SAML
Tutorial: Authenticate Using SAML with Azure Active Directory (a.k.a. Microsoft Entra ID)
This tutorial shows the steps to authenticate your Users using SAML. You can configure CloudConexa SAML authentication to use Azure Active Directory as the Identity Provider.
Configuring CloudConnexa User authentication to use SAML
The Administrator can configure CloudConnexa to authenticate access to User Portal, download of WPC Profile, and WPC connections using a SAML 2.0 compliant Identity Provider.
The Administrator needs to follow the steps below. The steps below use Azure Active Directory as the Identity Provider. Basic configuration guides for some of the other popular Identity as a Service (IDaaS) providers are provided separately.
Login to CloudConnexa Administration portal at https://cloud.openvpn.com and do the following:
Navigate to Settings section and click on the User Authentication tab
Click on the Edit button positioned on the top right
Click on the Configure button under the SAML option
The SAML Configuration web page opens in a new browser window/tab and show the information needed to configure CloudConnexa as a Service Provider in your Identity Provider
Login to the administration console of the Identity Provider to configure CloudConnexa as a SAML Provider. The steps for Azure Active Directory are below:
On the Active Directory main page click on Enterprise application option.
Click on the New application button
Select the non-gallery application option in the Add your own app section
Provide name for your app and click Add. On the home page of your app, select the Set up single sign on option.
Then choose SAML option. On the Set up Single Sign-On with SAML page click on the Edit icon and:
Enter the Issue Name displayed in the SAML Configuration web page of CloudConnexa into Identifier (Entity ID) input field of Azure Active Directory
Enter the SSO URL displayed in the SAML Configuration web page of CloudConnexa into the Reply URL (Assertion Consumer Service URL) input field of Azure Active Directory
Scroll down the page to SAML Signing Certificate section. In this section you can copy the link shown in the App Federation Metadata URL field this will be needed later
Azure Active Directory will only provide the NameID value to the Service Provider by default which CloudConnexa will map to the username of the User. If you want CloudConnexa to have more information about the User and to use the value of a specific User attribute to map the User into a CloudConnexa User Group, you need to configure parameters to be sent from Azure Active Directory to App. You can do that by filling in the User Attributes & Claims section of your App
You can also configure Azure AD to send groups using Active Directory attributes synced from Active Directory instead of Azure AD objectIDs. Only groups synchronized from Active Directory will be included in the claims. For example, you can send the Mail-Enabled Security Groups synchronized from Office 365. See, Microsoft Documentation on how a group claim can return the ‘Security group’ for the ‘Group ID’ Source attribute.
Note
The User Attributes & Claims appear in a shortened format on some configuration web pages. The complete URL form is needed for configuration. Refer to Troubleshooting Azure AD.
Now that CloudConnexa has been set up as an application, you need to provide applicable Users access to CloudConnexa application by doing the following:
Go to the Enterprise application menu, choose your created app and select Assign Users and groups
Click on Add User
Click on Users, then choose the User you want to assign to application and click on the Select button
Then at the bottom of the page you will find active Assign button, click on it. The User should appear among the list of assigned Users
Go back to the browser tab/window displaying the CloudConnexa and take the following actions:
Click on the Next button
Provide an Idp Name, Select IdP Metadata URL, and paste the App Federation Metadata URL value copied earlier in step ‘2.f’ into the IdP Metadata URL text field
If earlier in step ‘2.g’ you had set up additional parameters to map into CloudConnexa User information, do the following or else click on the Next button:
Expand the Advanced settings section
In the Attribute Mapping section provide the Identity Provider parameter names corresponding to the CloudConnexa User information fields that you want to be populated with information from the Identity Provider’s parameters (SAML attributes) and click on the Next button when done
Click on the Finish button after reviewing the SAML configuration
Now that the SAML configuration is done, we need to enable SAML as the User authentication method by clicking on the Edit button in the User Authentication tab
Select the SAML option
If earlier in step 2.g’you had setup an additional parameter with the intention to map the value of that parameter to OpenVPN Cloud User Group, do the following or else click on the Update Settings button:
Click on the Add Rule button
Enter in SAML IdP User Group(s) field one or more of the values that will present in the IDP provided parameter that you had mapped to the Group attribute in step ‘3.c.ii’and select the corresponding you want those values to map into. For example, the IdP User’s department value of ‘DEV’ could map to CloudConnexa User Group ‘Dev’ which has been configured to provide access to resources for developers. Repeat the step to add more rules as desired and click on the Update Settings button when done
If you are passing attributes synced from Active Directory instead of Azure AD objectIDs as mentioned in step 2.g.i, you need to find the value of the EnternalDirectoryObjectID that will be sent accross. For example to find the EnternalDirectoryObjectID for an Office 365 Security Group named ‘Dev’, you would use PowerShell to connect and signin to Exchange Online and run the command below and use the value returned for EnternalDirectoryObjectID to map to CloudConnexa User Group ‘Dev’
Get-DistributionGroup "Dev" | Format-List Name,ExternalDirectoryObjectID
Click the Confirm button on the confirmation dialog
SAML is now enabled
Sign in to the User Portal
Now that SAML is enabled for the WPC when a User wants to sign in to the User Portal to download Connect Client or manage Devices etc., the User will sign in using SSO credentials. When the User visits the User Portal (for example, at https://test8.openvpn.com), the User will see the Identity Provider’s login screen
On successful first authentication, the Administrator will see the User details show up in the Administration portal.
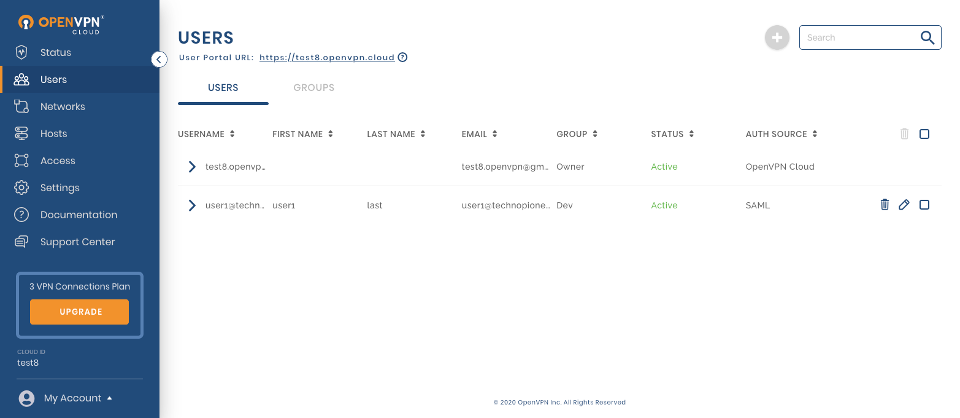
In the screenshot above, you can see that the user1 has been added after SAML authentication because the Auth Source is shown as SAML.
Tutorial: Authenticate Using SAML with G Suite
This tutorial shows the steps to authenticate your Users using SAML. You can configure CloudConexa SAML authentication to use G Suite as the Identity Provider.
Configuring CloudConnexa User authentication to use SAML
The Administrator can configure CloudConnexa to authenticate access to the User Portal, download of a .ovpn Profile, and WPC connections using a SAML 2.0 compliant Identity Provider.
The Administrator needs to follow the steps below. The steps below use G Suite as the Identity Provider. Basic configuration guides for some of the other popular Identity as a Service (IDaaS) providers are provided separately.
Sign in to the CloudConnexa Administration portal at
https://cloud.openvpn.com/.Navigate to Settings section and click on the User Authentication tab.
Click on the Edit button positioned on the top right.
Click on the Configure button under the SAML option.
The SAML web page opens and shows the information needed to configure CloudConnexa as a Service Provider in your Identity Provider.
Log in to the Google administration console to configure CloudConnexa as a SAML Service Provider, and follow steps below:
Click on the menu and navigate to Apps > Web and mobile apps, then Add App "Add custom SAML app".
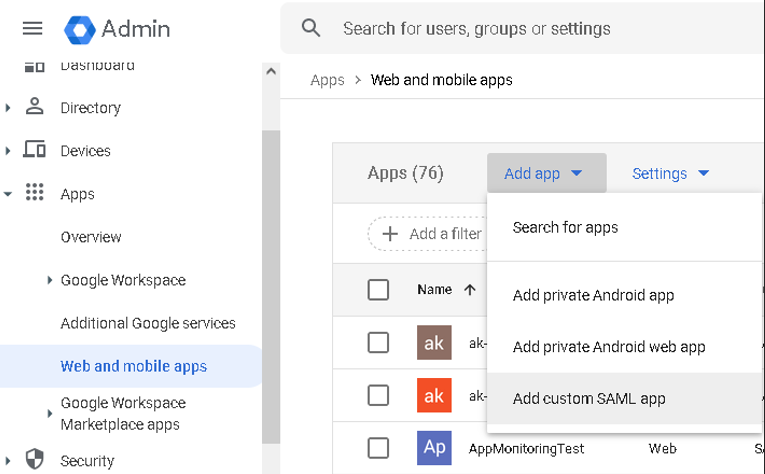
Then, follow this 4 step procedure:
Step 1. Enter an App name with a description, and click Continue.
Step 2. Here, you'll find the Identity Provider (IdP) information needed later to configure CloudConnexa. Download the IdP Metadata file. Click Continue.
Step 3. Provide the Service Provider Details:
Enter the Issuer Name displayed in the SAML Configuration web page of CloudConnexa into the Entity ID input field.
Enter the Configuration SSO URL displayed in the SAML Configuration web page of CloudConnexa into the ACS URL input field.
Click Continue.
Step 4. Attribute Mapping. Google IdP will only provide the NameID attribute to the Service Provider by default, which CloudConnexa will map to the username of the User. If you do not want CloudConnexa to have more information about the User and to use the value of a specific User attribute configuration, you can skip this step. Click the Finish button.
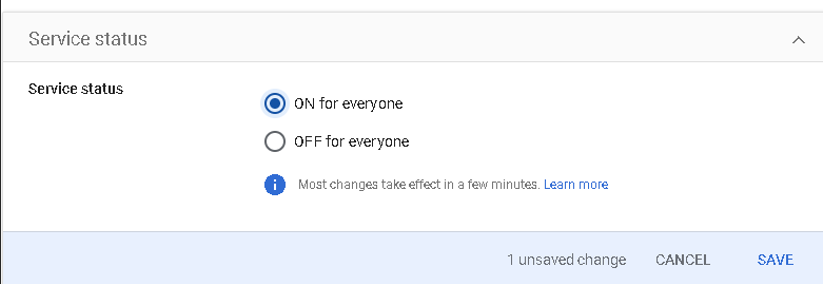
Now that CloudConnexa has been set up as an application, you can assign it to all Users. Access the created SAML App (Apps > Web and mobile apps. Select the created App), Under "User Access" select "ON for everyone", then click Save.
Go back to the browser tab/window displaying the CloudConnexa and take the following actions:
Click on the Next button.
Provide an IdP Name. Select IdP Metadata XML, and do the following:
Open the IdP metadata file that you downloaded in step ‘2.b of Step 2’ and copy the XML text shown.
Paste the text into the IdP Metadata XML text field.
If earlier in step ‘2.b of Step 4′ you set up additional parameters to map to the CloudConnexa User information, do the following or else click on the Next button:
Expand the Advanced settings section.
In the Attributes Mapping section, provide the Identity Provider parameter names corresponding to the CloudConnexa User information fields that you want to be populated with information from the Identity Provider’s parameters (SAML attributes) and click on the Next button when done.
Click on the Complete button after reviewing the SAML configuration.
Now that the SAML configuration is done, we need to enable SAML as the User authentication method by clicking on the Edit button in the User Authentication tab.
Select the SAML option.
If earlier in step ‘2.b of Step 4’ you set up an additional parameter with the intention to map the value of that parameter to the CloudConnexa User Group, do the following or else click on the Update Settings button:
Under SAML, click the View Group Mapping button.
Click the "+" button to add Rule.
Enter into the SAML IdP User Group(s) field one or more of the values that will be present in the IdP provided parameter that you mapped to the Group attribute in step "3.c.ii", and select the corresponding parameters you want those values to map into. For example, the IdP User's department value of 'DEV' could map to CloudConnexa User Group 'Dev' which has been configured to provide access to resources for developers. Repeat the step to add more rules as desired and click on the Update Settings button when done.
Click the Confirm button on the confirmation dialog.
SAML is now enabled.
Now that SAML is enabled for the WPC, when a User wants to sign in to the CloudConnexa Administration portal to download the Connect Client or manage Devices etc., the User will sign in using SSO credentials. When the User visits the User Portal (for example, at https://test8.openvpn.com), the User will see the Identity Provider's login screen.
Log in to CloudConnexa Portal
Now that SAML is enabled for the WPC when a User wants to sign in to the User Portal to download the Connect Client or manage Devices etc., the User will sign in using SSO credentials. When the User visits the User Portal (for example, at https://test8.openvpn.com ), the User will see the Identity Provider’s login screen
On successful first authentication, the Administrator will see the User details show up in the Administration portal.
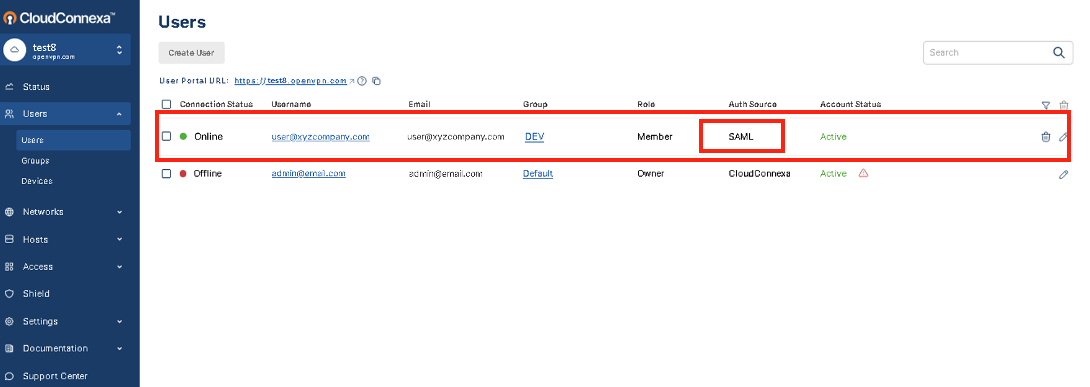
In the screenshot above, you can see that the user1 has been added after SAML authentication because the Auth Source is shown as SAML.
Tutorial: Authenticate Using SAML with Keycloak
This tutorial shows the steps to authenticate your Users using SAML. You can configure CloudConexa SAML authentication to use Keycloak as the Identity Provider.
Steps: Retrieve certificate value and IdP endpoint from Keycloak
Navigate to Keycloak and sign in with your Administrator account.
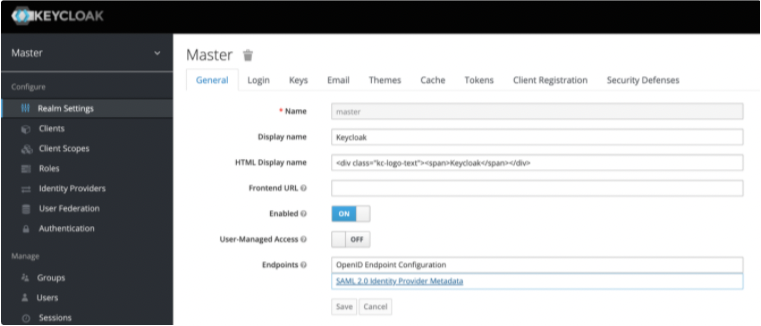
Access Realm Settings > Endpoints and click SAML 2.0 Identity Provider Metadatal.
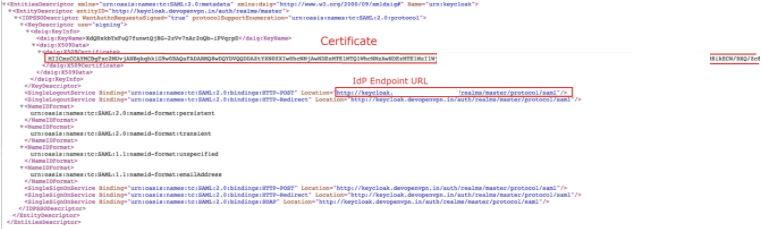
Copy the IdP X.509 Public Certificate and the IdP Authentication Endpoint URL, which are used later in the CloudConnexa set up process.
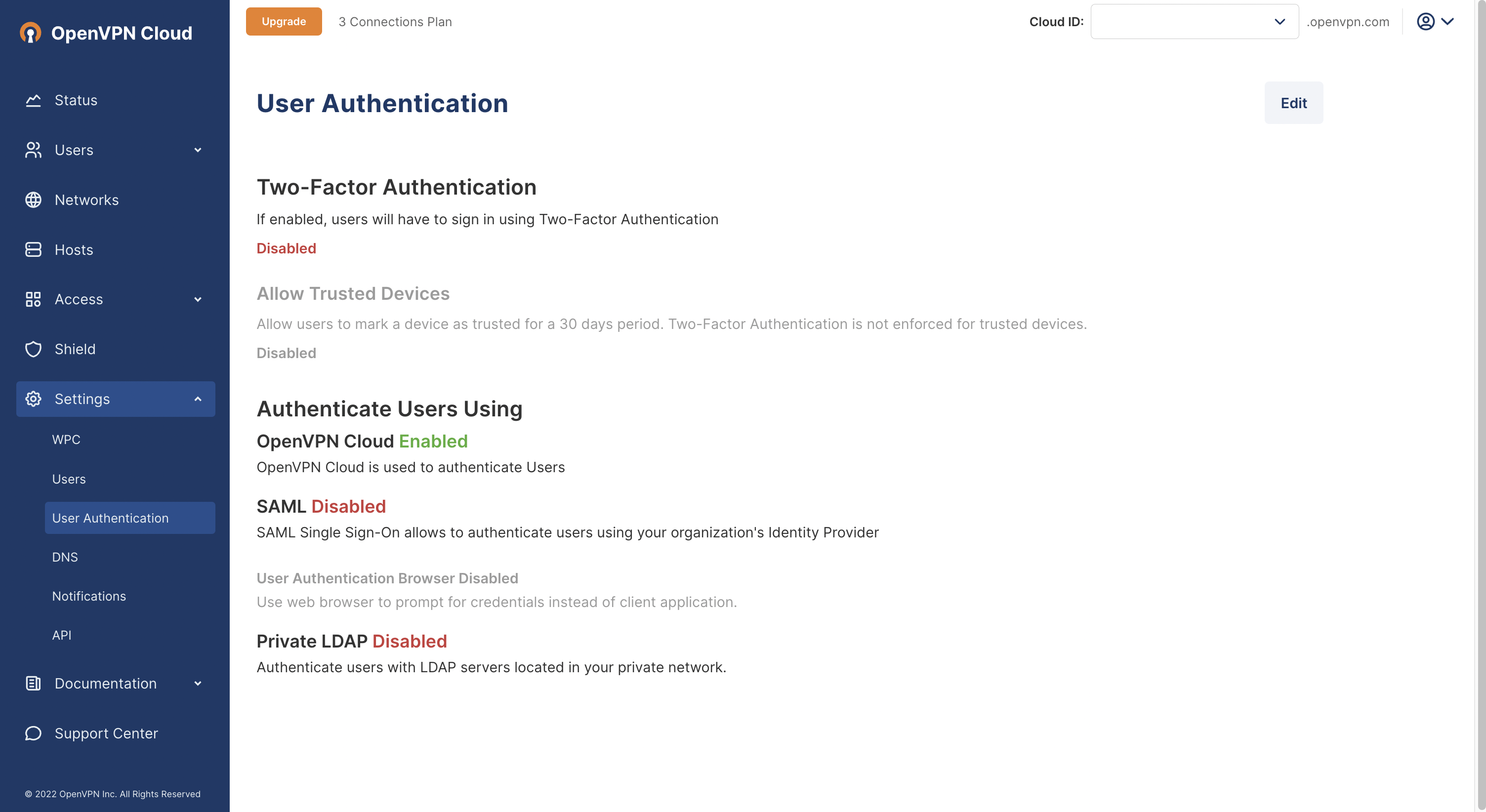
Steps: Configure and enable SAML in CloudConnexa
Sign in to the CloudConnexa
https://cloud.openvpn.com/Access Settings > User Authentication and click Edit.
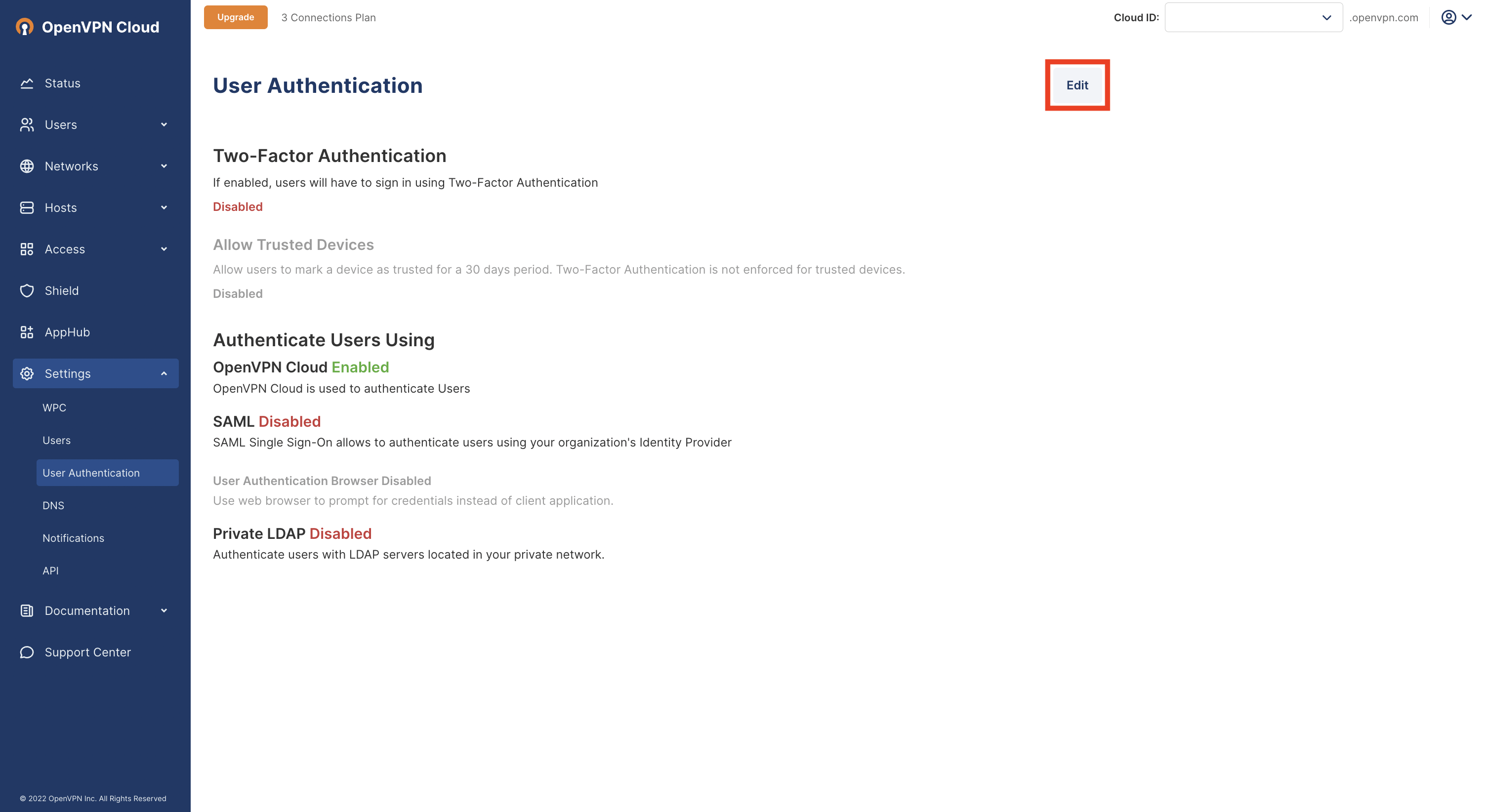
Click on Configure in the Authenticate Users Using > SAML section.
The SAML Configuration window opens. Click Next.
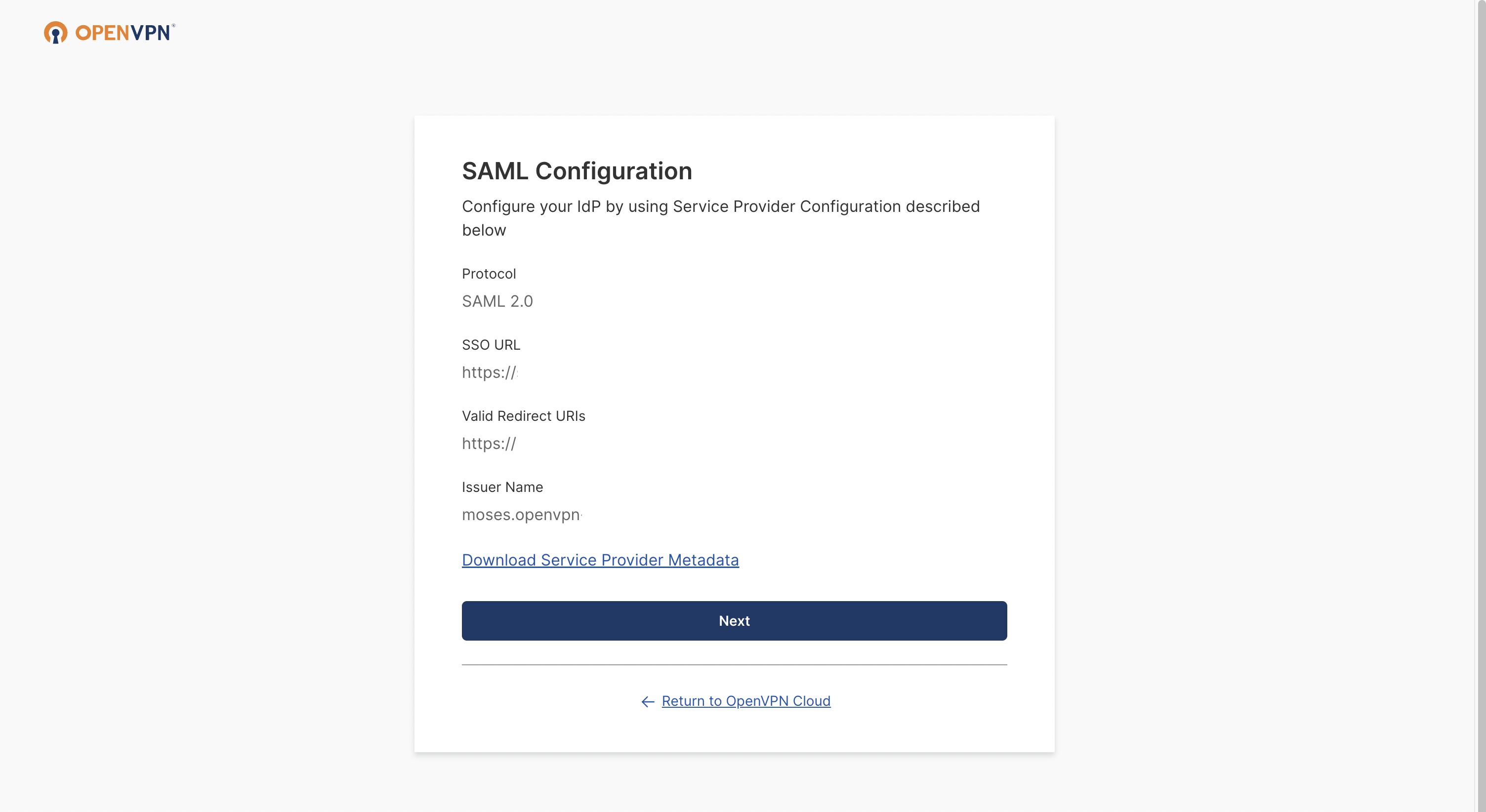
Add your IdP Name (optional), and then select Manual Configuration.
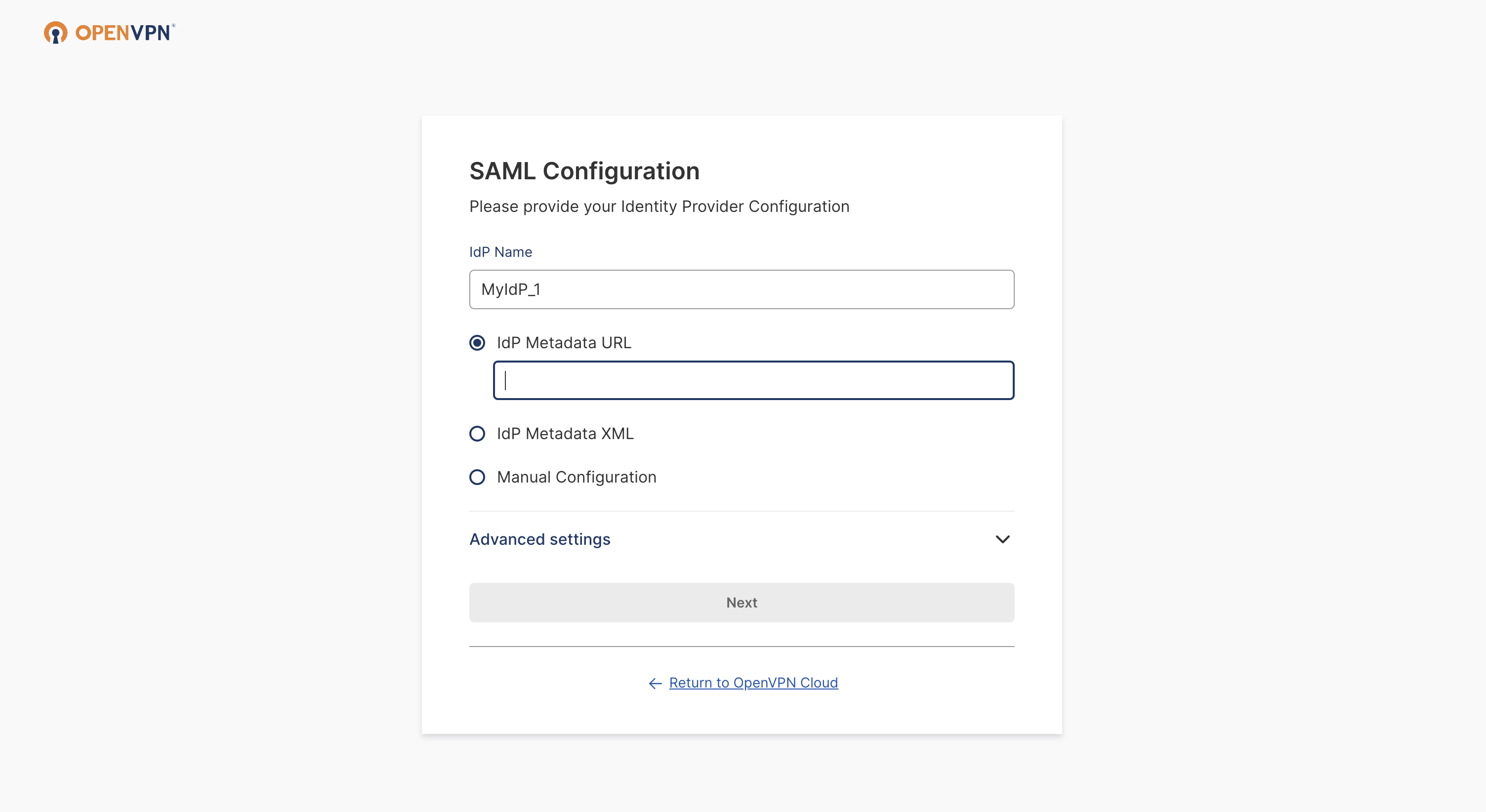
Paste the previously copied IdP Authentication Endpoint URL and the IdP X.509 Public Certificate.
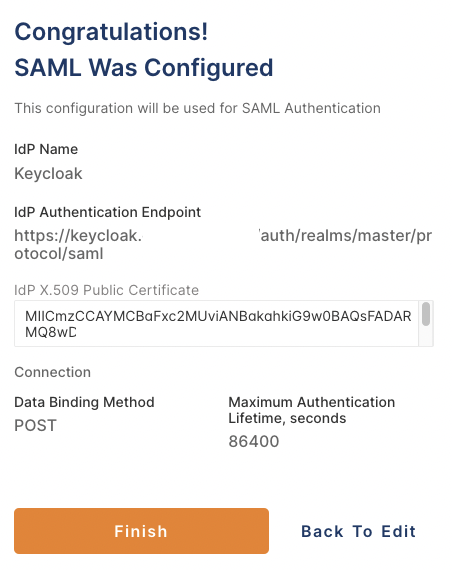
Click Next, review the displayed information, then click Finish.
You now have the option to use SAML to authenticate Users.
Steps: Create a new Keycloak client
Navigate to Keycloak and sign in as an Administrator.
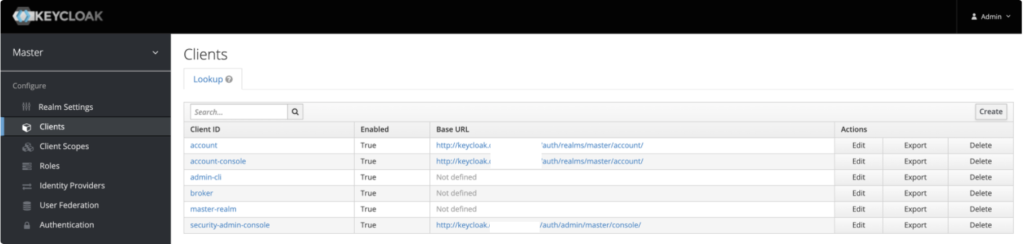
Access Clients and click Create.
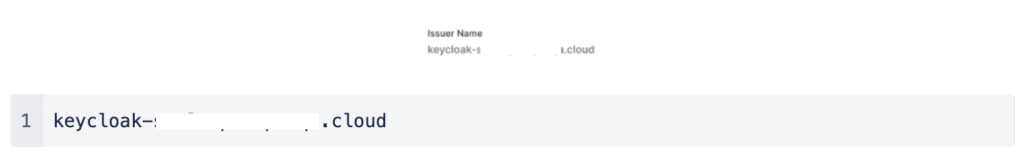
Set the Client ID to be the same as the Issuer Name that was displayed in the SAML configuration on the CloudConnexa portal:
Select SAML as the Client Protocol.
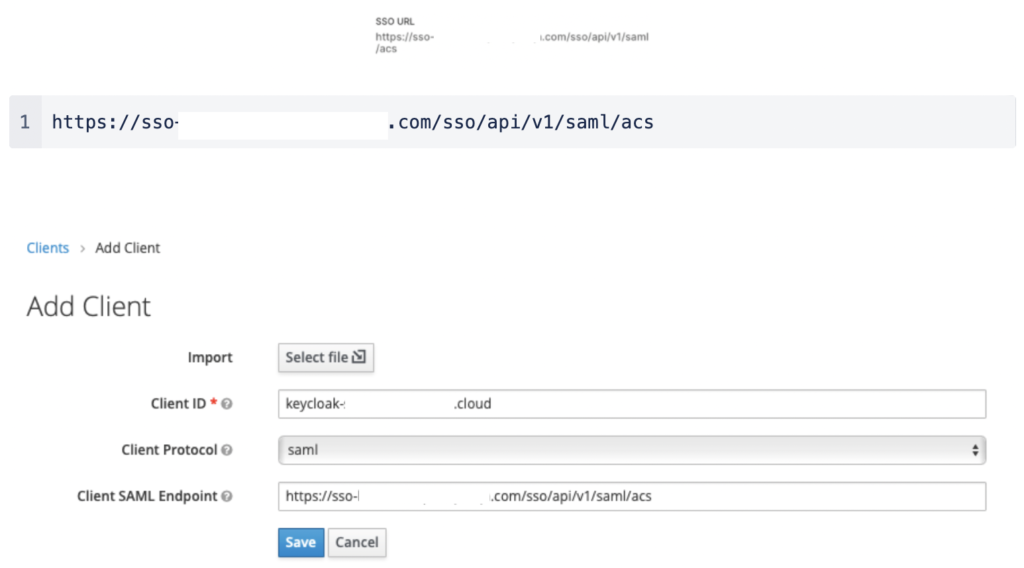
Enter the SSO URL for the Client SAML Endpoint:
Click Save.
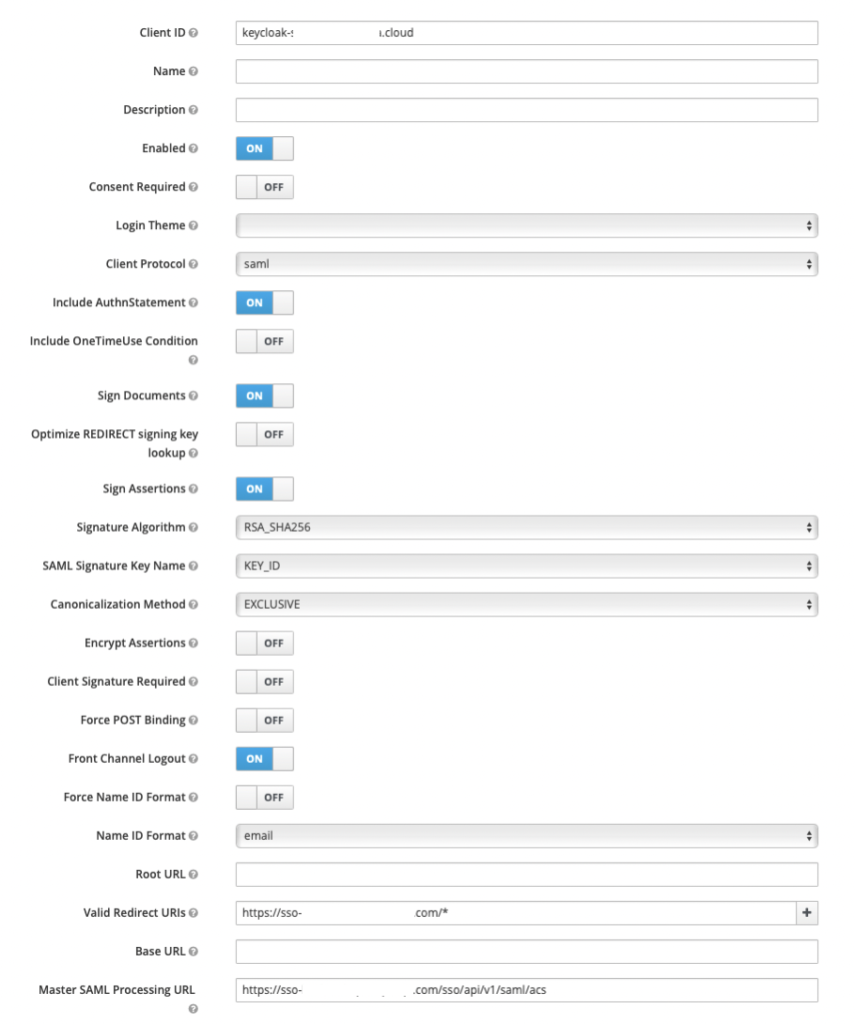
The settings tab displays the default values.
Enable Sign Assertions.
Disable Client Signature Required and Force POST Binding.
Set the Name ID format to email.
Enter this value in Valid Redirect URIs, which allows redirects to the ACS URL:

All other values are left as default.
Steps: Create a Keycloak User account
Navigate to Keycloak, access Users, and click Add User.
Fill out the form with your data.
Note
You can select Email Verified if you use a test email that doesn’t allow verification.
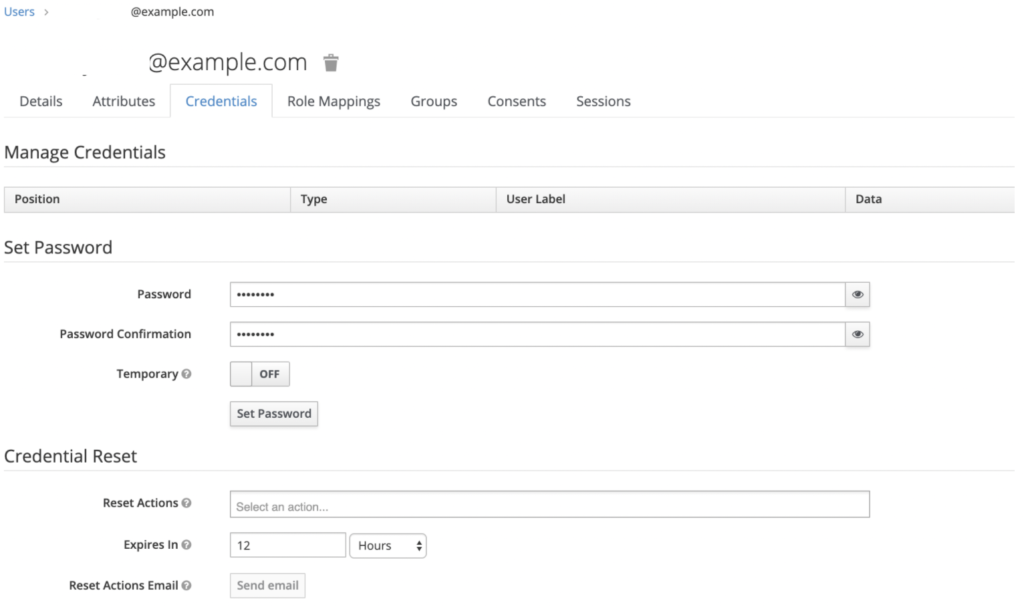
Open the Credentials tab and assign a password for the User account, and click Set Password.
Steps: Configure attributes and group mapping in Keycloak
Navigate to Keycloak, access Clients, and click on your Client ID.
Click on the Mappers tab, which allows you to create SAML attributes.
Note
At the time of publication, CloudConnexa only supports First Name, Last Name, Email, and Groups for mapping attributes.
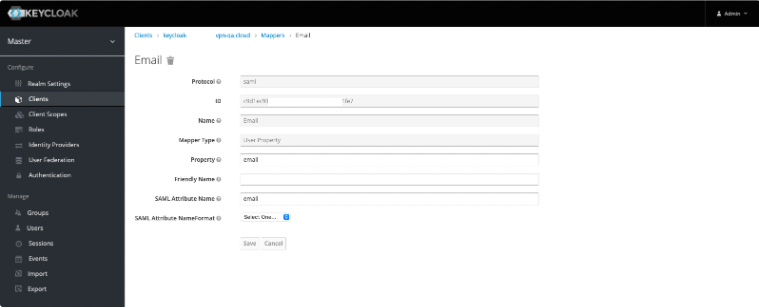
Click Create, and in Mapper Type select User Property.
Add a separate attribute entry for each of First Name, Last Name, and Email.
Note
You must use these defined Property name values in the Property field.
Attribute
Property
Purpose
Email
email
To pass the email value to the service provider.
First Name
firstName
To pass the first name value to the service provider.
Last Name
lastName
To pass the last name value to the service provider.
Set the SAML Attribute Name value to be the same as each corresponding Property name value.
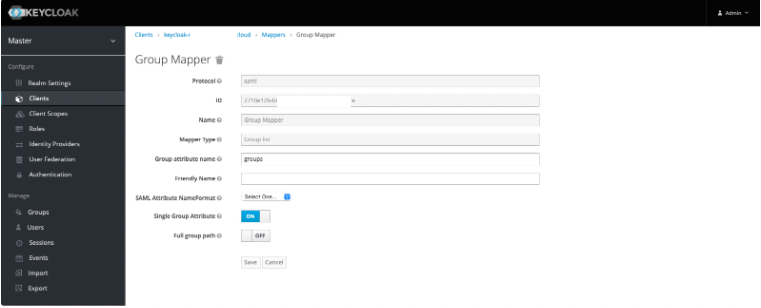
Click Create, and in Mapper Type select Group List to create a Group Mapper.
Note
You must use groups as the defined Group attribute name.
Attribute | Group attribute name | Purpose |
Group | groups | To pass the groups value to the service provider. |
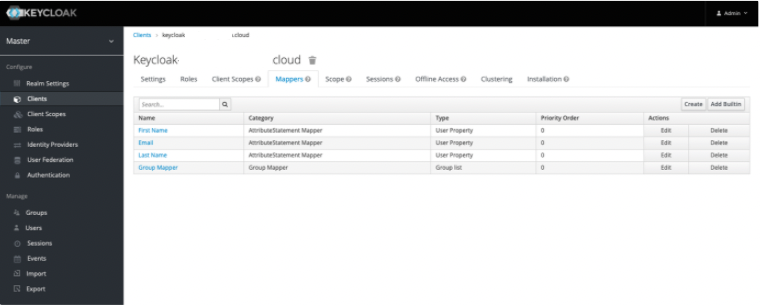
Steps: Configure attribute mapping in CloudConnexa
To finalize your attribute mapping set up, you must ensure that the Property values and SAML Attribute values match the Attribute Mapping values in your SAML Configuration on CloudConnexa.
Access CloudConnexa > Settings > User Authentication > SAML > View Attirbute Mapping to check that those values match :
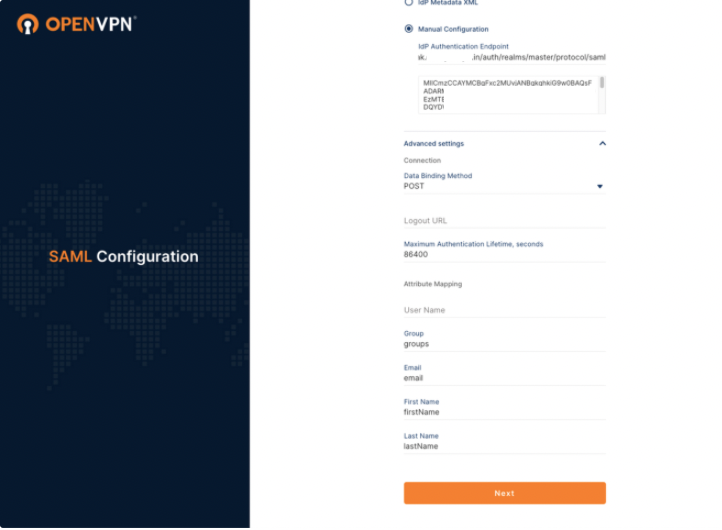
Steps: Set up group mapping in CloudConnexa
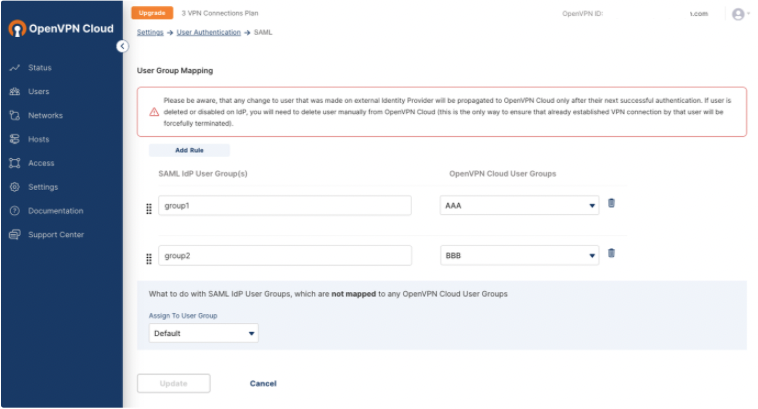
Access CloudConnexa Settings > User Authentication > SAML > View Group Mapping and click Add Rule.
Enter the name of the group(s) from your identity provider under SAML IdP User Group(s) and then select a group from the CloudConnexa User Groups that you want to map to your IdP group(s).
Steps: Sign in to User Portal with Keycloak
Navigate to the CloudConnexa account page at: https://myaccount.openvpn.com/product-select
Click Not an Owner? Sign In Here.
CloudConnexa recognizes that your domain uses SAML and displays the Single Sign On prompt.
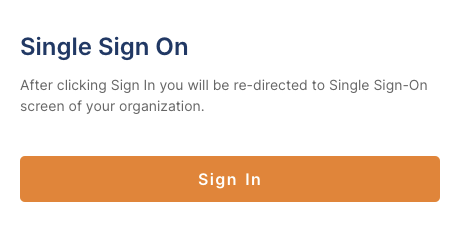
Click Sign In.
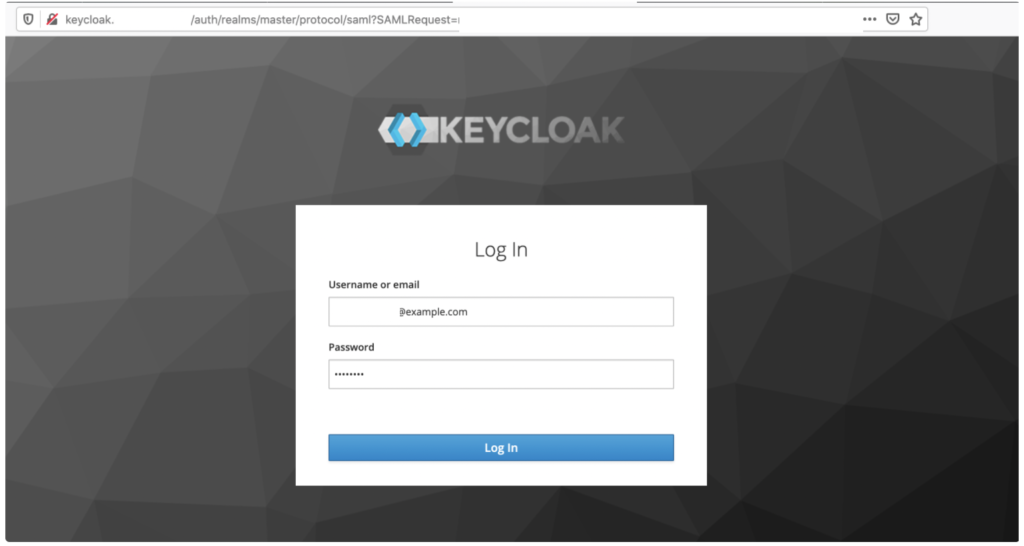
The Keycloak Log In page opens.
Enter the Keycloak test account email and password and click Log In.
The CloudConnexa Get Connected page opens with app download and installation instructions.
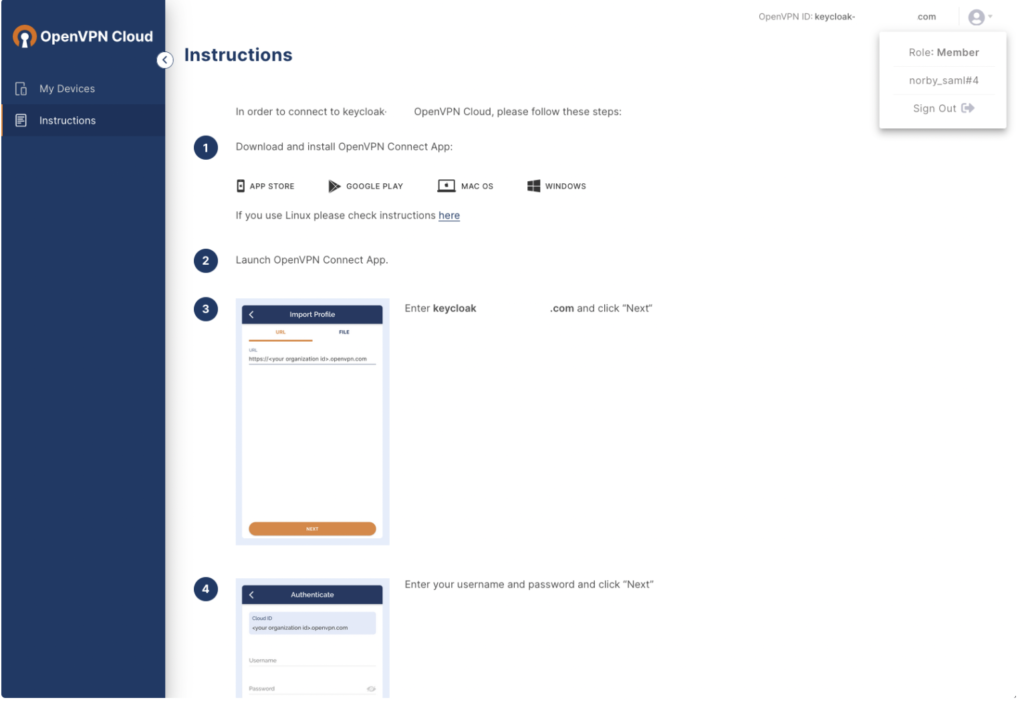
Tutorial: Authenticate Using SAML with Okta
This tutorial shows the steps to authenticate your Users using SAML. You can configure CloudConexa SAML authentication to use Okta as the Identity Provider.
Configuring CloudConnexa User authentication to use SAML
The Administrator can configure CloudConnexa to authenticate access to the User Portal, download of WPC Profile, and WPC connections using a SAML 2.0 compliant Identity Provider.
The Administrator needs to follow the steps below. The steps below use Okta as the Identity Provider. Basic configuration guides for some of the other popular Identity as a Service (IDaaS) providers are provided separately.
Sign in to the CloudConnexa Administration portal at
https://cloud.openvpn.com/.Navigate to Settings section and click on the User Authentication tab.
Click on the Edit button positioned on the top right
Click on the Configure button under the SAML option
The SAML Configuration web page opens in a new browser window/tab and shows the information needed to configure CloudConnexa as a Service Provider in your Identity Provider.
Login to the administration console of the Identity Provider to configure CloudConnexa as a SAML Service Provider. The steps for Okta are below:
Navigate to Applications tab, Add Application and click on the Create New App button.
Select Platform as Web and SAML 2.0 as Sign on method then click on the Create button.
Provide an Application Name and click on the Next button. In the General tab:
Enter the Issuer Name displayed in the SAML Configuration web page of CloudConnexa into the Audience URI (SP Entity ID) input field of Okta
Enter the SSO URL displayed in the SAML Configuration web page of CloudConnexa into the Single Sign On URL Validator and ACS (Consumer) URL input field of Okta
Checkmark the Use this for Recipient URL and Destination URL option
Select EmailAddress as the Name ID format
Click on the Next button
On the last page, select I'm an Okta customer adding an internal app, and click on the Finish button.
Click on the Sign On tab and click on the View set up Instructions button.
The
X.509 Certificateand the Identity Provider Single Sign-On URL will be needed later. Copy and paste this information for use later or keep this browser window open.Now that CloudConnexa has been set up as an application, you need to provide applicable Users access to CloudConnexa application. Click on the Assignment tab of the application and assign it to applicable Users or select the User and assign the application.
Okta will only provide the NameID value to the Service Provider by default which CloudConnexa will map to the username of the User. If you want CloudConnexa to have more information about the User and to use the value of a specific User attribute to map the User into a CloudConnexa User Group, you need to configure parameters to be sent from Okta to App See, https://help.okta.com/en/prod/Content/Topics/Users-groups-profiles/usgp-map-attributes.htm. In addition, refer to this support document.
Go back to the browser tab/window displaying the CloudConnexa and take the following actions:
Click on the Next button
Provide an IdP Name Select Manual Configuration, and do the following:
Click on the Next button
Provide an IdP Name, Select Manual Configuration, and do the following:
Paste the Identity Provider Single Sign-On URL value copied earlier in step ‘2.f’ into the IdP Authentication Endpoint
Paste the
X.509 Certificatecopied earlier in step ‘2.f’ into theIdP X.509 Public Certificate
If earlier in step ‘2.h you had set up additional parameters to map into CloudConnexa User information, do the following or else click on the Next button:
Expand the Advanced settings section
In the Attribute Mapping section provide the Identity Provider parameter names corresponding to the CloudConnexa User information fields that you want to be populated with information from the Identity Provider’s parameters (SAML attributes) and click on the Next button when done
Click on the Finish button after reviewing the SAML configuration
Now that the SAML configuration is done, we need to enable SAML as the User authentication method by clicking on the Edit button in the User Authentication tab
Select the SAML option
If earlier in step ‘2.h’ you had set up an additional parameter with the intention to map the value of that parameter to CloudConnexa User Group, do the following or else click on the Update Settings button:
Click on the Add Rule button
Enter in SAML IdP User Group(s) field one or more of the values that will present in the IDP provided parameter that you had mapped to the Group attribute in step ‘3.c.ii’and select the corresponding you want those values to map into. For example, the IdP User’s department value of ‘DEV’ could map to CloudConnexa User Group ‘Dev’ which has been configured to provide access to resources for developers. Repeat the step to add more rules as desired and click on the Update Settings button when done
Click the Confirm button on the confirmation dialog
SAML is now enabled
Login to User Portal
Now that SAML is enabled for the WPC when a User wants to sign in to the User Portal to download Connect Client or manage Devices etc., the User will sign in using SSO credentials. When the User visits the User Portal (for example, at https://test8.openvpn.com), the User will see the Identity Provider’s login screen
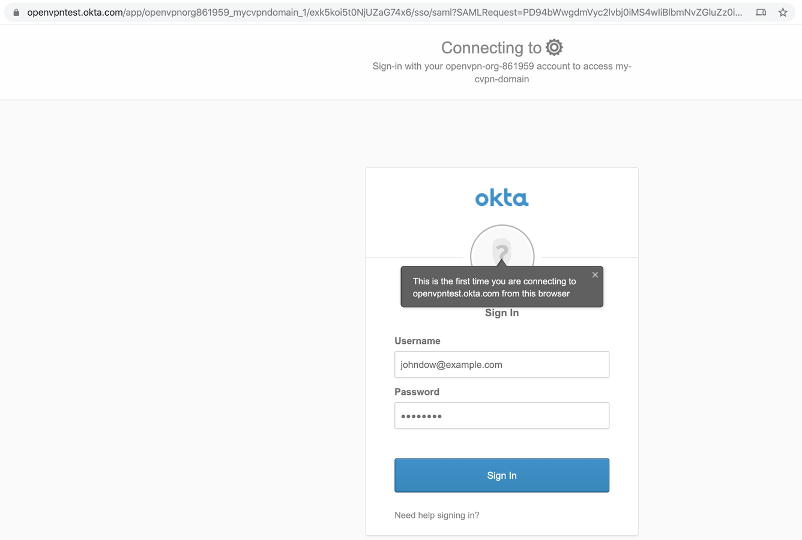
On successful first authentication, the Administrator will see the User details show up in the Administration portal.
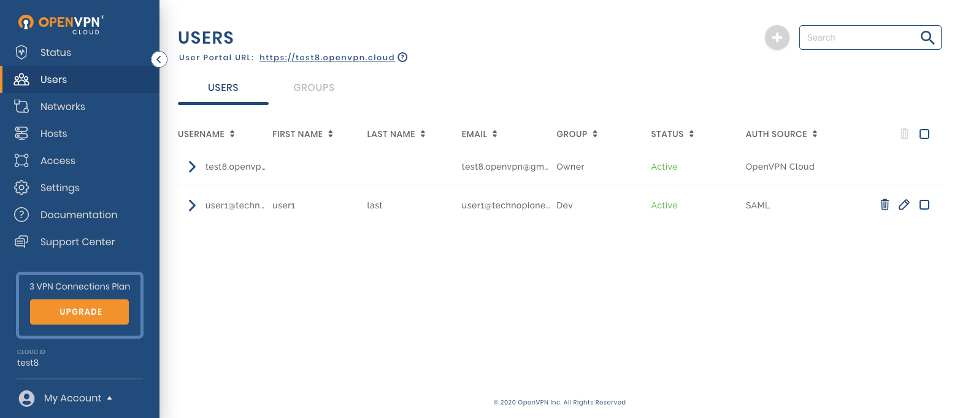
In the screenshot above, you can see that the user1 has been added after SAML authentication because the Auth Source is shown as SAML.
Tutorial: Authenticate Using SAML with OneLogin
This tutorial shows the steps to authenticate your Users using SAML. You can configure CloudConexa SAML authentication to use OneLogin as the Identity Provider.
Configuring CloudConnexa User authentication to use SAML
The Administrator can configure CloudConnexa to authenticate access to User Portal, download of WPC Profile, and WPC connections using a SAML 2.0 compliant Identity Provider.
The Administrator needs to follow the steps below. The steps below use OneLogin as the Identity Provider. Basic configuration guides for some of the other popular Identity as a Service (IDaaS) providers are provided separately.
Sign in to the CloudConnexa Administration portal at https://cloud.openvpn.com.
Navigate to Settings section and click on the User Authentication tab
Click on the Edit button positioned on the top right
Click on the Configure button under the SAML option
The SAML Configuration web page opens in a new browser window/tab and show the information needed to configure CloudConnexa as a Service Provider in your Identity Provider
Sign in to the OneLogin administration console to configure CloudConnexa as a SAML service provider.
Navigate to Applications tab and click on the Add App button
Enter SAML Test Connector (Advanced) in the search bar to find the application and click on it
Provide a Display Name and click on the Save button to add the application and start configuring it
Navigate to Configuration
Enter the Issuer Name displayed in the SAML Configuration web page of CloudConnexa into Audience (Entity ID) input field of OneLogin
Enter the SSO URL displayed in the SAML Configuration web page of CloudConnexa into both the ACS (Consumer) URL Validator and ACS (Consumer) URL input fields of OneLogin
Select Assertion as the drop-down list value for the SAML signature element field and click on the Save button
OneLogin will only provide the NameID value to the Service Provider by default which CloudConnexa will map to the username of the User. If you want CloudConnexa to have more information about the User and to use the value of a specific User attribute to map the User into a CloudConnexa User Group, you need to configure additional parameters to be sent by navigating to the Parameters tab and clicking on the Add (+ icon)
Click on the Include in SAML assertion checkbox, provide a Field Name, and click on the Save button
Choose and select a Value that is one of the attributes of the User. You can search for the attribute too.
Click on the Include SAML assertion checkbox and click on the Save button
Repeat the above process for adding more parameters that will correspond to the username, email, first name, last name, and User Group of CloudConnexa User. Once done, navigate to the SSO tab
Click on the copy/paste icon next to the Issuer URL in order to copy the value in the field. This will be used later in the CloudConnexa configuration.
Now that CloudConnexa has been set up as an application, you need to provide applicable Users access to CloudConnexa application. One of the ways to do this is to:
Select the User and click on the Applications tab
Click on the Add (+ icon) to add an Application for the User
Select the newly configured CloudConnexa application and click on the Continue button
Go back to the browser tab/window displaying the CloudConnexa and take the following actions:
Click on the Next button
Provide an IdP Name and paste the Issuer URL value copied earlier in step ‘2.m’ into the IdP Metadata URL
If earlier in step ‘2.h’ you had set up additional parameters to map into CloudConnexa User information, do the following or else click on the Next button:
Expand the Advanced settings section
In the Attribute Mapping section provide the Identity Provider parameter names corresponding to the CloudConnexa User information fields that you want to be populated with information from the Identity Provider’s parameters (SAML attributes) and click on the Next button when done
Click on the Finish button after reviewing the SAML configuration
Now that the SAML configuration is done, we need to enable SAML as the User authentication method by clicking on the Edit button in the User Authentication tab
Select the SAML option
If earlier in step ‘2.h’ you had set up an additional parameter with the intention to map the value of that parameter to CloudConnexa User Group, do the following or else click on the Update Settings button:
Click on the Add Rule button
Enter in SAML IdP User Group(s) field one or more of the values that will present in the IDP provided parameter that you had mapped to the Group attribute in step ‘3.c.ii’and select the corresponding you want those values to map into. For example, the IdP User’s department value of ‘DEV’ could map to CloudConnexa User Group ‘Dev’ which has been configured to provide access to resources for developers. Repeat the step to add more rules as desired and click on the Update Settings button when done
Click the Confirm button on the confirmation dialog
SAML is now enabled
Login to User Portal
Now that SAML is enabled for the WPC when a User wants to sign in to the User Portal to download Connect Client or manage Devices etc., the User will sign in using SSO credentials. When the User visits the User Portal (for example, at https://test8.openvpn.com), the User will see the Identity Provider’s login screen
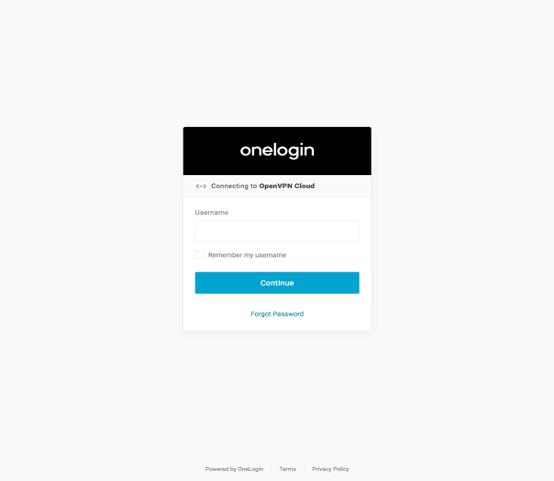
On successful first authentication, the Administrator will see the User details show up in the Administration portal.
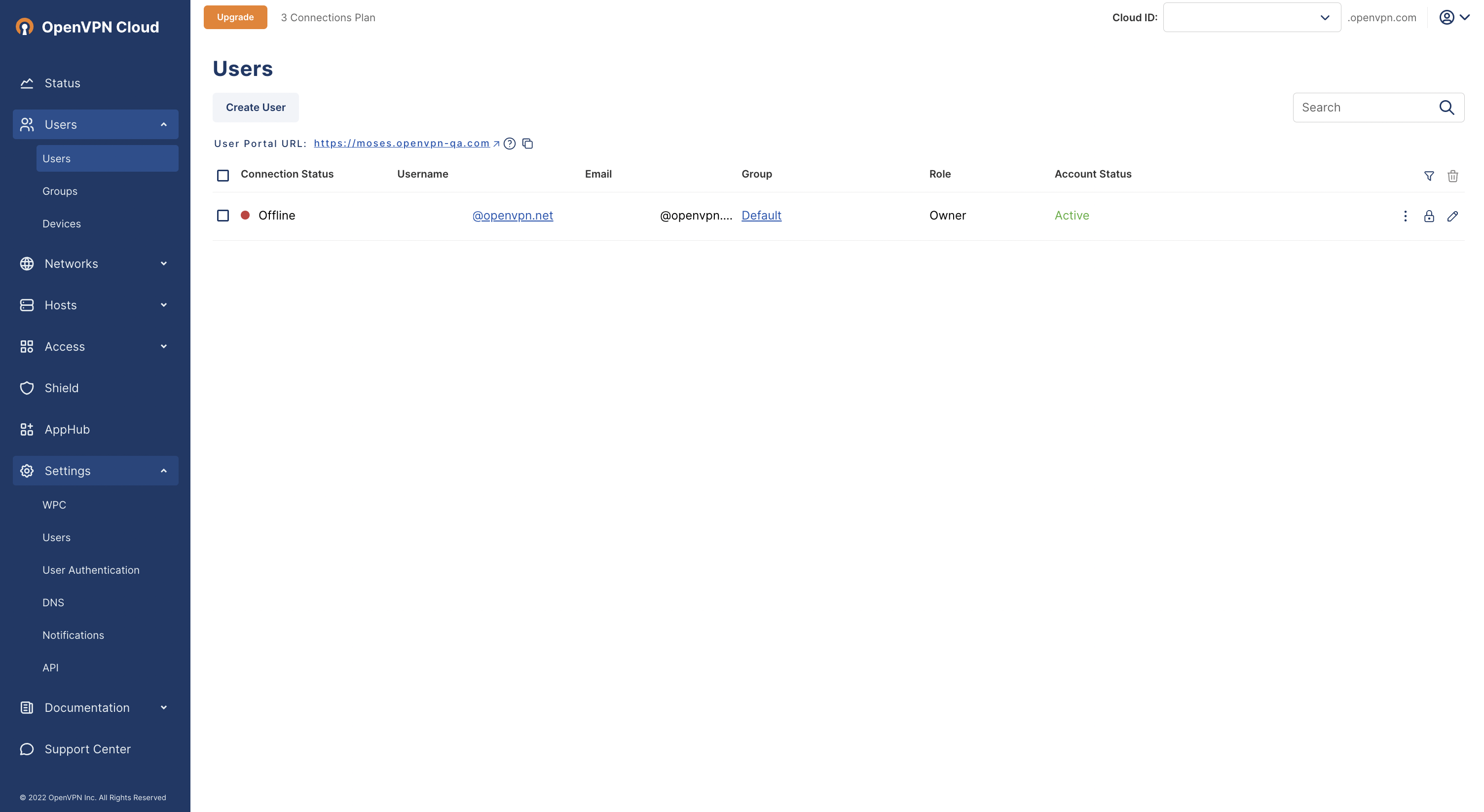
In the screenshot above, you can see that the user1 has been added after SAML authentication because the Auth Source is shown as SAML.
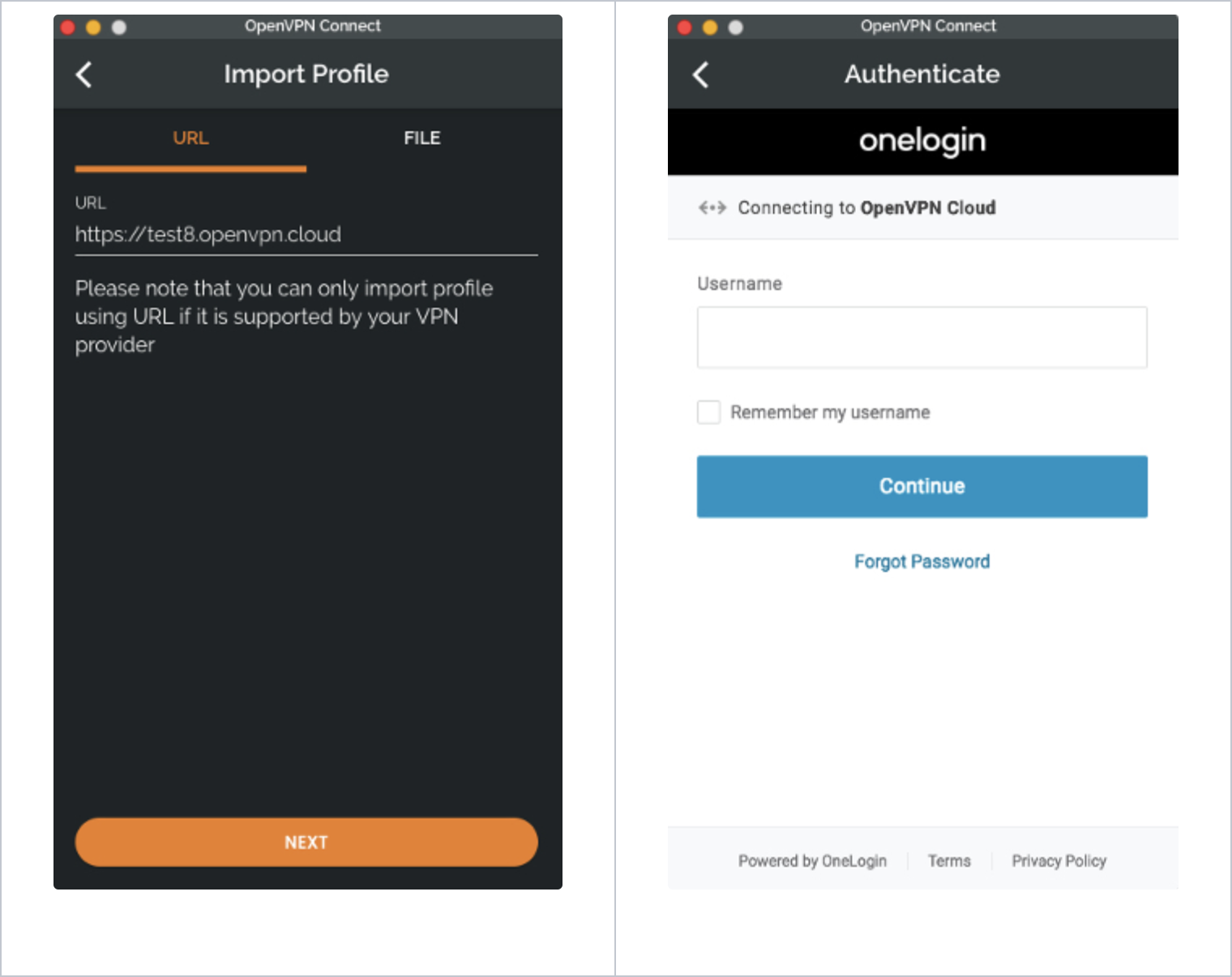
Authentication during Profile download
Now that SAML is enabled for the WPC when a User wants to add the WPC Profile using Connect Client, the User will sign in using SSO credentials.
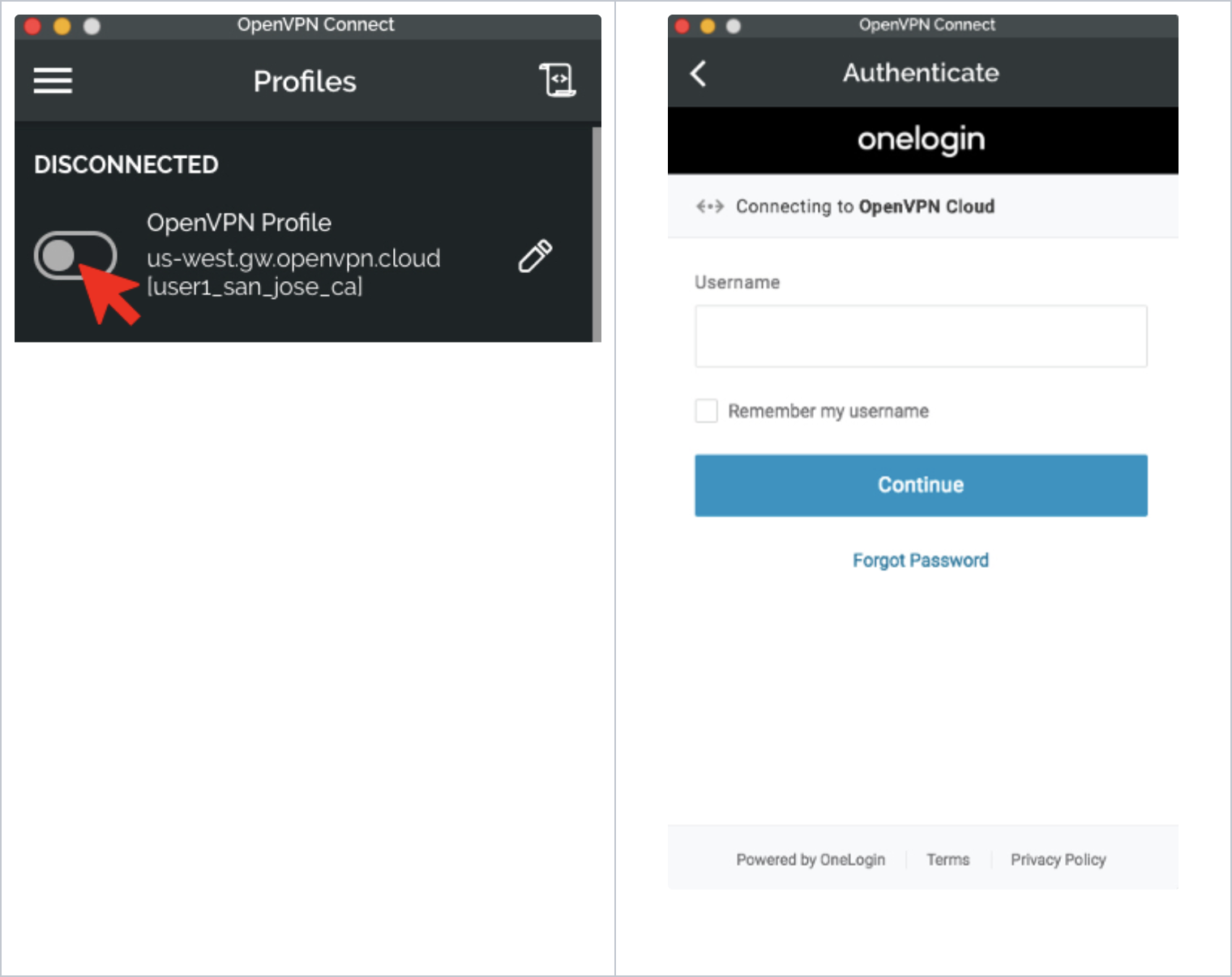
Authentication during WPC connection
Now that SAML is enabled for the WPC when a User belonging to a User Group whose Authentication Type parameter is set as Password and Profile wants to connect to the WPC using Connect Client, the User will sign in using SSO credentials.
Tutorial: Login to User Portal From SAML Identity Provider
You can have your users to sign in to the CloudConnexa User Portal directly from your SAML IdP application dashboard.
If you want your Users to sign in to the CloudConnexa User Portal directly from your Identity Provider’s application dashboard, please follow the steps below:
Note
Sign in from the Identity Provider’s dashboard will not result in a WPC connection. Users will still need to establish a WPC connection using OpenVPN Connect client.
First, carry out the steps below to find the value of the Relay State used during the SAML authentication:
Install and open SAML extension (https://chrome.google.com/webstore/detail/saml-devtools-extension/jndllhgbinhiiddokbeoeepbppdnhhio?hl=en-US) using Chrome web browser
Login to CloudConnexa as a User by opening
https://[cloud-id].openvpn.comusing the Chrome web browserFind and click on the resulting SAML response/request in the opened SAML extension
Find and copy the value for Relay State (see the screenshot below)
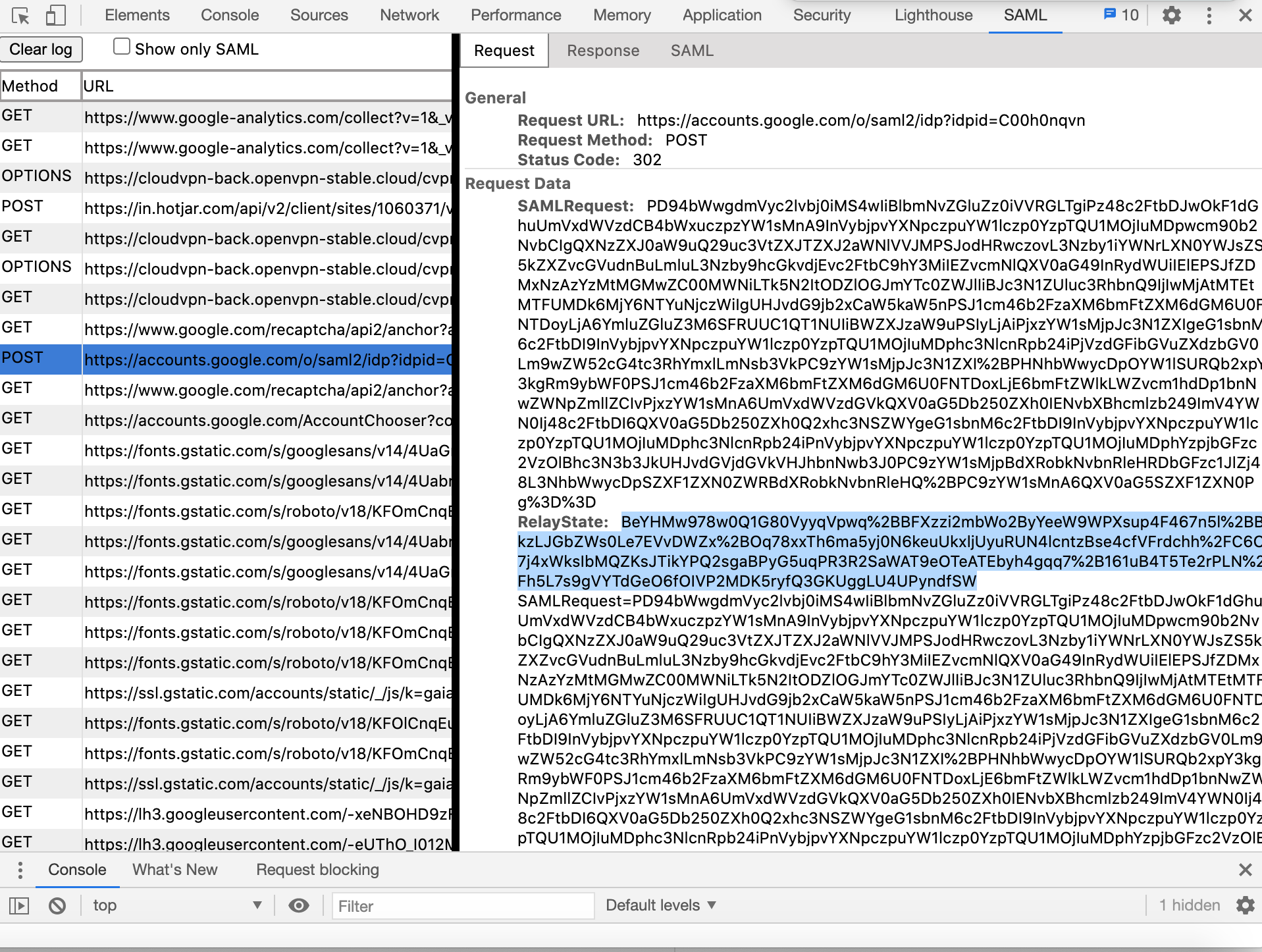
Paste the copied value into https://www.urldecoder.org/ and decode
Log into the Identity Provider’s Administration portal and carry out these steps:
Open the settings for the application configured to represent CloudConnexa
Copy decoded value from step 1.e and paste it in the Relay State or equivalent field
After some time, changes will take effect on IdP side and Users will be able to login to the CloudConnexa User Portal from the Identity Provider’s application dashboard.