Tutorial: Add Duo Two-Factor Authentication to Access Server
Follow these instructions to add Duo two-factor authentication to your users’ Access Server logins.
Overview
Adding Duo 2FA to Access Server provides your business with added security features. You’ll provide remote, encrypted connections for users and more secure authentication. By adding Duo’s authentication service through this integration, you extend the functionality. You add the ability for more authentication options, such as 2FA through SMS text, validation over a voice call, and push notifications with the Duo app.
Access Server also has built-in TOTP MFA support.
Important
If you using Duo MFA, you can't also enable TOTP MFA as it will cause user authentication problems.
When you add Duo 2FA to Access Server, your users' logins will be more secure. The diagram shows how the authentication flows with the setup.
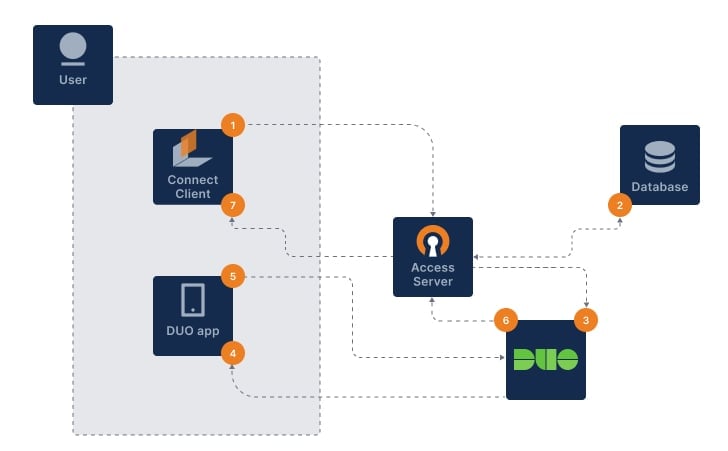
The user signs in with OpenVPN Connect.
Access Server authenticates username and password (primary auth).
Access Server notifies DUO via HTTPS API to begin the 2FA procedure.
DUO sends secondary auth via the user’s chosen method.
The user sends a correct response.
DUO sends an authentication response back to Access Server.
OpenVPN connection established.
A Duo account.
An installed Access Server.
Sign in to the Duo Admin Panel and click Applications.
Click Protect an Application, then find OpenVPN Access Server and click Protect.
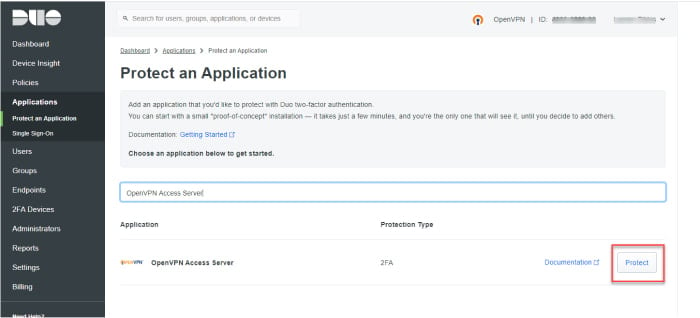
Access Server is added to your Duo-protected applications.
Note the integration key, secret key, and API key that are displayed for a future step in the configuration.
Next, you’ll download the post-auth script from Duo’s GitHub repository. Then you’ll add your integration key, secret key, and API hostname from the application configuration within your Duo Admin panel (noted above).
Download the Duo OpenVPN Access Server package from the duo_openvpn_as GitHub repository.
Extract the Duo OpenVPN Access Server package.
Open the duo_openvpn_as.py script with a text editor.
Find the section where you fill in your integration credentials and enter your integration key, secret key, and API hostname:
# Fill in your integration credentials on the following three lines: IKEY = 'DUO_INTEGRATION_KEY_HERE' SKEY = 'DUO_INTEGRATION_SECRET_KEY_HERE' HOST = 'DUO_API_HOSTNAME_HERE'
Move or upload the duo_openvpn_as.py script to the Access Server scripts folder (/usr/local/openvpn_as/scripts/) on your server.
Connect to your Access Server console and get root privileges.
Load the script and restart the Access Server service:
cd /usr/local/openvpn_as/scripts/ ./sacli --key "auth.module.post_auth_script" --value_file="/usr/local/openvpn_as/scripts/duo_openvpn_as.py" ConfigPut ./sacli start
Test your setup by signing in as a VPN user.
Tip
It would be good to test with both a user who is already enrolled in Duo authentication and one who is yet to enroll.
Duo also provides additional documentation on its website: OpenVPN Access Server Documentation, OpenVPN Access Server FAQ page, and OpenVPN Knowledge Base articles.
If you no longer use Duo for your users and need to remove the integration, follow these steps:
Connect to your Access Server console and get root privileges.
Remove the Duo setup:
cd /usr/local/openvpn_as/scripts/ ./sacli --key "auth.module.post_auth_script" ConfigDel
Reload the service to commit the changes:
./sacli start