Tutorial: Authenticate Using SAML with G Suite
This tutorial shows the steps to authenticate your Users using SAML. You can configure CloudConexa SAML authentication to use G Suite as the Identity Provider.
Configuring CloudConnexa User authentication to use SAML
The Administrator can configure CloudConnexa to authenticate access to the User Portal, download of a .ovpn Profile, and WPC connections using a SAML 2.0 compliant Identity Provider.
The Administrator needs to follow the steps below. The steps below use G Suite as the Identity Provider. Basic configuration guides for some of the other popular Identity as a Service (IDaaS) providers are provided separately.
Sign in to the CloudConnexa Administration portal at
https://cloud.openvpn.com/.Navigate to Settings section and click on the User Authentication tab.
Click on the Edit button positioned on the top right.
Click on the Configure button under the SAML option.
The SAML web page opens and shows the information needed to configure CloudConnexa as a Service Provider in your Identity Provider.
Log in to the Google administration console to configure CloudConnexa as a SAML Service Provider, and follow steps below:
Click on the menu and navigate to Apps > Web and mobile apps, then Add App "Add custom SAML app".
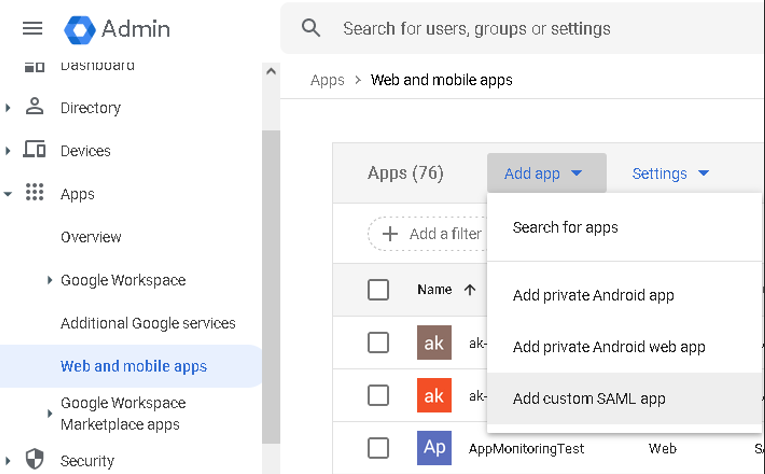
Then, follow this 4 step procedure:
Step 1. Enter an App name with a description, and click Continue.
Step 2. Here, you'll find the Identity Provider (IdP) information needed later to configure CloudConnexa. Download the IdP Metadata file. Click Continue.
Step 3. Provide the Service Provider Details:
Enter the Issuer Name displayed in the SAML Configuration web page of CloudConnexa into the Entity ID input field.
Enter the Configuration SSO URL displayed in the SAML Configuration web page of CloudConnexa into the ACS URL input field.
Click Continue.
Step 4. Attribute Mapping. Google IdP will only provide the NameID attribute to the Service Provider by default, which CloudConnexa will map to the username of the User. If you do not want CloudConnexa to have more information about the User and to use the value of a specific User attribute configuration, you can skip this step. Click the Finish button.
Now that CloudConnexa has been set up as an application, you can assign it to all Users. Access the created SAML App (Apps > Web and mobile apps. Select the created App), Under "User Access" select "ON for everyone", then click Save.
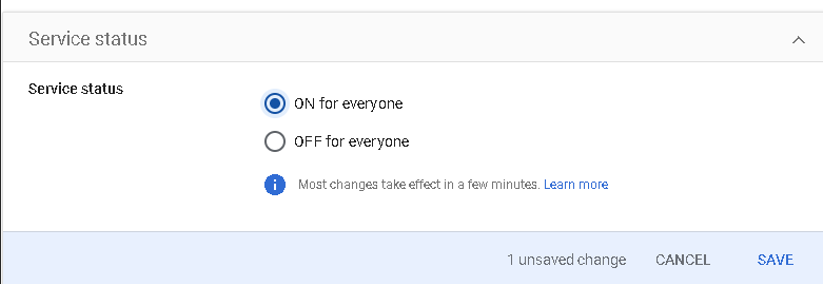
Go back to the browser tab/window displaying the CloudConnexa and take the following actions:
Click on the Next button.
Provide an IdP Name. Select IdP Metadata XML, and do the following:
Open the IdP metadata file that you downloaded in step ‘2.b of Step 2’ and copy the XML text shown.
Paste the text into the IdP Metadata XML text field.
If earlier in step ‘2.b of Step 4′ you set up additional parameters to map to the CloudConnexa User information, do the following or else click on the Next button:
Expand the Advanced settings section.
In the Attributes Mapping section, provide the Identity Provider parameter names corresponding to the CloudConnexa User information fields that you want to be populated with information from the Identity Provider’s parameters (SAML attributes) and click on the Next button when done.
Click on the Complete button after reviewing the SAML configuration.
Now that the SAML configuration is done, we need to enable SAML as the User authentication method by clicking on the Edit button in the User Authentication tab.
Select the SAML option.
If earlier in step ‘2.b of Step 4’ you set up an additional parameter with the intention to map the value of that parameter to the CloudConnexa User Group, do the following or else click on the Update Settings button:
Under SAML, click the View Group Mapping button.
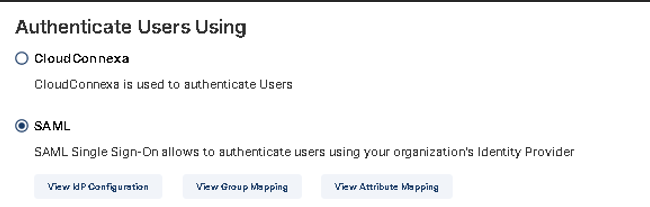
Click the "+" button to add Rule.
Enter into the SAML IdP User Group(s) field one or more of the values that will be present in the IdP provided parameter that you mapped to the Group attribute in step "3.c.ii", and select the corresponding parameters you want those values to map into. For example, the IdP User's department value of 'DEV' could map to CloudConnexa User Group 'Dev' which has been configured to provide access to resources for developers. Repeat the step to add more rules as desired and click on the Update Settings button when done.
Click the Confirm button on the confirmation dialog.
SAML is now enabled.
Now that SAML is enabled for the WPC, when a User wants to sign in to the CloudConnexa Administration portal to download the Connect Client or manage Devices etc., the User will sign in using SSO credentials. When the User visits the User Portal (for example, at https://test8.openvpn.com), the User will see the Identity Provider's login screen.
Log in to CloudConnexa Portal
Now that SAML is enabled for the WPC when a User wants to sign in to the User Portal to download the Connect Client or manage Devices etc., the User will sign in using SSO credentials. When the User visits the User Portal (for example, at https://test8.openvpn.com ), the User will see the Identity Provider’s login screen
On successful first authentication, the Administrator will see the User details show up in the Administration portal.
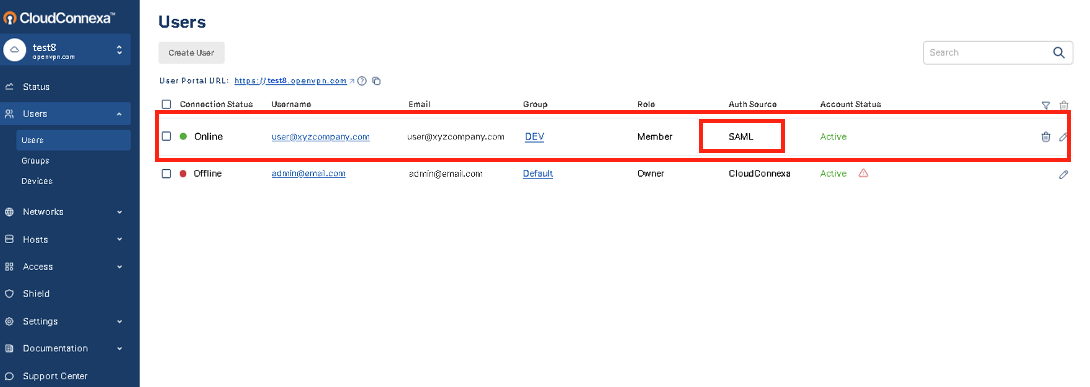
In the screenshot above, you can see that the user1 has been added after SAML authentication because the Auth Source is shown as SAML.