Introduction to CloudConnexa
CloudConnexa is a cloud-delivered service that provides a secure networking and remote access solution with the essential features needed to implement a zero-trust solution. It enables a smooth transition from perimeter security to zero-trust network access.
Introduction
CloudConnexa is a cloud-delivered service that provides a secure networking and remote access solution with the essential features needed to implement a zero-trust solution. It enables a smooth transition from perimeter security to zero-trust network access.
The service can be accessed by connecting to one of CloudConnexa's Points of Presence (PoP) worldwide. CloudConnexa is a multi-tenant service that creates a virtual private overlay network that spans all the PoPs. This overlay network provides connectivity and access to various entities, users, private network applications, or IoT devices.
CloudConnexa also has vertically integrated security features like content filtering and IDS/IPS into the service. Refer to Cyber Shield.
How does CloudConnexa work?
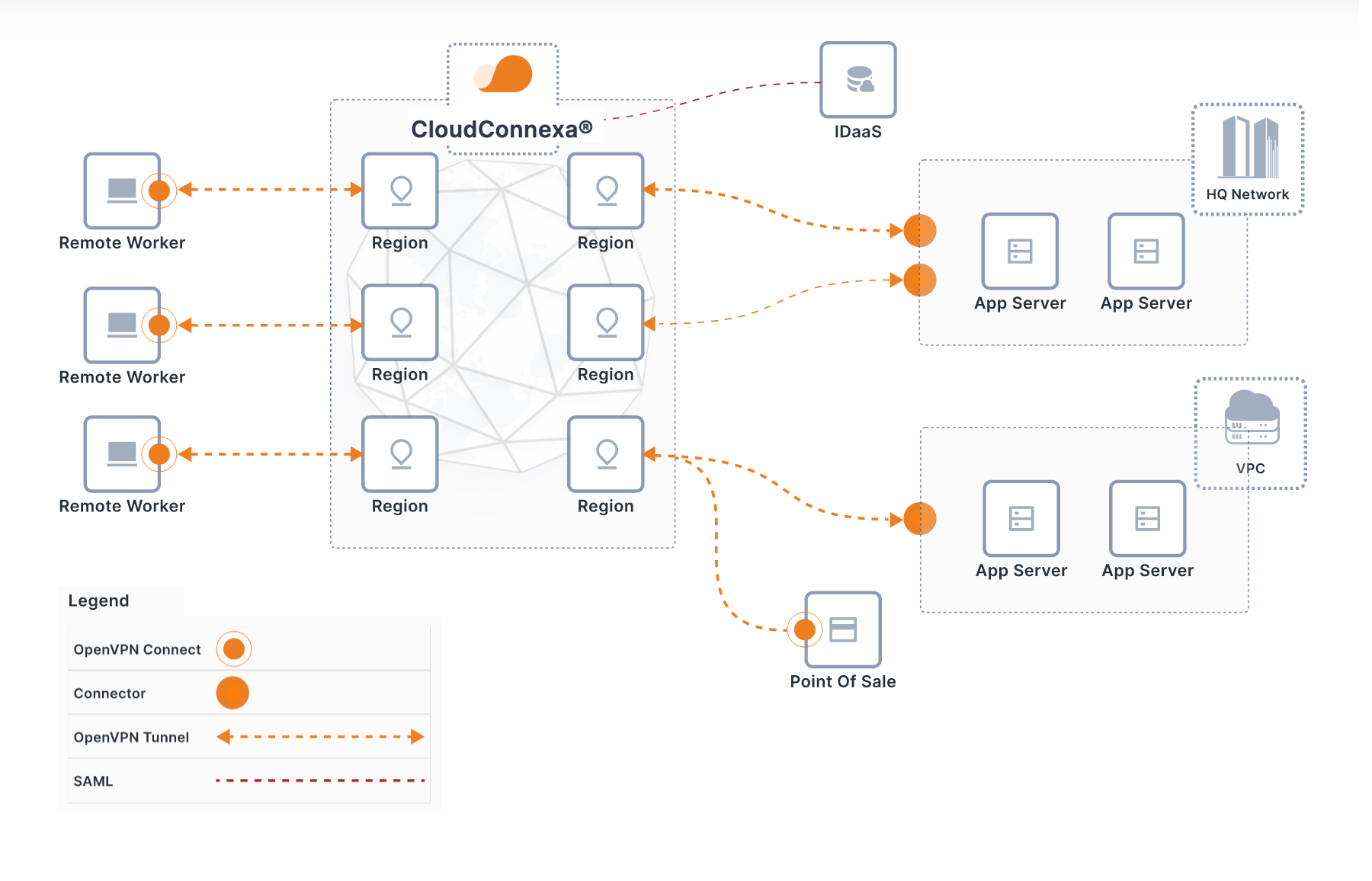
The worldwide CloudConnexa PoPs are called Regions. CloudConnexa has data centers in these geographical areas, where the service's multi-tenant, kernel-optimized, high-performance servers are hosted.
These Regions interconnect using a full-mesh topology. Full-mesh connectivity ensures that there is always direct connectivity between Regions to reduce latency and redundant routes present.
CloudConnexa service is multi-tenant. That means that the Regions, the core network that connects all these Regions, and all other elements of this platform are shared with all customers and are virtually isolated. As there are no dedicated servers for each customer, the service is efficient, available from all Regions, and can be instantly configured.
A virtual overlay network, called Wide-area Private Cloud (WPC), is created immediately when you sign up for CloudConnexa. You will be asked to provide a Cloud ID, a unique identifier to identify your WPC. Your Cloud ID will be whatever you provide as long as it is unique. It's of the format [company_name].openvpn.com. By forming a URL with this Cloud ID https://[company_name].openvpn.com, you can access the Administration portal and import connection configuration files into clients. The connection configuration files are called connection Profiles. Connection profiles (.ovpn text files) contain the directives, parameters, and certificates required to establish the OpenVPN connection to Regions. These commonly include addresses and ports to contact the server, information for verifying peer identity, securing the TLS control channel, and other settings.
In simple terms, you can think about your CloudConnexa WPC (identified with the Cloud ID) as a virtual distributed router and a powerful next-generation firewall out there in the cloud and the 30+ worldwide Regions as the virtual ports of this router. How do you connect users, servers, and networks to the ports (that is, Regions) of this virtual distributed router (your WPC)? CloudConnexa uses the OpenVPN protocol to create secure encrypted tunnels over the internet to those Regions. Think of the OpenVPN tunnels as a virtual super-long ethernet cable that connects your devices to the ports of your cloud router (that is, your WPC). So, what is needed to create those tunnels? You need to use a client app on the device that needs to set up the tunnel. The official client is OpenVPN Connect. It is available for Windows, macOS, iOS, and Android. For Linux, we recommend using our open-source openvpn3 client, which also supports DCO, a technology that further improves data throughput performance. OpenVPN protocol-compatible routers like Ubiquiti and firmware like OpenWrt and others can be used, too.
Why is the same OpenVPN client application sometimes called a client and sometimes a Connector? The term Connector distinguishes the connection from a typical on-demand client connection like that of remote users. Even though it is the same client app, the context in which it is set up in the Administration Portal and the corresponding connection profile allows the Connector to create an always-on unattended connection. A Connector provides access to applications hosted on servers it runs on or networks it connects to the WPC. So, to summarize, Connectors make networks and applications part of the WPC, and Devices with the client app installed are used to connect to the WPC to consume service made available via Connectors.
Hosts, Networks, and Applications are representations of an application server, a private Network, and any TCP/IP service with a domain name in CloudConnexa. So an application server on which the connector is installed to provide access to the application that is being served is represented as a Host in CloudConnexa, whereas a private network that provides access to the WPC for the devices on the network and can also provide access to others for applications hosted on that private network or site is represented as a Network entity in CloudConnexa. Applications are services that are identified by a domain name that are made accessible to the WPC. Services that need to be accessed using IP addresses are represented by IP Services.
Access Groups can be configured to control access to Networks, Hosts, and the Applications and IP Services they make available.
Once Connectors set up outbound tunnels to CloudConnexa Regions, your users can connect to any of the CloudConnexa Regions with their devices and access the Applications and IP Services your connected Networks and Hosts make available.
CloudConnexa Owner's Guide: Secure Networking & ZTNA Explained
CloudConnexa is a cloud-delivered service offering a secure networking and remote access solution designed to implement a zero-trust framework. It facilitates a smooth transition from traditional perimeter security to modern Zero Trust Network Access (ZTNA).
Key characteristics include:
Multi-tenant service: CloudConnexa creates a "virtual private overlay network" called a Wide-area Private Cloud (WPC) that spans across its global Points of Presence (PoPs), known as Regions. This overlay network is shared among customers but "virtually isolated," ensuring efficiency and instant configuration.
Global Reach: The service is accessible by connecting to one of CloudConnexa's worldwide PoPs (Regions), allowing resources, users, and devices to connect from anywhere with internet access.
Integrated Security: It includes "vertically integrated security features like content filtering and IDS/IPS" (Intrusion Detection System/Intrusion Prevention System) through its Cyber Shield functionality.
VPN Protocol: CloudConnexa uses the OpenVPN protocol to establish "secure encrypted tunnels over the internet" connecting devices to its Regions. The official client application is OpenVPN Connect, available for various operating systems.
A WPC is a "virtually dedicated worldwide private network exclusively for your use," created upon signing up for CloudConnexa.
Cloud ID: Each WPC is uniquely identified by a Cloud ID, chosen during signup (e.g., [company_name].openvpn.com). This ID is permanent once set.
Administration Portal: The Administration Portal and connection profiles are accessed via https://[Cloud ID].openvpn.com.
Virtual Router: A WPC can be conceptualized as a "virtual distributed router and a powerful next-generation firewall out there in the cloud," with Regions acting as its "virtual ports."
Multiple WPCs: An owner can manage "multiple independent WPCs from the same account" for different departments or use cases, providing complete isolation and segmentation.
Regions are the "geographic area that serves as a CloudConnexa Point of Presence (PoP)."
Infrastructure: Each Region hosts "high-performance multi-tenant servers" across multiple data centers.
Full-Mesh Topology: All CloudConnexa Regions are "interconnected using a full-mesh topology," ensuring direct connectivity, reduced latency, and redundant routes.
Connection Point: Devices, Networks, and Hosts must connect to a Region to join the WPC. It's recommended to choose the closest Region for optimal performance.
IPv6 Support: CloudConnexa Regions support IPv6, allowing dual-stack and IPv6-only devices to use IPv6 for transport without fallback to IPv4.
Global Distribution: Regions are located worldwide, including numerous cities in the USA (e.g., Los Angeles, Chicago, New York), Canada (Montreal, Toronto, Vancouver), Europe (London, Paris, Frankfurt), and Asia Pacific.
Service Health Status: The health of the CloudConnexa service, including individual Regions, can be monitored on a dedicated status page.
Connectors are used by private networks and application servers to interface with CloudConnexa and provide continuous, "always ON" connectivity.
Types:
Network Connector: Connects an entire private network to CloudConnexa, acting as a router between the WPC and the private network. It can be deployed on hardware routers or general-purpose computing devices/VMs configured as software routers.
Host Connector: Connects a specific host (e.g., an application server or IoT device) to CloudConnexa, making services available on that host accessible through the WPC.
Deployment: Connectors can be deployed using OpenVPN or IPsec tunneling protocols. CloudConnexa provides specific guides and templates for various platforms, including:
Routers: DD-WRT, OpenWrt, PfSense, Teltonika, Ubiquiti (EdgeMAX).
Cloud IaaS: AWS VPC (using VPG or Transit Gateway), Azure VNet (using ARM templates), GCP VPC.
Operating Systems: Windows Server (for routing and NAT), macOS (for routing and NAT), Linux (OpenVPN 3 client with DCO support).
Profile Management: Connection profiles (.ovpn files) are downloaded from the Administration Portal for configuration. For Linux, a token can be used with the openvpn-connector-setup command.
SNAT: Source Network Address Translation (SNAT) can be enabled to set the source IP address of all inbound traffic from the WPC to the IP address of the connected Region, simplifying routing configuration for remote access by eliminating the need for backward routing.
Status Monitoring: The Administration Portal's "Status" page displays the number of currently online Connectors and allows for filtering and viewing detailed connection information. Notifications for Connector status changes can be configured.
CloudConnexa distinguishes between Owners, Administrators, and Members (Users).
Owner Role: The creator of the CloudConnexa account, possessing "billing and subscription management privileges in addition to configuration and management."
Administrator Role: Has "the same privileges as the account Owner except" for subscription, billing, and changing/deleting the Owner's account.
Member Role: Standard users with "no special administrative privileges," who simply use the service as configured.
User Provisioning: Users can be added manually (individually or in bulk via API), or through external Identity Providers (IdP) like SAML (Okta, Azure AD, OneLogin, G Suite, Keycloak) or LDAP, which allow for automatic assignment to User Groups based on identity attributes.
Authentication: Supports CloudConnexa's username/password, SAML Single Sign-On, and Private LDAP authentication.
Security Features for Users:
Two-Factor Authentication (2FA): Can be enabled for users, with an option to allow trusted devices. Owners can clear trusted devices or reset 2FA for a user.
Device Identity Verification & Enforcement (DIVE): Reduces the attack surface by "locking the device profile containing the digital certificate to the device's identity," ensuring "only authorized devices to connect to your WPC." Policies can be configured based on OS, OS version, antivirus presence, client certificate, and disk encryption.
Connection Timeout: Configurable setting to automatically disconnect user connections after a specified duration (default 24 hours) for security policy enforcement.
Connect Auth Policy: Determines if and when a user is prompted for credentials during connection (e.g., "Every time," "On prior auth timeout," "No").Device Allowance: Limits the "maximum number of Devices per user account" that can connect to the WPC.
Profile Distribution Mode: Can be "Automatic" (default, where devices and profiles are automatically created on user authentication) or "Manual" (requiring the owner/admin to create devices and distribute .ovpn profiles offline).
User Groups allow "a set of Users to share common settings" and differentiate configurations.
Settings Shared:
Allowable Regions for connection.
Connection authentication mode (Connect Auth).
Maximum devices per user.
Mode of internet traffic routing (Internet Access method).
Access control to specific Networks, Hosts, Applications, or IP Services (via Access Groups).
Required device posture attributes (Device Posture policies).
Required location context (Location Context policies).
Primary and Secondary User Groups: A user belongs to one Primary User Group (PUG), which defines inherited settings. They can also be assigned to up to twenty Secondary User Groups (SUGs), which provide "additive access to resources."
IdP Integration: User Group Mapping with SAML or LDAP allows automatic assignment of PUG and SUGs based on identity attributes, with priority rules for mapping.
Location Context Policy: Allows or blocks connections "based on the IP address of the connecting device," considering IP address ranges or country (determined by IP geolocation).
Device Posture Policy: Configures policies "to allow or maintain the connection" based on device attributes such as operating system, OS version, antivirus software, client certificate presence, and disk encryption.
A CloudConnexa Network is a "representation of your actual physical private network" and its reachable Applications and IP Services.
Purpose: Connects private networks to the WPC, allowing users to access private applications or using the network for internet access.
Routing Options:
Application Domain-based Routing (Recommended): Routes traffic to applications using their domain names, even if IP addresses overlap across networks. It "cloaks IP addresses," making the actual application server IPs and network routes not disclosed to the client. This also allows for per-application micro-segmentation.
IP Routing (IP Services): Identifies traffic to be routed based on subnet IP addresses configured as IP Services.
Both can be used concurrently.
Internet Gateway: A Network can be configured to act as an "Internet Gateway," providing "an exit point (default route)" for internet traffic from the WPC. This is crucial when "Internet Access" for User Groups, Networks, or Hosts is set to 'Split Tunnel OFF' (all traffic tunneled). Multiple Internet Gateways can be set up, with CloudConnexa's "smart routing algorithm" choosing the most optimum route based on geographic proximity and network characteristics.
Management: Networks can be added using a Network Wizard (for remote access, secure internet access, or site-to-site connectivity scenarios) or form-based configuration. Details include connection status, Internet Access/Gateway settings, tunneling protocol, and allocated WPC subnets.
Routes Configuration: When enabled, allows defining custom routes for Networks to optimize the routing table pushed to clients and Connectors.
A Host is a "computing entity (for example, a desktop, smartphone, or IoT device) with an installed OpenVPN client that accesses the WPC."
Purpose: Provides services running on that specific Host to be accessible via the WPC.
Applications & IP Services: Granular services can be configured for access control. Host Applications use domain names implicitly resolved to the Host Connector's tunnel IP address. Host IP Services define accessible IP address subnets and protocols.
Deployment: A Host Connector is installed directly on the Host.
Internet Access: Can be configured to restrict internet access, tunnel all internet traffic through CloudConnexa, or allow direct internet exit.
Access Groups define "specific access control configuration by specifying the access relationship between Sources (i.e. Who?) and Destinations (i.e. What?)."
Default Behavior: When a WPC is newly created, the topology is 'Full Mesh' with an 'allow by default' policy. Access Groups become active and enforce a 'deny by default' approach when the WPC Topology is set to 'Custom'.
Components:
Sources: User Groups, Hosts, Networks, and source IP Services from those Networks.
Destinations: Shared Applications via AppHub, User Groups, Hosts, Networks, and IP Services/Applications reachable from Networks or Hosts
Bidirectional: If access is allowed from Source A to Destination B, it implies bidirectional communication (B can communicate with A).
Use Cases: API Access Control, Site-to-Site Access Control, Site-to-Applications Access Control, IP Subnet-to-IP Subnet Access Control.
Important Note: After setting WPC Topology to 'Custom', the "Default Full Mesh Access Group" should be deleted or edited for specific access policies to take effect.
Manages how internet traffic is routed for User Groups, Networks, and Hosts.
Settings:
Split Tunnel On (Level-1 Security): "Private and trusted internet traffic is tunneled; all other internet traffic uses local internet." "Trusted internet traffic" includes internet destinations (domain names or IP subnets) configured as Applications or IP Services.
Split Tunnel Off (Level-2 Security): "All traffic is tunneled; Internet traffic exits from selected Internet Gateways." This is used for maximum security and control, requiring at least one Network to be configured as an Internet Gateway.
Restricted Internet (Level-3 Security): Blocks all internet traffic except to trusted internet destinations, offering the "strictest control."
Internet Gateway Selection: Specific Internet Gateways can be chosen for User Groups, Networks, or Hosts to customize traffic control, improve load distribution, or match capabilities with security controls.
Cyber Shield is CloudConnexa's integrated security suite, protecting networks and users from cyber threats.
Components:
Domain Filtering (Content Filtering): Provides DNS content filtering to "block malicious and suspicious websites," even if internet traffic doesn't pass through the WPC. Classifies web content into 43 categories organized into eight groups.
Protection Levels: Offers preset levels ("Monitor Only," "Basic Protection," "Safe Browsing," "High Productivity") or a "Custom" level to select individual categories to block. "Basic Protection" blocks "Malicious" categories (Malware, C2, Web spam/scam, Ransomware, Adware, Cryptojacking, DGA, Phishing).
Allow List: Defines domains that are "always allowed," overriding blocked categories.
Block List: Defines specific domains to block, creating a custom domain filtering category.
Domain Matching Logic: Checks domain names from right to left (TLD first).
Traffic Filtering (IDS/IPS): A built-in Intrusion Detection System (IDS) and Intrusion Prevention System (IPS). When monitoring, it identifies malicious traffic (malware, intrusion, DoS, phishing, vulnerabilities/exploits, known threats, adware, cryptojacking, Tor) based on signatures classified into three threat priority levels: Critical, High, and Medium. When blocking is enabled, it acts as an IPS.
Metrics & Reporting: Provides dashboards to view top 10 content categories and threat categories, event counts, and detailed reports (CSV exportable) for observed and blocked domain filtering and traffic filtering events.
AppHub provides a platform for "securely consuming and distributing applications between businesses," essentially creating a "secure extranet."
Roles:
App Provider: A business that shares its applications
App Client: A business that requests and consumes shared applications. (A business can be both.)
Application Sharing Process:
Invitation: App Provider sends an invitation using the App Client's email address or Cloud ID.
Reception: App Client receives the invitation. If not a CloudConnexa customer, directs to sign-up. If existing, directs to accept.
Approval: App Client approves the invitation (via email link or Administration Portal).
Activation: Access to the shared application becomes active for the App Client.
Access Control: The App Client can optionally set up an Access Group to control access to the shared application for its own users.
Use Cases: Sharing applications between different business entities or between multiple WPCs owned by the same company.
CloudConnexa offers comprehensive API and logging capabilities for programmatic management and auditing.
API:
Functionality: Allows programmatic configuration and management of the WPC.
Authentication: Requires creating API credentials (client ID and secret) and obtaining an OAuth 2.0 access token.
Documentation: Available in the Administration Portal (Swagger documentation).
Audit Log:
Purpose: Maintains records of all modifications to CloudConnexa configurations, including changes made by Administrators, API, and Users (via the User Portal). Crucial for security teams to identify unauthorized changes and for regulatory compliance (GDPR, HIPAA, PCI-DSS).
Logged Entities: Covers a wide range of configuration changes for Access Groups, Cyber Shield settings, Hosts, Networks, Users, User Groups, Device Posture policies, DNS settings, Log Streaming, and authentication settings.
Viewing & Exporting: Audit log entries can be viewed, filtered by various criteria (entity type, operation type, change source, initiator IP, etc.), and exported as CSV files.
DNS Log:
Purpose: Aggregates and presents statistics on all DNS requests made by connected clients through CloudConnexa's DNS servers. Shows allowed, blocked (by Cyber Shield), and failed requests.
Requirement: CloudConnexa DNS Proxy function must be enabled for DNS logs to be available.
Filtering & Exporting: Entries can be filtered by domain, query type, resolution status, user/device, host/connector, and user group. Exportable as CSV.
Log Streaming:
Purpose: Collects specific events from WPC log sources and streams them in JSON format (compressed as .gz files) to a configured AWS S3 bucket. Facilitates integration with third-party log collection tools like Splunk and DataDog.
Event Types: Includes DNS logs (registered domain and subdomain levels), OpenVPN tunnel connection/disconnection events, Cyber Shield Domain Filtering blocked events, and Cyber Shield Traffic Filtering blocked events.
Status & Notifications: Log Streaming status (Active, Paused, Error) can be monitored. Email alerts can be configured for status changes and when log events exceed a plan allowance.
The "Settings" section allows for global configuration of the WPC, Users, and DNS.
WPC Settings:
WPC Topology: Controls access control enforcement. "Full Mesh" (default) allows full access; "Custom" enables Access Groups for a "deny by default" approach.
Default Region for Connector: Sets the default CloudConnexa Region for new Connector configurations.
Source Network Address Translation (SNAT): When enabled, sets the source IP address of inbound traffic from the WPC to the connected Region's IP address. Disabled by default, with SNAT often handled by Connectors directly.
WPC Subnet Range: Configures the IP address range from which Tunnel IP addresses are assigned to User Devices and Connectors. Should not overlap with private networks.
Domain Routing IP Addresses: Sets the IP Subnet range for intermediary IP addresses used in Application Domain-based Routing.
Custom OpenVPN Options: Allows pushing custom OpenVPN options to all clients.
Enable Configuring Routes for Networks: When enabled, allows defining custom Routes under Network IP Services to optimize routing tables for Clients and Connectors.
User Settings:
Connection Timeout: Sets the maximum duration for user connections before automatic disconnection.
Default Connection Authentication (Connect Auth): Defines the default authentication policy for newly created User Groups.
Default Device Allowance: Sets the maximum number of devices per user for newly created User Groups.
Device Identity Verification & Enforcement (DIVE) Policy: Configures the DIVE policy for users, ensuring only authorized devices connect.
Profile Distribution Mode: Determines whether CloudConnexa automatically creates devices and profiles or if manual distribution is required.
User Authentication Method: Configures authentication for users (CloudConnexa username/password, SAML Single Sign-On, or Private LDAP).
User Group Mapping: For SAML and LDAP, allows mapping IdP attributes to CloudConnexa User Groups, supporting primary and secondary group assignments based on priority rules.
SCIM 2.0: Supports System for Cross-domain Identity Management (SCIM) for automatic user and group provisioning from IdPs (e.g., Okta, Azure, JumpCloud, OneLogin).
Two-Factor Authentication (2FA): Enables or disables 2FA for users and allows/disallows trusted devices.
DNS Settings:
Private DNS Servers: Allows configuring CloudConnexa to use external private DNS servers instead of its default.
DNS Records: Allows adding custom DNS records for public or private domains, which CloudConnexa's Proxy DNS servers will use for resolution.
Default DNS Suffix: Sets a default DNS suffix.
DNS Zone: Configures CloudConnexa's DNS proxy servers to forward DNS requests to different authoritative DNS servers based on defined zones.
CloudConnexa DNS Proxy: Can be turned off, but this impacts features like custom DNS, application routing, content filtering, DNS records, DNS zones, and AppHub application sharing.
Notifications: Configures email alerts for the Owner and Administrators for various events, including high subscription usage, subscription limit exceeded, Connector status changes (online/offline), LDAP Server connectivity warnings, and Log Streaming status changes/high usage.
The documentation provides extensive tutorials and use case examples for configuring CloudConnexa:
Remote Access & ZTNA: Accessing AWS VPC, GCP VPC, Azure VNet, home networks, remote desktop servers, and public SaaS applications. Includes implementing ZTNA with device posture, location context, and application domain-based routing.
Networking: Site-to-Site Networking (with IPsec or OpenVPN, and application domain-based routing), connecting networks with overlapping IP addresses, and deploying multiple Connectors for performance and availability.
Internet Security: Securing all internet traffic through an Internet Gateway, restricting login access to SaaS with whitelisting, securing DNS traffic, and using Cyber Shield for content filtering and IDS/IPS.
IoT Secure Communications: Securing IoT applications by connecting individual hosts or small networks.
Configuration Tutorials: Detailed guides for authentication (SAML, LDAP), Connectors (various OS and router types), DNS, Log Streaming, Device Identity Verification & Enforcement (DIVE), and Cyber Shield.
AppHub Usage Examples: Demonstrates sharing applications between different businesses and between multiple WPCs of the same business.
Automation: Includes details on using Public API and Terraform for automation.