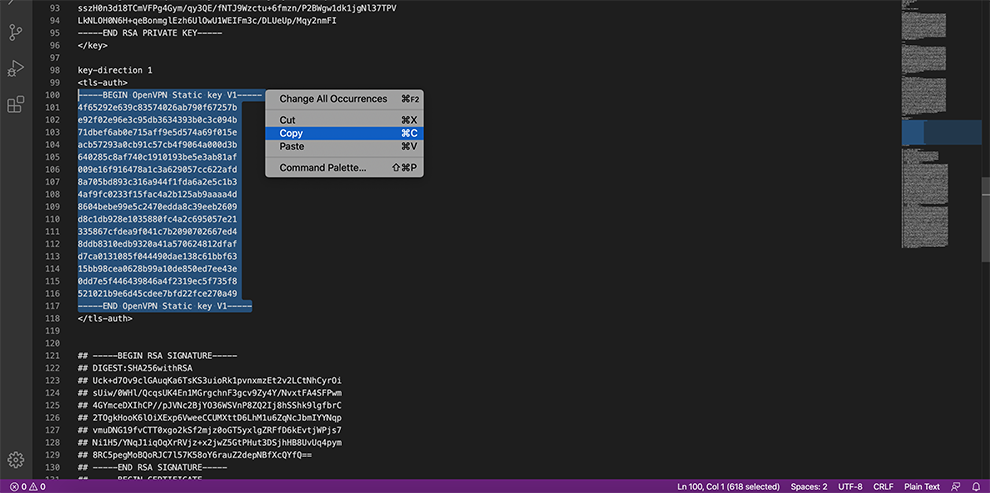
TLS Auth Key: The static key CloudConnexa should use for generating HMAC send/receive keys. You may find this key surrounded by the <tls-auth>..</tls-auth> brackets. Copy the contents from your Profile, starting from –BEGIN CloudConnexa Static key V1– until you reach –END CloudConnexa Static key V1–.
Additional Config: Any additional configurations you want to define for the WPC connection.
Policy based Routing: This field should be left blank.
PKCS12 Key: This field should be left blank.
Static Key: This field should be left blank.
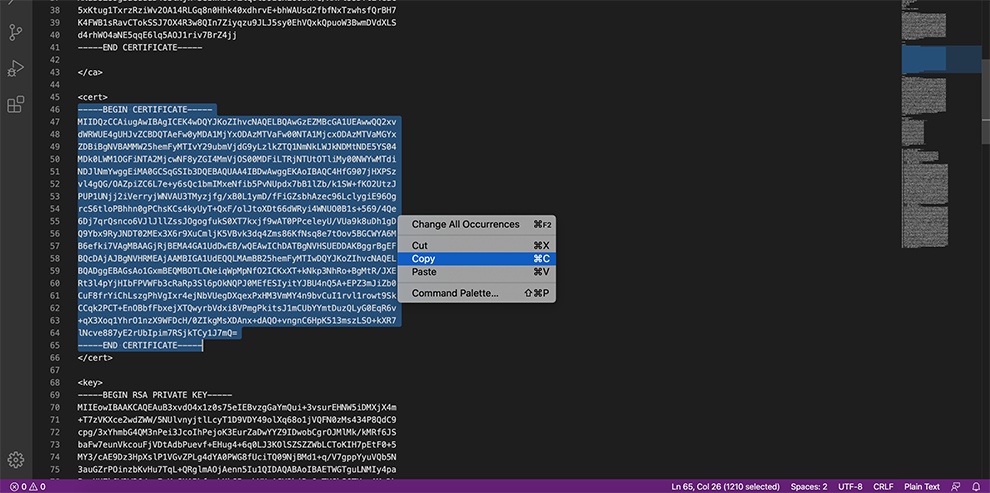
CA Cert: The CA certificate used by the WPC server, found between the <ca>…</ca> brackets inside the Profile. Start copying from –BEGIN CERTIFICATE– until you hit the first –END CERTIFICATE–.
Public Client Cert: The CA certificate used by the WPC client, found between the <cert>..</cert> brackets inside the Profile. Start copying from –BEGIN CERTIFICATE– until you hit –END CERTIFICATE–.
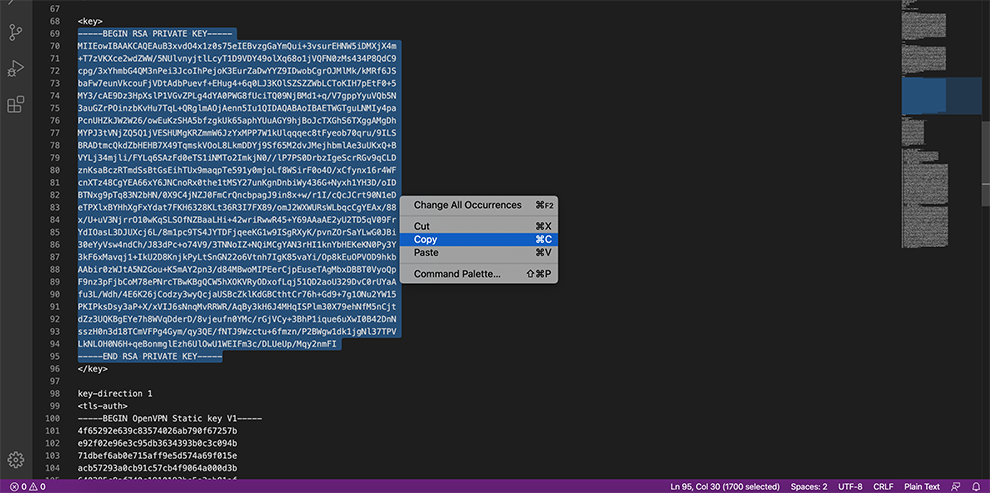
Private Client Key: The client’s private key used by the WPC client, found between the <key>..</key> brackets inside the Profile. Start copying from –BEGIN RSA PRIVATE KEY– until you hit –END RSA PRIVATE KEY–.
To start the WPC connection, click the Apply Settings towards the bottom of the page. You may view the status of your WPC connection by visiting the Status tab, and then the CloudConnexa tab.
Tutorial: Configure an OpenWrt Router To Connect to CloudConnexa
This tutorial contains instructions on how to use an OpenWrt router and configure it to use a Connector profile to connect to CloudConnexa and make the network part of your WPC.
Introduction
Many of our Users have expressed interest in using CloudConnexa protocol compatible routers to connect to CloudConnexa instead of using the Connector application.
While connecting in this manner may not yield the best performance, due to the limited processing power and memory of the router, it could be useful in cases where convenience, rather than high throughput, is required.
Important
The information provided here is for EDUCATIONAL and INFORMATIONAL purposes only. We are not responsible for any damages you incur as a result of using these instructions here. For technical support, you need to contact the supplier of the router or the appropriate community forums. It is not guaranteed that all versions of the firmware will work as expected with CloudConnexa and some features may be incompatible. It is best to update the firmware to the latest version.
Note
Refer to instructions from OpenWrt for the latest information.
Downloading the Connector Profile
To configure the routers you need to use specific sections of the OpenVPN Connector Profile in specific setting configurations.
First, you need to download the Profile in .ovpn format from the Network configuration you have created in the Administration portal to represent the router’s Network.
The Profile can be downloaded by selecting it as the option in the drop-down list shown after clicking on Deploy.
Open the downloaded Profile file in a text editor. In Windows, the file must be opened in a text editor other than Notepad (e.g. Wordpad / Notepad++).
Configuring OpenWrt
To connect to the CloudConnexa service using your OpenWrt router, please follow the steps below:
If you have not already upgraded to the latest of OpenWrt, please follow the instructions on the OpenWrt website.
Login to the LuCI web interface, and then go to System -> Software.
Install the openvpn-openssl and the luci-app-openvpn packages on your system by putting the name of the package in the Download and install package: textbox and then click OK.
After the packages have been installed, refresh the web page. The OpenVPN option should appear under VPN. If the option does not appear, log out of the administration interface and then log back in.
In the LuCI interface, go to VPN > OpenVPN.
If your router supports the OVPN configuration file upload option, follow the steps in OVPN configuration file upload, otherwise follow Template based configuration.
OVPN configuration file upload
To upload the Profile to your router, follow the steps below:
VPN > OpenVPN.
Under ovpn configuration file upload, in the textbox instance name, enter CloudConnexa; Choose the downloaded profile in
.ovpnformat and click upload.Under the OpenVPN instances, check the Enabled checkbox from the newly created instance (CloudConnexa) and click start.
Click Save and Apply.
Template based configuration
In the blank text box that appears, enter CloudConnexa as the name, and use the Client configuration for a routed multi-client WPC drop-down option, and click Add.
Note
This is in the
template-based configurationtext boxinstance name.In the Profile editor that appears, click the Switch to advanced configuration >> link.
Note
You will need to edit the newly created instance.
From VPN > OpenVPN in the Profile editor:
Choose from the "additional field" drop-down list
fast_io.Check the fast_io checkbox.
Click the Save button.
In the Networking tab of the Profile editor:
Under — Additional Field —, add the sndbuf and rcvbuf fields.
Change the sndbuf and rcvbuf values to both 0.
Change the dev textbox to read tun0.
Select adaptive under the comp_lzo option.
Click the Save button.
In the VPN tab of the Profile editor:
Check the pull checkbox.
In the remote text box, enter the remote value from your Profile file. They should be near the top of the file and after the word remote (e.g. eu-west.gw.openvpn.com 1194 udp).
Click the + button next to the text box, and repeat the entry for the 443 tcp entry below (e.g. eu-west.gw.openvpn.com 443 tcp).
Click the Save button.
In the Cryptography tab of the Profile editor:
Under –Additional Field— , add the ca field.
In the Profile you have downloaded, copy the contents between the <ca> and </ca> tag into a new file. Make sure you include all of the —–BEGIN CERTIFICATE—– and —–END CERTIFICATE—– lines in the new file. There should be a total of four of such lines, and when copying the contents into a new file, omit the <ca> and </ca> tags in the beginning and the end, since these will be added automatically by OpenWrt.
Upload the certificate into OpenWrt by selecting the new file you have created.
Under –Additional Field— , add the cert field.
In the Profile you have downloaded, copy the contents between the <cert> and </cert> tag into a new file. Make sure you include all of the —–BEGIN CERTIFICATE—– and —–END CERTIFICATE—– lines in the new file. There should be a total of two of such lines, and when copying the contents into a new file, omit the <cert> and </cert> tags in the beginning and the end, since these will be added automatically by OpenWrt.
Upload the certificate into OpenWrt by selecting the new file you have created.
Under –Additional Field— , add the key field.
In the Profile you have downloaded, copy the contents between the <key> and </key> tag into a new file. Make sure you include all of the —–BEGIN RSA PRIVATE KEY—– and —–END RSA PRIVATE KEY—– lines in the new file. There should be a total of two of such lines, and when copying the contents into a new file, omit the <key> and </key> tags in the beginning and the end, since these will be added automatically by OpenWrt.
Upload the key into OpenWrt by selecting the new file you have created.
Under –Additional Field— , add the tls_auth field.
In the Profile you have downloaded, copy the contents between the <tls-auth> and </tls-auth> tag into a new file. Make sure you include all of the —–BEGIN CloudConnexa Static key V1—– and —–END CloudConnexa Static key V1—– lines in the new file. There should be a total of two of such lines, and when copying the contents into a new file, omit the <tls-auth> and </tls-auth> tags in the beginning and the end, since these will be added automatically by OpenWrt.
Upload the TLS auth key file using SCP to your router in the /etc/openvpn/ folder with the file name tlsauth.key. If you already have a WPC Profile that is using this file name, change the file name accordingly and then update the path value in the tls_auth text box that appears. If you are using Notepad++ to copy the contents of the file over a PuTTY or an SSH session, please make sure the new file is using the Windows EOL format, otherwise the copied lines will not be transferred properly. This option can be changed in Edit -> EOL Conversion -> Windows Format.
Click Save & Apply to save the CloudConnexa configuration on your router.
On the top of the LuCI interface, go to Network -> Interfaces.
Click Add new interfaces…
Enter CloudConnexa under the Name text box.
Select Unmanaged under the Protocol text box.
Click the drop-down next to Interface: and enter tun0 into the text box.
Click Create interface to save the custom interface.
On the top of the LuCI interface, go to Network -> Firewall.
Click the Add button.
Use the following settings for the newly created zone:
Name: OC
Input: drop
Output: accept
Forward: drop
Masquerading: Checked
MSS Clamping: Unchecked
Covered Networks: CloudConnexa (checked)
Inter-Zone Forwarding -> Allow forward from source zones: lan (checked)
Click Save & Apply to save the newly created zone.
To start the VPN connection, go to VPN -> OpenVPN, check the Enabled checkbox and then the start button under the CloudConnexa Profile.
Tutorial: Configure a PfSense Router To Connect to CloudConnexa
This tutorial contains instructions on how to use a PfSense router and configure it to use a Connector profile to connect to CloudConnexa and make the network part of your WPC.
Introduction
Many of our Users have expressed interest in using CloudConnexa compatible routers to connect to CloudConnexa instead of using the Connector application.
While connecting in this manner may not yield the best performance, due to the limited processing power and memory of the router, it could be useful in cases where convenience, rather than high throughput, is required.
Important
The information provided here is for EDUCATIONAL and INFORMATIONAL purposes only. We are not responsible for any damages you incur as a result of using these instructions here. For technical support, you need to contact the supplier of the router or the appropriate community forums. It is not guaranteed that all versions of the firmware will work as expected with CloudConnexa and some features may be incompatible. It is best to update the firmware to the latest version.
Downloading the Connector Profile
Sign in to the CloudConnexa Administration portal at https://cloud.openvpn.com.
Navigate to Networks.
Select Networks.
Click the name of the router Network.
Click the Connectors tab.
Click the Deploy drop-down menu of the Connector you wish to modify.
Select Deploy Connector.
Click the Provider Type drop-down menu.
Select pfSense.
Click Download OVPN Profile.
Alternatively, you may download the profile by clicking the Network name, and the edit icon for the Network.
Or from the Connectors menu.
Open the downloaded Profile file in a text editor. In Windows, the file must be opened in a text editor other than Notepad (e.g. Wordpad / Notepad++).
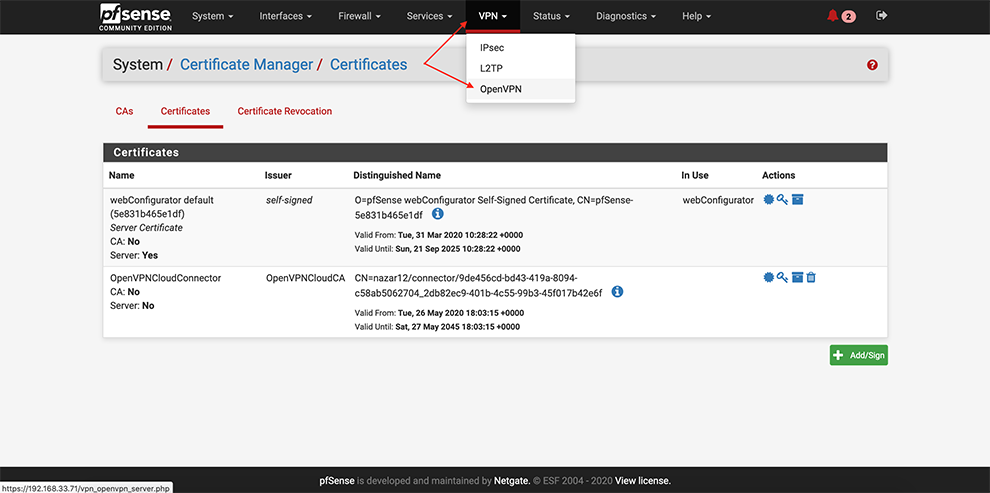
Configuring pfSense
From the main menu go to System → Cert. Manager
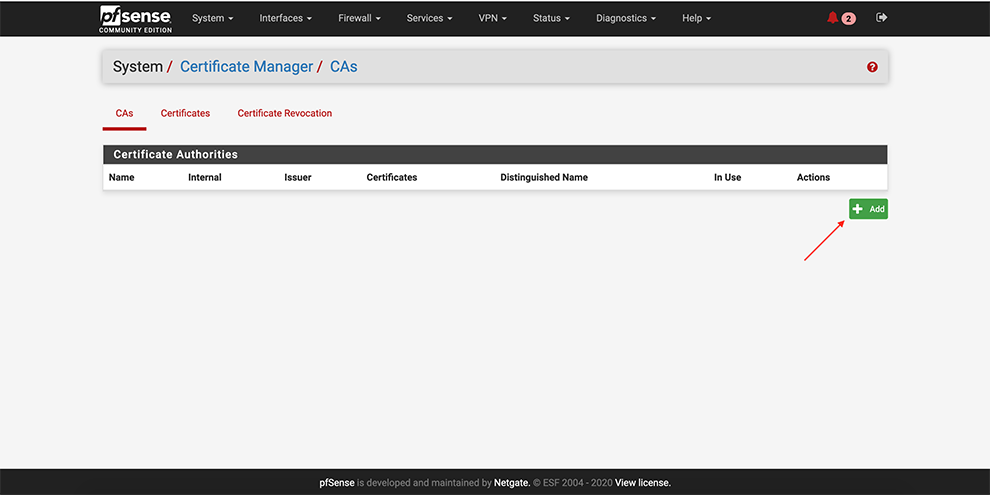
Next, go select CAs → Add
Select Method Import an existing Certificate Authority
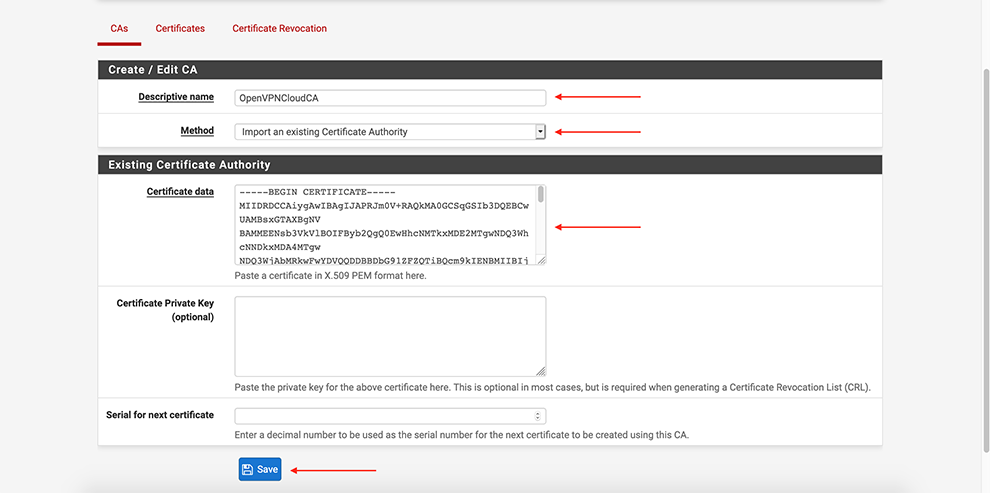
Set some “Descriptive name”
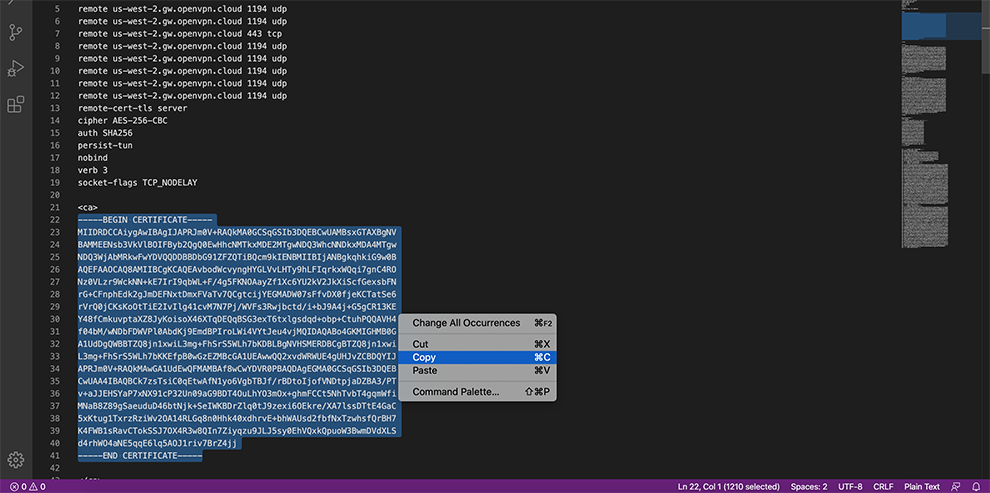
In the Certificate Data space, copy the data from the Connector’s Profile: everything between Certificate Authority <ca> and </ca>
Click Save
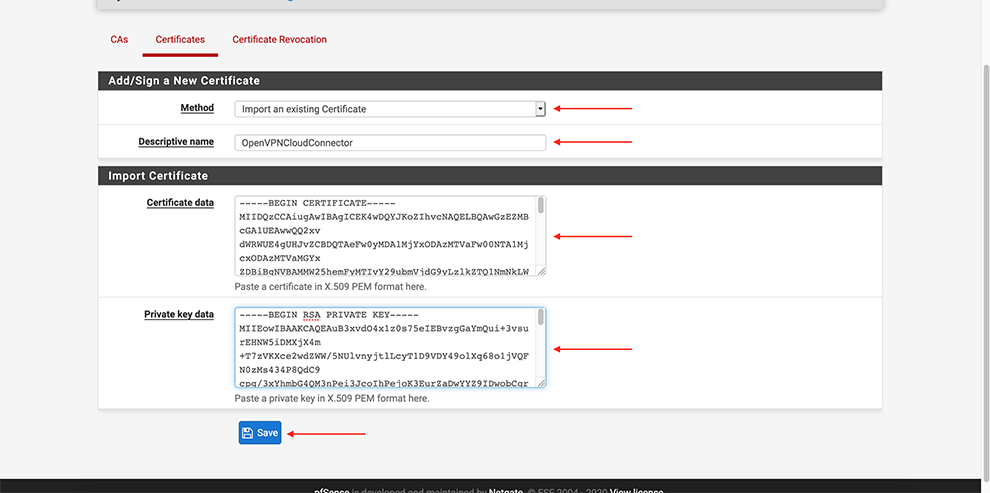
Certificates → Add
Select Method Import an existing Certificate
Set some “Descriptive name”
In the Certificate Data space, copy the data from the Connector’s Profile: everything between the Certificate data and between the Private key data <cert> and <cert>.
In the Private key data space, copy the data from the Connector’s Profile: everything between <key> and <key>.
In certificate type, choose: X.509 (PEM)
Click Save
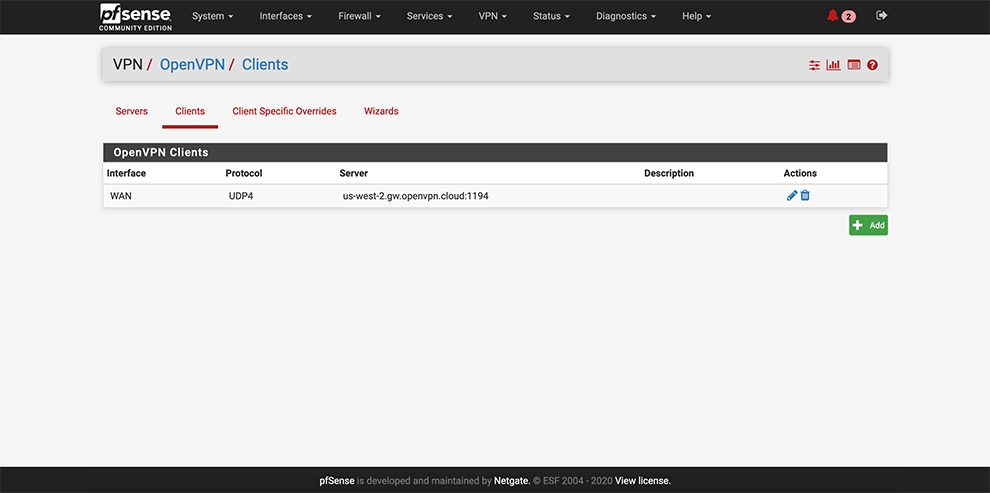
From the main menu go to VPN → OpenVPN
Select Clients → Add a client
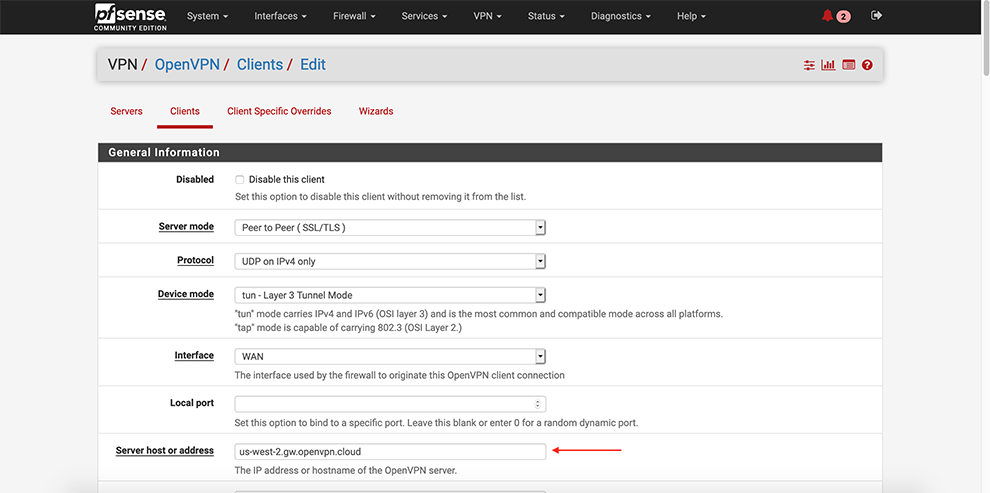
Enter preferable PGMT Hostname of the Cloud Connexa server in the Server Host or address field. Refer to Region Locations to find hostnames if needed.
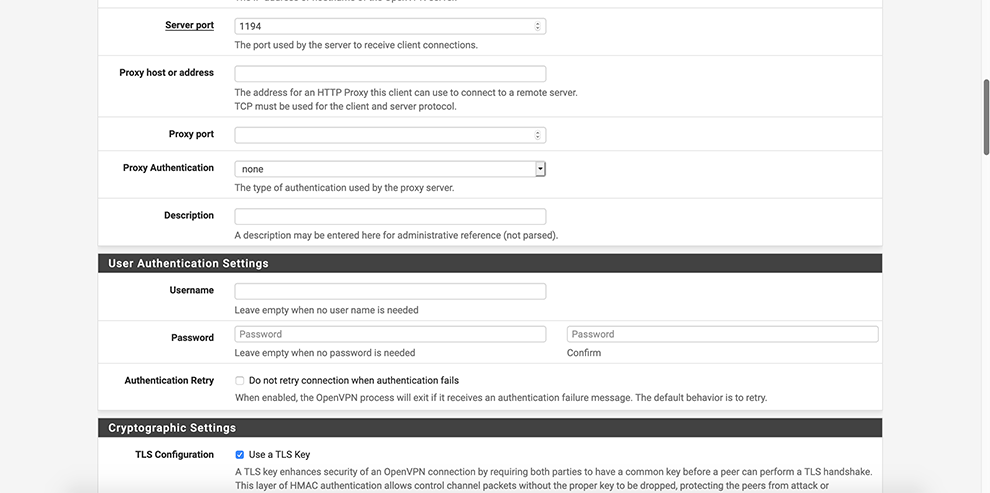
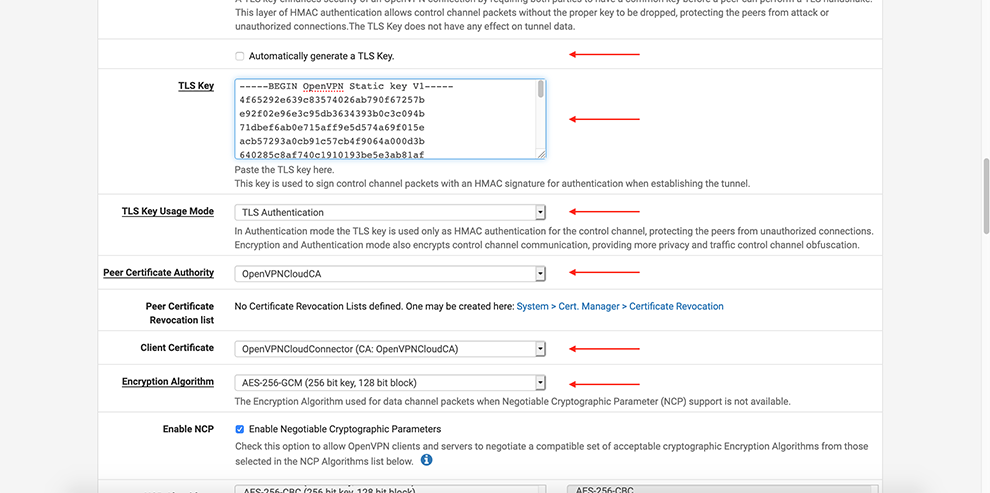
Uncheck Automatically generate a TLS Key
In the TLS Key space, copy the data from the Connector’s Profile: everything between the TLS Key <tls-auth> and <tls-auth>.
Select your Certificate Authority in the Peer Certificate Authority drop-down menu
Select your Certificate in the Client Certificate drop-down menu
Select AES-256-GCM in the Encryption Algorithm Data Encryption Algorithms drop-down menu
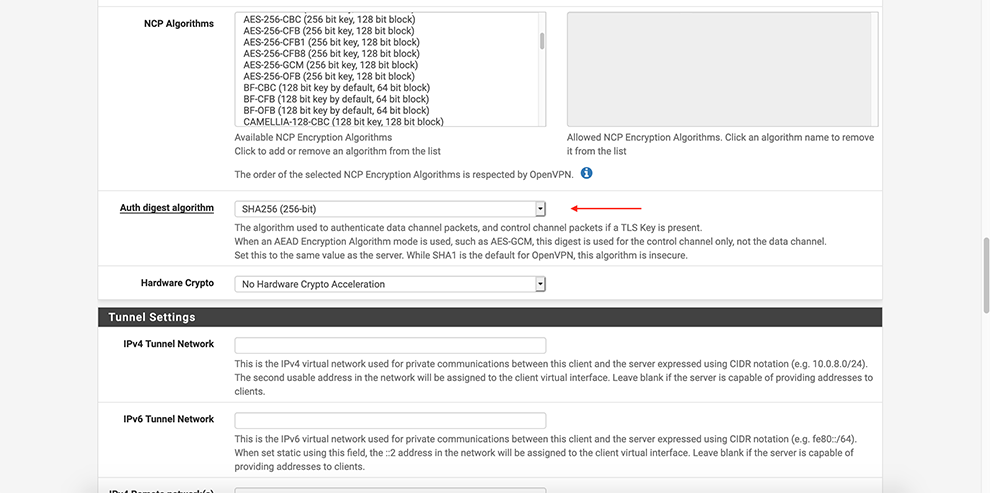
Select SHA256 in the Auth Digest Algorithm drop-down menu
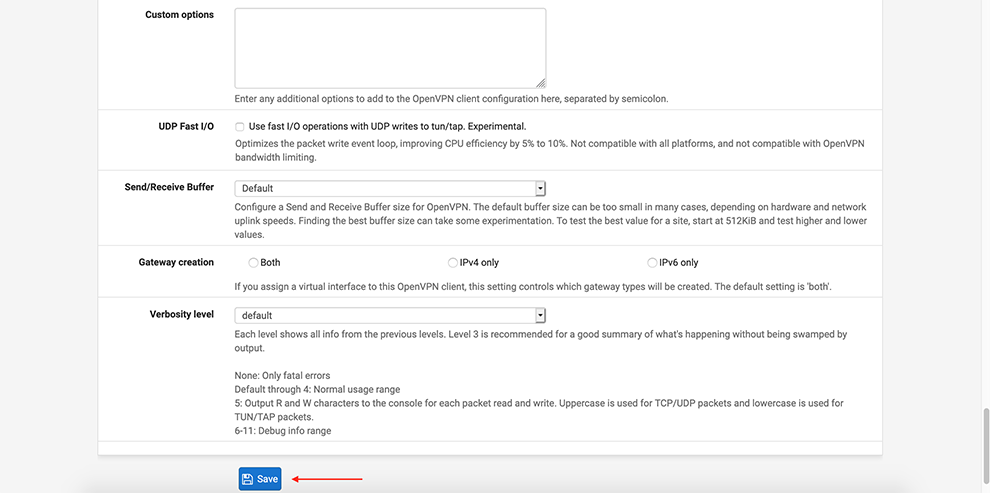
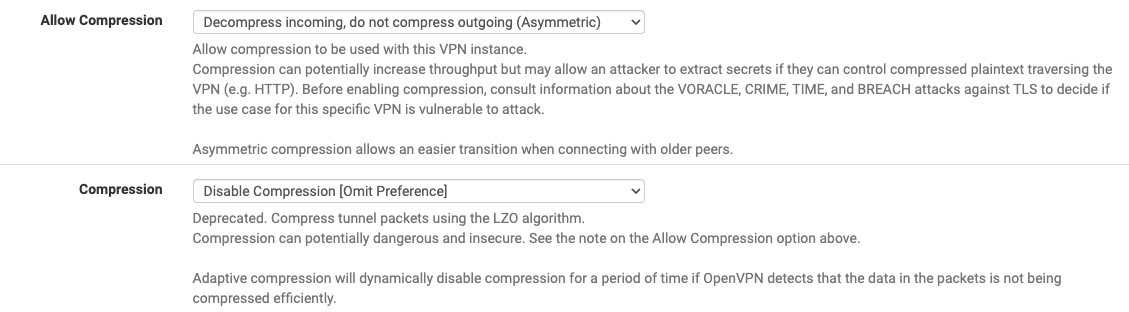
Select Disable Compression in the Compression drop-down menu
In Allow compression drop-down choose: Decompress Incoming, do not compress outgoing (asymmetric)
In Compression drop-down choose: Disable Compression [Omit Preference].
Click Save
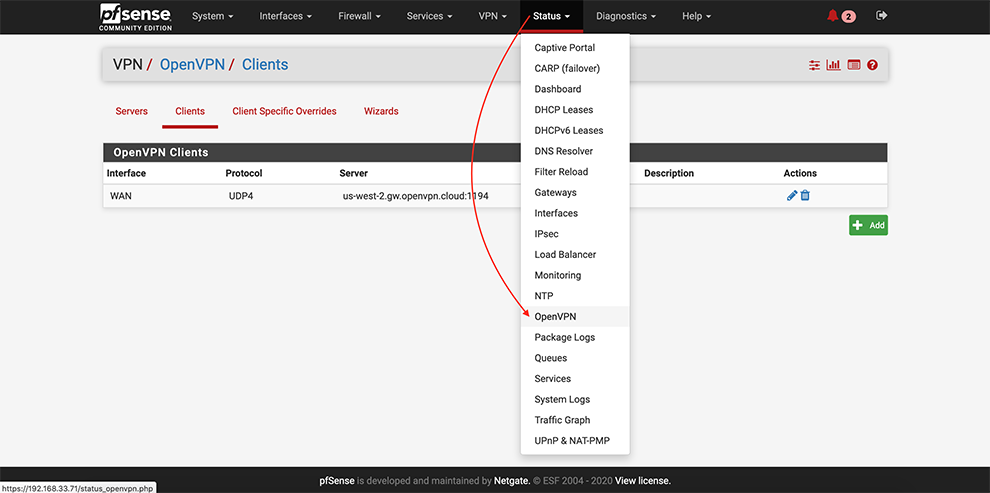
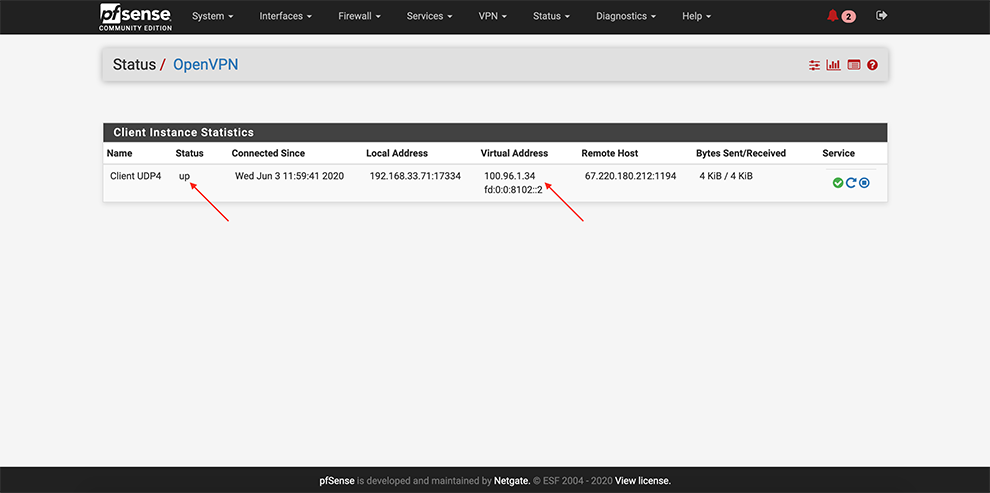
From the main menu go to Status → OpenVPN
Ensure that OpenVPN service is up and Virtual IP Addresses are assigned
Enable the tunnel interface by carrying out the steps below:
Interfaces > assignment
Add > Choose the tunnel created for CloudConnexa. It will be shown as LAN. Click on the name > Enable it and change the name if desired.
Click Save.
Apply changes.
On Status > Interfaces check that the tunnel interface is added with status: Up.
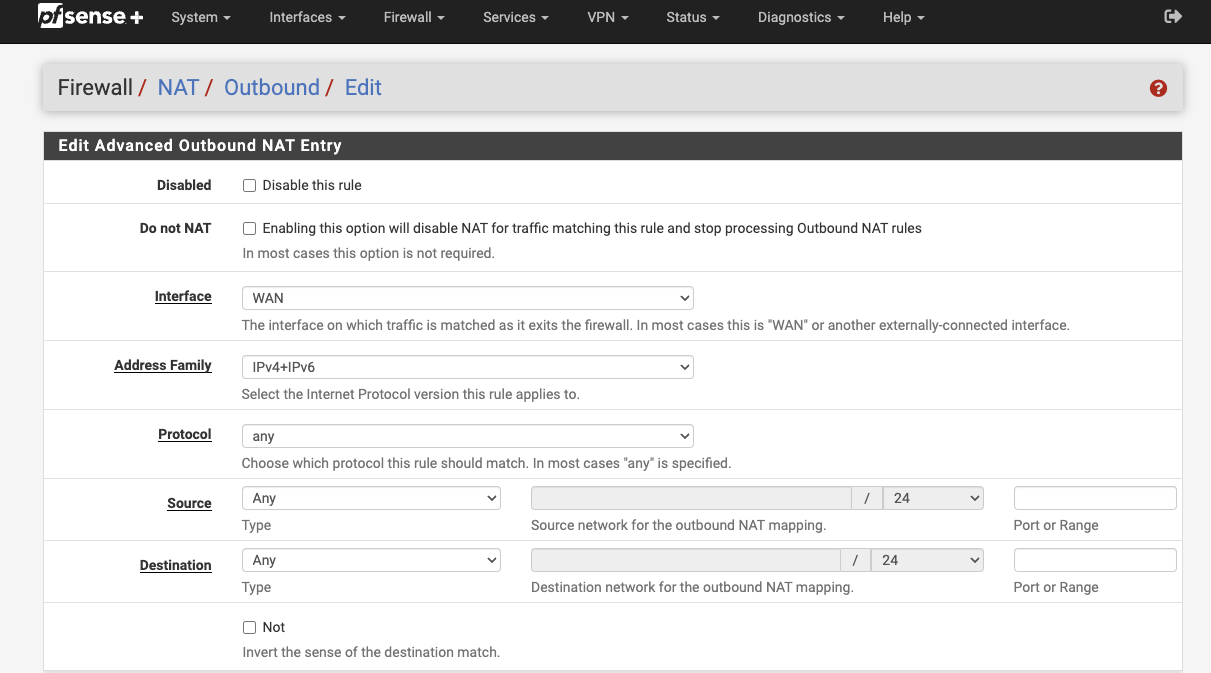
Enable NAT by carrying out the steps below:
Firewall > NAT > Outbound
Outbound NAT Mode: Hybrid
Add > interface Pointing to local resources
Interface > WAN
Address Family > IPv4+IPv6
Protocol > Any
Source > Any
Destination > Any
Click Save
Apply Changes
Note
If there are any problems, please check Status > System logs > Firewall to ensure that there are no firewall rules blocking traffic.
Tutorial: Configure a Teltonika Router To Connect to CloudConnexa
This tutorial contains instructions on how to use a Teltonika router and configure it to use a Connector profile to connect to CloudConnexa and make the network part of your WPC.
Introduction
You can configure a Teltonika-compatible router for Network Connector deployment. You must use specific sections from the OpenVPN Connector Profile and apply them to the associated router settings.
Downloading the Connector profile
Sign in to the CloudConnexa Administration portal at https://cloud.openvpn.com.
Navigate to Networks.
Select Networks.
Click the name of the router Network.
Click the Connectors tab.
Click the Deploy drop-down menu of the Connector you wish to modify.
Select Deploy Connector.
Click Provider Type drop-down menu.
Select Teltonika.
Click Download OVPN Profile.
Alternatively, you may download the profile by clicking the Network name, and the edit icon for the Network.
Or from the Connectors menu.
Configuring the Teltonika router
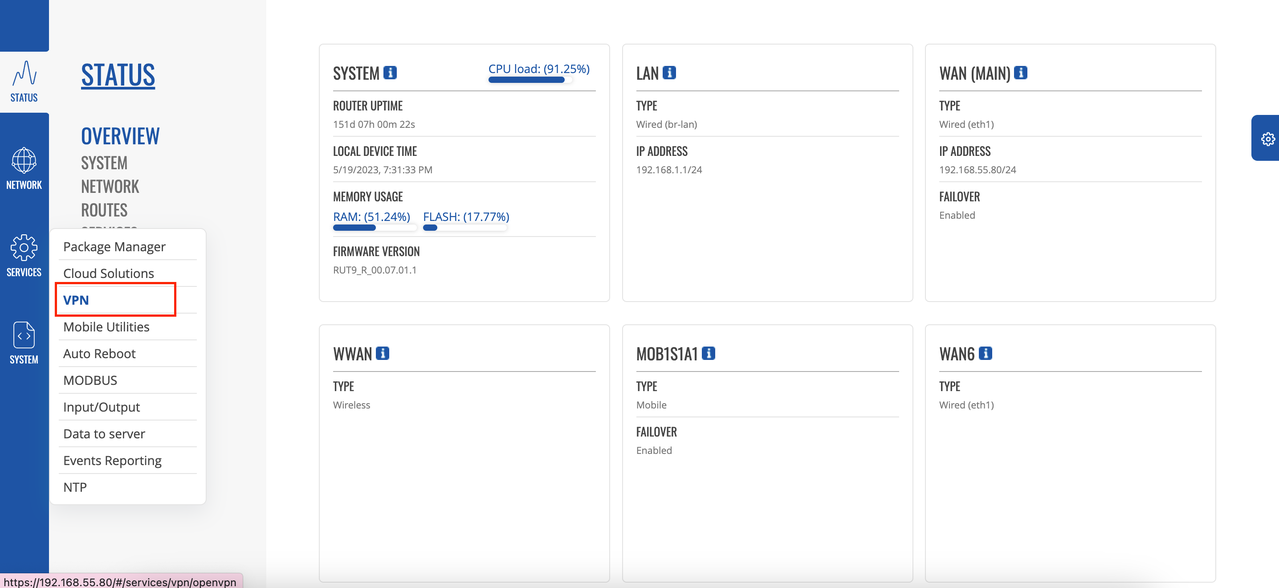
Sign in to the Teltonika router UI.
Access Services > VPN
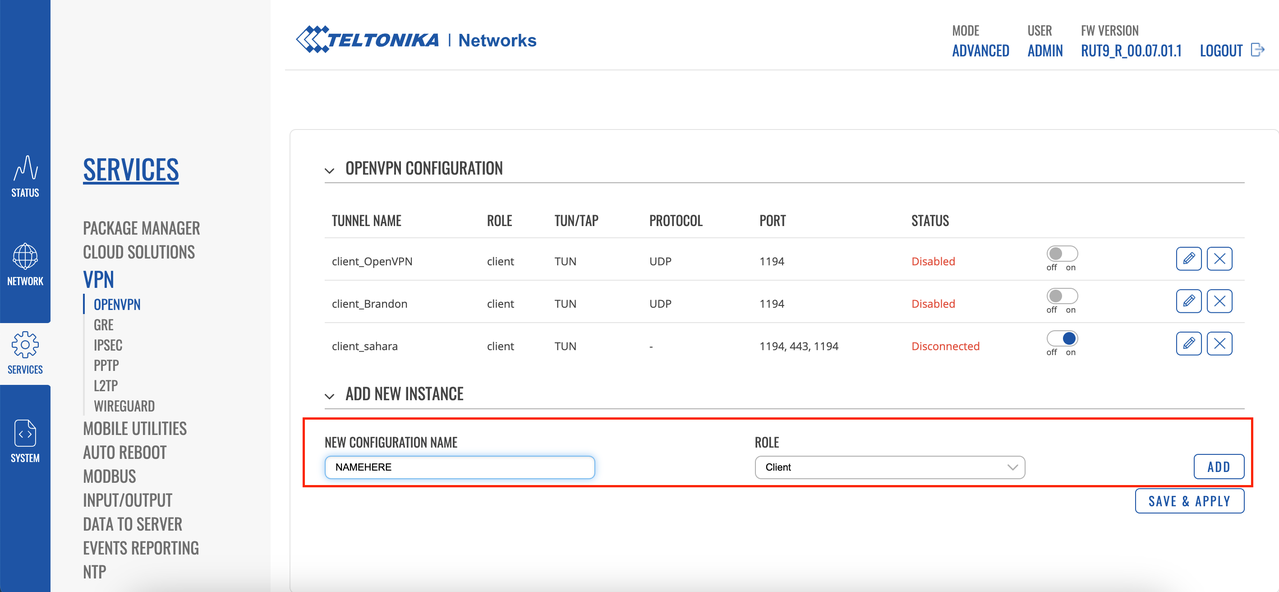
Click to select Client as the Role, add a name, and click Add New.
Click Edit for the newly created Profile.
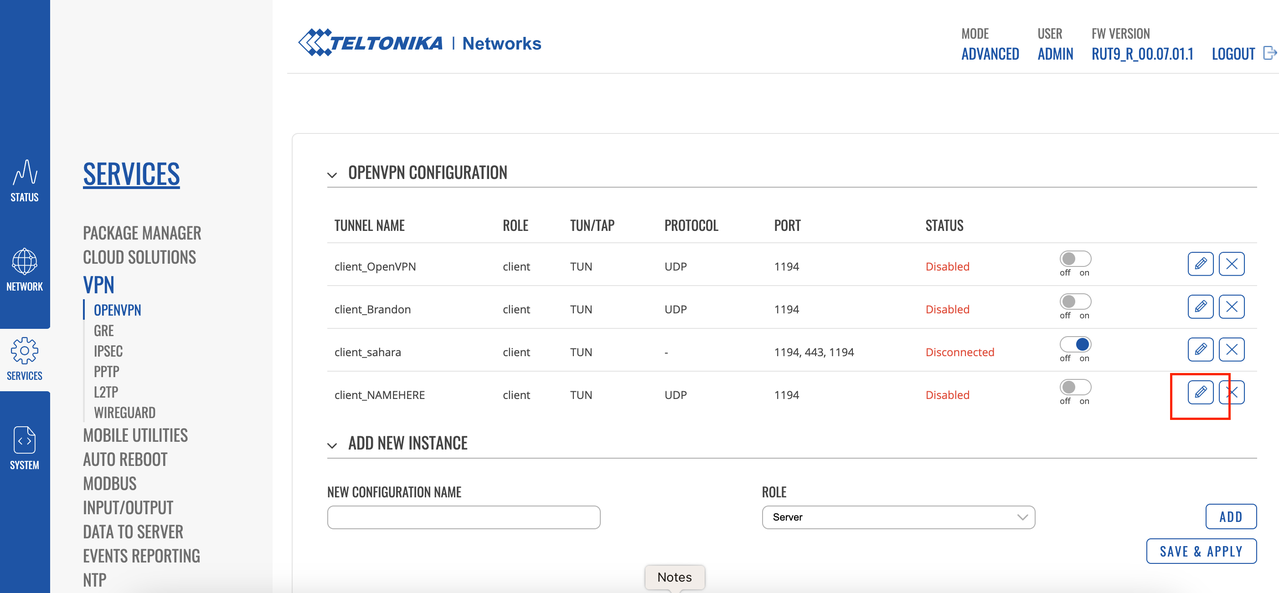
Set these parameters on the Main Settings screen.
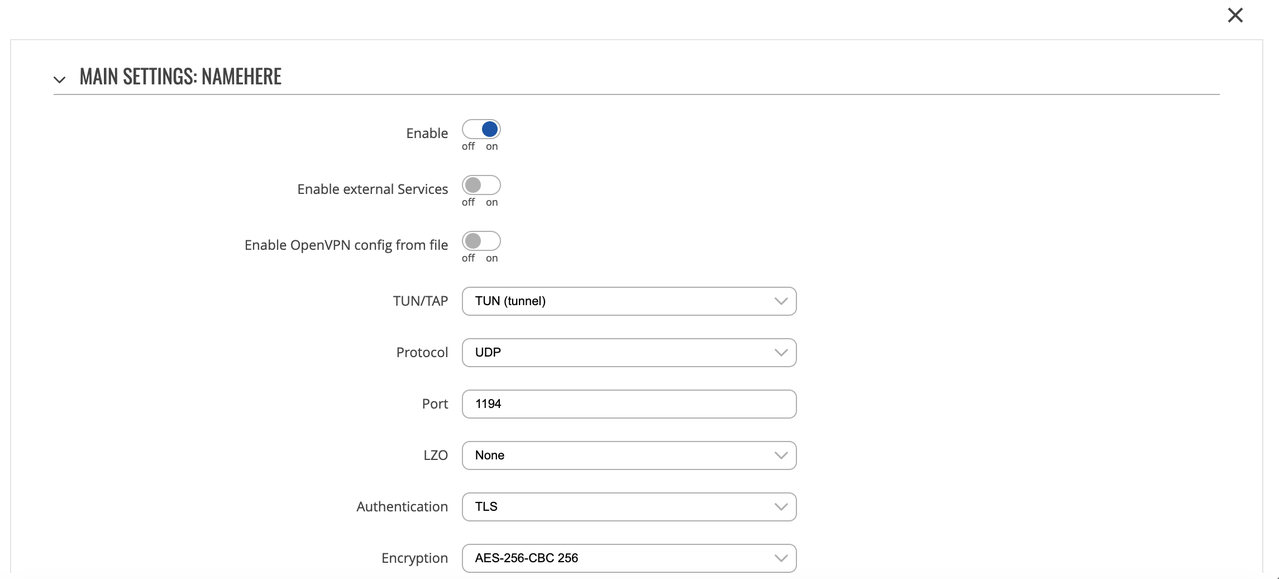
Parameter
Value
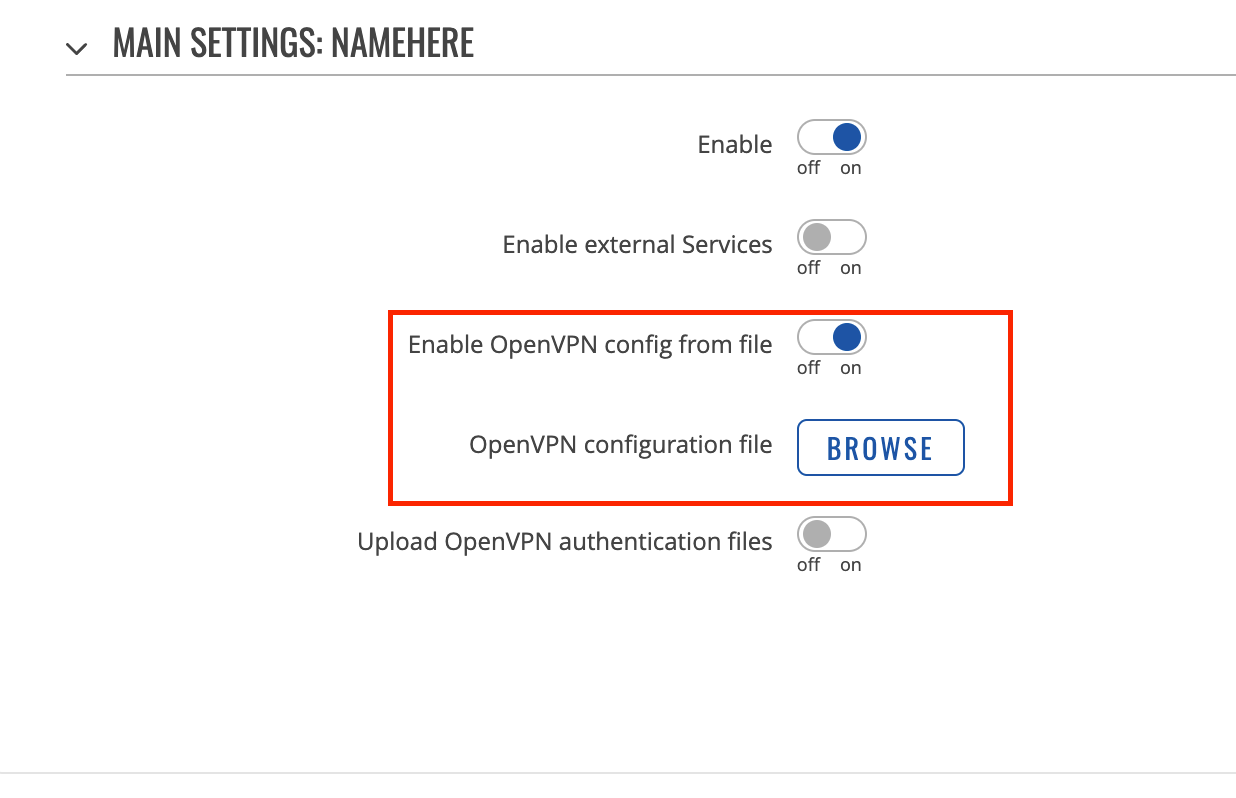
Enable OpenVPN config from file
Disable
Enable
Enable
TUN/TAP
TUN(Tunnel)
Protocol
UDP
Port
1194
LZO
Disable
Authentication
TLS
Encryption
AES-256-CBC-256
TLS cipher
All
Remote Host/IP address
Open the
.ovpnProfile in a text editor, and copy and paste the Host address.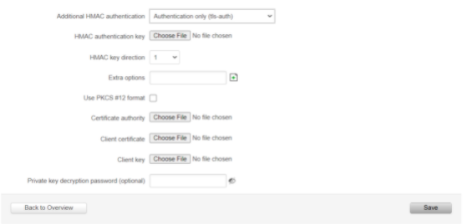
Resolve retry
Infinite
Keep alive
A helper directive designed to simplify the expression of –ping and –ping-restart. This option can be used on both the client and server side, but it is enough to add this on the server side because it will push appropriate –ping and –ping-restart options to the client. If used on both server and client, the values pushed from the server will override the client local values.
Remote Network IP address
Network IP Address
Remote Network IP netmask
Network subnet mask
HMAC authentication algorithm
SHA256
Additional HMAC authentication
Authentication only (tls-auth)
HMAC authentication key
1. In the
.ovpnProfile, copy the content between the<tls-auth> and </tls-auth> tags and paste them into a new file.2. Be sure that you include all of the --- BEGIN OpenVPN Static key V1--- and ---END OpenVPN Static key V1--- lines in the new file. There should be a total of two such lines.
3. When copying the contents into a new file, be sure to delete the starting <tls-auth> tag and the ending </tls-auth> tag.
4. Save the new file with a
.keyextension and upload it.HMAC key direction
1
Extra options
Not filed
Use PKCS #12 format
Disable
Certificate authority
1. In the
.ovpnProfile, copy the content between the <ca> and </ca> tags and paste them into a new file.2. Be sure that you include all of the ---BEGIN CERTIFICATE--- and ---END CERTIFICATE--- lines in the new file. There should be a total of four such lines.
3. When copying the contents into a new file, be sure to delete the starting <ca> tag and the ending </ca> tag.
4. Save the new file with a
.crtextension and upload it.Client certificate
1. In the
.ovpnProfile, copy the content between the <cert> and </cert> tags and paste them into a new file.2. Be sure that you include all of the ---BEGIN CERTIFICATE--- and ---END CERTIFICATE--- lines in the new file. There should be a total of two such lines.
3. When copying the contents into a new file, be sure to delete the starting <cert> tag and the ending </cert> tag.
4. Save the new file with a
.crtextension and upload it.Client key
1. In the .ovpn Profile, copy the content between the <key> and </key> tags and paste them into a new file.
2. Be sure that you include all of the ---BEGIN RSA PRIVATE KEY--- and ---END RSA PRIVATE KEY--- lines in the new file. There should be a total of two such lines.
3. When copying the contents into a new file, be sure to delete the starting <key> tag and the ending </key> tag.
4. Save the new file with a
.keyextension and upload it.Private key decryption password (optional)
Not required
Save your changes, and restart the WPC connection.
Navigate to Services > WPC and check that the configuration is enabled.
Navigate to Status > Network > OpenVPN and check that the status is Connected.
Tutorial: Configure a Ubiquiti (EdgeMAX) Router To Connect to CloudConnexa
This tutorial contains instructions on how to use a Ubiquiti (EdgeMAX) router and configure it to use a Connector profile to connect to CloudConnexa and make the network part of your WPC.
Introduction
You can configure a Ubiquiti compatible router for Network Connector deployment. You must use specific sections from the OpenVPN Connector Profile and apply them to the associated router settings.
Note
You must ensure that your router OS is EdgeRouter X v2.0 or newer.
Downloading the Connector profile
Sign in to the CloudConnexa Administration portal at https://cloud.openvpn.com.
Navigate to Networks and open your router Network.
Click the name of the router Network.
Click the Connectors tab.
Click the Deploy drop-down menu of the Connector you wish to modify.
Select Deploy Connector.
Click Provider Type drop-down menu.
Select Ubiquiti.
Click Download OVPN Profile and save it on your local computer.
Alternatively, you may download the profile by clicking the Network name, and the edit icon for the Network.
Or from the Connectors menu.
Configuring the Ubiquiti (EdgeMAX) router
Copy the
.ovpnProfile to the router using secure copy protocol (SCP) between your local computer and the router.Access terminal and execute this command:
scp <path to Profile/Profile_name.ovpn> <username>@<Router_external_IP_Address>:/config/auth,where<path to Profile/Profile_name.ovpn>is the absolute path for the.ovpnProfile, and the username is the to login on your router using SSH andRouterexternalIPAddressas the IP address of the router.Connect to the router via SSH.
Enter config mode and create a new interface, and commit and save your changes. Use these commands:
configureset interfaces
openvpn vtun0 config-file /config/auth/Profile.ovpnNote
OpenVPN tunnel interface must be name
vtun<num>commitsaveexitConnect to the router through HTTPS.
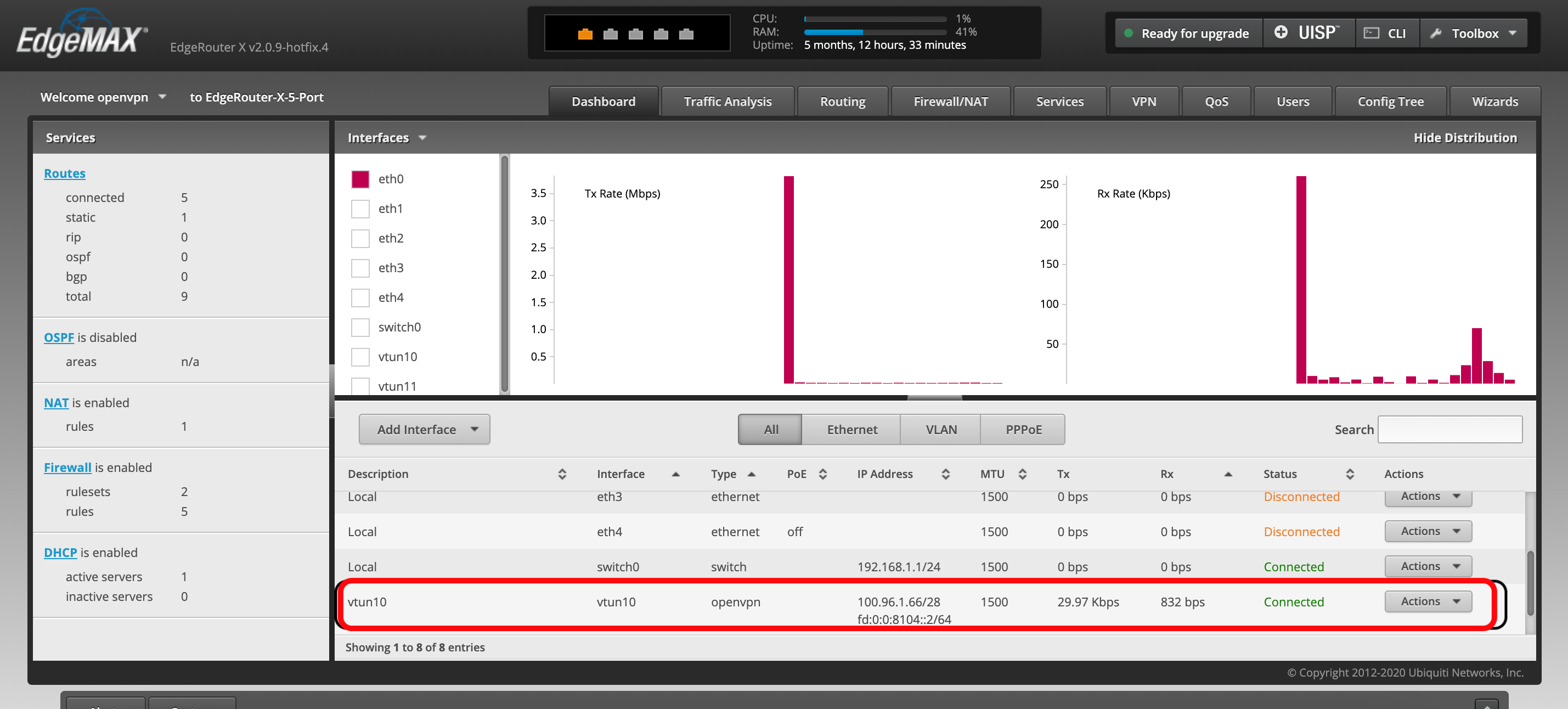
Navigate to the Dashboard tab.
Check that your newly created interface <interface_name> exists with an interface type of openvpn, a Connected status, and an assigned IP address.