Secure your Enterprise Without Sacrificing Productivity or Compliance
Secure all of your data in transit with our Zero Trust VPN.
Secure all of your data in transit with our Zero Trust VPN.

ZERO TRUST VPN
 $5.4M
$5.4MThe average cost of a breach for enterprise-level companies.
* Varonis Report, 2024Bad actors are counting on human error, allowing them to get in and move between systems. Stop lateral movement and reduce the risk of a successful cyberattack with our Zero Trust VPN.
Get Enterprise




Self-hosted or cloud-delivered: We've got your network security covered.
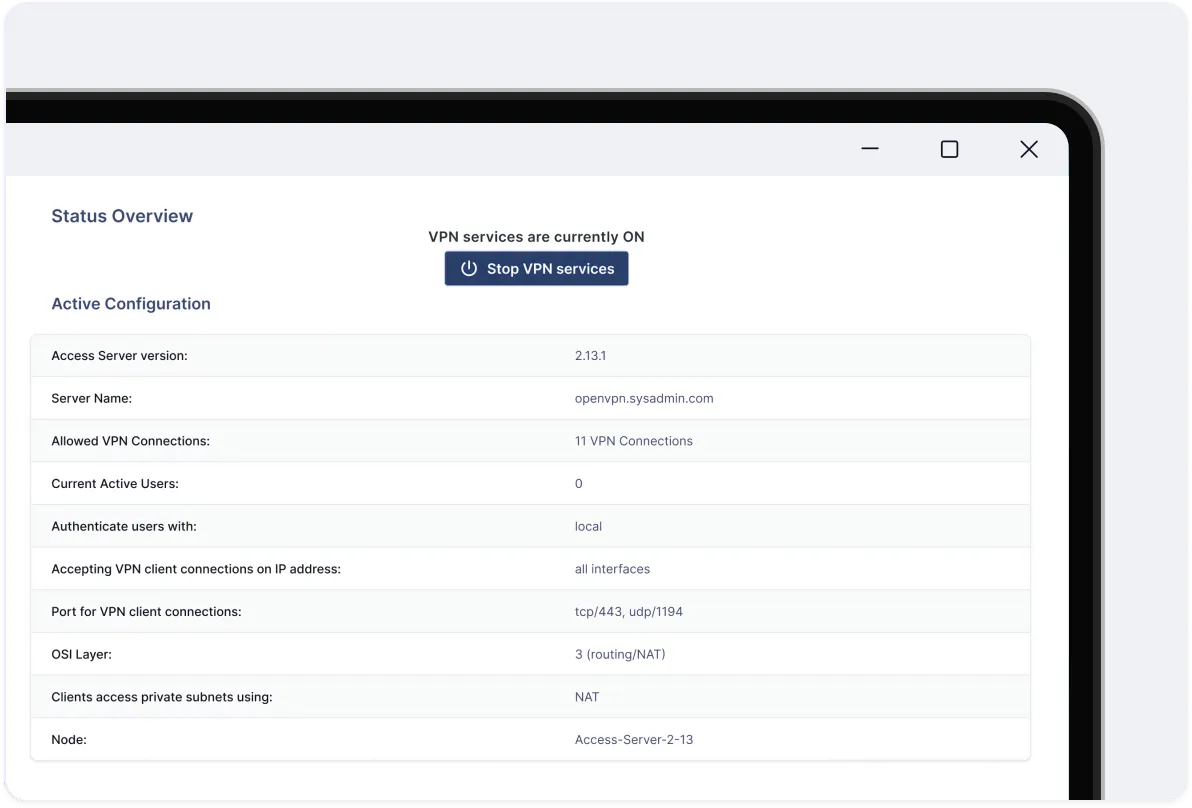
Access Server gives you complete control over your security architecture with customizable access policies and private tunneling.
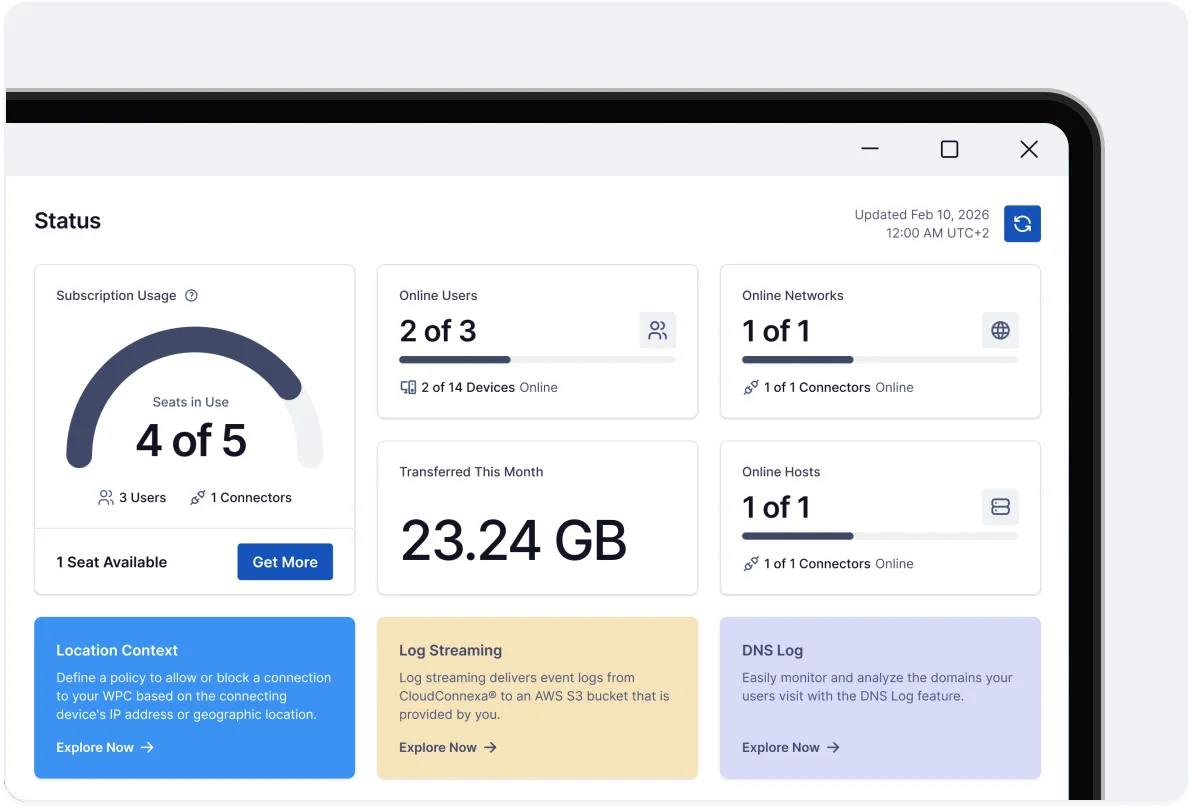
Connect your applications, private networks, workforce, and IoT devices — without complex, hard-to-scale hardware or self-managed server software.
 NewsJun 10, 2025
NewsJun 10, 2025OpenVPN DCO Added to Linux Kernel for Built-In Speed and Security
Read More Customer SpotlightJun 26, 2025
Customer SpotlightJun 26, 2025Maddox AI Is Revolutionizing Quality Control in Manufacturing
Read More PartnerMay 6, 2025
PartnerMay 6, 2025Ingram Micro is now an authorized distributor of OpenVPN
Read More ReportsApr 27, 2025
ReportsApr 27, 2025ESG Research Report: Secure Access Tech Trends
Read More