Tutorial: Learn About the Levels of Security Afforded by the Use of Various Internet Access Options
This tutorial shows you how you can achieve various levels of security by combining the internet access options with the use of cyber shield features.
Traffic to private resources on your connected Networks always traverses the tunnel to CloudConnexa but there are different ways that you can control the traffic destined to the internet.
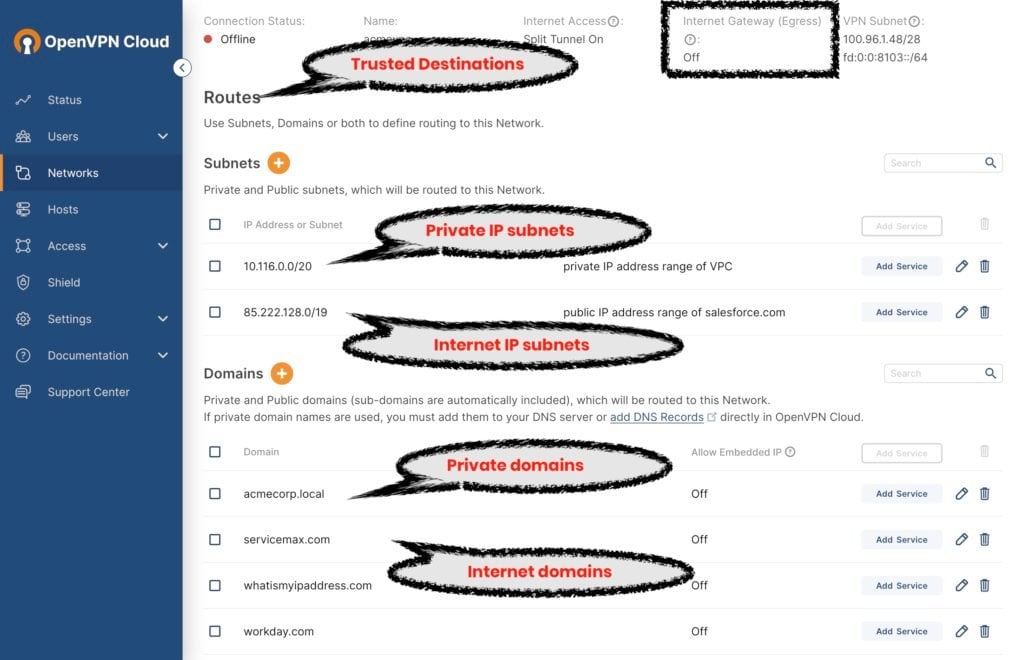
Split-Tunnel ON: If you want to steer traffic to certain internet destinations within the tunnel for additional protection and to use login restriction policies for SaaS (for example, Restrict Marketo Logins), you can add the IP address ranges or domain names of these internet destinations as Routes for the connected Networks. CloudConnexa will treat these internet destinations similar to private traffic and route them within the tunnel and make them exit from the Network those routes are defined against. The configured routes to private and internet destinations are referred to as trusted destinations and traffic to them is called trusted traffic (see the section below, Trusted Traffic or Trusted Destinations)
Traffic to internet destinations outside those configured as trusted destinations is not tunneled to CloudConnexa and gets direct access to the internet
Split-Tunnel OFF: CloudConnexa can tunnel all the internet traffic originating from a Network, Host, or User and route it to one or more of your connected private Networks that act as Internet Gateways to CloudConnexa (see, to set a Network as internet gateway). This provides you the ability to inspect all internet traffic for threats and apply your corporate policies with 3rd party security solutions that you have deployed on your Network.
Restricted Internet: You can also block access to the internet as a whole and only allow access to the private and internet trusted destinations. This option enforces the strictest control and has the following advantages:
Cyber Safety - Eliminates download of malware, phishing, and other cyber threats because the only resources that can be visited are trusted
Content Restriction - enforces strict web browsing for a particular group of target Users such as students or trades working with specialized internet Devices like iPads for order taking
Traffic to trusted internet destinations is always encrypted and tunneled - for an additional layer of security the traffic to the internet transits CloudConnexa
Reduces the need for additional security Devices - As the only communication allowed is with trusted public destinations the need for additional security Devices like UTM is minimized
Trusted Source Network - The public IP address range of the connected private Network can be used as a trusted source Network in SaaS applications
Potential use cases:
Corporate Device safety - Ensure cyber safety of company-owned Devices used by your specialized workforce by restricting internet access to only those destinations needed for them to get their work done
Host Safety - lockdown and harden application servers by restricting them to only the allowed internet destinations for API interaction and software updates
Network Safety - lockdown entire Networks such as your private Network for IoT Devices to only communicate with the internet destinations that are needed for the IoT service
Educational Content Restriction - lockdown student Devices to just the web apps and websites needed for learning
One of these above internet access options can be set up per User Group, Network, or Host
Built-in security solutions and interaction with Internet Access settings
CloudConnexa has built-in content filtering (see the section below, Shield Domain Filtering) and IDS/IPS (see the section below, Shield Traffic filtering). In this section, we will see how those features add value based on the Internet Access setting options.
Split-Tunnel On:
DNS-based content filtering (Cyber Shield Domain Filtering) is effective with this setting choice because it is DNS-based and will be able to block access to domains even if the traffic has direct access to the internet
IDS/IPS (Cyber Shield Traffic filtering) is not as effective because the traffic transiting CloudConnexa is only trusted traffic other internet traffic uses the local internet connection
Split-Tunnel OFF:
DNS-based content filtering (Cyber Shield Domain Filtering) is effective with this setting choice because it is DNS-based and will be able to block access to domains regardless of how the traffic is routed
IDS/IPS (Cyber Shield Traffic filtering) is effective because all the internet traffic is transiting CloudConnexa
Restricted Internet:
DNS-based content filtering (Cyber Shield Domain Filtering) is not effective because the destination domain names are already trusted
IDS/IPS (Cyber Shield Traffic filtering) while not being used at full potential because all the monitored traffic is trusted can still be effective because it can detect and block malicious traffic from a compromised endpoint.
Security levels for internet routing
Given the above, we can assign a security level to internet access settings based on how well access to the internet is secured:
Split-Tunnel ON (Security Level 1):
Only traffic to trusted internet destinations is secured by tunneling through CloudConnexa other internet traffic exits directly using local internet
Cyber Shield Domain filtering is effective
Cyber Shield Traffic filtering while not being used at full potential because all the monitored traffic is trusted can still be effective because it can detect and block malicious traffic from a compromised endpoint.
Split-Tunnel OFF (Security Level 2):
All traffic is tunneled and can be examined by 3rd party security solutions stack (for example, UTM, Secure Web Gateway, etc.) deployed in any of your private Networks acting as an internet gateway to CloudConnexa
Cyber Shield Domain filtering is effective
Cyber Shield Traffic filtering is effective
Restricted Internet (Security Level 3)
All traffic to the internet is blocked except to trusted internet destinations which are tunneled to CloudConnexa
Cyber Shield Traffic filtering while not being used at full potential because all the monitored traffic is trusted can still be effective because it can detect and block malicious traffic from a compromised endpoint.
Trusted Traffic or Trusted Destinations
The routes that are configured for the Networks connected to CloudConnexa are considered to be trusted because they have been specifically configured to provide access. Therefore, the traffic to these destinations is called trusted traffic, and these destinations are called trusted destinations. Both private and Internet destinations can be configured as routes using IP addresses or domain names.
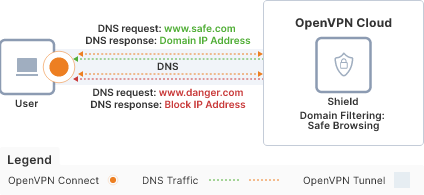
Content filtering ( Cyber Shield Domain Filtering)
Cyber Shield provides Domain Name System (DNS) content filtering to protect Users from malicious and suspicious websites, even when internet traffic isn’t transported through the tunnel. You can choose to simply monitor the number of domain name resolutions that fall into these content categories, or you can take security a step further and enable blocking. DNS-based filtering lets you block domain name resolutions for those websites that fall into undesirable or unsafe categories. Specific domain names can be added to allow and block lists. Cyber Shield provides data reporting on the number of observed and blocked domain name queries originating from your Users. You can drill down and investigate exactly which User Devices generated the DNS requests that were flagged with a particular content category. CSV report with the details of the observed/blocked domain names can be received via email.
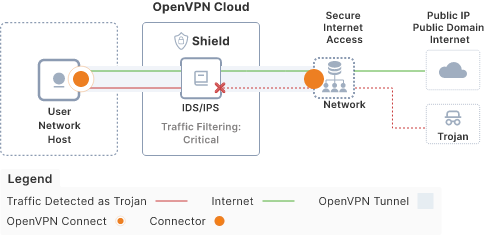
IDS/IPS (Cyber Shield Traffic Filtering)
Cyber Shield provides you with a built-in Intrusion Detection System (IDS) as well as an Intrusion Protection System (IPS). When traffic filtering monitoring is turned ON, Shield will act as an IDS and will monitor the traffic flowing through CloudConnexa in order to provide you with detailed statistics on traffic it has identified as malware, intrusion activity, denial of service, and other types of threats. Once presented with statistics on the type of traffic detected and the number of times that type of traffic was detected, you can drill down and investigate exactly which User’s Device generated that traffic. To nip threats in the bud, you can use Shield to protect your Network by blocking certain types of traffic. When you configure specific threat categories or threat priorities of traffic types to block, Shield will drop the packets of traffic matching those of the blocked categories/priorities and provide statistics on those blocked events. We recommend blocking Priority Critical (Level 1) traffic which identifies traffic generated due to malware, trojans, worms, and certain intrusion activity. IDS/IPS capability is especially useful when CloudConnexa provides an egress route for all internet traffic.
Tutorial: Block All Internet Traffic Except To Trusted Internet Destinations
Tutorial: Learn About the Levels of Security Afforded by the Use of Various Internet Access Options
Tutorial: Protect Your Users From Malware and Other Cyber Threats
Tutorial: Secure All Internet Traffic by Configuring a Private Network as an Internet Gateway
Tutorial: Use Multiple Geographically Distributed Internet Gateways to Improve Internet Performance
Tutorial: Steer Traffic To Specific Internet Destinations Through CloudConnexa