Tutorial: Configure Splunk for CloudConnexa Log Streaming
Abstract
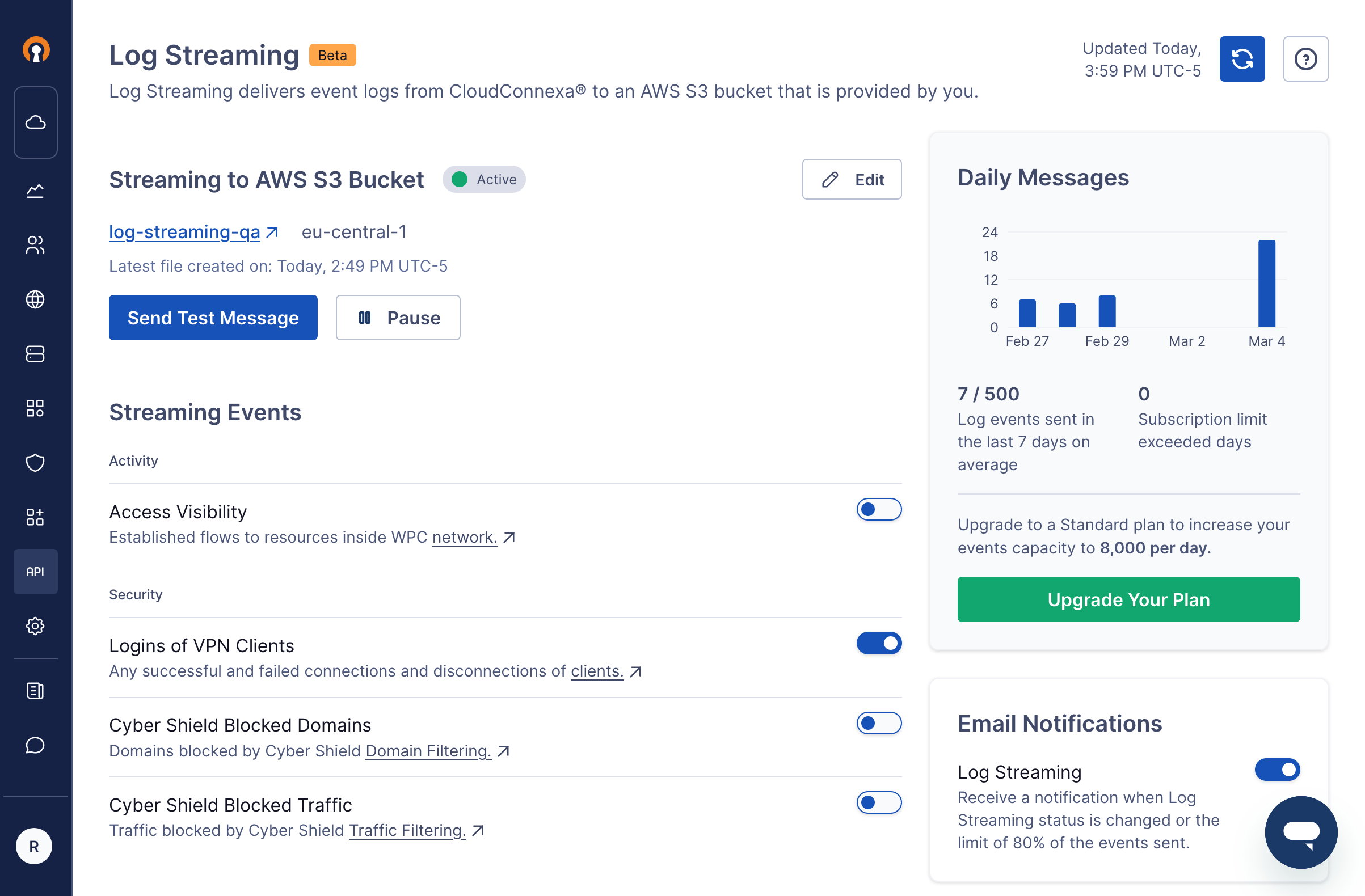
Configure Splunk to ingest logs from CloudConnexa.
Use the Splunk AWS add-on to ingest the log files present in your AWS S3 bucket.
Prerequisites
Configure
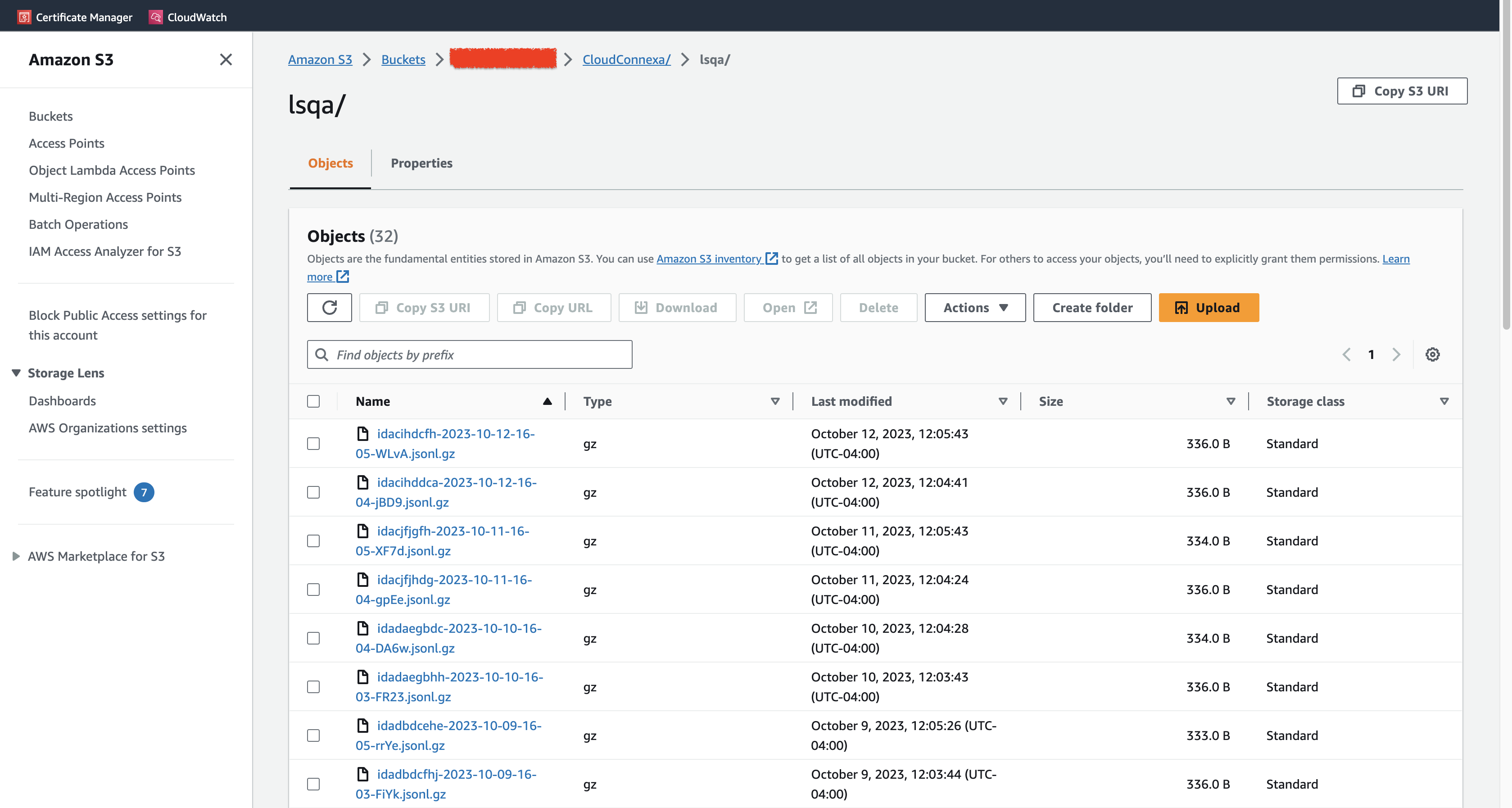
Download and install the AWS add-on for Splunk from Splunkbase. You can find the add-on here.
Configure the add-on to use generic S3 input. Refer to Splunk documentation.
After configuring S3 generic input, Splunk will scan the bucket periodically, parse files, and save them in the configured index.
Test
Log events from the file are parsed and should be visible in Splunk.