Protect and Nurture Your Business with Our Zero Trust VPN
Focus on scaling your business while we handle your network security.

Trusted by 20,000+ organizations for over two decades.
ZERO TRUST VPN
The size of your team doesn't dictate your cybersecurity strategy. Our secure, scaleable Zero Trust VPN can help:
 97%
97%
Percentage of small and mid-size businesses that find VPN solutions to be critical.
* Report: Secure Access Technology Trends; Enterprise Strategy GroupThreat actors target small and mid-size businesses without network security measures. A Zero Trust VPN can help reduce the risk of a cyberattack.
Get Started NowCompliant with global security standards





Enterprise-grade security for businesses of all sizes
Self-hosted or cloud-delivered: We've got your network security covered.
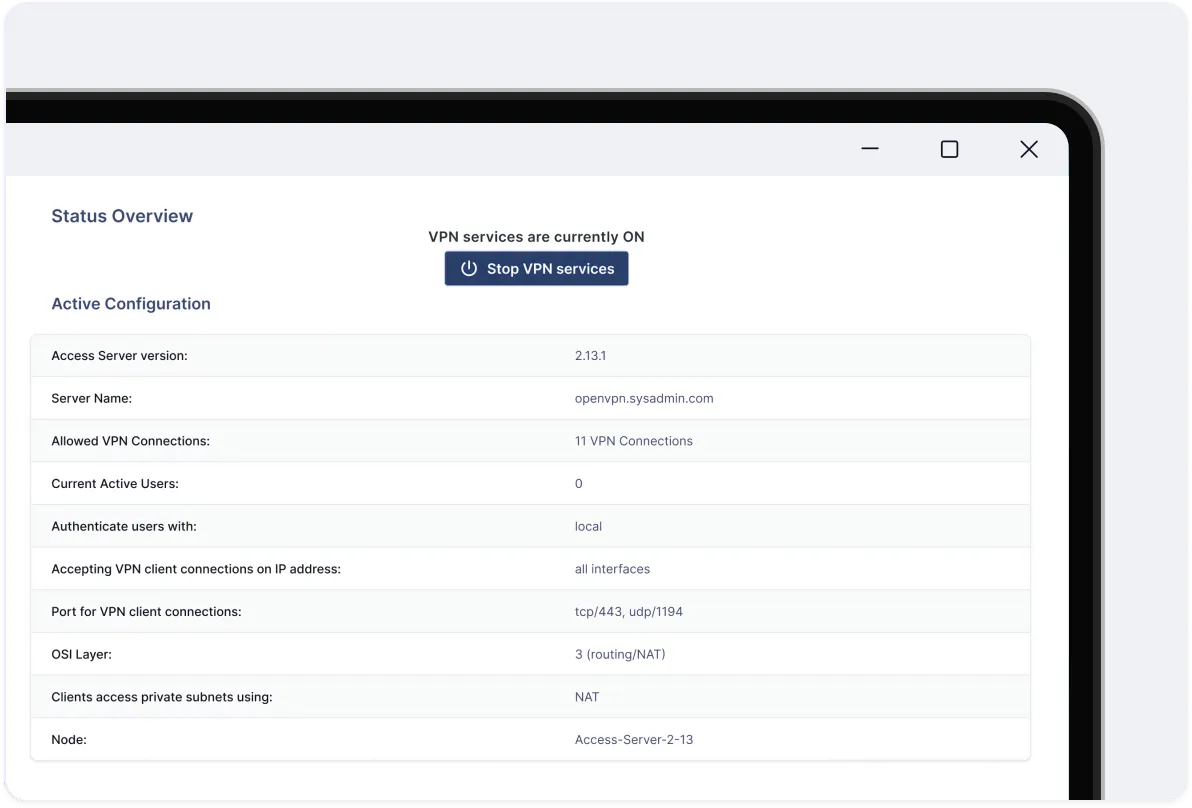
Access Server
Access Server gives you complete control over your security architecture with customizable access policies and private tunneling.
Deploy on IaaS providers, Docker, Linux, Hyper-V, and VMware ESXi
Get started fast with a ready-to-use templates
Protect your data by routing internet traffic through the Access Server
Enforce access policies with identity, device, and IP verification
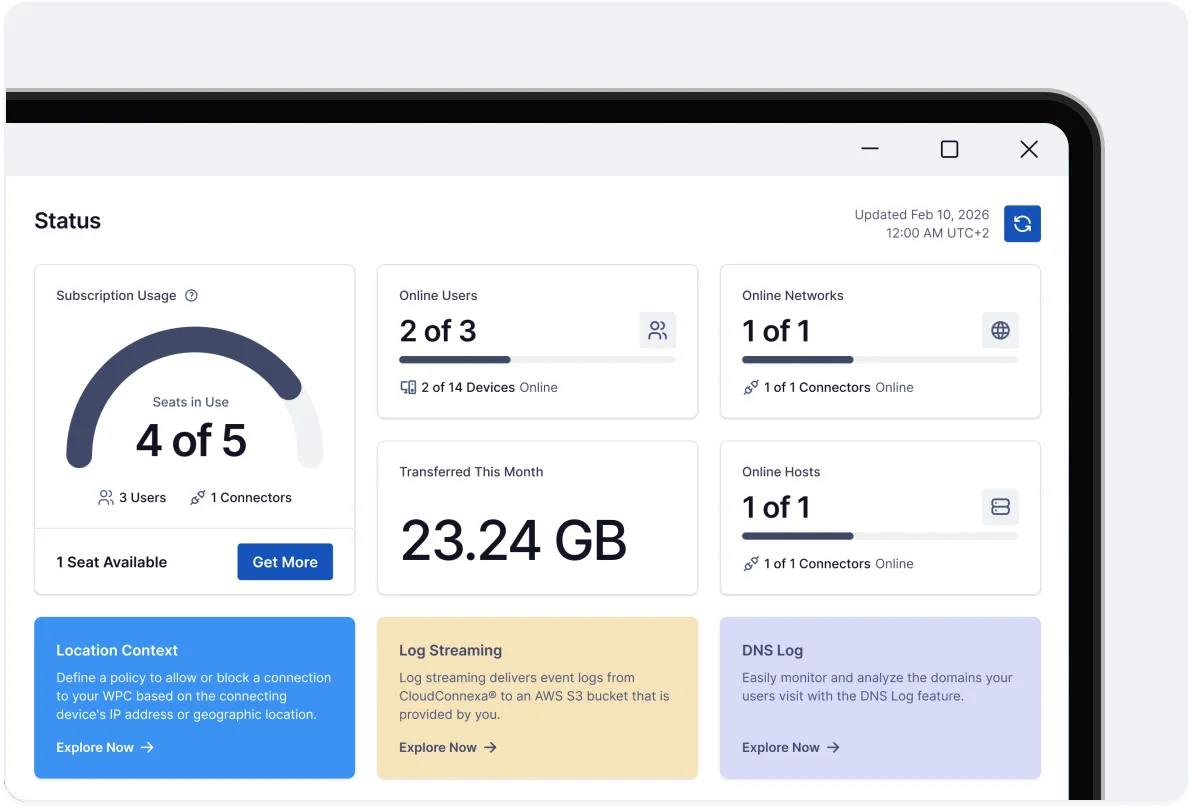
CloudConnexa®
Connect your applications, private networks, workforce, and IoT devices — without complex, hard-to-scale hardware or self-managed server software.
Enforce security with a full suite of Zero Trust controls
Connect networks seamlessly using OpenVPN or IPsec
Enhance protection with content filtering and IDS/IPS
Simplify routing with domain-based traffic rules
The most popular VPN for small and mid-size businesses
20K
Business Customers4M+
UsersFast
Performance and Deployment#1
Business VPN on G2
What's new from OpenVPN
 NewsJun 10, 2025
NewsJun 10, 2025OpenVPN DCO Added to Linux Kernel for Built-In Speed and Security
Read More Customer SpotlightJun 26, 2025
Customer SpotlightJun 26, 2025Maddox AI Is Revolutionizing Quality Control in Manufacturing
Read More PartnerMay 6, 2025
PartnerMay 6, 2025Ingram Micro is now an authorized distributor of OpenVPN
Read More ReportsApr 27, 2025
ReportsApr 27, 2025ESG Research Report: Secure Access Tech Trends
Read More