Tutorial: Connect AWS VPC to CloudConnexa with IPsec using Transit Gateway
This tutorial shows how to configure an IPsec connection to your AWS VPC using the Transit Gateway. Once configured, site-to-site IPsec tunnel(s) connects your AWS VPC to the configured CloudConnexa Region. On a successful connection, your CloudConnexa users and other networks connected to any of CloudConnexa's Regions can access the AWS VPC.
By default, instances you launch into an Amazon VPC can't communicate with your own (remote) network. You can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection and configuring routing to pass traffic through the connection. Although VPN connection is a general term, in this documentation, a VPN connection refers to the connection between your VPC and your own on-premises network. Site-to-Site VPN supports Internet Protocol security (IPsec) VPN connections.
This tutorial shows how to configure an AWS Site-to-Site VPN connection using a Transit Gateway between your AWS VPC and a CloudConnexa Region.
An IPsec VPN connection to your VPC using the Virtual Private Gateway (VPG) only allows access to resources inside a VPC. Refer to Tutorial: Connect AWS to CloudConnexa with IPsec using VPG. Use this Transit Gateway configuration if you have configured public resources as Applications and IP services to be reachable via this VPC. The virtual private gateway provides connectivity to a single Amazon Virtual Private Cloud (Amazon VPC) in a Region. The transit gateway provides connectivity to multiple Amazon VPCs in a region as well as to the internet.
This configuration guide is based on the AWS knowledge center article: How do I access the internet using Site-to-Site VPN in my on-premises network?
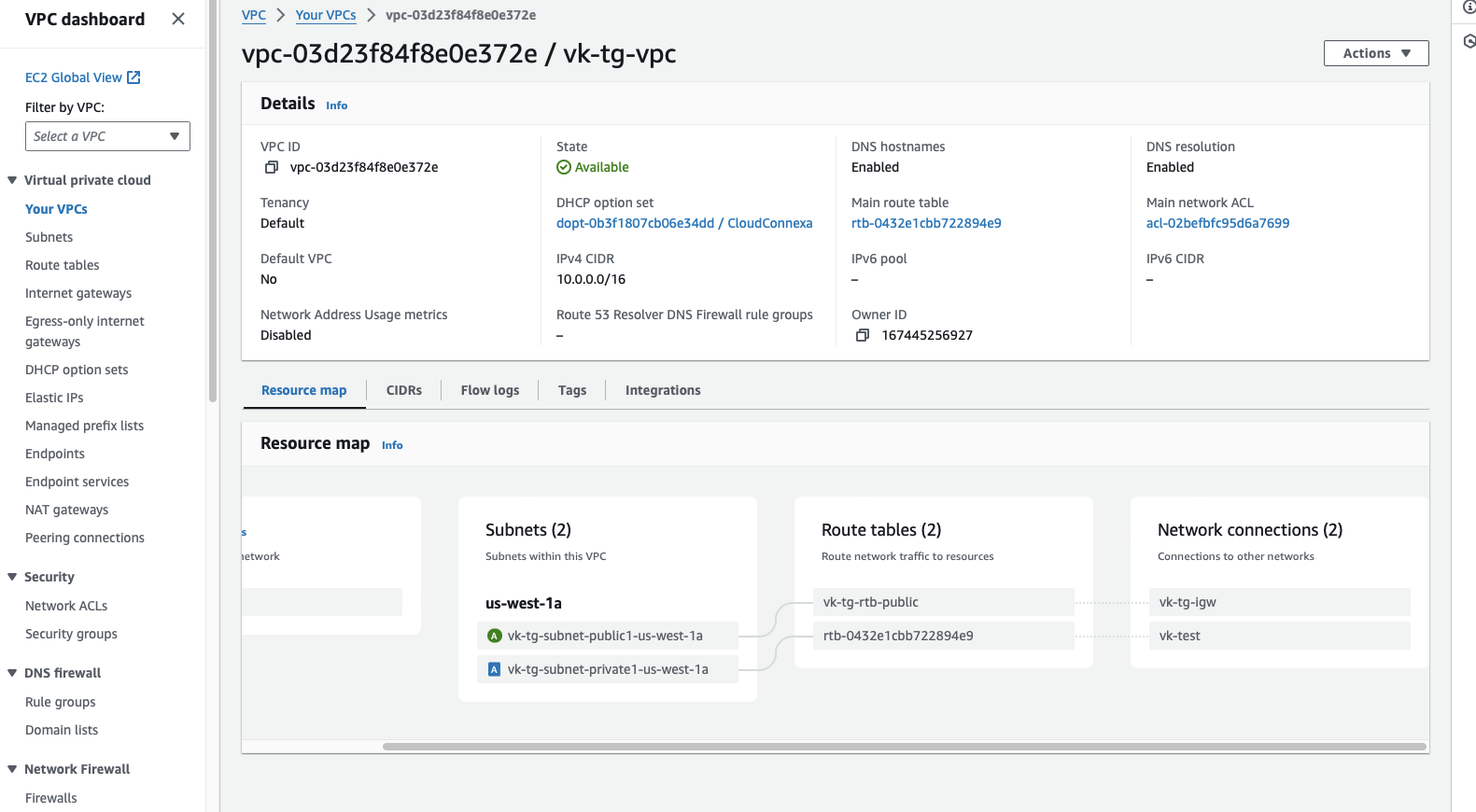
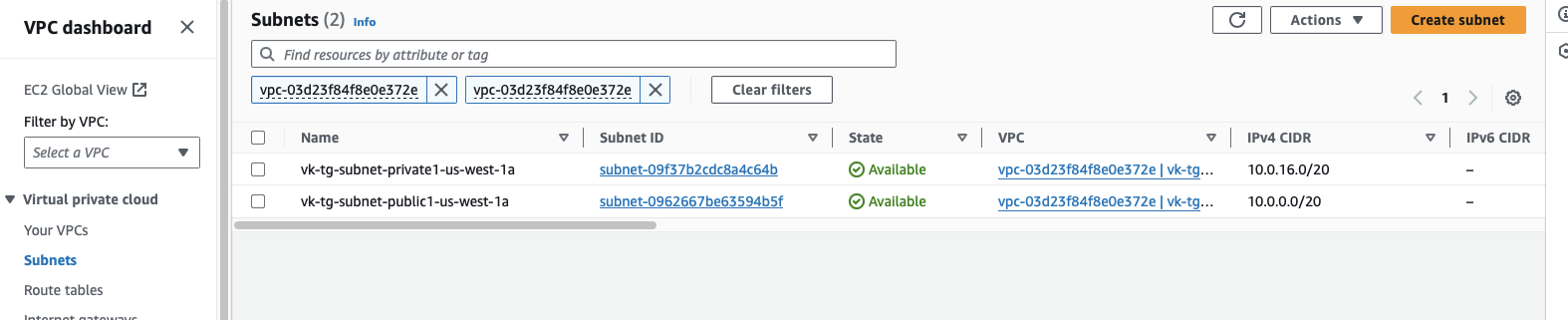
For this configuration, the steps are explained using an example VPC (10.0.0.0/16) with two subnets: a public subnet (10.0.0.0/20) and a private subnet (10.0.16.0/20).
Create a Transit Gateway.
Create a Site-to-Site VPN using the transit gateway. Use Tutorial: Connect AWS to CloudConnexa with IPsec using VPG as appropriate.
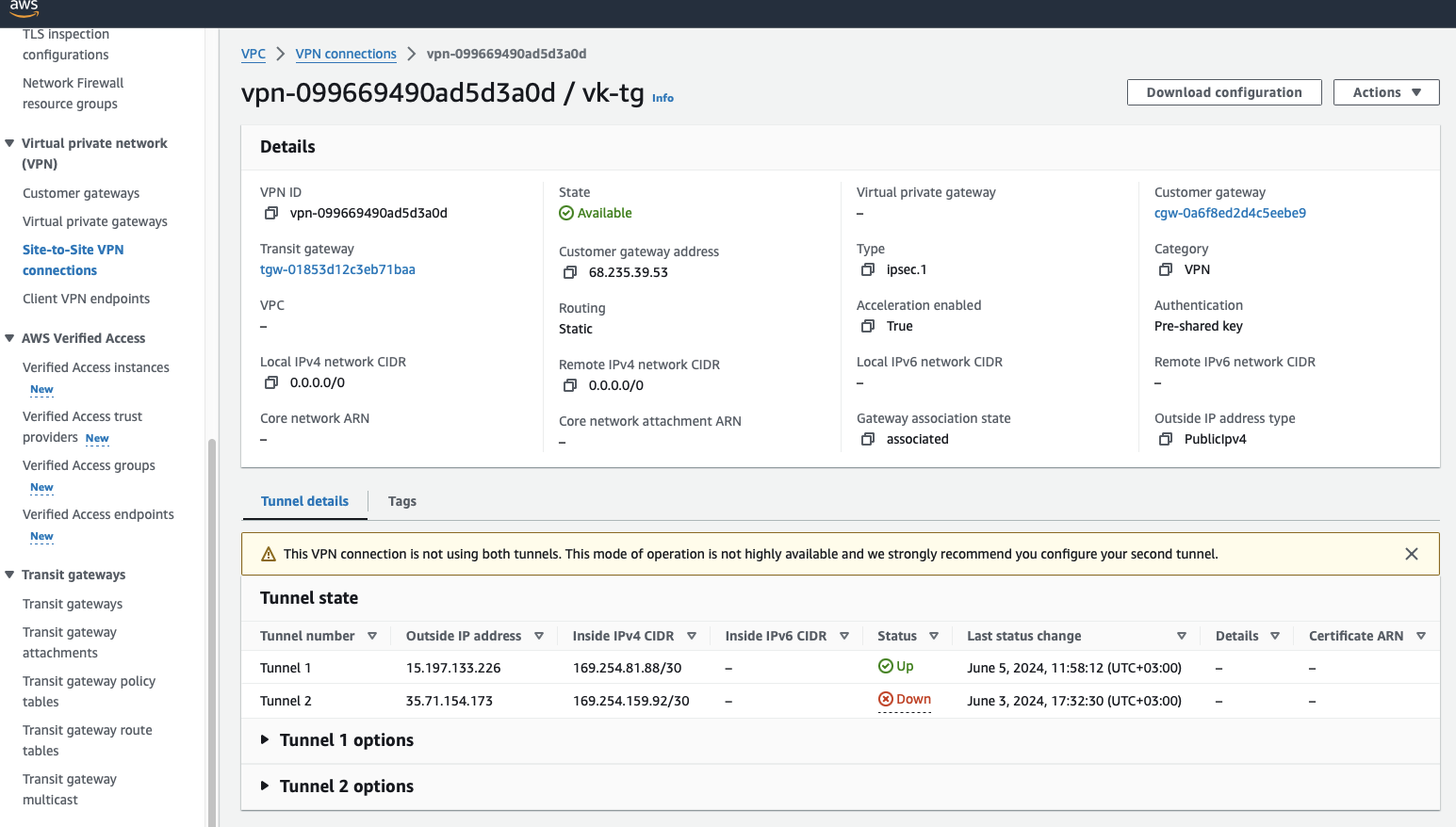
Attach VPC to transit gateway.
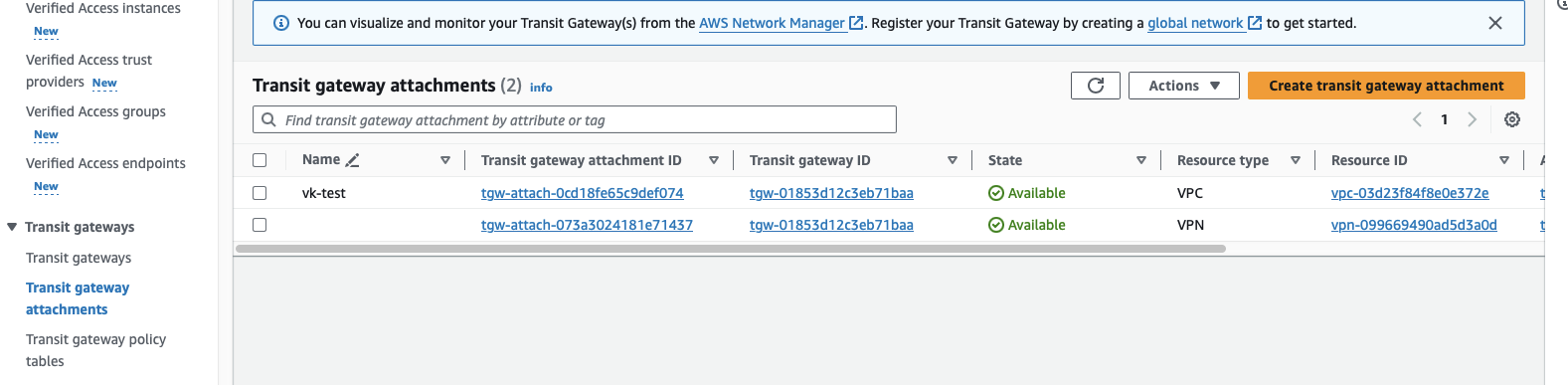
Create a NAT Gateway in the VPC's public subnet (
10.0.0.0/20).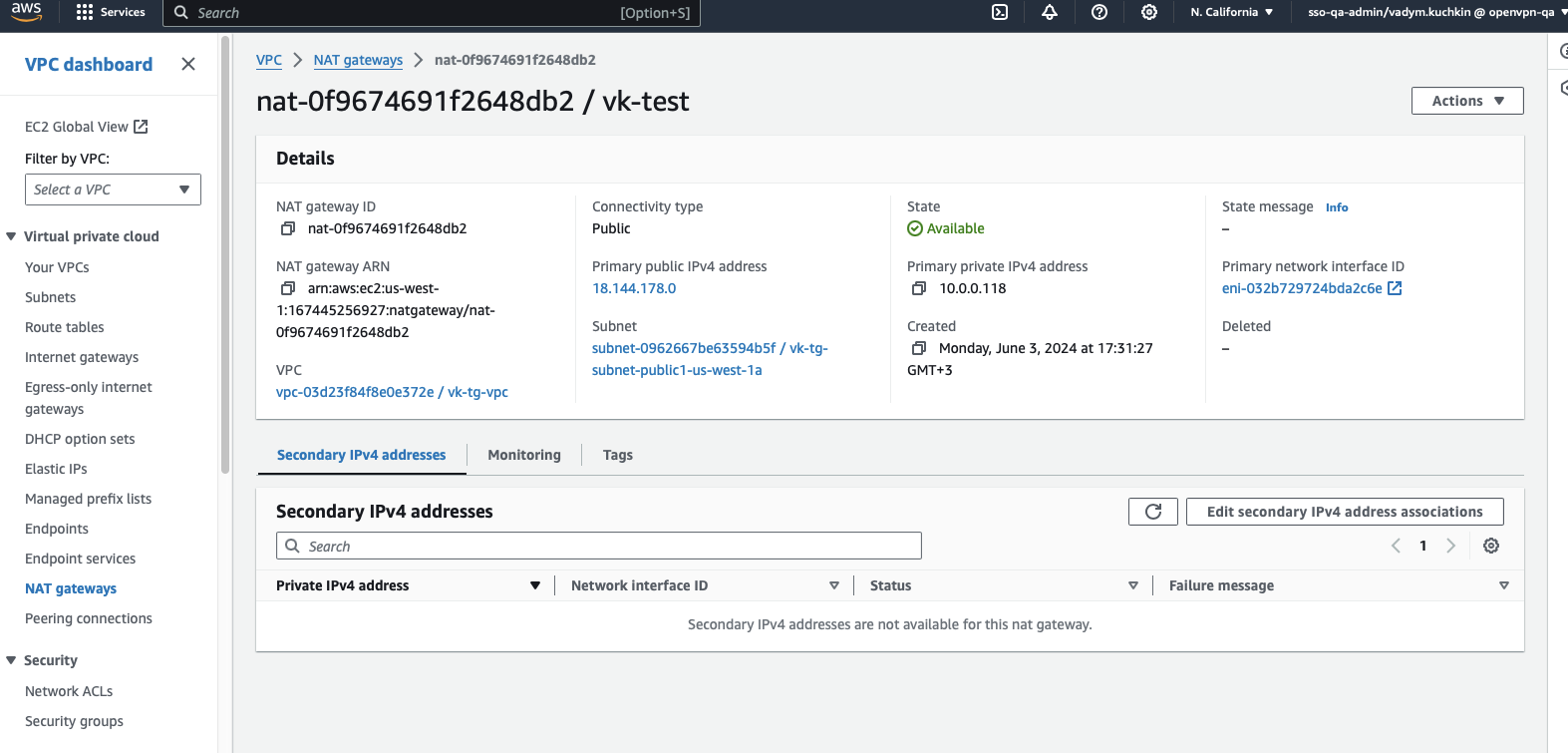
Add the below routes to the VPC's private subnet's route table:
0.0.0.0/0(default route, points to the NAT gateway)100.96.0.0/11(WPC subnet, points to the transit gateway)100.80.0.0/12(Domain routing subnet, points to the transit gateway)
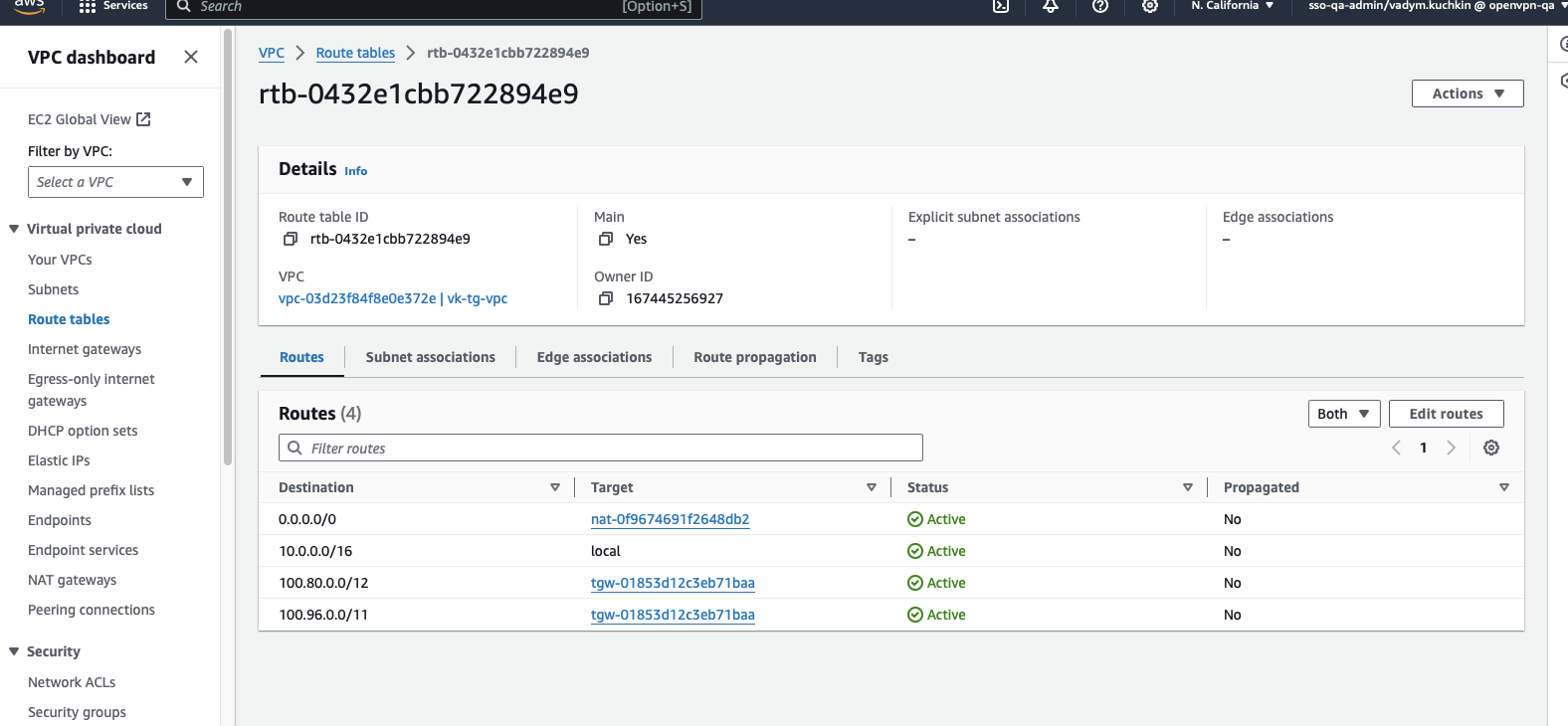
Add the below routes to the VPC's public subnet's route table:
100.96.0.0/11(WPC subnet, points to the transit gateway)100.80.0.0/12(Domain routing subnet, points to the transit gateway)
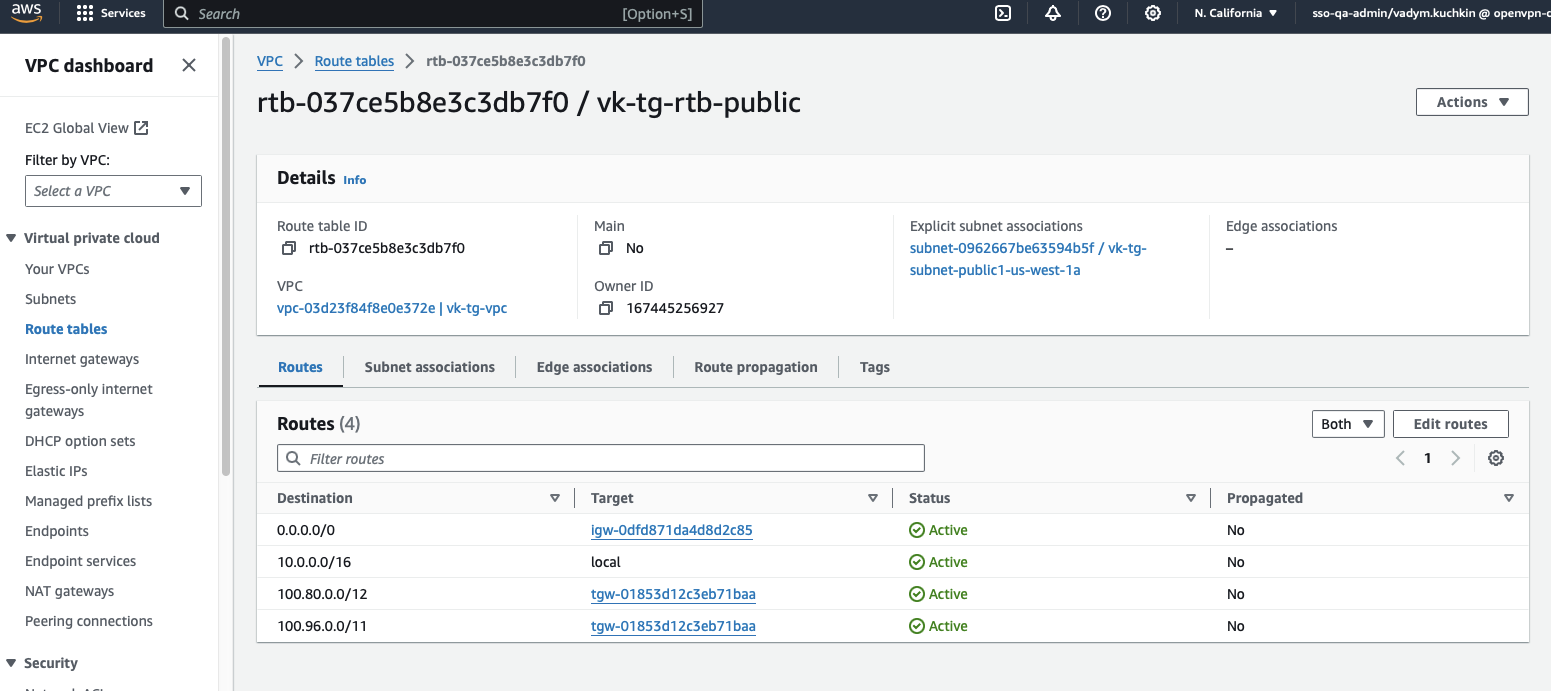
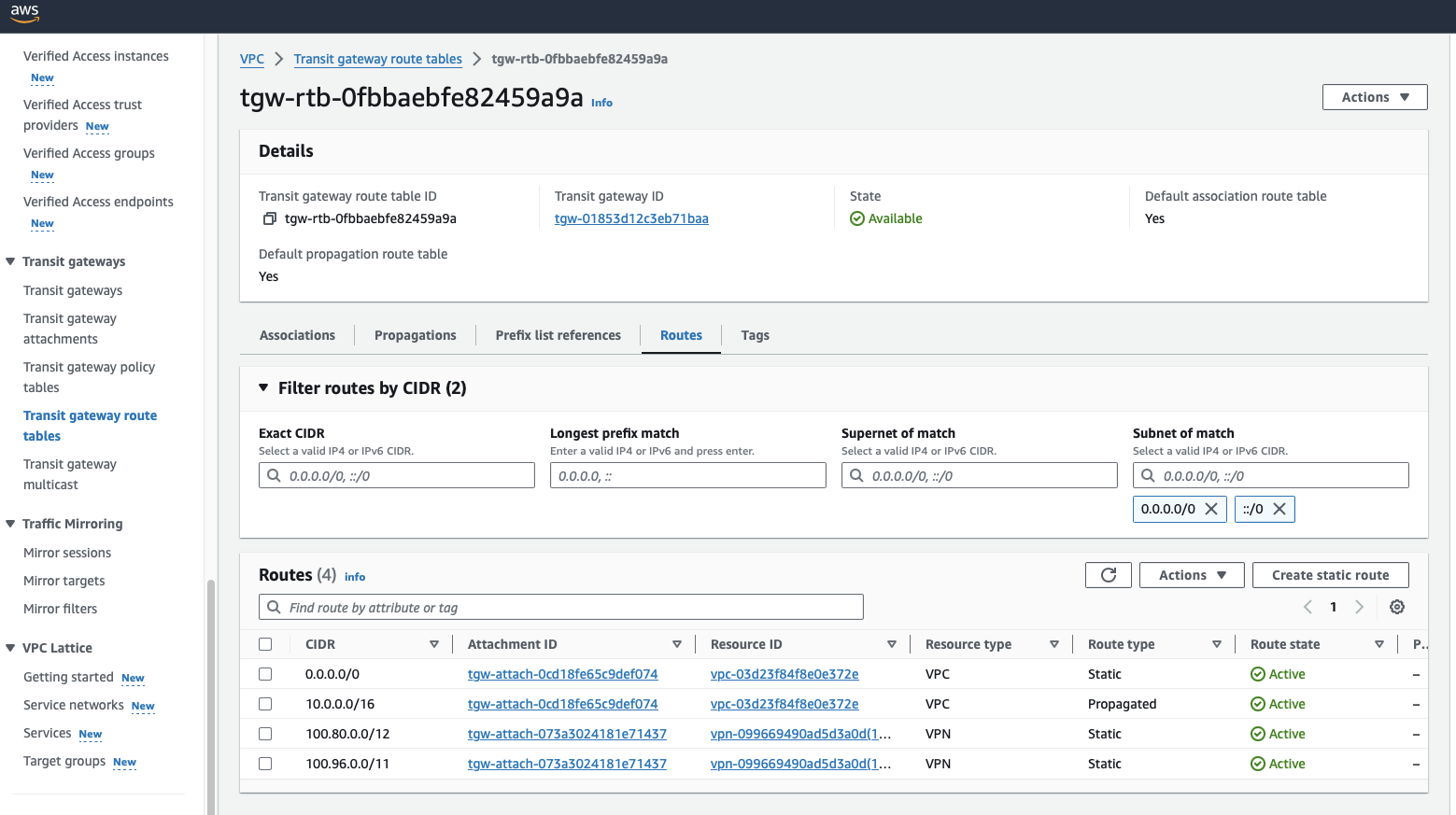
Add the below routes to the transit gateway's route table:
0.0.0.0/0(default route, points to the VPC resource)100.96.0.0/11(WPC subnet, points to the VPN resource)100.80.0.0/12(Domain routing subnet, points to the VPN resource)