Tutorial: Integrate Okta with Access Server via LDAP
Configuring Okta to integrate with Access Server can be done with LDAP. This requires requesting the LDAP Interface feature added to your Okta account.
Overview
Configuring Okta to integrate with Access Server can be done with LDAP. This requires requesting the LDAP Interface feature added to your Okta account.
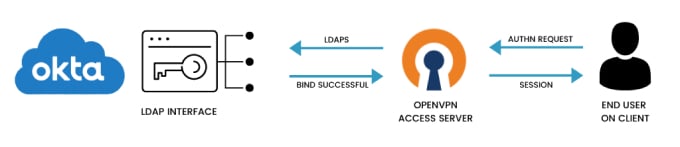
The following pieces will make up the LDAP integration between Okta and OpenVPN Access Server:
An active LDAP Interface in your Okta directory integrations.
An Okta Read Only admin account as your bind user.
Defining the configuration for the bind in Access Server.
An installed Access Server.
An Okta directory.
Sign in to the Okta Admin Console with Super admin privileges.
Click Directory > People.
Click Add Person and enter a username to distinguish them as the LDAP bind user.
After activating the user, click Security > Administrators.
Click Add Administrator and type your new user's name in the Grant administrator role to field.
Click Read Only Administrator.
Click Add Administrator.
Sign in to the Okta Admin Console with Super admin privileges.
Click Directory > Directory Integrations.
Click Add LDAP Interface.
Tip
If this isn't an option, you must request it from Okta Support.
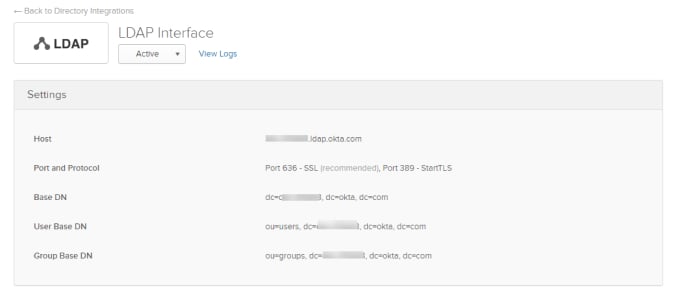
From the LDAP Interface page, you'll find most of the settings necessary for the configuration in Access Server.
Sign in to the Admin Web UI.
Click Authentication > LDAP.
Fill in the LDAP settings with the following information from Okta:
Primary Server
Host Name: <org_subdomain>.ldap.okta.com
Use SSL to connect to LDAP servers
Yes
Credentials for Initial Bind
Use these credentials = Yes
Bind DN
uid=<bind user email>, dc=<org_subdomain>, dc=okta, dc=com
Password
Enter the bind user's Okta password.
Base DN for User Entries
OU=Users, DC=<org_subdomain>, DC=okta, DC=com
Username Attribute
uid
Additional LDAP Requirements
Add additional parameters here, for instance, searching for members of a specific group, for example: memberOf=CN=<group>, OU=groups, DC=<org_subdomain>, DC=okta, DC=com
Users can now sign in with their Okta credentials.