The Best vs. the Rest: OpenVPN Alternatives & Comparison
Curious how OpenVPN stacks up? Let's dive in.
Curious how OpenVPN stacks up? Let's dive in.

 | Tailscale | Perimeter 81 | Twingate | NordLayer | |
|---|---|---|---|---|---|
| Configuration wizards | |||||
| Connection visibility | |||||
| DNS log | |||||
| Audit log | |||||
| SIEM integration |
 | Tailscale | Perimeter 81 | Twingate | NordLayer | |
|---|---|---|---|---|---|
| Full-mesh topology | |||||
| Multi-region | |||||
| Kernel-level encryption support |
 | Tailscale | Perimeter 81 | Twingate | NordLayer | |
|---|---|---|---|---|---|
| Built-in IDS/IPS | |||||
| Built-in content filtering | |||||
| DNS security |
 | Tailscale | Perimeter 81 | Twingate | NordLayer | |
|---|---|---|---|---|---|
| Device posture enforcement (ZTNA) | |||||
| Location-based access (ZTNA) | |||||
| Identity-based access (ZTNA) | |||||
| Multi-factor authentication | |||||
| Built-in certificate management | |||||
| Application micro-segmentation | |||||
| Identity provider integration |
 | Tailscale | Perimeter 81 | Twingate | NordLayer | |
|---|---|---|---|---|---|
| Routing using domain names (IP overlap resolution) | |||||
| Split-tunneling using domain names |
 | Tailscale | |
|---|---|---|
| Easy configuration | ||
| Scalable | ||
| Automatic key rotation | ||
| Peer-to-peer by default | ||
| Based on end-to-end open source | ||
| Flexible server configuration | ||
| Multiple use cases | ||
| Unlimited free tier | ||
| Native support for IPv6 |
Secure connections for every use case.

Learn more about all OpenVPN capabilities.
Self-hosted or cloud-delivered: We've got your network security covered.
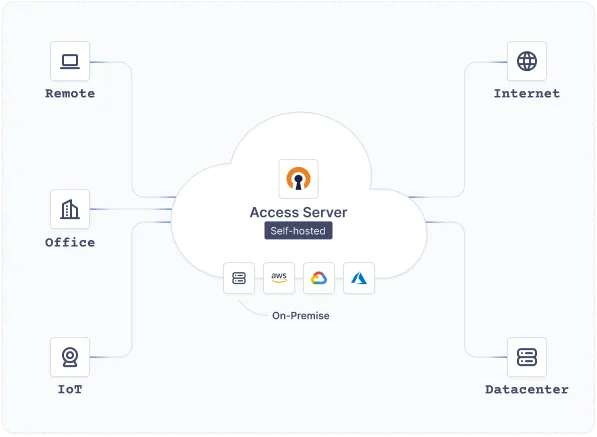
Access Server gives you complete control over your security architecture with customizable access policies and private tunneling.
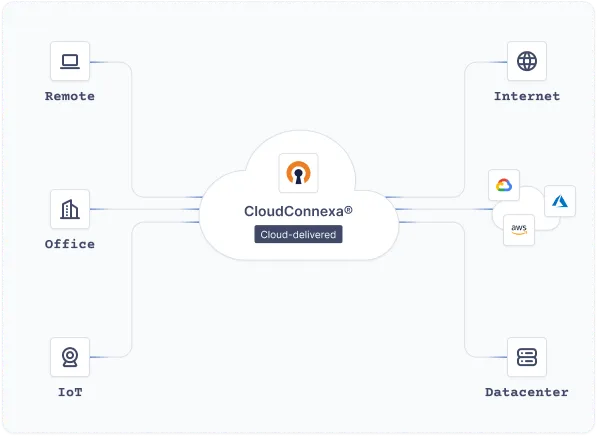
Connect your applications, private networks, workforce, and IoT devices — without complex, hard-to-scale hardware or self-managed server software.




