Introduction
Thank you for choosing Access Server.
This manual provides documentation for the Admin Web UI in Access Server. It walks you through using the web-based interface to configure your VPN server—no advanced Linux knowledge required.
Access Server can be installed and used for free with up to two simultaneous VPN connections. Additional connections and features are available through subscription licensing.
For more information about Access Server and licensing options, visit the product page on the OpenVPN website.
You can install Access Server on any officially supported Linux distribution.
Refer to our system requirements for the most up-to-date list of compatible operating systems and platform recommendations.
Glossary of terms
We commonly use these terms when referring to topics related to Access Server:
- Access Server
The self-hosted OpenVPN solution that provides secure VPN connections through an encrypted tunnel. It includes integrated certificate management, support for internal and external authentication systems, and bundled client software.
- Admin Web UI
The web-based interface for administrators to configure Access Server settings, manage users and groups, view server status, and control access policies.
- Authentication Method (auth method)
The mechanism Access Server uses to verify user identity. This can include local authentication, LDAP, RADIUS, PAM, or SAML-based single sign-on.
- Client Web UI (CWS)
A web portal hosted by Access Server that end users can access to download connection profiles and preconfigured OpenVPN Connect apps for supported platforms.
- Connection Profile
A file that contains the necessary configuration for a VPN client to securely connect to the Access Server. It doesn't contain user credentials.
- Group
A collection of users with shared access settings or permissions. Groups can be used to simplify management of routing, access control, and authentication behavor.
- Multi-Factor Authentication (MFA)
An additional layer of authentication, typically using a time-based one-time password (TOTP) generated by an app on the user’s device. Used alongside a username and password for added security.
- OpenVPN Connect
The official VPN client developed by OpenVPN Inc., available for Windows, macOS, Android, and iOS. It is the recommended client for connecting to Access Server. For Linux and other platforms, open-source OpenVPN clients are available.
- User
A person who authenticates to Access Server to establish a VPN connection. In technical terms, a user also refers to an account within Access Server that defines identity, permissions, and credentials.
- User Credentials
A set of login details used to authenticate to Access Server, typically consisting of a username and password. If MFA is enabled, a verification code is also required.
The ports listed below are the default settings; you can change them from the Admin Web UI.
Service | Protocol | Default Port |
|---|---|---|
OpenVPN daemons | UDP | 1194 |
OpenVPN daemons | TCP | 443 (shared) |
Web services | TCP | 443 (shared) |
Web services | TCP | 943 |
Clustering API | TCP | 945 |
Below, we provide three commonly supported network configurations. Depending on your needs, these configurations may be good starting points. After deploying your VPN server, Access Server creates a VPN IP subnet for easy routing and grants further protection when you enable access to private networks.
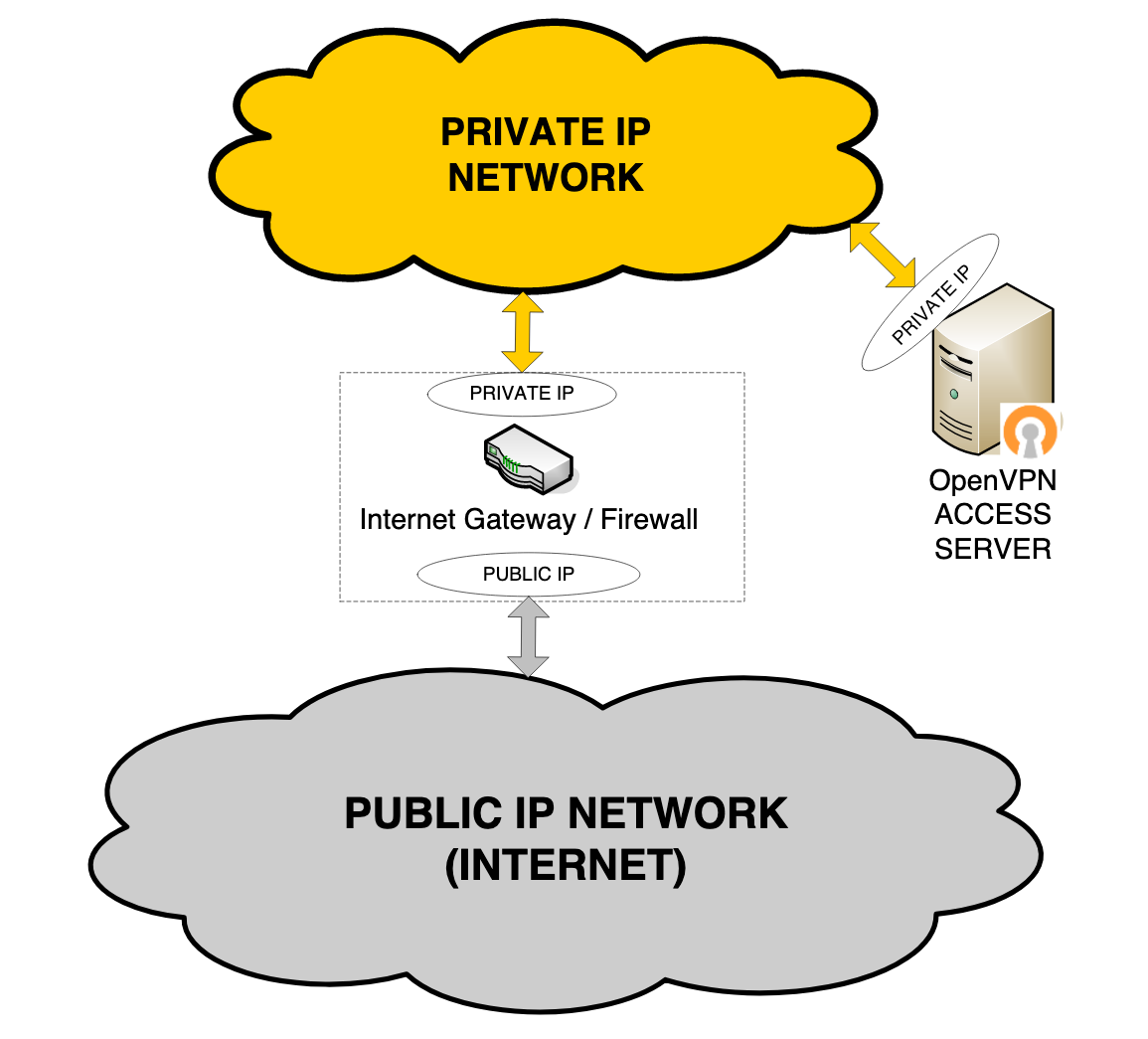
Use your Access Server to set up secure access to your private network behind a firewall. With this configuration, you deploy the Access Server on your internal corporate network. Users outside the network gain access using the VPN. In this configuration, Access Server has one network interface to the private network.
Note
Other interfaces may be present on the system that aren't utilized by Access Server.
For this configuration, the internet gateway forwards TCP/UDP port traffic from the public-facing IP address to Access Server's private IP address. At least one TCP port (typically port 443) is forwarded. That port can carry both the VPN tunnel traffic and the web client server/Connect client traffic.
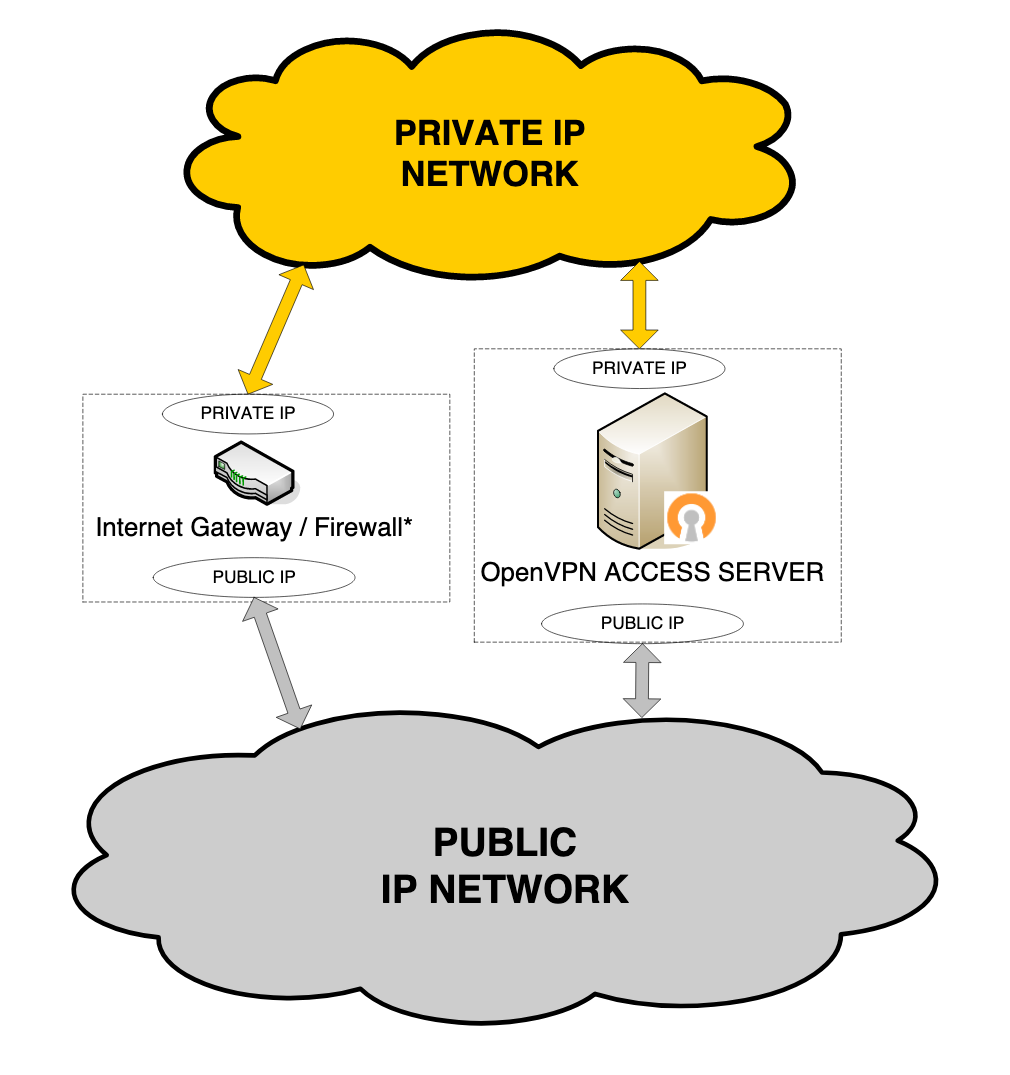
Use your Access Server on your internal corporate network with its own public IP address. Access Server communicates with clients outside the corporate network via its public IP interface. It uses another network interface to communicate with hosts on the private IP network and to propagate packets between VPN tunnels and the private network.
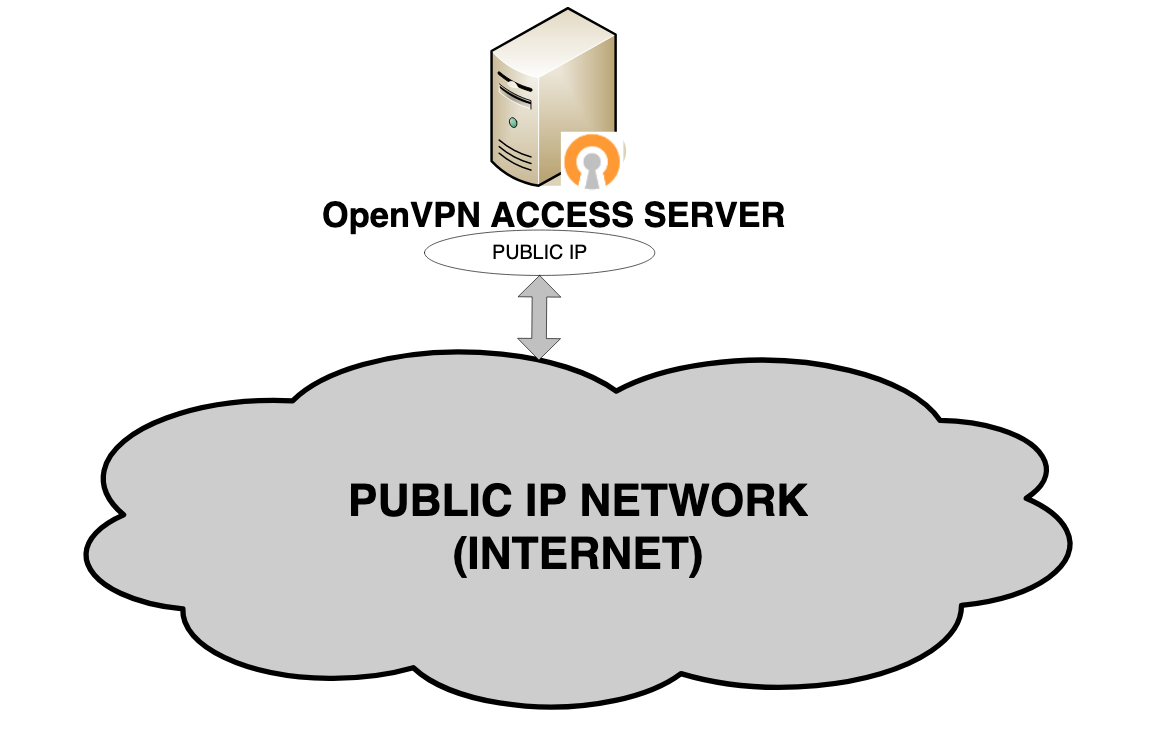
Use Access Server in a data center to create a virtual IP network to which all VPN clients can connect to communicate with services deployed on the server itself.
Accessing resources on a private network via Access Server
You can provide your users access to resources in your private network by establishing an OpenVPN tunnel from the user’s device to an Access Server installed on your private network. This is ideal for users away from the office who may need access to a shared NAS, network, databases, web servers, and more. Access Server, by default, integrates easily into your network by carrying out Source Network Address Translation (SNAT) on incoming packets.
Access Server within a private network with routing
Access Server provides access to connected VPN clients using NAT by default. This allows for easy integration into an existing private network. A limitation of NAT is that it is unidirectional. Communications initiated by the VPN clients to resources on your private network will be unimpeded, but to initiate communication directly from the private network to the VPN clients, you need to use routing. Refer to routing for an overview of configuring these settings.
Routed site-to-site-setup
You can connect two (or more) different networks together using a site-to-site setup with OpenVPN Access Server.
More use cases
We provide additional information about the following use cases: secure IoT communication, secure remote access, protecting access to SaaS, and enforcing zero trust access.
Refer to our getting started topic when you're ready.