Zero Trust and VPNs: NOT Mutually Exclusive
Never trust, always verify. This is the basic premise behind a zero trust network. Zero trust can be an important piece of your layered cybersecurity, requiring strict identification to access a network. You don’t trust a connection without verifying it carefully.
Many people in the tech industry have tried to paint the picture that zero trust and VPNs are mutually exclusive — but this could not be further from the truth. The right VPN solution will provide your business with all of the tools and capabilities necessary for building a strong zero trust network.
Take a look for yourself:
| Zero Trust Network | OpenVPN Access Server |
|---|---|
| Enforces Network Segmentation | Network segmentation is achieved using Group ACL (Access Control Lists). |
| Prevents Lateral Movement | Allows administrators to configure whether or not users have access to private subnets, preventing lateral movement. |
| Implements Access Control | Access control rules let administrators specify which user or group has access to which IP addresses or subnets, and if VPN clients can contact each other or not. |
| Prevents Threats | Leverage existing centralized network security infrastructure to provide a unified defense against cyber threats throughout the company’s networked devices regardless of location. |
As you can see, the right VPN provides zero trust architecture for your network, protecting your organization from the inside out.
“Claiming that your VPN doesn’t offer zero trust network access is like claiming your car isn’t safe because it doesn’t offer seatbelts. The seatbelts are there (in a good car, anyway) — you just have to actually use them if you want them to be effective. If you choose not to buckle up, you can hardly criticize the car for being unsafe.” - Francis Dinha, OpenVPN CEO
OpenVPN + Zero Trust In Action
Contrary to what we often see in the news, breaches are not just the result of cybercriminals hacking into a network. Many breaches start on the inside, which is why it is so important for organizations to never trust and always verify. One of the best ways to provide this type of zero trust protection is by configuring your VPN to provide access control.
With OpenVPN Access Server, you can allow LDAP Active Directory authentication: from there you can apply specific settings to your Access Server users to determine who can log on, and what network services they have access to. By configuring Access Server in this way, you are heading in the right direction towards “never trust, always verify.”
A great example of using OpenVPN Access Server for zero trust comes from an HVAC company. This company operates three large, independent divisions in the United States. They provide customers with a single, integrated solution for HVAC equipment, building automation, and system balancing needs.
It is essential that the company be able to verify every person accessing the network. Leaders need to ensure that team members have secure access to essential resources, while still preventing unauthorized entities from accessing sensitive data.
The company utilizes OpenVPN Access Server for the ability to implement the access control they need, using LDAP to access Active Directory. They set up an integration between OpenVPN Access Server and their Active Directory service, and now their server is configured so that team members only had access to the resources they need to get their jobs done.
The switch has had a dramatic impact on the employees and outside technical staff, allowing them to easily access the information they need to serve their customers — while providing the company with ways to ensure that only authorized users have access to the various resources.
Configuring OpenVPN Access Server For Zero Trust
Zero trust means always authenticating identity and never using the network as a boundary. With zero trust you need to authenticate everyone whether they are in the office using the corporate network or out of the office. A way to do this with Access Server is to require that everyone use the VPN to access sensitive resources — regardless of whether they are in the office or working remotely.
OpenVPN Access Server can be configured to allow LDAP Active Directory authentication: from there you can apply specific settings to your Access Server users to determine who can log on, and what information they can access. By configuring Access Server to allow LDAP, you are taking the control of your network into your own hands — which is exactly where it should be.
You can configure your Windows Server running an Active Directory so that OpenVPN Access Server can connect to it and use the objects in the directory for authentication. Through this, you can:
- enable SSL to ensure a secure link between Access Server and the Active Directory server
- configure rules for different Active Directory groups (for example: only allow one AD group to use the VPN while other groups are blocked)
- allow only specific Active Directory users to log in
- apply specific settings (like special access) to specific users and groups on Active Directory
To configure your Windows Server running an Active Directory:
1) Log on to the Admin UI as OpenVPN administrative user.
2) Go to Authentication, LDAP, and set the address of your server, bind user, and base DN of your LDAP directory.
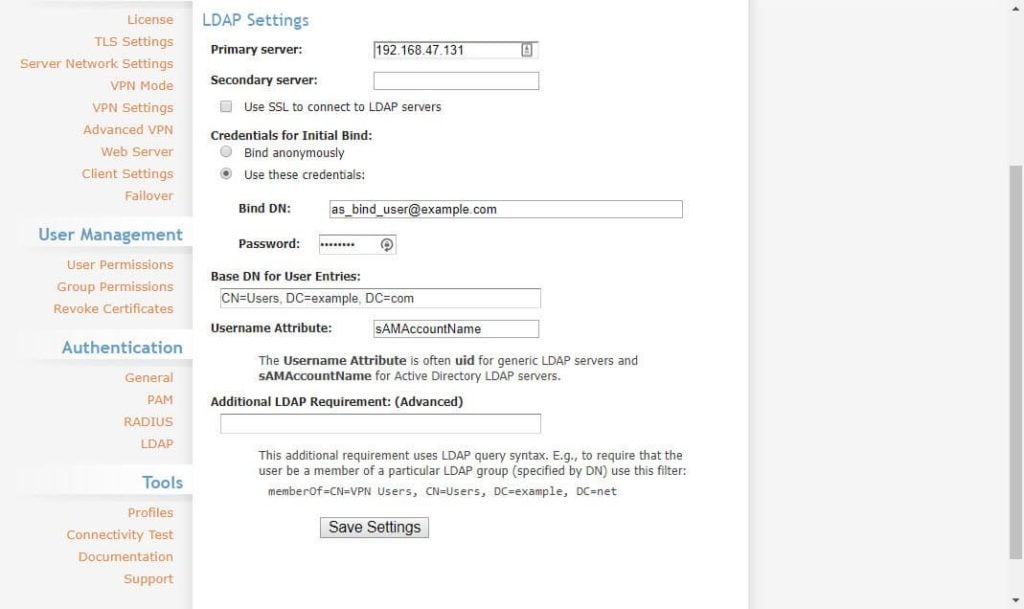
3) Click save settings to store the changes. There’s no need to click Update Running Server yet.
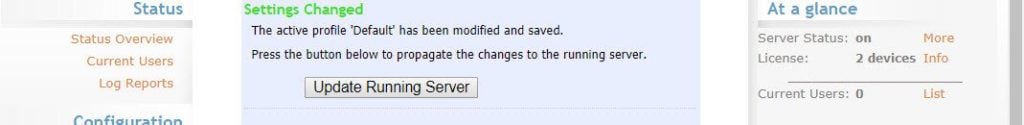
4) Go to Authentication, General, and set it to LDAP, and save settings.
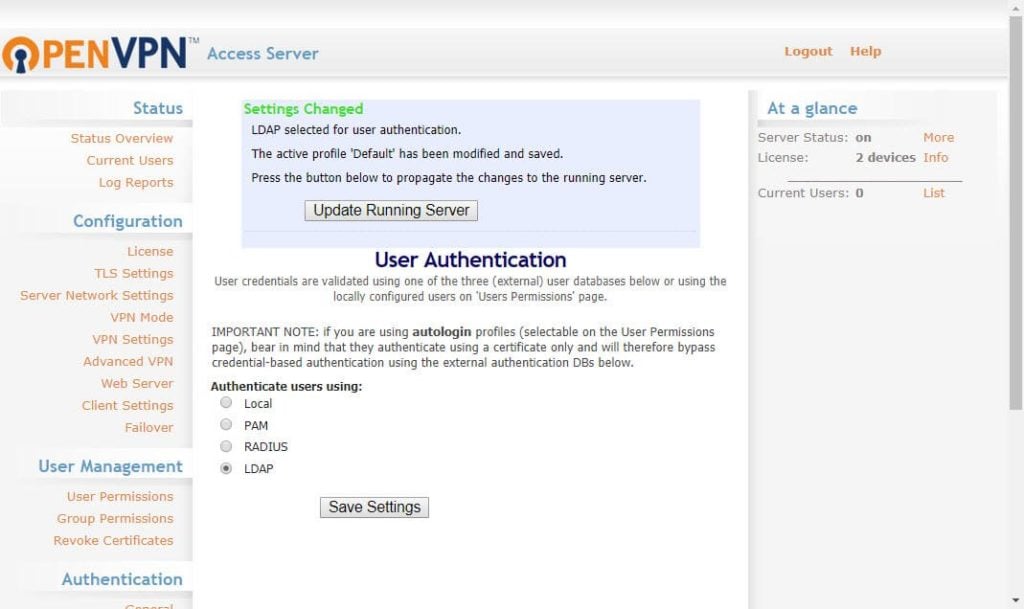
5) This time make sure to click Update running servers to implement the changes.
For more detailed instructions, we offer a step-by-step guide that will walk you through the process. It will also show you how to apply specific settings to Access Server users; allow only specific users to log on; and set it so that only users from a particular group can log on. In order to configure OpenVPN Access Server with Google Secure LDAP, you can also follow the instructions in this helpful Google Secure LDAP guide.
With OpenVPN Access Server, admins can set up permissions at the global, group, or user level, creating granular permissions, which are key parts of setting up a zero trust network.
Final Thoughts On Zero Trust Network Access
The majority of businesses adopt the incorrect (and unsafe) assumption that anything contained within their own network is trustworthy. But the truth is that security threats can arise quickly from within an organization. This is why it is so important to have the right security solutions in place, including a VPN and zero trust network.
Keep in mind that setting your business up with zero trust network will require a catered approach. Your business network won't be the same as another's. You likely have a hybrid setup, which combines both the existing architecture (on-site network folders, a locally-hosted database, etc) with cloud architecture (virtual private cloud, customer relationship management systems, hosted web domains, etc).
How do you protect all of this?
Establish perimeter protections for cloud deployments including micro tunnels and multi-factor authentication. Carefully implement securities that are still convenient for users and don't open you up to vulnerabilities.
It’s also important to define what zero trust means within your organization — and learn what it means to other organizations. When implementing and using zero trust technologies and practices, make sure there is clear communication with any other organization involved, since your definitions of “zero trust” might look drastically different than theirs.
And above all, be sure to leverage trusted solutions to your advantage. Your VPN has all of the capabilities you need to implement a strong zero trust network. Everything you need is right there waiting to be put into use.
If you have questions or would like assistance configuring your VPN for zero trust, reach out to the OpenVPN support team. We are here to help!