Shut Out Threats. Keep IoT Talking.
Get end-to-end encryption and IoT security solutions for all of your company’s devices.

Get end-to-end encryption and IoT security solutions for all of your company’s devices.

Create a secure virtual network to protect all traffic shared by your IoT devices Access Server gives businesses of all sizes the enterprise-grade encryption, security, and reliability to support their growing IoT environment affordably.
Learn More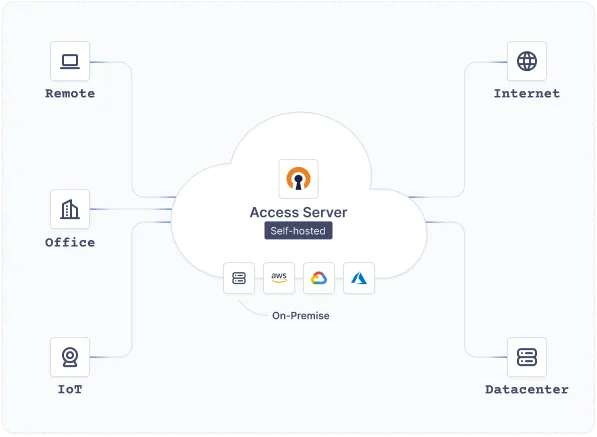
CloudConnexa supports OpenVPN protocol and the OpenVPN Connect application is available for every major device operating system to provide extensive interoperability across the emerging IoT landscape. Easily create a separate private network for all IoT devices, or separate groups of devices through access control.
Learn More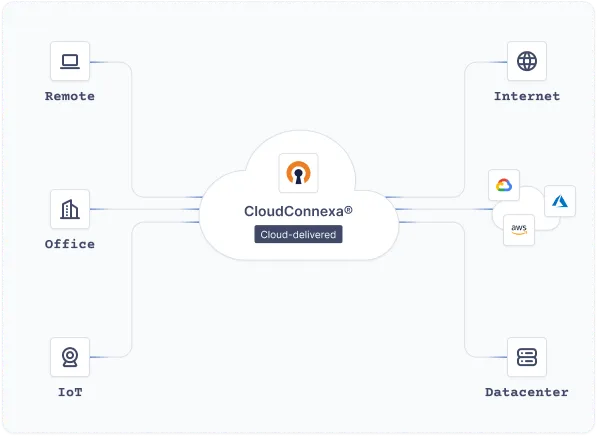
Easy to configure options, add users, and that it has two factor authentication built in. You can configure the system to allow connections on common ports so that you're able to connect from pretty much anywhere in the world.
Configuring and updating my own server is super simple. In my experience, I've always had some difficulty setting up hardware VPN appliances, but OpenVPN was no-nonsense.
The OpenVPN Access Server AMI is a great out of the box VPN solution for your AWS VPC...
OpenVPN offers users a very simple and secure VPN option that is both economical and quick to install. Users are able to easily install it on their client devices.
The availability of client software for all operating systems and mobile devices means my customers can connect regardless of their setup.
Excellent, flexible solution for our Azure environment.